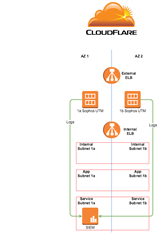
I understand that Sophos UTM 9 can send logs via syslog or snmp. I'm looking to setup external logging; high level idea in image below.
Currently I'm looking at either Splunk or ELK (Elasticache + LogStash + Kibana). Note that I cannot use a managed logging solution like Loggly or Sumo Logic.
The Splunk Add-on for Splunk doesn't seem like what I need and I'm not finding much documentation on how to properly export logs to a SIEM. I write properly because logging isn't as easy as it sounds; for example you shouldn't send syslogs straight to the syslog collector because of the collector is rebooted logs could disappear.
Sophos support told me that SNMP is the best way to export logs but again, I cannot find any examples with popular SIEMs to implement.
I also looked at the SUM to manage both Sophos UTM 9s but I didn't like the interface and the SUM doesn't do as much "centralized management" as I was hoping.
What is the community doing for centralized logging and if possible could you share config steps?
This thread was automatically locked due to age.