Hi all,
I make a habit of wondering through the UTM reports looking for trouble.
I came upon something that has me seriously alarmed.
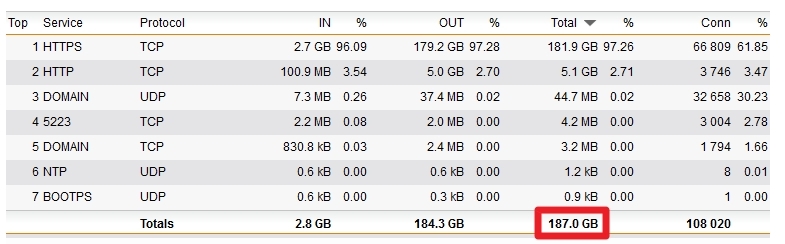
Under LOGGING & REPORTING \ Network Usage I query on "Top Services"
The first two are HTTP and HTTPS of course.
#3 is the focus. It says 8472.
This page explains https://tcp-udp-ports.com/port-8472.htm this is the port that VMWare uses for High Availability and Fault Tolerance between VSphere virtual machines. Those of us who regularly get general security news know that VMWare has it's kimono wide open to the world of hackers. It's not clear to me if there is any way to secure a VMWare environment.
I myself, pulled out all my VMWare infrastructure about a decade ago as I was thinking the company was not keeping up with the rise in security risks.
Since I don't have any of my own VMWare infrastructure, I was wondering if some other product I have is using it.
The only think I can think of is the Sophos UTM itself.
If this product is based on VMWare technology, I'm going to loose it. Quite literally. I'll replace the UTM the next day.
Backing up a bit: Can anyone help explains what this report means given I have no "known" VMWare technology in house?
Clicking around the reports a bit more, I found that all this traffic was coming from/to the UTM IP address.
So it seems the UTM is built on VMWare technology, this is probably a legacy decisioni from the original manufacturer, Astaros. Astaros Security Linux was the product if memory serves me. With this in mind, I'm just wondering if there's someone out there with the technical chops to assess the security risks of this product.
Much thanks, in advance.
Warmest Regards.
Doug
This thread was automatically locked due to age.