This is my network structure:
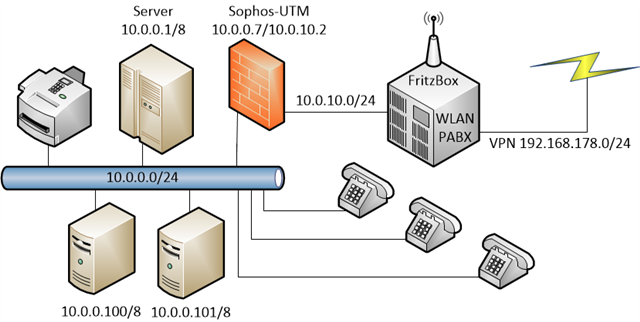
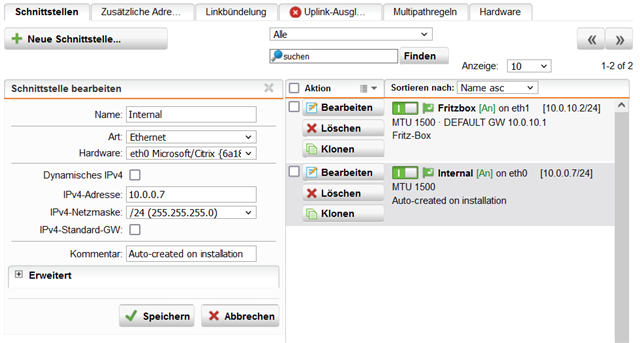
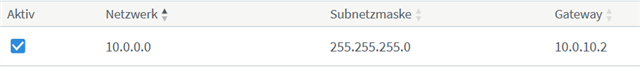
The Computers on the internal network are setup as 10.0.0.x/24 as well as the definition of the network on UTM9.
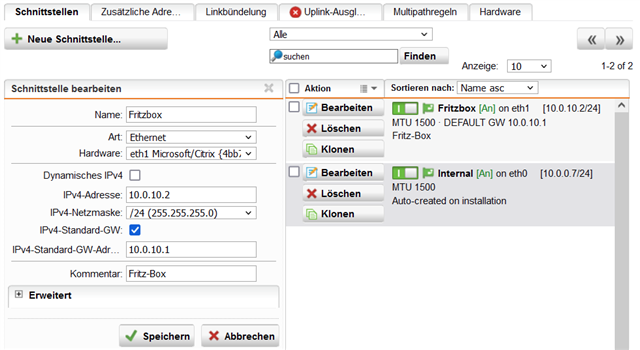
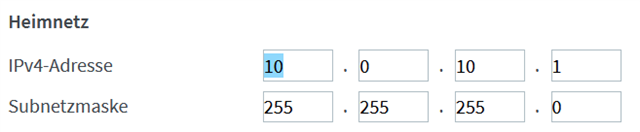
Behind the UTM9 firewall there is the Fritzbox, which is the gateway to the internet. For the FritBox I have assigned a 10.0.10.x/24 network.
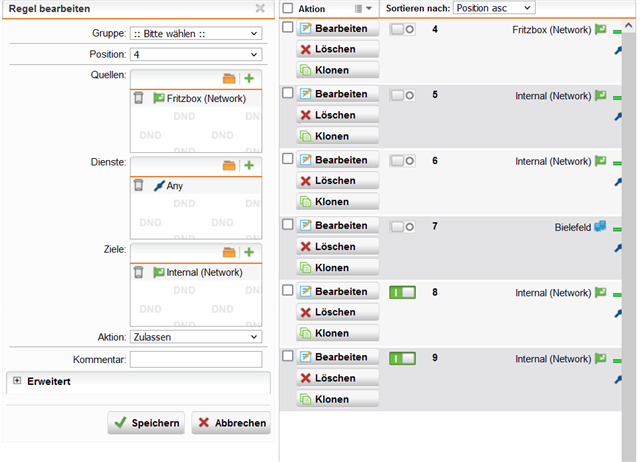
When I define a new firewall rule under Network Protection, to connect the 10.0.0.x/24 network to the 10.0.10.x/24 network in both direction for any IP protocol, should it than possible to connect to the FritzBox from the internal Computers? Also the IP-Phones need the connection to the FitzBox!
Before I have installed Sophos, I had a working VPN connection to another Fritzbox. If I setup also an additional firewall rule under Network Protection for the 192.168.178.0/24 network, should than again work this VPN?
Of cource, the above rules must be placed before the internet connection, so that Sophos UTM will the handle first!
I ask these questions, because I am not able to test it with the risk, that the connection to the internet will be disconnected, because I am runing an private Web-Radio and I don't want to interrupt my listeners!
Thanks a lot for your support!
** Summary **
Due to the fact, that it is a lot to read, I try summary it.
But first, many thanks to Phillipp for his help and patience.
It is important, that the internal network 10.0.0.0/24 and the Fritzbox network 10.0.10.0/24 are indepandant and also all clients in this networks have a 255.255.255.0 mask!
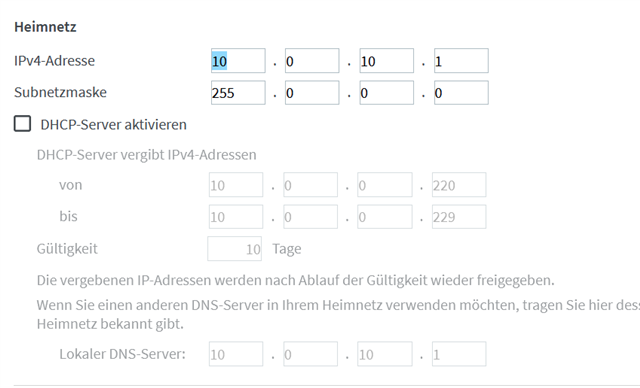
Therefore in the Fritzbox the DHCP-server has to be enabled, that clients on WLAN will get a IP. For that I have for the DHCP-Server set the gateway to the Fritzbox, but the DNS to an DNS-Server inside the internal Network.
In the Fritzbox under Home network->network properties->Static routing table you have to setup a entry for the internal network and the gateway has to be the external Sophos port on the Fritzbox network.
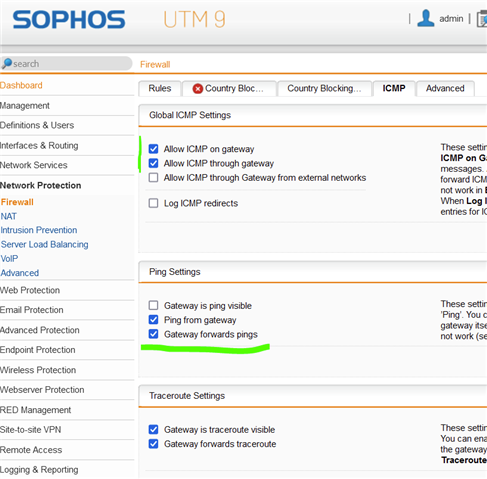
Finally in Sophos you need under network Protection->Firewall->Rules there is an entry necessary, which allows the traffic between the internal network and the FritzBox network.
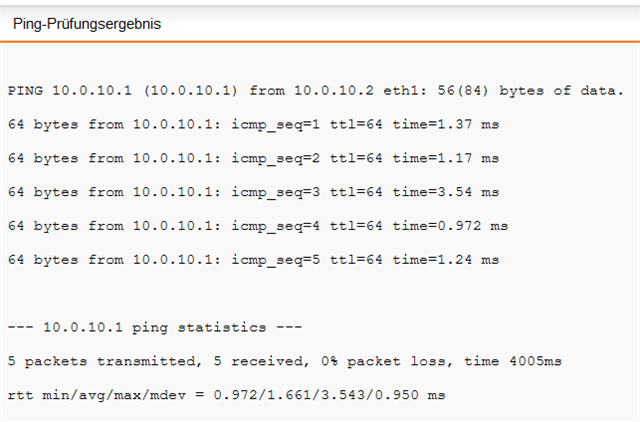
Than everything should work, including WLAN.
For the VPN I have setup a new VPN connection between the external FritzBox and Sophos.
This thread was automatically locked due to age.