Hello,
we use our Sophos UTM as a SMTP Relay in front of our Exchange Servers.
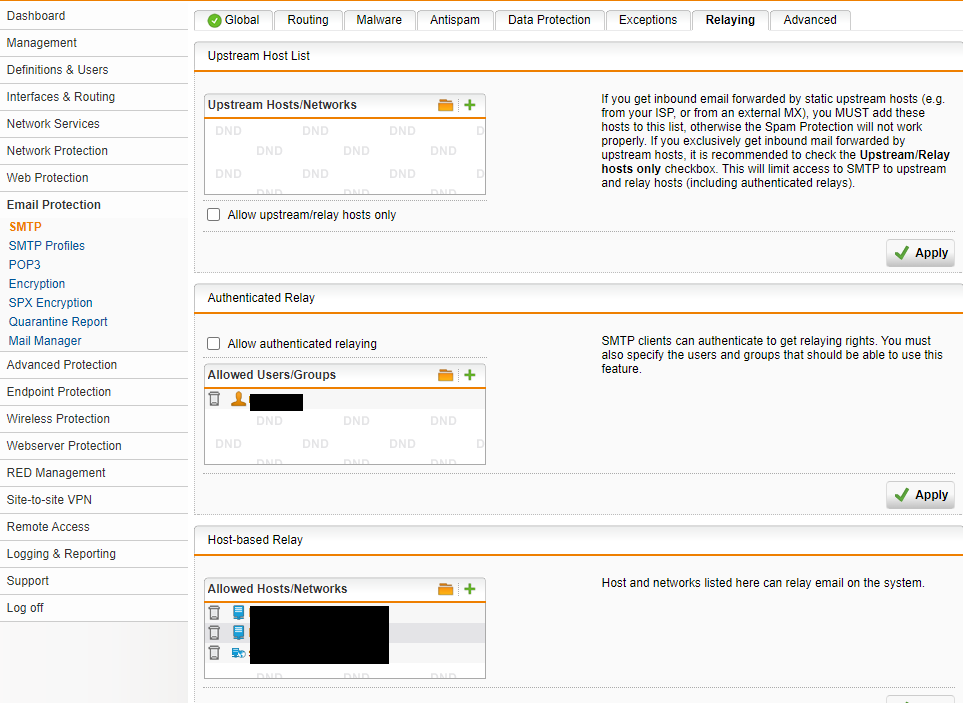
We have several Web applications that are hosted elsewhere an that use our Sophos as SMTP Relay - all of them figure in the list of "Allowed Hosts/Networks" under Host-based Relaying. That is working as expected.
Now I am about to configure a new Webapplication that needs to relay by user authentication. I add the user in the list of "Allowed users/groups" under "User based relay". That is working as expected.
The only problem is that by opening the "authenticated relaying", there are lots of Denied connections that potentially slow down the system, or even block user accounts after several denied connections.
I am looking for a way to limit the "Authenticated relaying" to a limited Network group (the IPs of my Web Application).
Can anybody help me?
Thanks,
George
This thread was automatically locked due to age.


