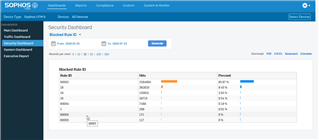
i m trying iview on my utm.
So i check the results , and see that dashboard:
What is this rule 60002 ??
I looked for it , and didn t understand exactly what it is .
May this kind of "rule" or blocking traffic reduce my network reactivity?
This thread was automatically locked due to age.