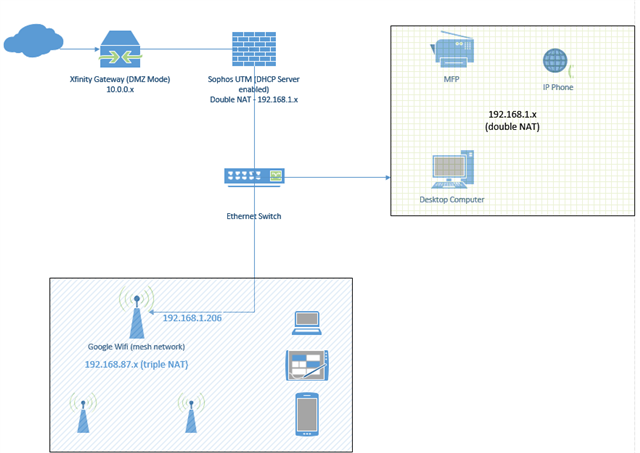
Hello,
I have installed Sophos UTM Home v9.409-9 on a fanless PC behind an Xfinity Arris Modem/Gateway in DMZ mode and it's working well. I do have a new problem though and am unsure how to best re-configure the UTM and/or the network. I was previously using a Unifi AC Lite AP connected to a switch behind the UTM, but am now trying a Google Wifi (3 pack) mesh wireless network. The problem is that the Google Wifi is a router and DHCP cannot be disabled so the hosts connected to the Google Wifi are triple NATed and therefore makes routing and inter-network communication challenging. I've made do by creating a firewall rule from the IP address of the main Google Wifi unit --> ANY --> Internet IPv4 to allow my Nest thermostats to reach the internet, but would like to resolve the triple NAT fiasco while still letting the UTM inspect all traffic from hosts on any of my internal networks.
The gateway used to be configured in Bridge mode, but it causes the UTM interface to lose connectivity often, which DMZ mode has resolved. However, the gateway's DHCP server is enabled, the UTM also has DHCP server enabled and the Google Wifi has DHCP server enabled. Cabling would be ideal, but isn't feasible due to the complexity of cabling through two stories of an existing home without ripping into too many walls.
Can anyone provide some advice on the best way to reconfigure the network or reconfigure the UTM to eliminate the triple NAT? Ideally, I'd like to have both wired and wireless devices on the same subnet and traffic still filtered through the UTM so I'd have more control over the devices behind the UTM. I also plan to add some IP security cameras connected to the ethernet jack on one of the Google Wifi Nodes but can't foresee how it's going to work with triple NAT.
Below is my current network diagram. Thanks in advance for your advice and assistance.
This thread was automatically locked due to age.