Just upgraded my SG230 Firewall to Firmware 9.720-5.
Since then, the usual passthrough.fw-notify URL as shown below:
(*****)://passthrough.fw-notify(dot)net/static/auth_transparent.html?return=(****)://www.google(dot)com/ Note: the above (*****) is "https" and (dot) is a period. Changed to avoid SPAM filtering on this forum
is returning an error message: "Invalid Request, check URL."
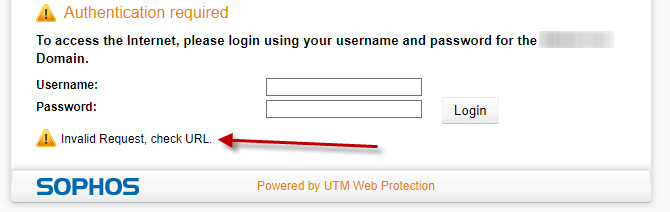
This always, in the past, simply authenticated the user and dumped them onto the Google home screen based on the "return" token in the URL. It appears that the users are being authenticated but the return URL token is not being parsed? This is making users think they are not authenticated.
This is what I find in the webfilter log:
Line 491: Line 51379: 2024:10:21-07:37:34 astaro httpproxy[5974]: id="0001" severity="info" sys="SecureWeb" sub="http" name="http access" action="pass" method="GET" srcip="10.241.1.157" dstip="" user="" group="" ad_domain="" statuscode="404" cached="0" profile="REF_uUXkJCrrpe (Main User-Based_Restrictions)" filteraction=" ()" size="2469" request="0x7fa54699ec00" url="(*****)://passthrough.fw-notify(dot)net/favicon.ico" referer="(*****)://passthrough.fw-notify(dot)net/static/auth_transparent.html?return=(*****)://www.google(dot)com/" error="File not found" authtime="0" dnstime="0" aptptime="0" cattime="0" avscantime="0" fullreqtime="1073277" device="0" auth="4" ua="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36" exceptions="" Again Note: the above (*****) is "https" and (dot) is a period. Changed to avoid SPAM filtering on this forum
Any ideas what is going on? No other changes made to the Firewall, just the FW update.
Thanks
