Hi All,
Our ISP is in the process of setting up a new WAN link which has automatic BGP failover for us and i need to work out the configurations need on our UTMs in order to get internal traffic to route properly in the event of failover.
The way the new link will work is 1 connection will be install in our primary site which will be the active link and the redundant link will be install in our backup site. The 2 sites are connected via an MPLS link as per the below diagram.
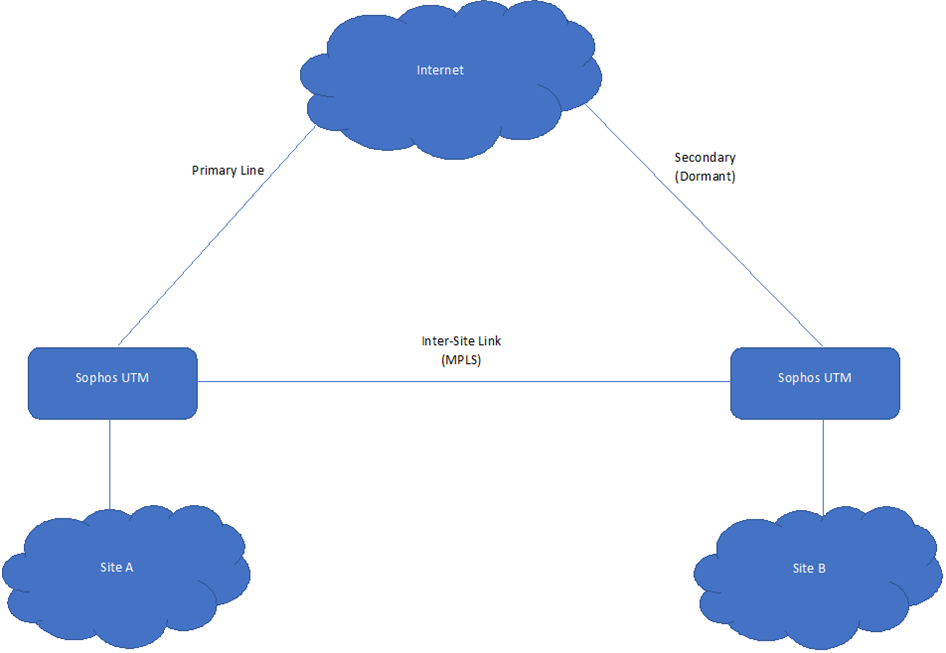
In the event the primary link fails the ISP will automatically route incoming traffic via the secondary link but we are responsible for ensuring that outgoing traffic works as needed.
Reading up on this i believe that the best way to achieve this would be to add a Default Gateway to the interface on the UTM in site A which will activate uplink balancing and then use multipath routes to route the traffic. The complication is that the MPLS is currently use for traffic destined for site B and this need to continue to work.
With this in mind I'm not sure if i set the Uplink Balancing as Active\Stand By or Active\Active and what the best way configuring any multipath riles would be.
Any assistance would be greatly appreciated.
Thanks,
Andrew
This thread was automatically locked due to age.


