My goal: Have a usergroup in Windows active Directory Users and Computers which can connect via SSL VPN but only access one specific (git) server we host via a url, not via an IP.
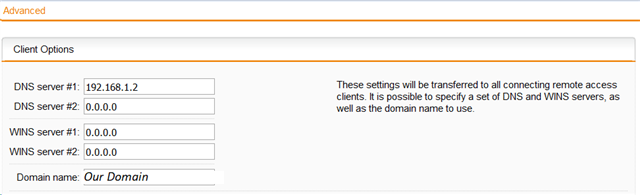
What I have achieved so far; the user can connect via VPN, it can access the server via the IP but if the user pings the url (subdomain.domain.com) it forwards to an external IP instead of the internal (192.168.1.4) IP. I cannot ping any other server on the network.
For other Network(and VPN) users we made a forward LookupZone(on the windows server) so the URL works as desired, but for this new VPN group it somehow doesn't use this forward lookup zone.
I only want the URL to be pointing to that internal IP when you are connected via VPN.
Attached some pictures of the setup now:
Remote Acces SSL Profile: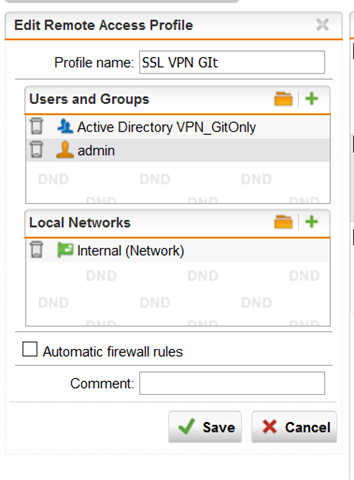
Network Protection-Firewall:(only copied the relevant rule for this group)

Network Definition of GIT repo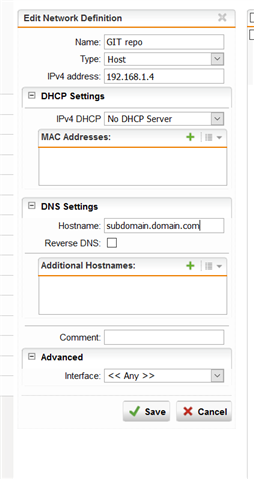
Preferably we stick with SSL VPN since the user will be using the vpn connection for pushing/pulling of code.
So how can we make that subdomain.domain.com points to 192.168.1.4 for the new vpn group?
This thread was automatically locked due to age.