Hi, this is my network diagram: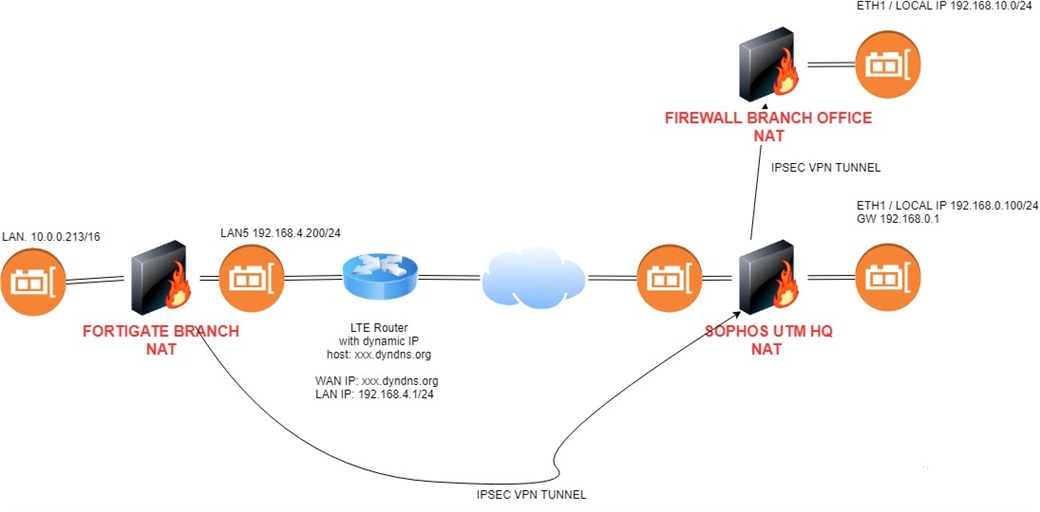
1) I am sitting on the left in the Fortigate Branch office at 10.0.0.0/16 and have a working vpn tunnel to the HQ to 192.168.1.0/24
2) SOPHOS UTM HQ has a working VPN tunnel to Firewall Branch office 192.168.10.0/24
I have two problems:
A) subnet 10.0.0.0/16 can not reach subnet 192.168.10.0/24
I have added a static route to 192.168.10.0/24 to the "fortinet branch device", to be sure that all traffic to this network is routed trough that tunnel.
So why is the Sophos UTM not forwarding any traffic to 192.168.10.0/24, this is a directly connected route. So it should be automatically forwarded.
A traffic rule policy is active to allow traffic fom ANY to 192.168.10.0/24
B) routing all traffic through the tunnel using the Sophos UTM as a final GW to the public internet is not working.
I would like to route all traffic from Fortigate Branch through the VPN tunnel using the Sophos UTM as a gateway to the public internet then.
Traffic enters and leaves the tunnel, but the Sophos UTM doesn't forward anything out through the WAN interface then.
the host 192.168.0.100 has perfect access to the public internet though, I have masquerading active.
Every help is very appreciated.
This thread was automatically locked due to age.


