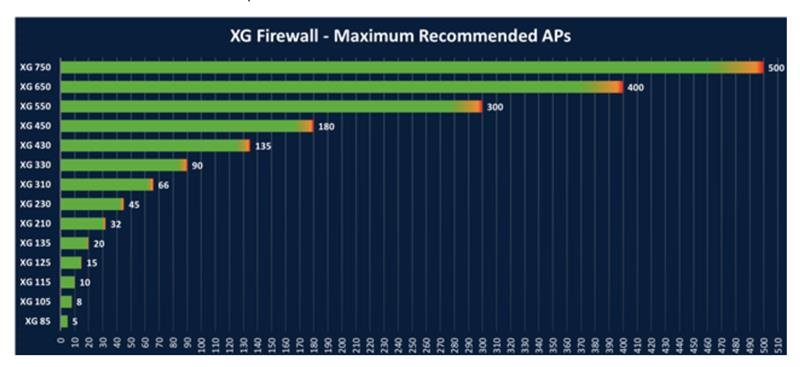
There is any UPDATED formal documentation from Sophos regarding how many Access Points can be managed by Firewall according the model?
This is the only documentation I have found but it's not updated. I'm interested for the new model XGS
This thread was automatically locked due to age.


