We have 2 Central Managed APs on the remote side of a SD RED 60 - in a VLAN.
There is a DHCP Server on XG on that VLAN Interface. The APs actually get IPs from DHCP Server on XG.
AP1 7c:5a:1c:05:0d:b0
AP2 7c:5a:1c:05:06:44
But on XG TCP Dump I can see that the APs are generating unreplied DHCP Discovers every 3 seconds. Also these packets are reported as dropped (well known and unresolved issue: Violation, Local_ACL)
I need to know the IP configuration directly from the AP: from which time is the current IP lease and when will it expire.
How can I get this information from the AP?
Lease list on XG DHCP:
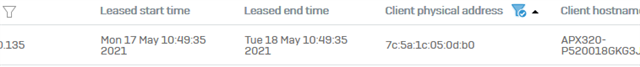
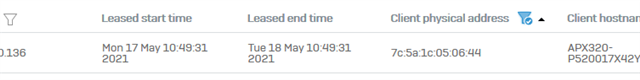
Discovers:
12:43:35.852984 reds24.1340, IN: IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 7c:5a:1c:05:0d:b0, length 300 12:43:38.893991 reds24, IN: ethertype IPv4, IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 7c:5a:1c:05:06:44, length 300 12:43:38.893991 reds24.1340, IN: IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 7c:5a:1c:05:06:44, length 300 12:43:38.923014 reds24, IN: ethertype IPv4, IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 7c:5a:1c:05:0d:b0, length 300 12:43:38.923014 reds24.1340, IN: IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 7c:5a:1c:05:0d:b0, length 300 12:43:41.963948 reds24, IN: ethertype IPv4, IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 7c:5a:1c:05:06:44, length 300 12:43:41.963948 reds24.1340, IN: IP 0.0.0.0.68 > 255.255.255.255.67: BOOTP/DHCP, Request from 7c:5a:1c:05:06:44, length 300
Discovers detail:
12:43:35.852984 reds24.1340, IN: IP (tos 0x0, ttl 64, id 0, offset 0, flags [none], proto UDP (17), length 328)
0.0.0.0.68 > 255.255.255.255.67: [udp sum ok] BOOTP/DHCP, Request from 7c:5a:1c:05:0d:b0, length 300, xid 0xfd2da40f, secs 31391, Flags [none] (0x0000)
Client-Ethernet-Address 7c:5a:1c:05:0d:b0
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
MSZ Option 57, length 2: 576
Parameter-Request Option 55, length 7:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Hostname
Domain-Name, BR, NTP
Vendor-Class Option 60, length 12: "udhcp 1.23.2"
12:43:38.893991 reds24.1340, IN: IP (tos 0x0, ttl 64, id 0, offset 0, flags [none], proto UDP (17), length 328)
0.0.0.0.68 > 255.255.255.255.67: [udp sum ok] BOOTP/DHCP, Request from 7c:5a:1c:05:06:44, length 300, xid 0x68f5c629, secs 31394, Flags [none] (0x0000)
Client-Ethernet-Address 7c:5a:1c:05:06:44
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
MSZ Option 57, length 2: 576
Parameter-Request Option 55, length 7:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Hostname
Domain-Name, BR, NTP
Vendor-Class Option 60, length 12: "udhcp 1.23.2"
12:43:38.923014 reds24.1340, IN: IP (tos 0x0, ttl 64, id 0, offset 0, flags [none], proto UDP (17), length 328)
0.0.0.0.68 > 255.255.255.255.67: [udp sum ok] BOOTP/DHCP, Request from 7c:5a:1c:05:0d:b0, length 300, xid 0xfd2da40f, secs 31394, Flags [none] (0x0000)
Client-Ethernet-Address 7c:5a:1c:05:0d:b0
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
MSZ Option 57, length 2: 576
Parameter-Request Option 55, length 7:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Hostname
Domain-Name, BR, NTP
Vendor-Class Option 60, length 12: "udhcp 1.23.2"
12:43:41.963948 reds24.1340, IN: IP (tos 0x0, ttl 64, id 0, offset 0, flags [none], proto UDP (17), length 328)
0.0.0.0.68 > 255.255.255.255.67: [udp sum ok] BOOTP/DHCP, Request from 7c:5a:1c:05:06:44, length 300, xid 0x68f5c629, secs 31397, Flags [none] (0x0000)
Client-Ethernet-Address 7c:5a:1c:05:06:44
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Discover
MSZ Option 57, length 2: 576
Parameter-Request Option 55, length 7:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Hostname
Domain-Name, BR, NTP
Vendor-Class Option 60, length 12: "udhcp 1.23.2"
XG dropped DHCP packets:
2021-05-17 12:43:35 0103021 IP 0.0.0.0.68 > 255.255.255.255.67 : proto UDP: packet len: 308 checksum : 47087 Date=2021-05-17 Time=12:43:35 log_id=0103021 log_type=Firewall log_component=Local_ACLs log_subtype=Denied log_status=N/A log_priority=Alert duration=N/A in_dev=reds24.1340 out_dev= inzone_id=13 outzone_id=4 source_mac=7c:5a:1c:05:0d:b0 dest_mac=ff:ff:ff:ff:ff:ff bridge_name= l3_protocol=IPv4 source_ip=0.0.0.0 dest_ip=255.255.255.255 l4_protocol=UDP source_port=68 dest_port=67 fw_rule_id=N/A policytype=0 live_userid=0 userid=0 user_gp=0 ips_id=0 sslvpn_id=0 web_filter_id=0 hotspot_id=0 hotspotuser_id=0 hb_src=0 hb_dst=0 dnat_done=0 icap_id=0 app_filter_id=0 app_category_id=0 app_id=0 category_id=0 bandwidth_id=0 up_classid=0 dn_classid=0 nat_id=0 cluster_node=0 inmark=0x0 nfqueue=0 gateway_offset=0 connid=1502713472 masterid=0 status=256 state=0, flag0=687196864512 flags1=0 pbdid_dir0=0 pbrid_dir1=0 2021-05-17 12:43:38 0103021 IP 0.0.0.0.68 > 255.255.255.255.67 : proto UDP: packet len: 308 checksum : 12663 Date=2021-05-17 Time=12:43:38 log_id=0103021 log_type=Firewall log_component=Local_ACLs log_subtype=Denied log_status=N/A log_priority=Alert duration=N/A in_dev=reds24.1340 out_dev= inzone_id=13 outzone_id=4 source_mac=7c:5a:1c:05:06:44 dest_mac=ff:ff:ff:ff:ff:ff bridge_name= l3_protocol=IPv4 source_ip=0.0.0.0 dest_ip=255.255.255.255 l4_protocol=UDP source_port=68 dest_port=67 fw_rule_id=N/A policytype=0 live_userid=0 userid=0 user_gp=0 ips_id=0 sslvpn_id=0 web_filter_id=0 hotspot_id=0 hotspotuser_id=0 hb_src=0 hb_dst=0 dnat_done=0 icap_id=0 app_filter_id=0 app_category_id=0 app_id=0 category_id=0 bandwidth_id=0 up_classid=0 dn_classid=0 nat_id=0 cluster_node=0 inmark=0x0 nfqueue=0 gateway_offset=0 connid=4087512576 masterid=0 status=256 state=0, flag0=687196864512 flags1=0 pbdid_dir0=0 pbrid_dir1=0 2021-05-17 12:43:38 0103021 IP 0.0.0.0.68 > 255.255.255.255.67 : proto UDP: packet len: 308 checksum : 47084 Date=2021-05-17 Time=12:43:38 log_id=0103021 log_type=Firewall log_component=Local_ACLs log_subtype=Denied log_status=N/A log_priority=Alert duration=N/A in_dev=reds24.1340 out_dev= inzone_id=13 outzone_id=4 source_mac=7c:5a:1c:05:0d:b0 dest_mac=ff:ff:ff:ff:ff:ff bridge_name= l3_protocol=IPv4 source_ip=0.0.0.0 dest_ip=255.255.255.255 l4_protocol=UDP source_port=68 dest_port=67 fw_rule_id=N/A policytype=0 live_userid=0 userid=0 user_gp=0 ips_id=0 sslvpn_id=0 web_filter_id=0 hotspot_id=0 hotspotuser_id=0 hb_src=0 hb_dst=0 dnat_done=0 icap_id=0 app_filter_id=0 app_category_id=0 app_id=0 category_id=0 bandwidth_id=0 up_classid=0 dn_classid=0 nat_id=0 cluster_node=0 inmark=0x0 nfqueue=0 gateway_offset=0 connid=4087512576 masterid=0 status=256 state=0, flag0=687196864512 flags1=0 pbdid_dir0=0 pbrid_dir1=0 2021-05-17 12:43:41 0103021 IP 0.0.0.0.68 > 255.255.255.255.67 : proto UDP: packet len: 308 checksum : 12660 Date=2021-05-17 Time=12:43:41 log_id=0103021 log_type=Firewall log_component=Local_ACLs log_subtype=Denied log_status=N/A log_priority=Alert duration=N/A in_dev=reds24.1340 out_dev= inzone_id=13 outzone_id=4 source_mac=7c:5a:1c:05:06:44 dest_mac=ff:ff:ff:ff:ff:ff bridge_name= l3_protocol=IPv4 source_ip=0.0.0.0 dest_ip=255.255.255.255 l4_protocol=UDP source_port=68 dest_port=67 fw_rule_id=N/A policytype=0 live_userid=0 userid=0 user_gp=0 ips_id=0 sslvpn_id=0 web_filter_id=0 hotspot_id=0 hotspotuser_id=0 hb_src=0 hb_dst=0 dnat_done=0 icap_id=0 app_filter_id=0 app_category_id=0 app_id=0 category_id=0 bandwidth_id=0 up_classid=0 dn_classid=0 nat_id=0 cluster_node=0 inmark=0x0 nfqueue=0 gateway_offset=0 connid=1409960448 masterid=0 status=256 state=0, flag0=687196864512 flags1=0 pbdid_dir0=0 pbrid_dir1=0 2021-05-17 12:43:41 0103021 IP 0.0.0.0.68 > 255.255.255.255.67 : proto UDP: packet len: 308 checksum : 47081 Date=2021-05-17 Time=12:43:41 log_id=0103021 log_type=Firewall log_component=Local_ACLs log_subtype=Denied log_status=N/A log_priority=Alert duration=N/A in_dev=reds24.1340 out_dev= inzone_id=13 outzone_id=4 source_mac=7c:5a:1c:05:0d:b0 dest_mac=ff:ff:ff:ff:ff:ff bridge_name= l3_protocol=IPv4 source_ip=0.0.0.0 dest_ip=255.255.255.255 l4_protocol=UDP source_port=68 dest_port=67 fw_rule_id=N/A policytype=0 live_userid=0 userid=0 user_gp=0 ips_id=0 sslvpn_id=0 web_filter_id=0 hotspot_id=0 hotspotuser_id=0 hb_src=0 hb_dst=0 dnat_done=0 icap_id=0 app_filter_id=0 app_category_id=0 app_id=0 category_id=0 bandwidth_id=0 up_classid=0 dn_classid=0 nat_id=0 cluster_node=0 inmark=0x0 nfqueue=0 gateway_offset=0 connid=1409957888 masterid=0 status=256 state=0, flag0=687196864512 flags1=0 pbdid_dir0=0 pbrid_dir1=0
This thread was automatically locked due to age.
