Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Note: Support would not be provided for this tool via Sophos Support
Overview
This recommended read describes the automated audit tool allowing you to audit one or more Sophos firewalls to comply with baseline security settings. The audit compares a defined set of expected settings (the baseline) with each firewall's actual running configuration and produces an HTML report indicating the audit Pass/Fail status.
Installation and Requirement:
The firewall audit can be installed using the Python pip installer. Python 3.9 is the minimum version required on your system prior to installation. We recommend installing it into a Python virtual environment so as not to interfere with any other Python packages installed on your system.
The scenario would use Python 3.12 as interpreter and Pycharm as IDE and will use a Windows environment.
Installation Steps:
Create Python Venv on IDE
python -m venv firewallaudit
![]()
Start the venv on IDE - for Windows
firewallaudit\Scripts\activate.bat
![]()
Download the sophos-firewall-audit
pip install sophos-firewall-audit
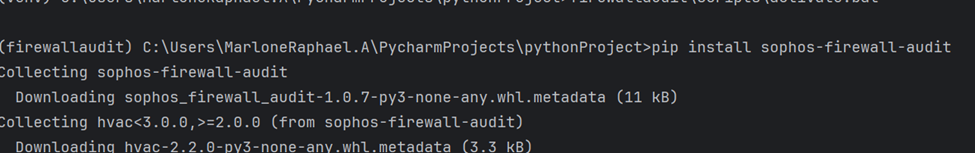
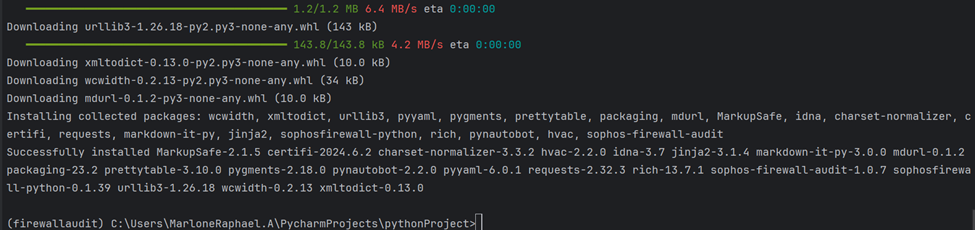
Note: Windows users may see the error message ModuleNotFoundError: No module named 'pkg_resources' when running the sophosfirewallaudit command. To correct this, run pip install setup tools.
Install setuptools to address the error
pip install setuptools
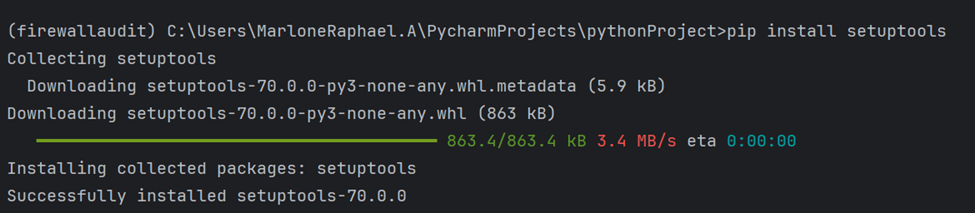
--help will now run.
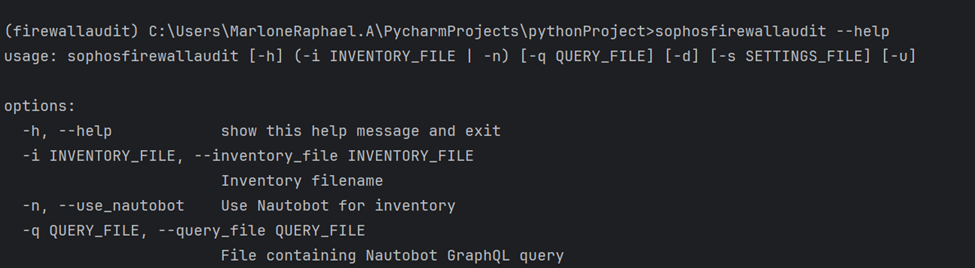
Update the firewall.yaml file of your firewall inventory
You may also down the example here: https://github.com/sophos/sophos-firewall-audit/blob/main/firewalls.yaml.example
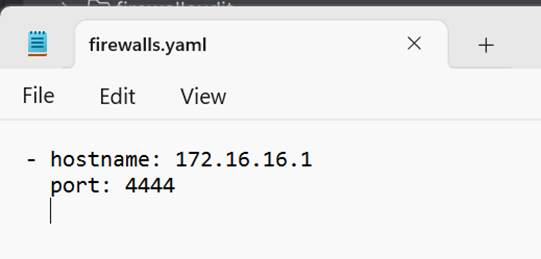
Here, you may also put more than one firewall on the list using the format:
-hostname: 172.16.16.1
port: 4444
hostname: 34dtmxgsfw1.ddns.net
port: 4444
hostname: 10.153.189.23
port: 4444
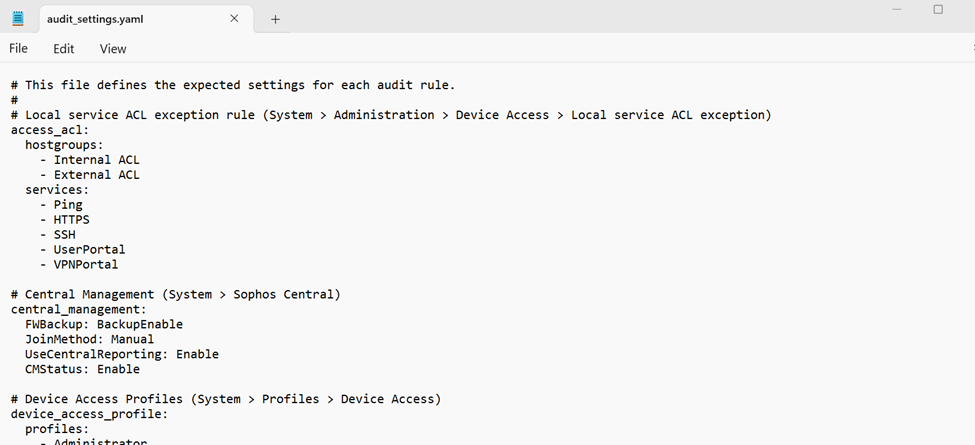
Update the auditsettings.yaml file
Example download is available here: https://github.com/sophos/sophos-firewall-audit/blob/main/audit_settings.yaml.example
You may use the default settings or tailor-fit it to your requirements.
Copy/save the Yaml files in your working directory.
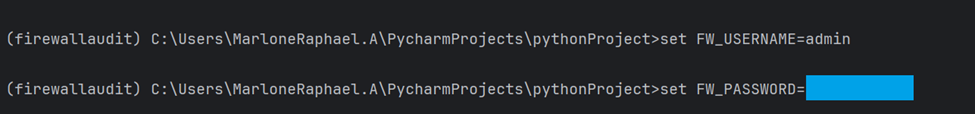
Set Credentials on Windows CMD
set FW_USERNAME=<Your firewall username>
set FW_PASSWORD=<Your firewall password>
You may also allow administrators with specific read-write permissions API access. Kindly refer here:
Note: Ensure you're configuring the set on CMD, not Powershell. When we use set in the PowerShell prompt, we set the variables rather than the environment variables. The audit script is trying to pull the credentials from the system environment, so it can't find those.
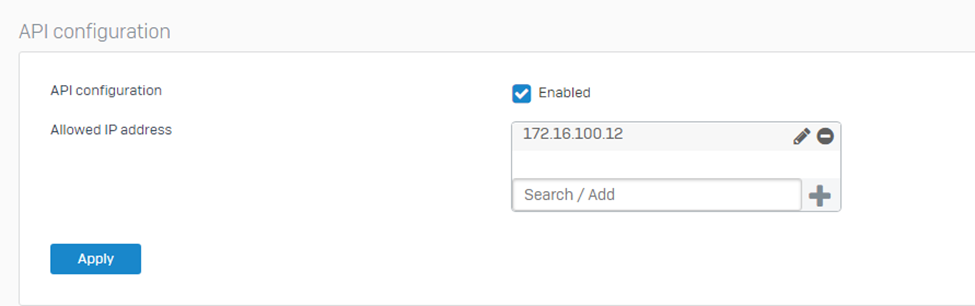
Confirm that API is turned on on the Target Sophos Firewall/s, including the allowed IP Address.
Under > Backup and firmware > API > API configuration
Run Audit: sophosfirewallaudit --inventory_file firewalls.yaml --settings_file audit_settings.yaml
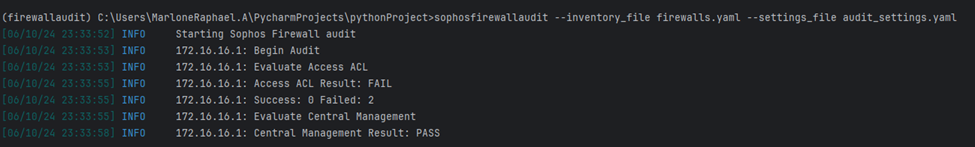
After running the command, the audit process will begin.
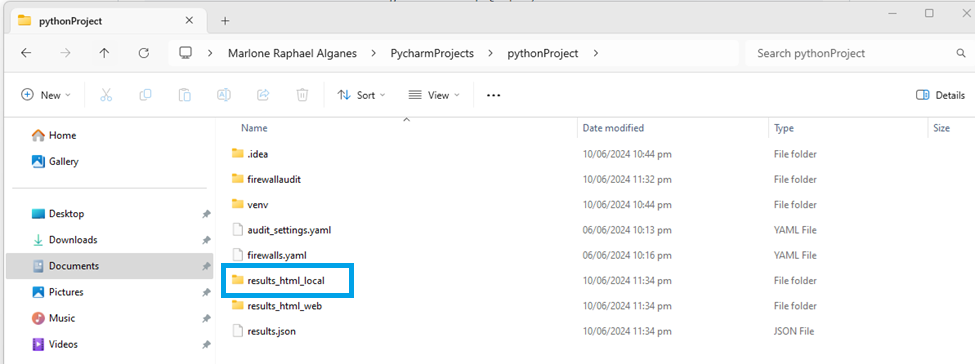
View Results locally > results_html_local > index HTML
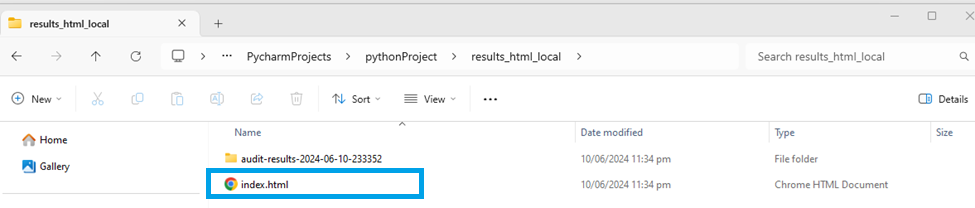
Viewing Sophos Firewall Audit Report
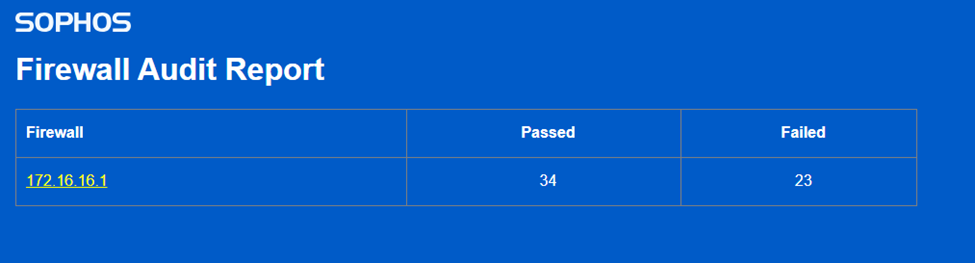
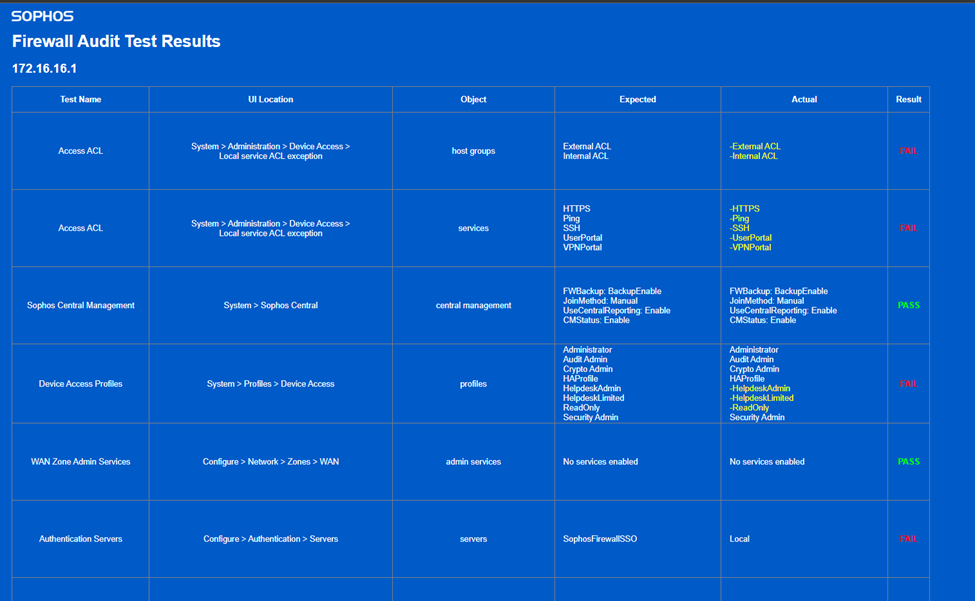
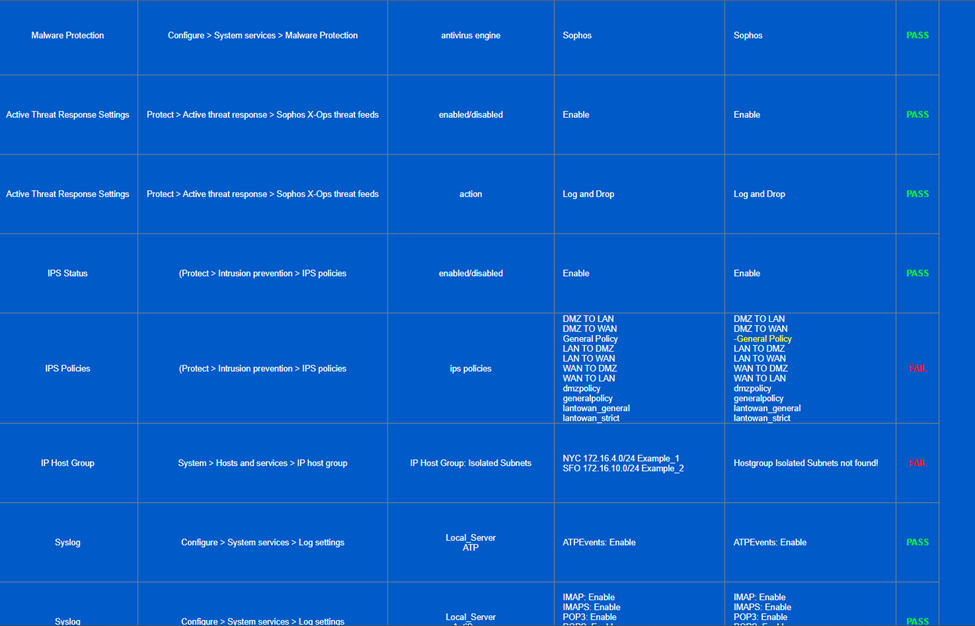
Related Information:
Further Information—The firewall audit is published as an open-source project on Github and can be installed using the instructions in the repository.
https://github.com/sophos/sophos-firewall-audit
Revamped spelling, spacing and grammar
[edited by: Erick Jan at 5:23 AM (GMT -8) on 27 Nov 2024]

