Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Note: The following KB is an updated version of the Sophos Firewall and Oracle Cloud Infrastructure (OCI) policy-based IPsec
Table of Contents
Overview
This Recommended Read describes how to configure Sophos Firewall with Oracle Cloud Infrastructure VCN.
Network Diagram
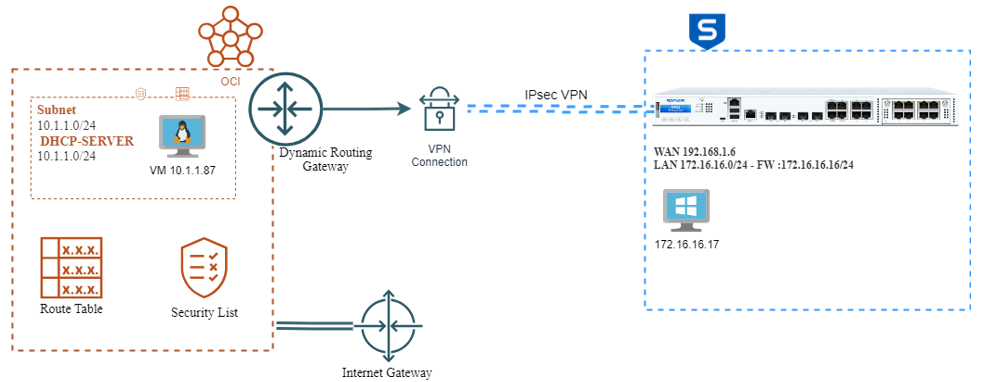
Oracle Cloud Infrastructure (OCI)
It is a platform of cloud services that enables you to build and run a wide range of applications in a high-availability. For more reference, see the link www.oracle.com/.../
In OCI, the IPsec Tunnel is composed of three objects
- Dynamic Routing Gateway ( DRG)
- Customer-Premise Equipment ( CPE)
- IPsec Connection
Configuration
VCN
In the console, go to the Main menu>Network>Virtual Cloud Network> Create VCN
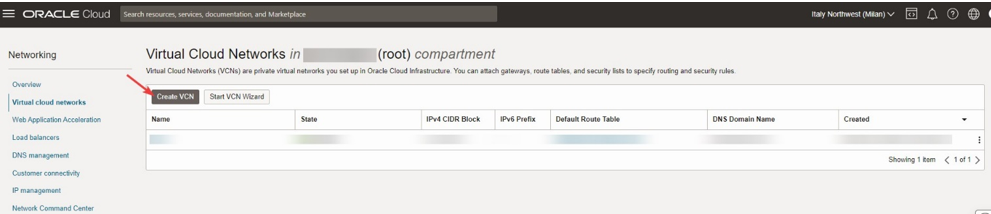
Select Compartment and insert IPv4 CIDR Blocks. For the following example we use 10.1.0.0/16
To create a virtual Cloud Network. In Networking> Virtual Cloud Networks> Virtual Cloud Network Details
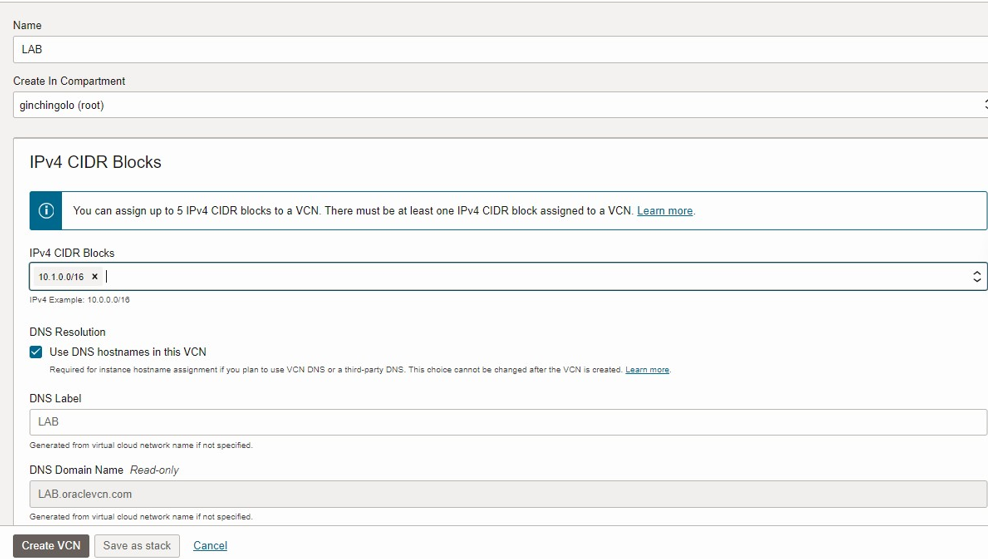
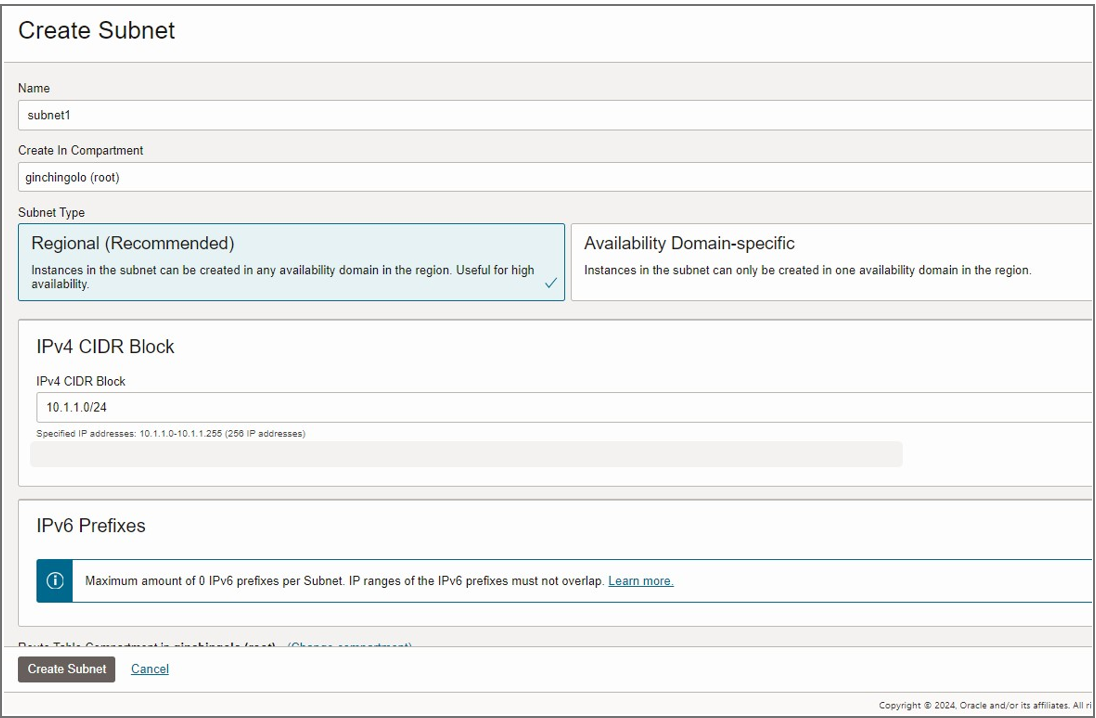
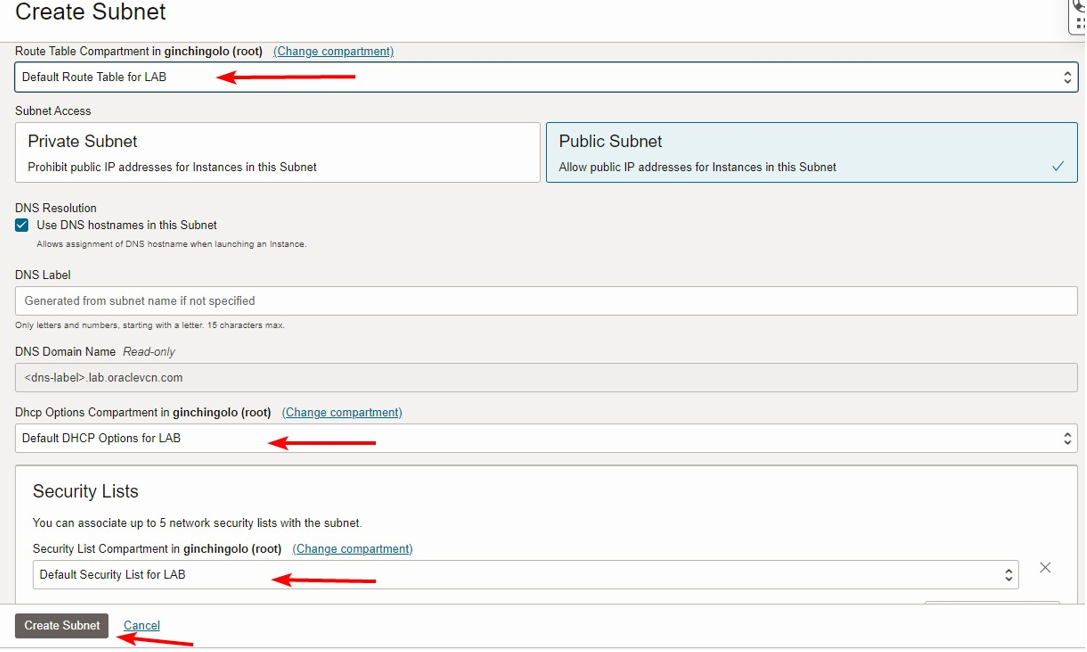
Create Subnet
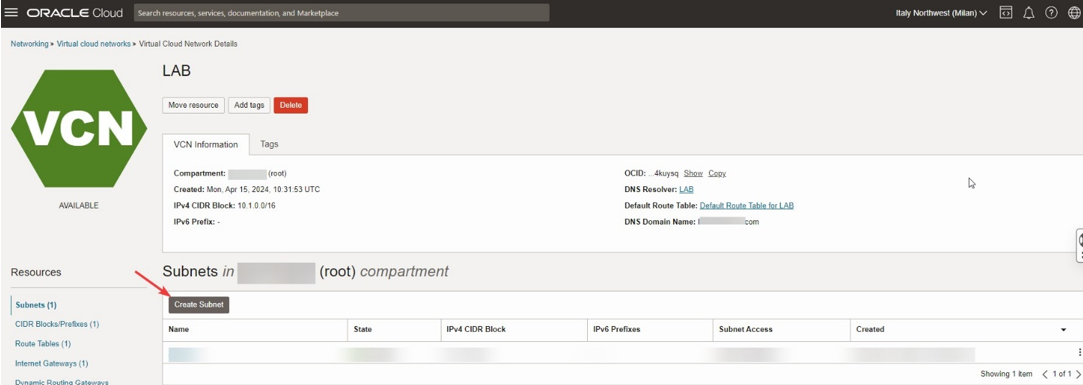
In Networking>Virtual Cloud Networks>Virtual Cloud Network>Click Create Subnet.
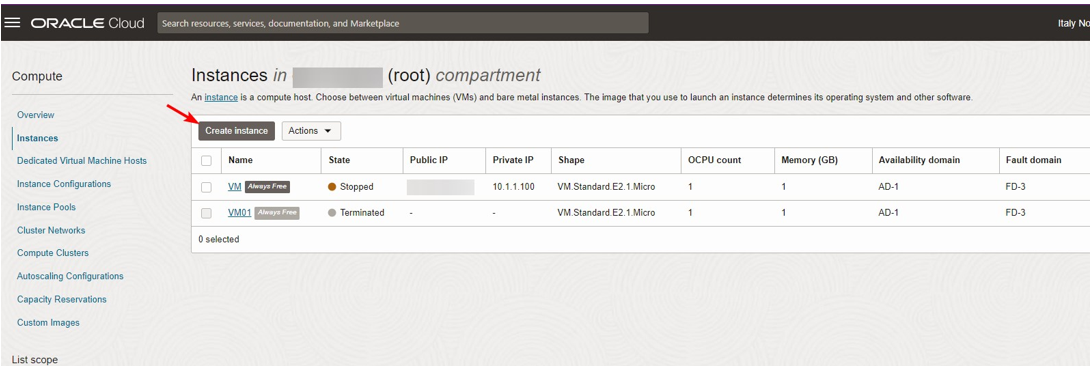
VM Instances
VM Instances
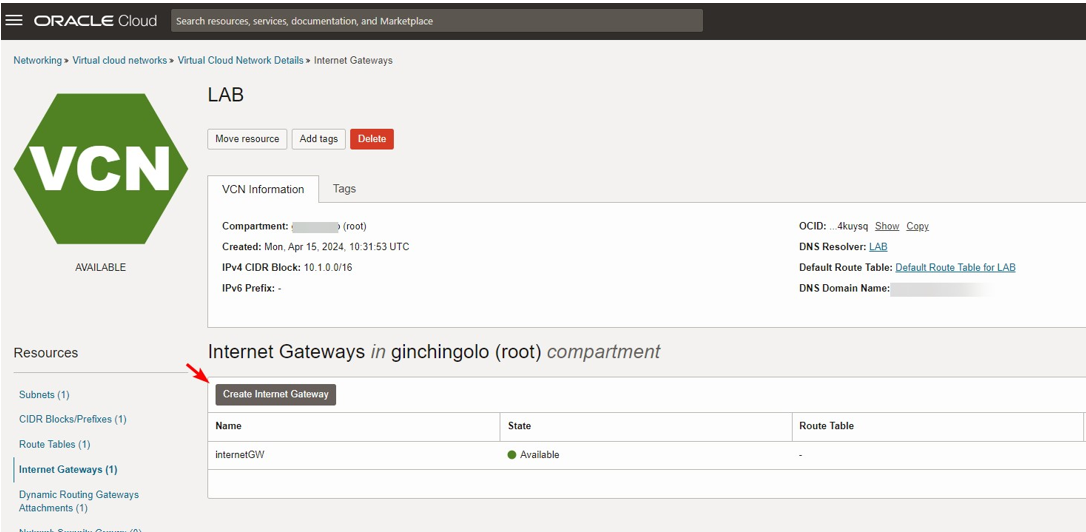
Go to Networking>Virtual Cloud Network> Virtual Cloud Network> Create Internet Gateways.
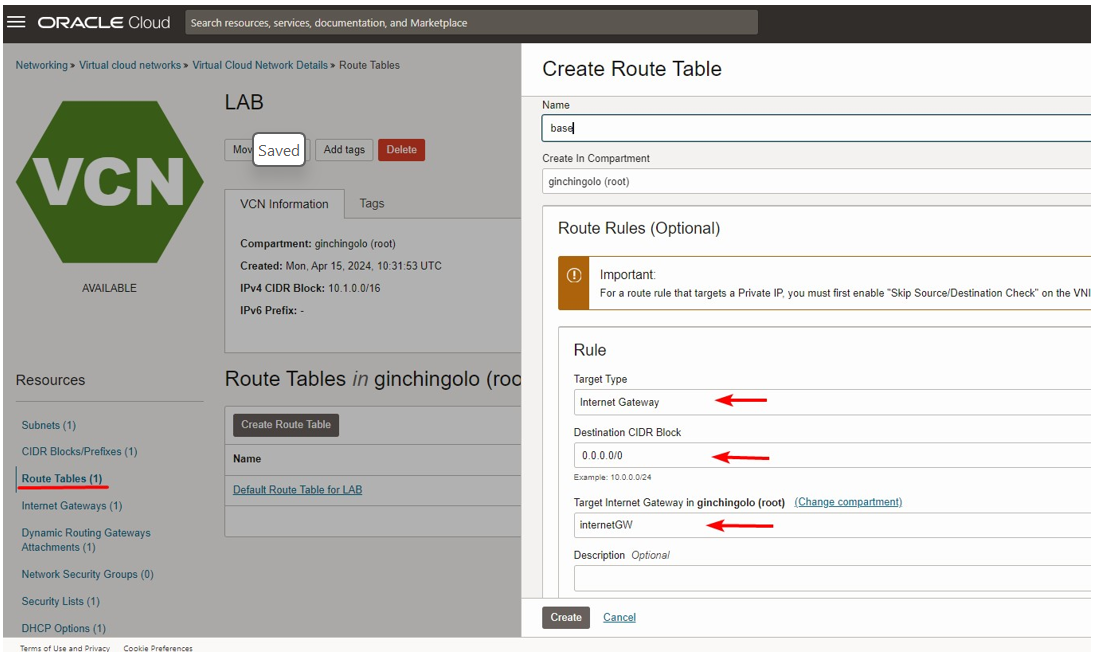
Routing Tables
Configure the following
- Target Type: Internet Gateway
- Destination CIDR Block: 0.0.0.0/0
- Target;internetGW
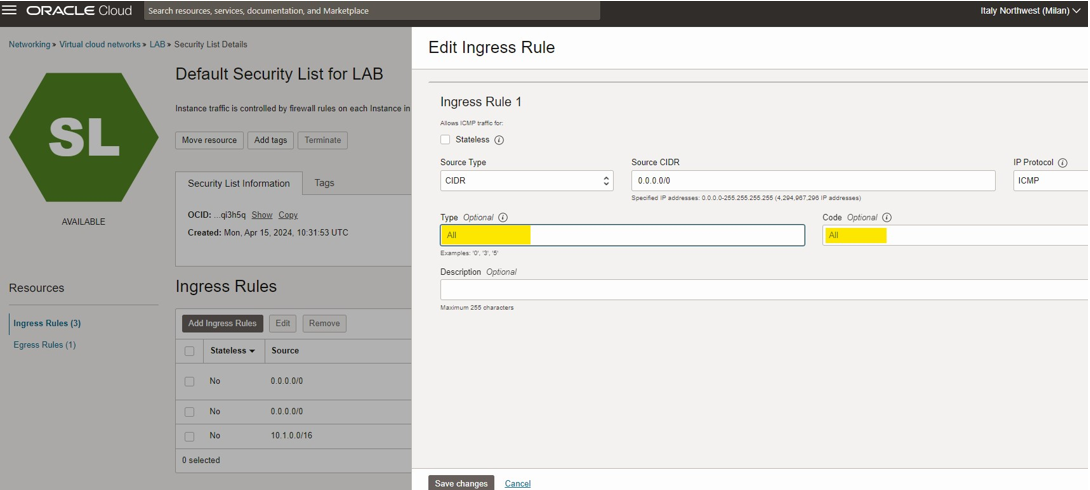
Security List
To change security and turn on ICMP for testing.
Under Networking>Virtual Cloud Network>LAB> Security List Details
Dynamic Routing Gateways
Go To Networking>Customer Connectivity>Dynamic Routing Gateways
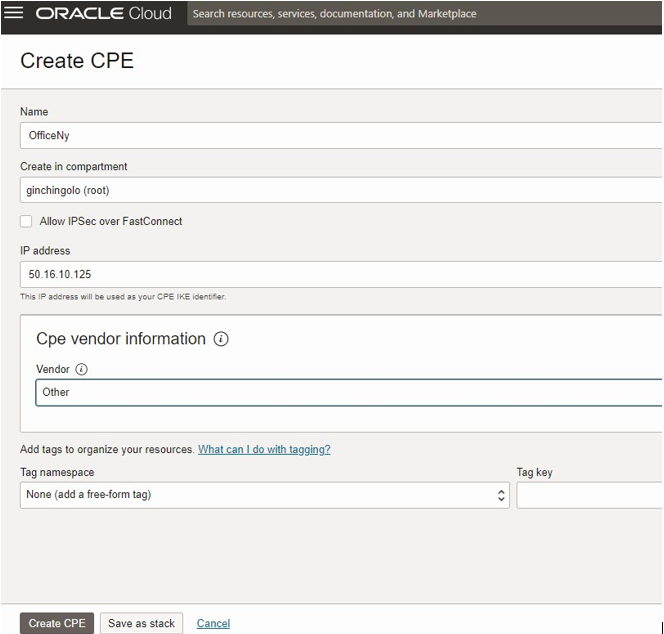
Customer-Premises Equipment( CPE)
Create CPE with ISP Address
IPsec Connection
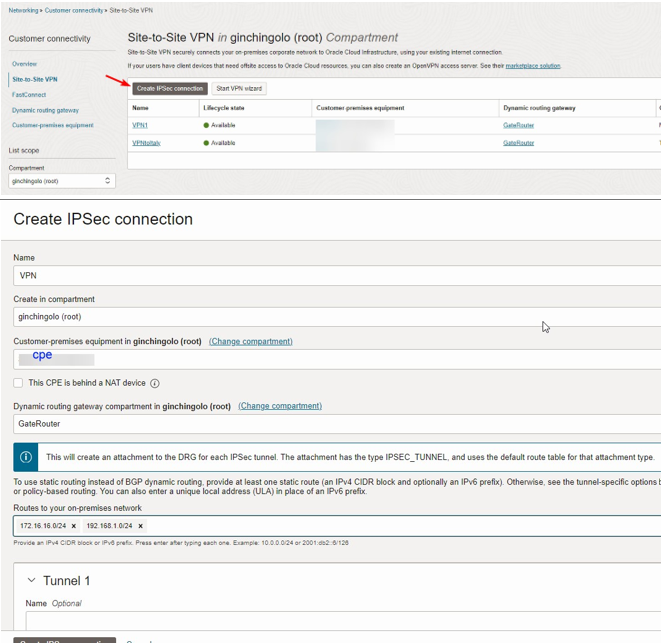
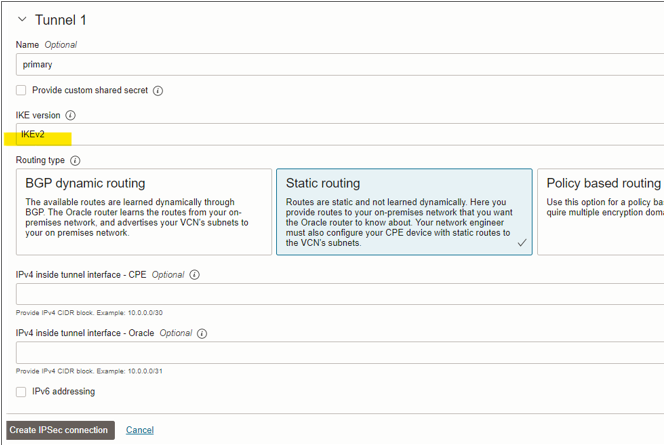
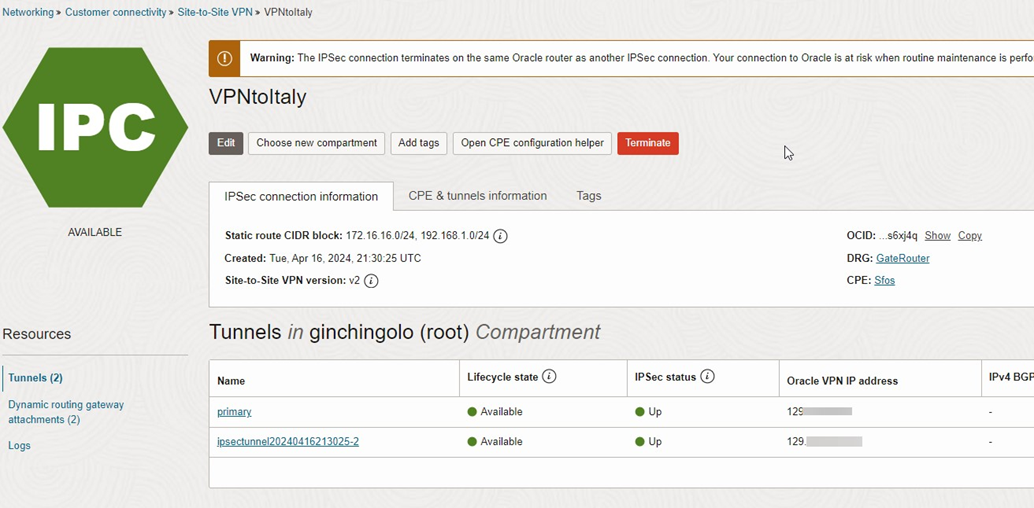
To create a VPN, go to Networking>Customer Connectivity>Site-to-site VPN and input all the necessary information.
- CPE
- IKE Version
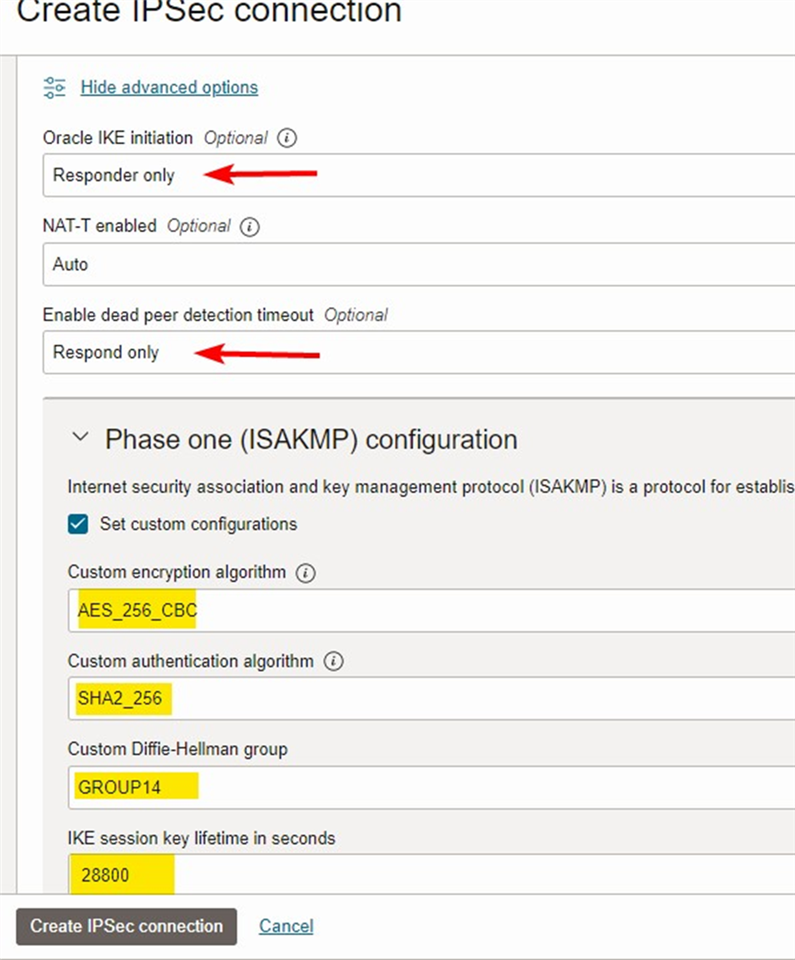
- Oracle IKE Initiation
- DPD
- Phase one & Phase two Configuration
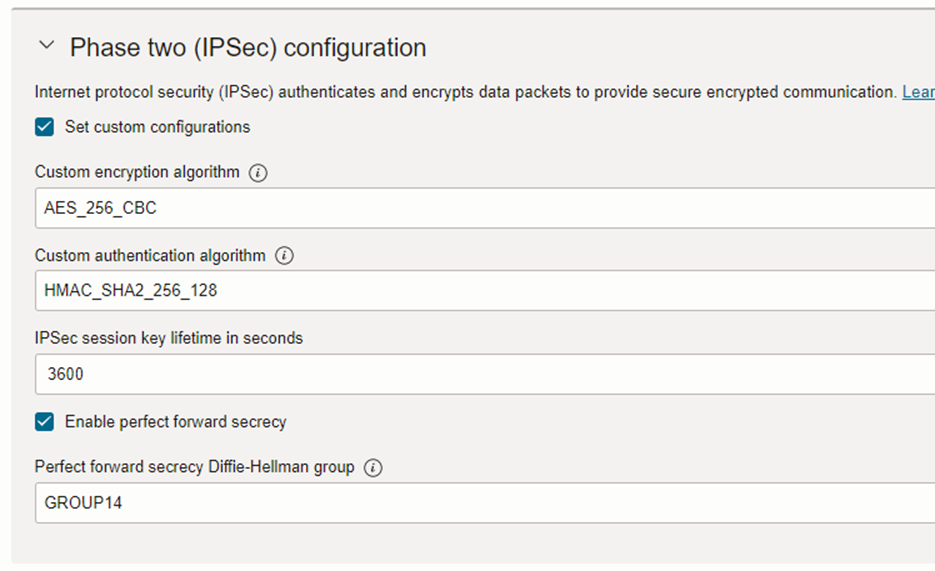
Follow the screenshot for more details.
Sophos Firewall Configuration
Version 20 firmware is used for the example. For Site-to-site VPN. kindly Go to
Configure>Site-to-site VPN
Ipsec Policies
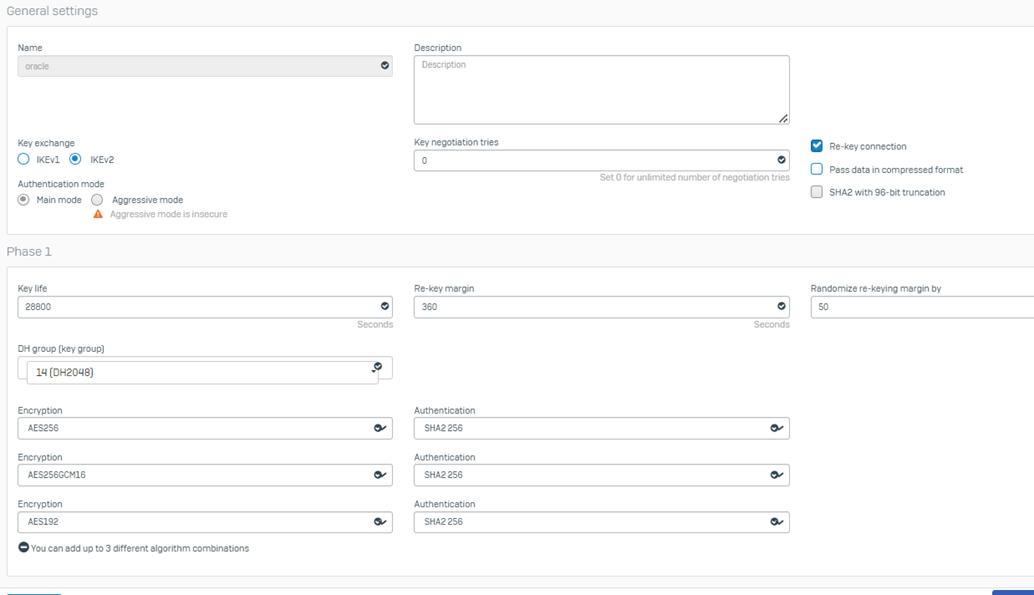
Click the Add button and define Phase one and Phase Two as noted below
Phase 1
- mode: main
- Allow re-keying
- dh group: 14
- lifetime:28800
- encryption aes-256
- authentication:sha2 256
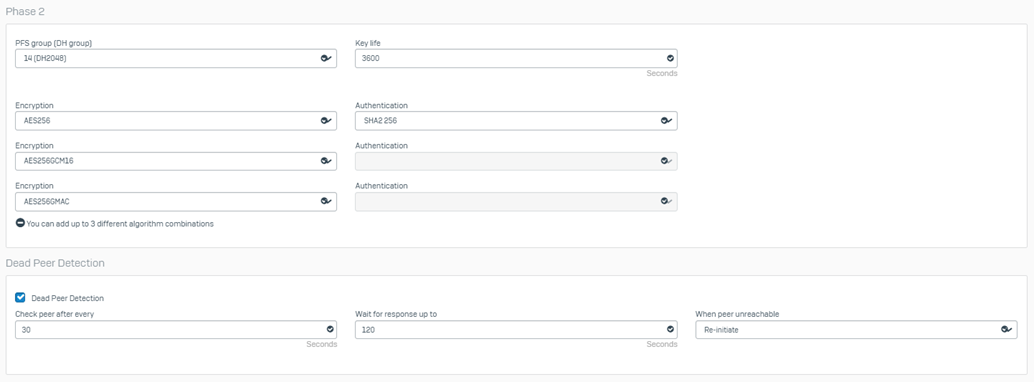
Phase 2
- pfs group: 14
- encryption: aes 256
- authentication: sha1
- keylife time: 3600
Note: Sophos will give a warning about using sha1.
Oracle Documentation states to use Sha1-96
Additional Encryption
Notes/Optional: Sometimes, vendors add support for additional encryption types before updating their documentation.
I've added a second set of encryption/Authentication to phase two settings, hoping this is the case with Oracle
- Aes256/sha2 256
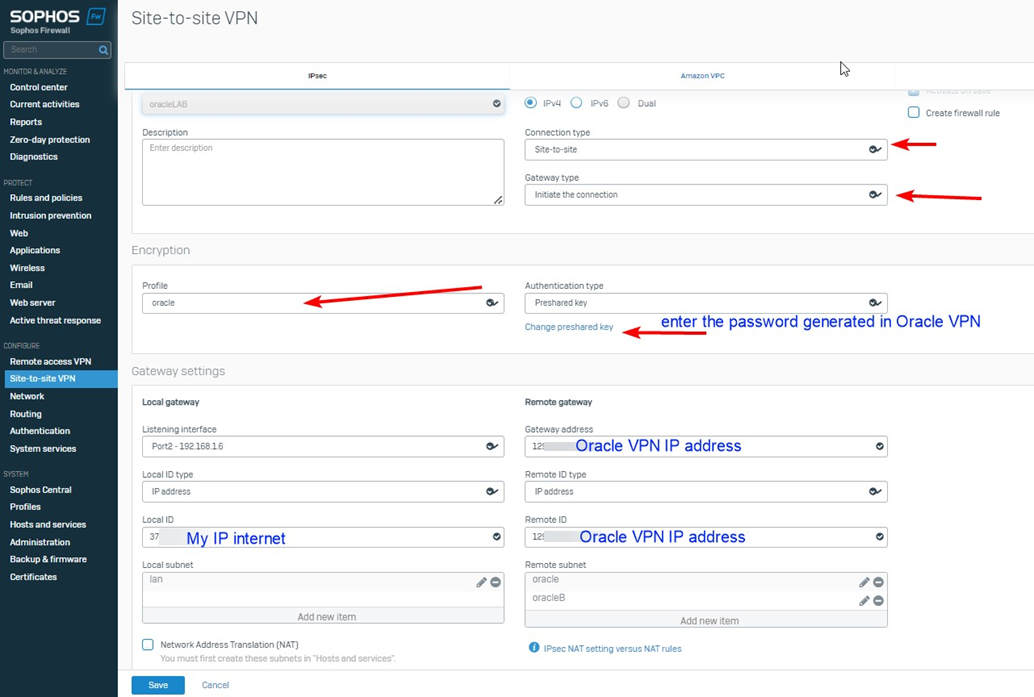
In Sophos Firewall, go to VPN> IPsec Connections
- Add new connection
- Type: site-to-site
- mode type: initiate
- Policy: the one created above
- Shared Secret: Defined for the primary tunnel
- Listening Interface: This should match the WAN IP, the Oracle CPE and IPsec IKE, CPE identifier configured to receive the tunnel from
- Gateway Address: WAN IP of the primary Oracle VPN
Note: If your Sophos WAN is behind NAT, You can use the "Local ID" to override the IP Address presented to the IKE identifier.
Local Networks
- Include any on-premises network.
Note: The following must match the "Static route CIDR" values entered upon creating the IPsec connection on CLI.
Remote Networks
- Any subnets within OCI that you desire to be reachable via tunnel
Click "Save" and then click the radio button to enable/activate the tunnel.
For Backup tunnel. The same configuration and setup will be needed. Create the backup IPsec connection on the Sophos Firewall and then proceed to the following steps:
- With the primary and backup tunnels in an off state, follow the steps in the Sophos KB to combine the tunnels into a failover group.
- Skip to the section: Create an IPSec VPN connection, Steps #3 to #7.
Updated Link
[edited by: Erick Jan at 2:53 AM (GMT -8) on 24 Dec 2024]
