Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This recommended read contains the troubleshooting steps & possible solutions when there’s an issue with OTP authentication, and AD users are getting locked after multiple failed attempts.
Background
As per the reported problem, SSL VPN Authentication for domain users (AD Users) with MFA(Multi-Factor Authentication) enabled on the Sophos firewall and account lockout threshold set on the AD Server gets blocked on 3rd wrong attempt even when the Threshold of wrong attempt set as five on the AD server.
We reproduced the issue locally as well with the below setup.
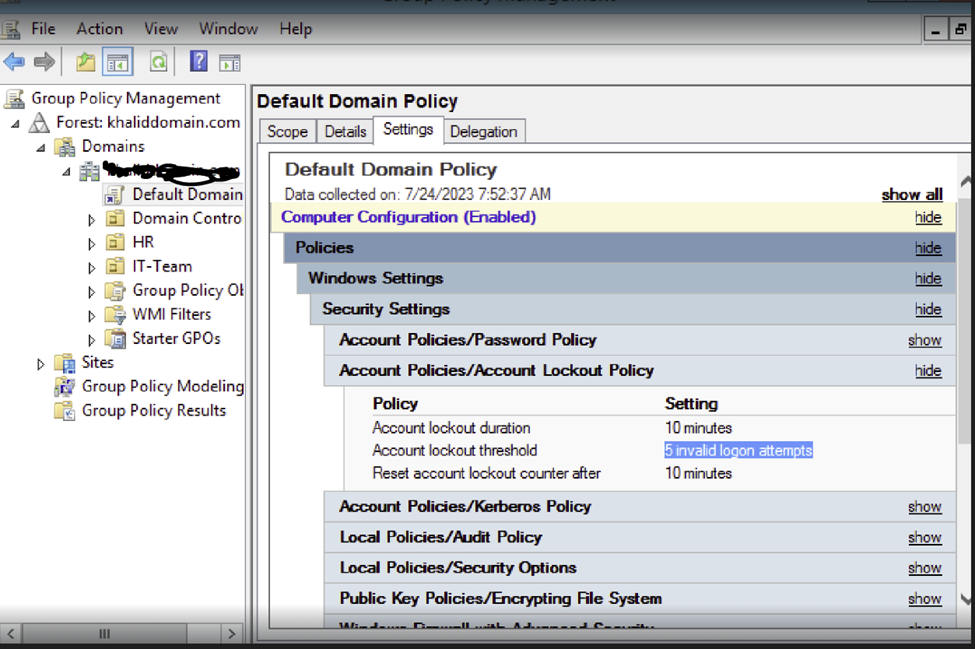
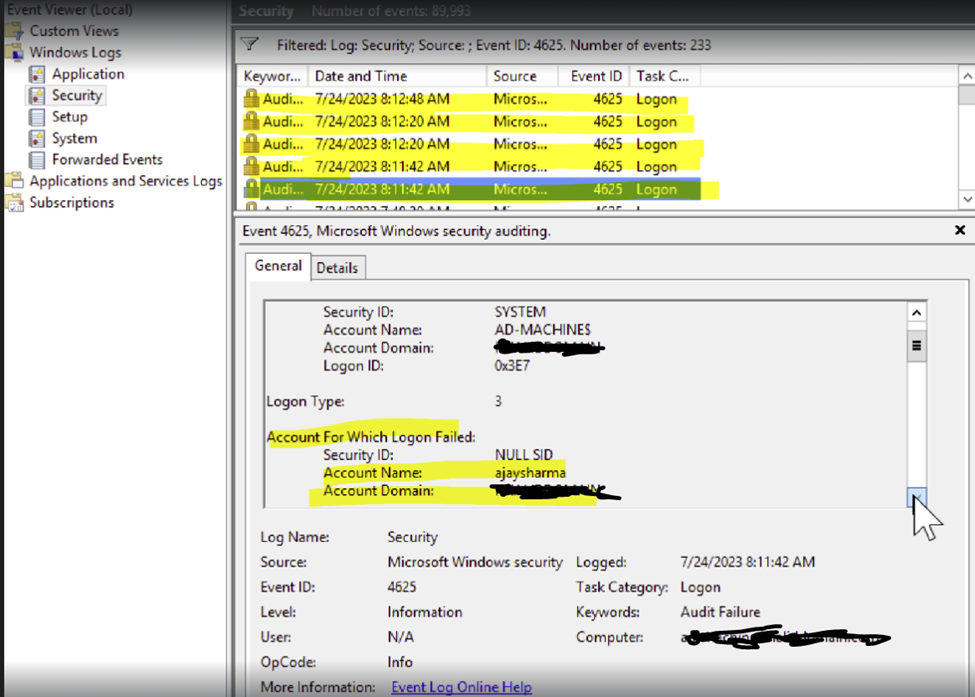
Domain user "ajaysharma" with MFA enabled on the firewall set the account threshold for the wrong attempt as five on the AD server and performed the incorrect attempt by trying to authenticate with the User Portal.
Configuration/Troubleshooting
Firewall user configuration setting:
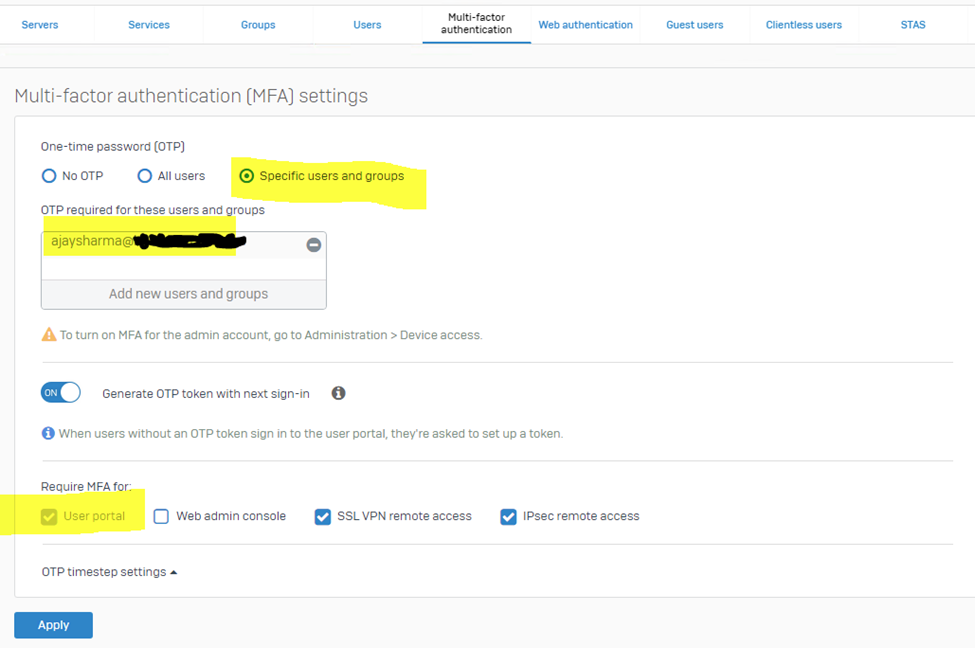
MFA settings on the firewall:
Active Directory Account locked threshold configuration:
An authentication request comes on the Sophos firewall whenever the authentication is triggered.
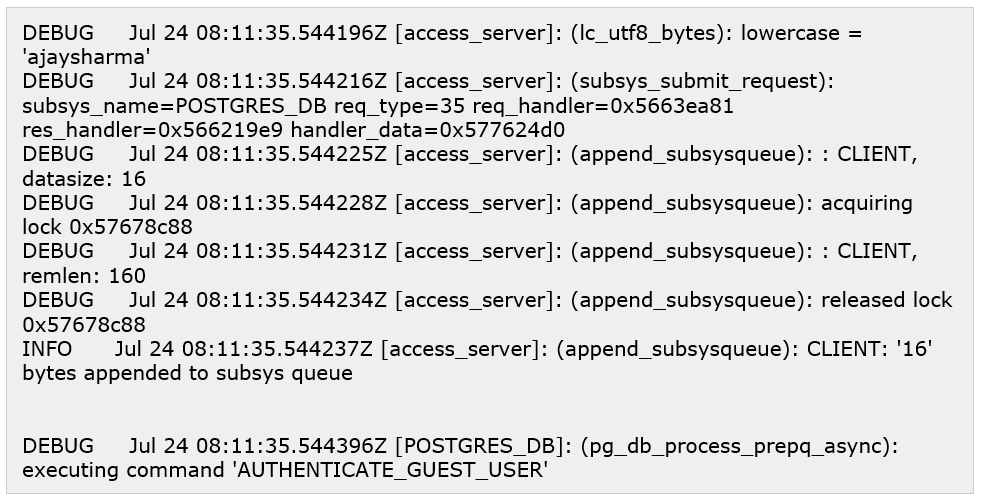
The Sophos Firewall will verify the user with a Short Password (i.e. User provided credential without the last six digits (last six digits we used for OTP verification)), and the AD server will reject the request since the entered credentials are incorrect. AD server logs this event as the 1st Logon Failure event in the Event Viewer Logs on the AD server.
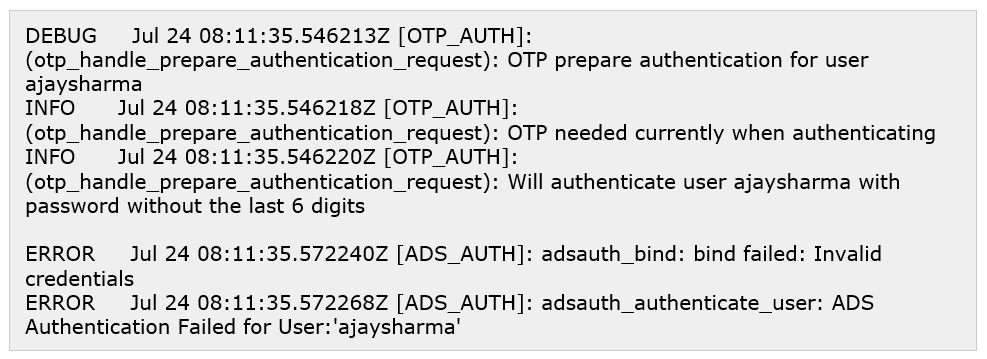
Now, the Sophos firewall will verify the user with the provided credentials and full Password (User-provided credential detail without any change) with the AD server. Firewall checks with Full Password verification are required in some cases with MFA like users logging in for the first time or scanning QR codes. AD also rejects this verification since the credentials are incorrect, logging it as 2nd Logon Failure (Incorrect Attempt) in the Event Viewer on the server itself.
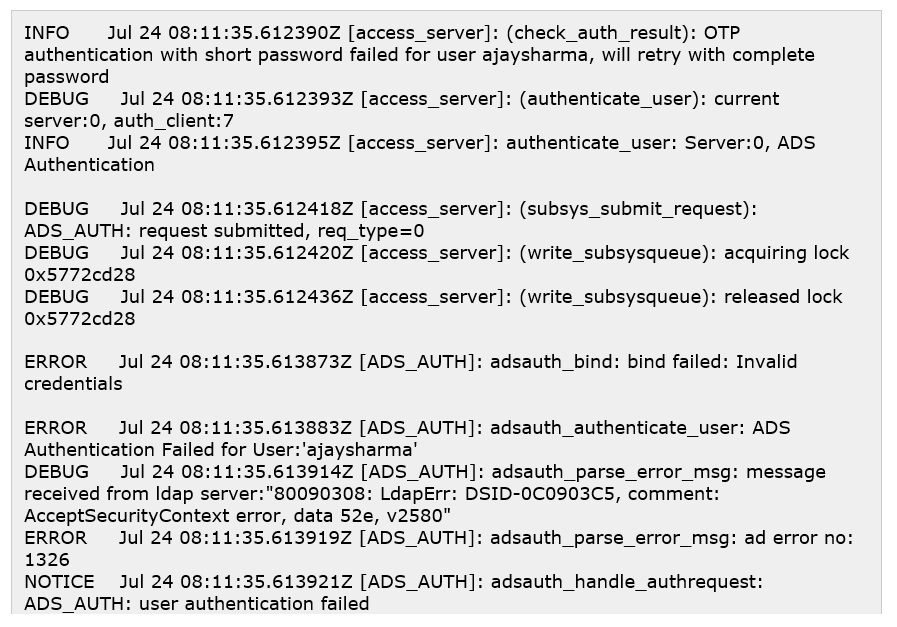
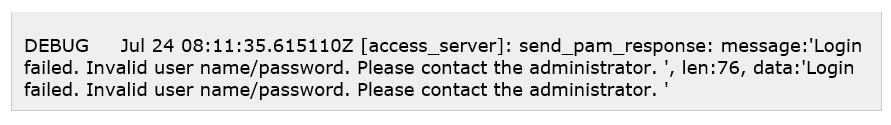
After the above verification, the First incorrect attempt shall be generated on the Sophos firewall.
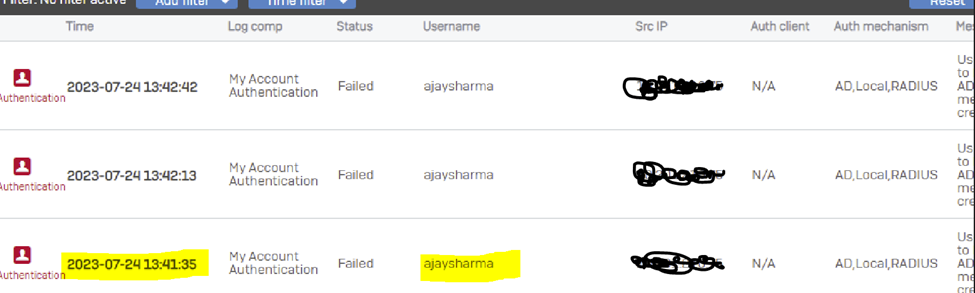
The AD server shows two logon failure attempt events for each login attempt, due to which, by the 3rd attempt, five logon failure events are generated. As the account lockout policy configuration is on the AD server, it blocks the user account on the 3rd attempt. So, this is expected behavior.
Workaround/Suggestion:
Alternatively, you can increase the account lockout threshold on the AD server (For Example, 10 or 12) per the requirement.
Added TAG
[edited by: Erick Jan at 4:17 AM (GMT -7) on 14 Oct 2024]
