Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended Read describes the configuration steps for Remote Access SSL VPN on Sophos Firewall when it is behind a NAT device.
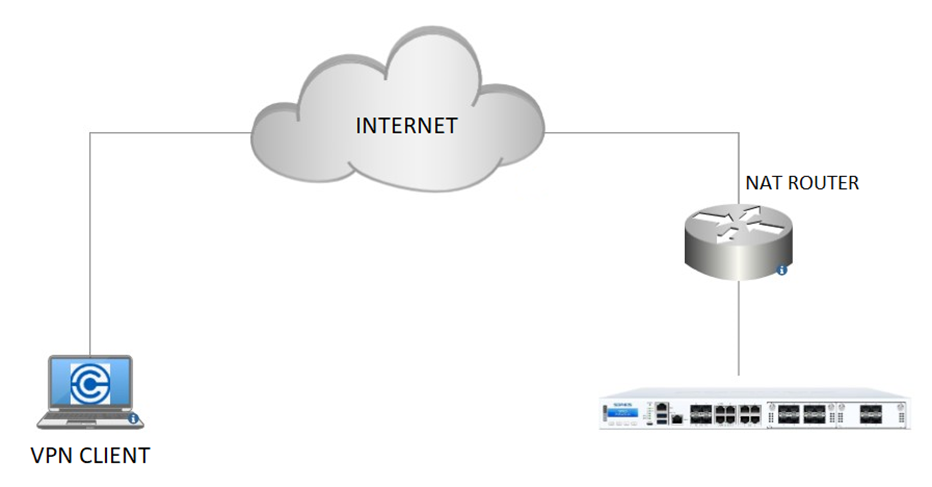
Requirements
- For this configuration to be achieved, you must have configuration access to the NAT device/router, or you can request your ISP to make the changes for you on a certain part of this guide. Otherwise, this would not be feasible.
- You should have other parts of the SSL configuration and setup followed, such as enabling it on WAN zone, allowed/permitted networks, etc., as detailed step-by-step in this document guide:
Configure SSL VPN Global Settings
In this setting on your Sophos Firewall, go to Remote access VPN > SSL VPN global settings > Override hostname. Then, you need to input the public-facing IP of the NAT router/device.
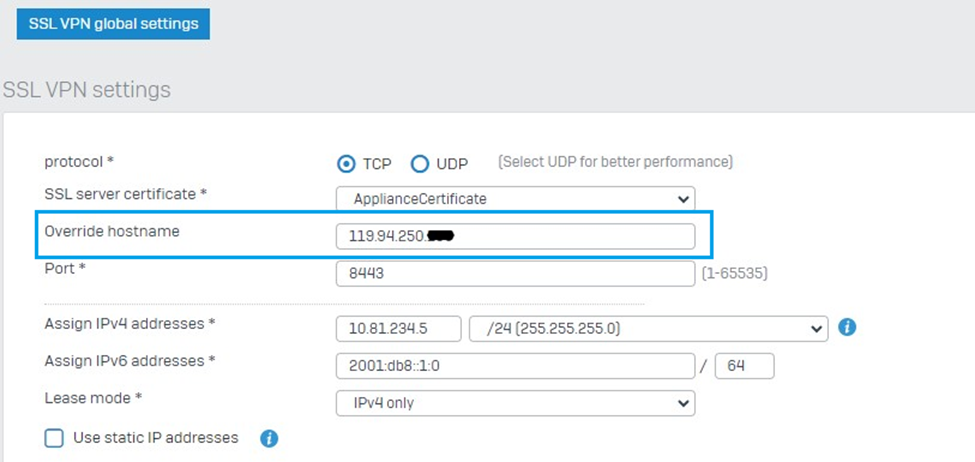
If the provided IP of the ISP is dynamic, you can use or opt for a DDNS in this configuration section. If you don’t have a DDNS and static Public IP on the ISP router, you must manually update the override hostname whenever the IP changes from the ISP side.
Using DDNS in the Override hostname section:
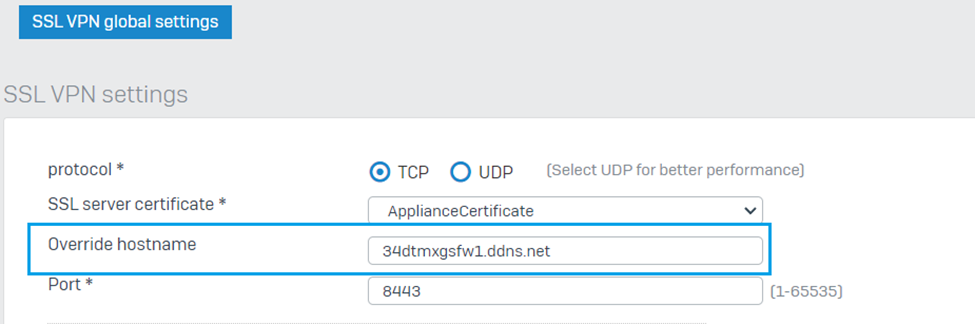
When you use DDNS in the Override hostname, You must also have a DDNS setting configured under Network > Dynamic DDNS
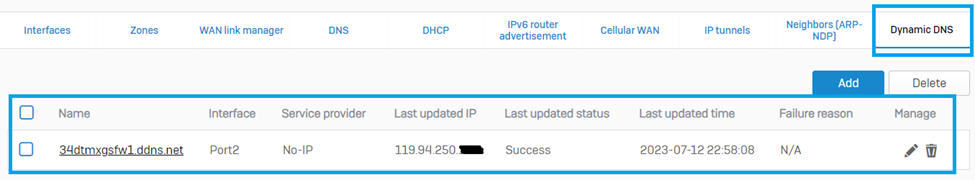
In the example, we’re using NO-IP as a DDNS provider. Note that only choose DDNS providers supported by SFOS to make this configuration work. Further, before using DDNS in the SSL VPN Override settings, the “Last Updated Status” must be “Success” here on this configuration section and you may also test externally to check that the hostname is publicly resolvable.
For more details on how to configure DDNS on Sophos Firewall, you may refer to this document guide:
After completing these settings, users must re-download and update the configuration file.
Configure Inbound NAT on the NAT Device/Router
In this section, you must have access to the router or be able to request configuration from the ISP. Configuration is an inbound NAT from the set Public IP or the Publicly resolvable hostname (DDNS) -> NATed / going to the Sophos Firewall with port 8443 (TCP or UDP)—it depends on the option you chose in the SSL VPN Global Settings and what port you use for SSL VPN.
Download the SSL VPN Client and Verify the .OVPN File
After the configuration for Sophos Firewall and NAT router has been done. Proceed to downloading and installing of the client and configuration file (.OVPN) > Then you may verify on the OVPN file if the Override configuration has taken effect. It should be able to contain something like "remote <public IP> 8443" where on public IP is your ISP's public IP.
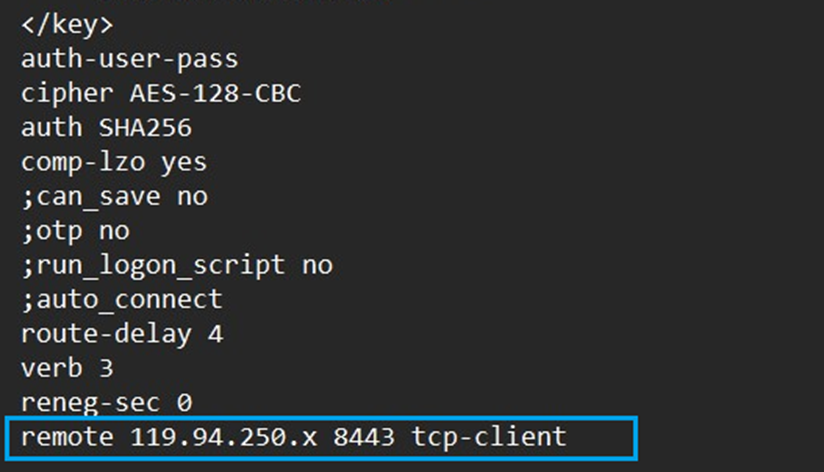
If you opt to use DDNS, you can also verify the settings in the .OVPN file
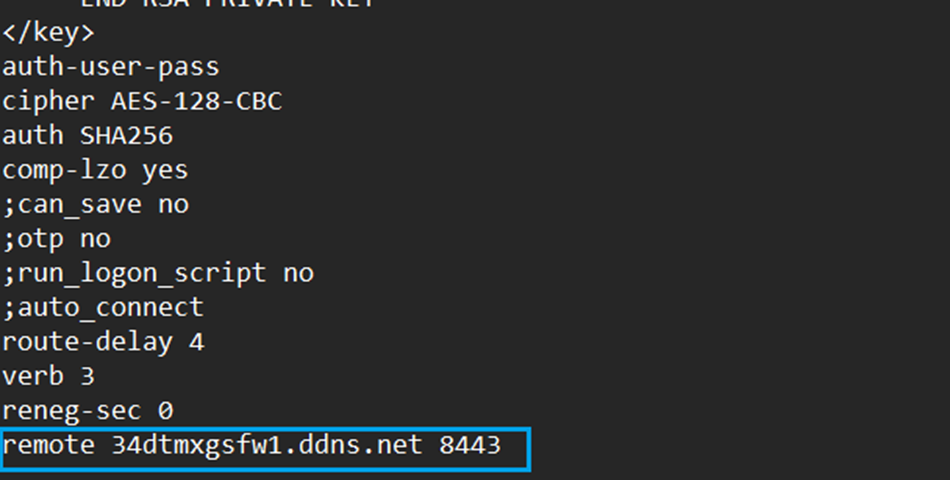
After this, the client should be able to establish connectivity with Sophos Firewall and on the permitted networks on your SSL VPN configuration.
Related Information
Doc guide: How to Configure SSL VPN on Sophos Firewall: https://docs.sophos.com/nsg/sophos-firewall/21.0/help/en-us/webhelp/onlinehelp/AdministratorHelp/RemoteAccessVPN/IPsecSSL/SophosConnect/index.html
Sophos Techvid: How to Configure SSL VPN on Sophos Firewall: https://techvids.sophos.com/watch/wtqMJE1La6TkFjAiaT2d3H
Updated links to latest
[edited by: Raphael Alganes at 11:11 AM (GMT -8) on 18 Dec 2024]
