Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
In some situations, we want to route traffic from an Appliance not over the internet but to another firewall and then to the internet. For this use case, SD-WAN Routes were created. We can use the same approach to route all traffic a firewall generates to another firewall. In this recommended read, we’ll reroute the traffic of CFR(Central Firewall Reporting) to another firewall.
How it works
We’ll use two Firewalls and an existing XFRM Tunnel (Route Based VPN). You can use MPLS as well; it’s a similar approach. We’ll create an SD-WAN Route for the specific traffic on both firewalls and allow the traffic with a matching Firewall Rule.
Central Datacenter
CFR uses the data center you choose when creating the data center. You’ll find your Sophos Central Datacenter here
CFR uses the same data center but in S3.
Sophos has different URLs for each Datacenter:
- tf-pre-signed-url-eu-central-1-prod-firewall-bucket.s3.eu-central-1.amazonaws.com
- tf-pre-signed-url-eu-west-1-prod-firewall-bucket.s3.eu-west-1.amazonaws.com
- tf-pre-signed-url-us-west-2-prod-firewall-bucket.s3.us-west-2.amazonaws.com
- tf-pre-signed-url-us-east-2-prod-firewall-bucket.s3.us-east-2.amazonaws.com
- tf-pre-signed-url-ap-south-1-prod-firewall-bucket.s3.ap-south-1.amazonaws.com
- tf-pre-signed-url-ap-northeast-1-prod-firewall-bucket.s3.ap-northeast-1.amazonaws.com
- tf-pre-signed-url-ca-central-1-prod-firewall-bucket.s3.ca-central-1.amazonaws.com
- tf-pre-signed-url-sa-east-1-prod-firewall-bucket.s3.sa-east-1.amazonaws.com
- tf-pre-signed-url-ap-southeast-2-prod-firewall-bucket.s3.ap-southeast-2.amazonaws.com
In our example, we’re working with the Frankfurt/Germany data center, EU-Central-1.
SD-WAN Rule
Our first step is to change the SD-WAN Route on the Device. We want to reroute Traffic to the tunnel.
The rule is quite simple. We’re using SD-WAN Routes to route everything into a Gateway Route:
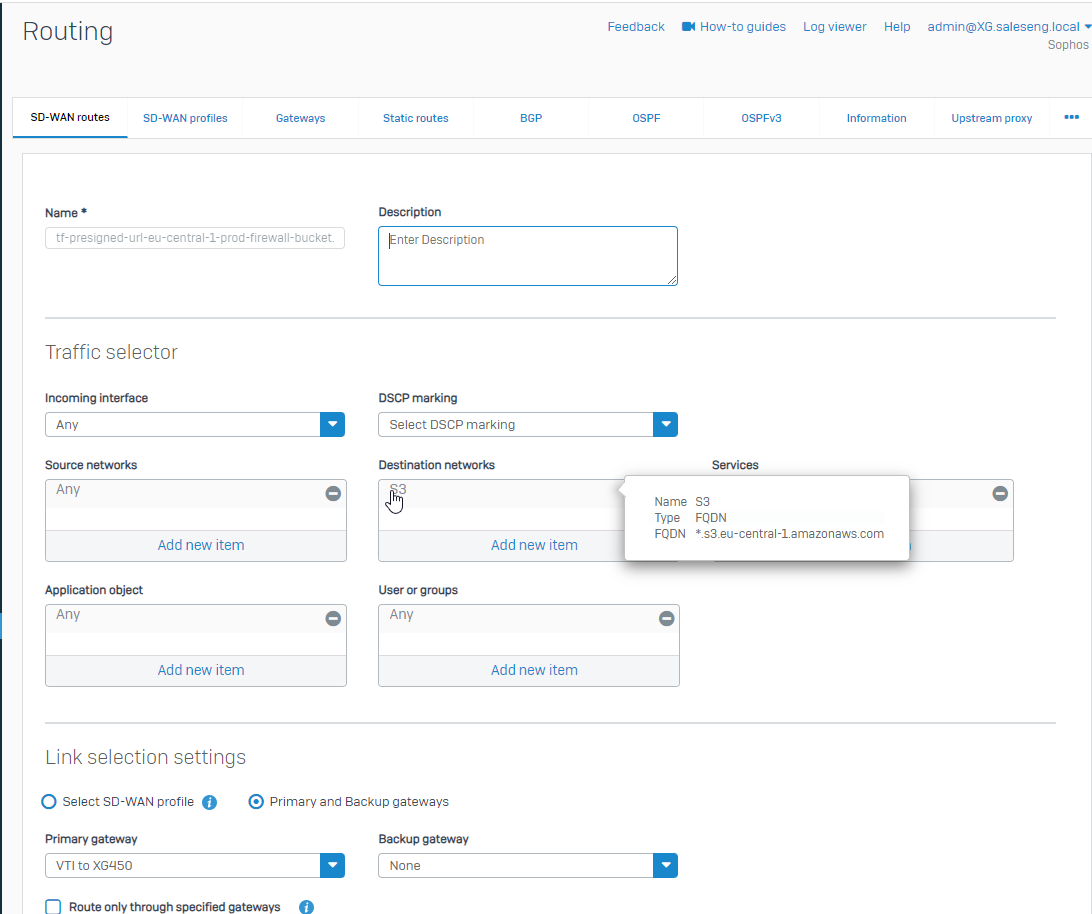
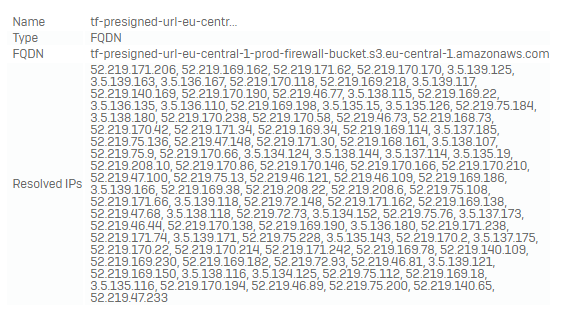
We’re working with a Wildcard; you can create an object like the one above.
Firewall Rule
On the other Firewall, we need to allow this Traffic to flow to WAN. In this example, a simple VPN to WAN Rule. You can/must adjust this to your needs. You can also create the same objects. 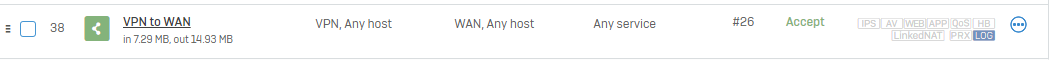
SD-WAN CLI Configs
Two different CLI Configs could affect your success: Reply Packets and System-Generated Traffic.
First: Reply Packets, which means if the packet on the second firewall comes back, it needs its route or uses the route back.
Second: System-Generated Traffic, meaning the SD-WAN Routes will be considered for Traffic generated by SFOS (which we want in this case).
Revamped RR
[edited by: Erick Jan at 9:26 AM (GMT -7) on 18 Sep 2024]
