Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This recommended read contains the steps to configure a Site-to-site IPsec VPN connection between Sophos Firewall and Sophos UTM using a preshared key as an authentication method for VPN peers.
Product and Environment
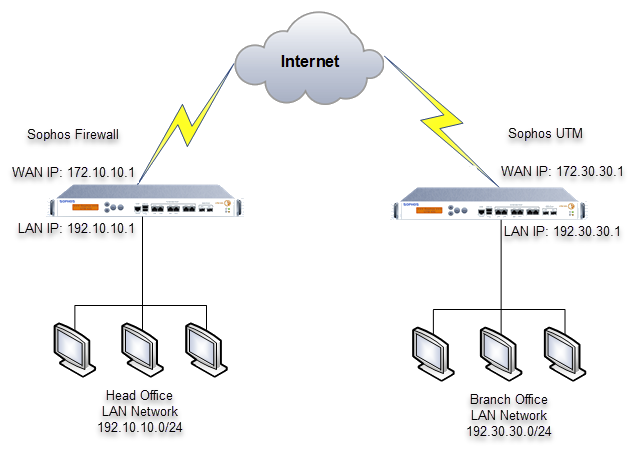
Sophos Firewall
Network diagram
Configuring Sophos Firewall
Adding local and remote LAN
- Go to Hosts and Services> IP host and select Add to create the local LAN as follows:
Setting Value Name XG_LANIP version IPv4 Type Network IP address 192.10.10.0Subnet /24 (255.255.255.0) - Click Save.
- Go to Hosts and Services> IP host and select Add to create the remote LAN as follows:
Setting Value Name SG_LANIP version IPv4 Type Network IP address 192.30.30.0Subnet /24 (255.255.255.0) - Click Save.
Creating an IPsec profile
- Go to Profiles > IPsec profiles and select Add.
- Configure as follows:
Note: The policies indicated here are just for illustration purposes. The administrator can choose a more secure policy according to their requirements.
Setting Value General settings Name XG_to_SGKey exchange IKEv1 Authentication mode Main mode Key negotiation tries 3Re-key connection Turned on Pass data in compressed format Turned off SHA2 with 96-bit truncation Turned off Phase 1 Key life 28800Re-key margin 120Randomize re-keying margin by 0DH group (key group) 14 (DH2048) Encryption AES256 Authentication SHA256 Phase 2 PFS group (DH group) Same as phase-I Key life 3600Encryption AES256 Authentication SHA256 Dead Peer Detection Dead Peer Detection Turned off - Click Save.
Creating an IPsec VPN connection
- Go to Site-to-site VPN > IPsec.
- Under IPsec connections, click Add.
- Configure as follows:
Setting Value General settings Name XG_to_SGIP version IPv4 Connection type Site-to-site Gateway type Respond only Activate on save Turned on Create firewall rule Turned off Encryption Profile XG_to_SGAuthentication type Preshared key Preshared key Enter a pre-shared key. Repeat preshared key Repeat the preshared key. Gateway settings Listening interface Port2 - 172.10.10.1Local subnet XG_LANGateway address 172.30.30.1Remote subnet SG_LAN - Click Save.
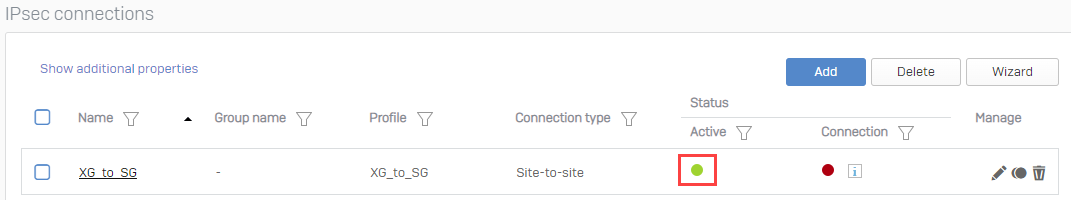
- You should see that the IPsec connection is activated, as shown below. You can also activate it manually by clicking the icon under the Active column.
Add two firewall rules allowing VPN traffic
- Go to Rules and Policies> Firewall rules and select Ipv4.
- Click Add firewall rule > New firewall rule.
- Configure two firewall rules as follows:
Setting Firewall rule 1 Firewall rule 2 Rule name Outbound_VPN_TrafficInbound_VPN_TrafficAction Accept Accept Rule position Top Top Rule Group None None Log firewall traffic Turned on Turned on Source zones LAN VPN Source networks and devices XG_LANSG_LANDuring scheduled time All the time All the time Destination zones VPN LAN Destination networks SG_LANXG_LANServices Any Any - Click Save on both firewall rules.
Configure device access
- Go to Administration > Device access.
- Under the IPsec column, select WAN.

- Click Apply.
Configuring Sophos UTM
Add network definitions
- Go to Definitions & Users > Network Definitions.
- Select Network Definitions and click New Network Definition.
- Configure as follows:
Setting Value Name SG_LANType Network IPv4 address 192.30.30.0Netmask /24 (255.255.255.0) - Click Save.
- Create another network definition as follows:
Setting Value Name XG_LANType Network IPv4 address 192.10.10.0Netmask /24 (255.255.255.0) - Click Save.
- Create another network definition as follows:
Setting Value Name Sophos_Firewall Type Host IPv4 address 172.10.10.1 - Click Save.
Creating an IPsec VPN connection
- Go to Site-to-site VPN > IPsec > Policies and click New IPsec Policy.
- Configure as follows:
Note: Ensure that the settings match the custom policy on Sophos Firewall. The policies indicated here are just for illustration purposes. The administrator can choose a more secure policy according to their requirements.
Setting Value Name SG_to_XGIKE encryption algorithm AES 256 IKE authentication algorithm SHA2 256 IKE SA lifetime 28800 IKE DH group Group 14: MODP 2048 IPsec encryption algorithm AES 256 IPsec authentication algorithm SHA2 256 IPsec SA lifetime 3600 IPsec PFS group Group 14: MODP 2048 Strict policy Turned off Compression Turned off - Click Save.
- Go to Site-to-site VPN > IPsec > Remote Gateways and click New Remote Gateway.
- Configure as follows:
Setting Value Name IPsec_to_XGGateway type Initiate connection Gateway Sophos_FirewallAuthentication type Preshared key Key Enter a pre-shared key.
Note: Ensure to use the same preshared key configured on Sophos Firewall.
Repeat Repeat the preshared key. VPN ID type IP address Remote networks XG_LAN - Click Save.
- Go to Site-to-site VPN > IPsec > Connections and click New IPsec Connection.
- Configure as follows:
Setting Value Name SG_to_XGRemote gateway IPsec_to_XGLocal interface External (WAN) Policy SG_to_XGLocal Networks SG_LANAutomatic firewall rules Turned on Strict routing Turned off Bind tunnel to local interface Turned off - Click Save.
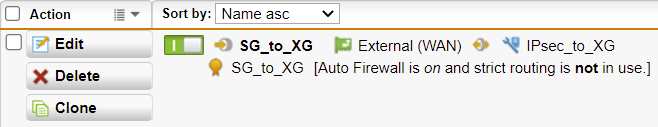
- You should see the following IPsec connection. Ensure to turn on the connection.
Establishing the IPsec connection
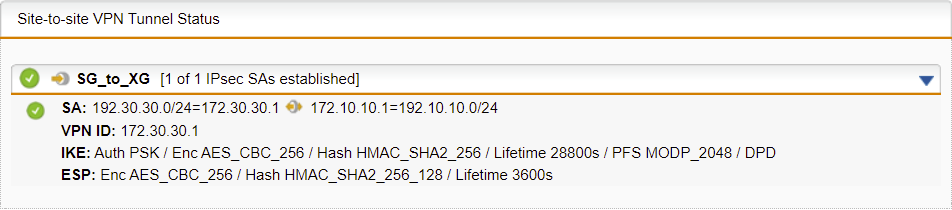
The IPsec connection should be established automatically. From Sophos UTM, verify that IPsec SA is established in Site-to-site VPN.
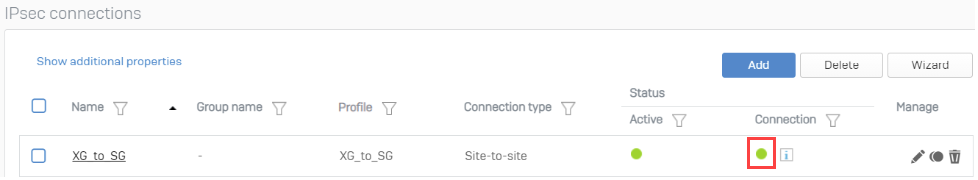
From Sophos Firewall, verify the connection in VPN > IPsec connections. The icon under the Connection column should be green.
Result
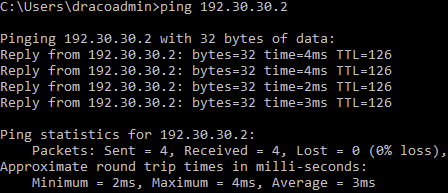
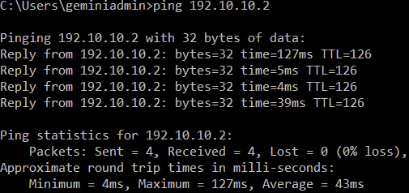
A ping test must work from a device behind Sophos Firewall to a device behind Sophos UTM and vice versa.
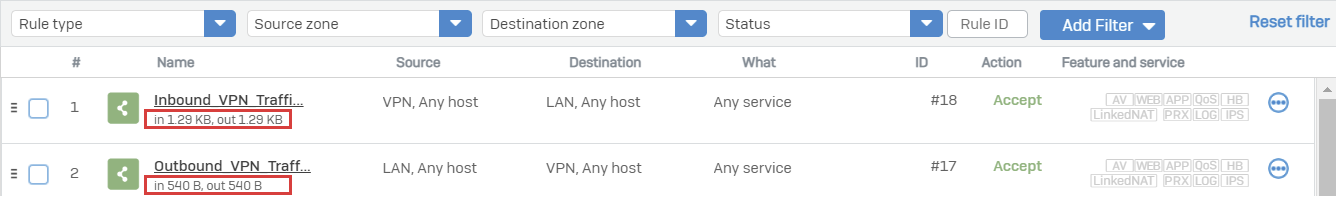
From Sophos Firewall, go to Rules and Policies> Firewall rules and verify that the VPN rules allow ingress and egress traffic.
View the existing connections in Current activities > IPsec connections.
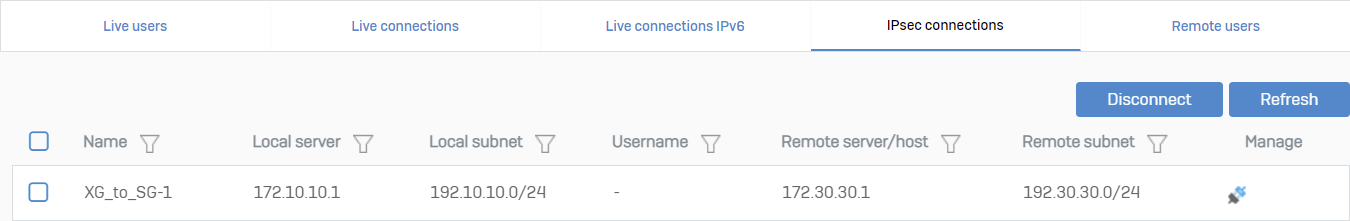
Verify the IPsec usage in Reports > VPN.
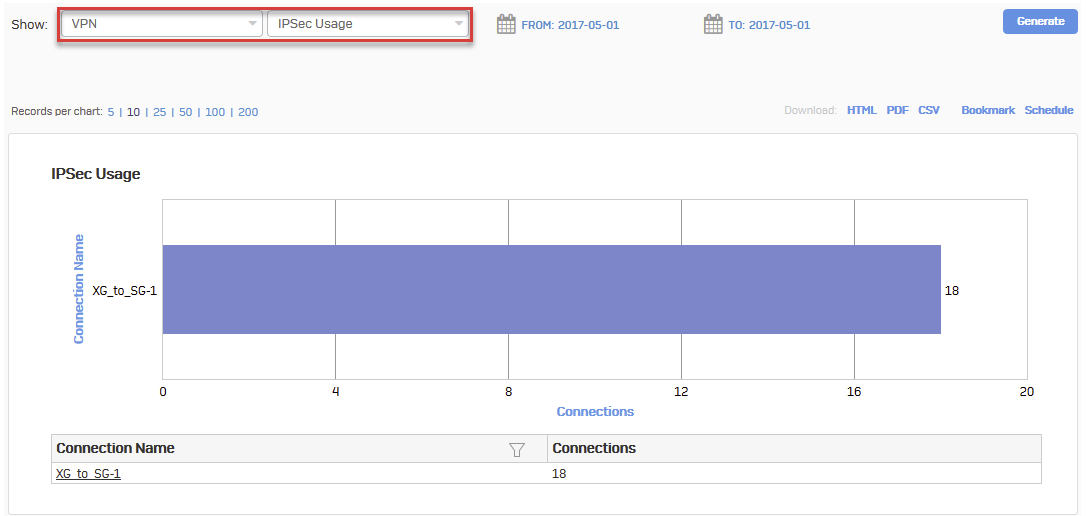
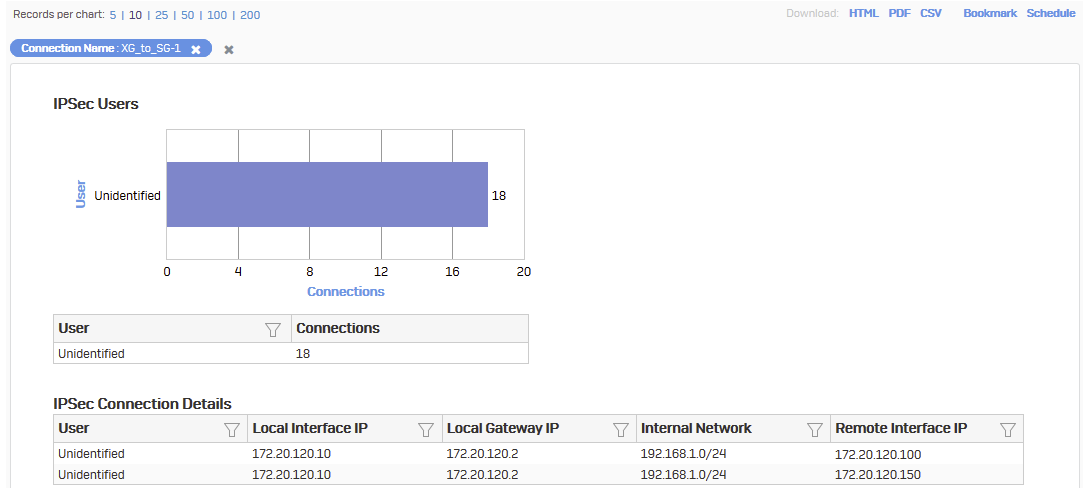
Click the connection name for details.
Note:
- Sophos UTM does not support IKEv2.
- Ensure that VPN firewall rules are on top of the firewall rule list.
- In a head and branch office configuration, Sophos Firewall on the branch office usually acts as the tunnel initiator, and Sophos Firewall on the head office acts as a responder due to the following reasons:
- The head office device cannot start the connection if the branch office device is configured with a dynamic IP address.
- As the number varies for the branch offices, it is recommended that each branch office retries the connection instead of the head office retrying all connections to the branch offices.
Related information
- Sophos Firewall: How to establish a Site-to-Site IPsec VPN connection using RSA Keys
- Sophos Firewall: Create a policy-based IPsec VPN connection using preshared key
- Sophos Firewall: How to change firewall rule order
Added TAG
[edited by: Erick Jan at 5:56 AM (GMT -7) on 28 Oct 2024]


