Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended Read describes the process and configuration required to build a VPN tunnel between a Sophos Firewall and an AWS VPN gateway using interface-based tunnels and BGP for dynamic route exchange.
As a pre-requisite, you must have a working environment on AWS, with ports allowed for communication going in and out of AWS (Network ACLs, Security Groups, and so on)
Configure the Amazon Side
A) Create a Customer Gateway
1. Navigate to VPC > Virtual Private Network (VPN) > Customer Gateways
2. Click Create Customer Gateway
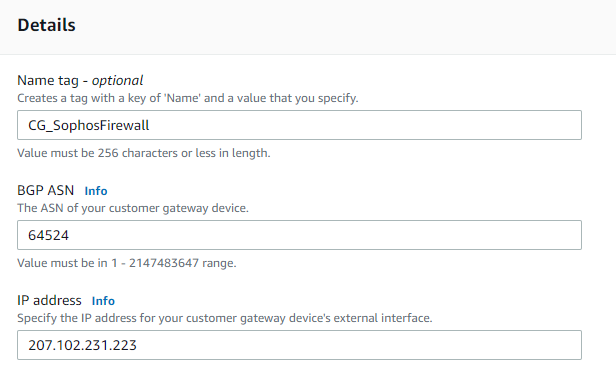
3. Enter a meaningful name (e.g. CG_SophosFirewall)
4. BGP ASN = Enter a private ASN in the range of 645212 -65,534 (e.g. 64524)
5. IP address = Type the Public IP of the Sophos Firewall
B) Create a Virtual Private Gateway
1. Click Virtual Private Gateways
2. Go to > Create Virtual Private Gateway
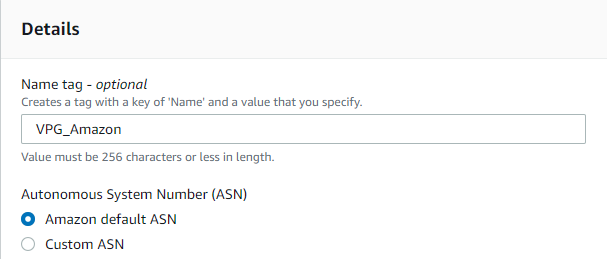
3. Enter a meaningful name (e.g. VPG_Amazon)
4. Autonomous System Number (ASN) = Amazon default ASN
5. Click Create Virtual Private Gateway
6. Once the VPG is created, select it and click Attach to VPN
7. Available VPC = Select your VPC
8. Click Attach to Virtual Private Gateway
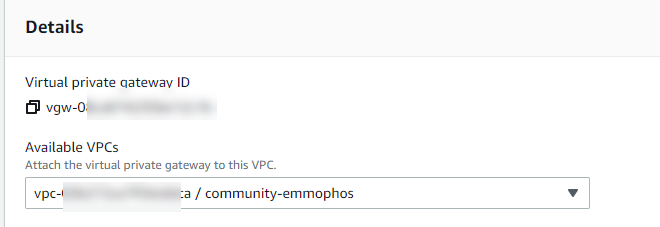
9. After a few seconds, it should show like this:
![]()
C) Create a Site-to-Site VPN Connection
1. Go to Site-to-Site VPN Connections > Create VPN connection
2. Name TAG = Enter a meaningful name (E.g AWS_TO_Sophos)
3. Target Gateway Type = Virtual Private Gateway
Virtual Private Gateway = Select the VPG created in Step 2
4. Customer Gateway = Existing
Customer Gateway ID = Select the CG we created in Step 1
5. Routing Options = Dynamic
Local IPv4 network CIDR - Optional (No need to add, but if you want, you can add 0.0.0.0/0)
Remote IPv4 network CIDR - Optional (No need to add, but if you want, you can add 0.0.0.0/0)
6. Tunnel 1 Options
Inside IPv4 CIDR for tunnel 1 = Enter a size /30 CIDR from 169.254.0.0/16 (e.g. 169.254.
Pre-Shared Key for tunnel 1 = Type your own or leave it blank, and AWS will create one automatically.
Advanced Options for Tunnel 1 = Select Edit Tunnel 1 option
Note: What you select here must match the IPsec Policy to be created in the Sophos Firewall for simplicity. I am only selecting one option for simplicity for each entry (this isn’t best practice, and you should match them according to your Company Policies, and Security levels)
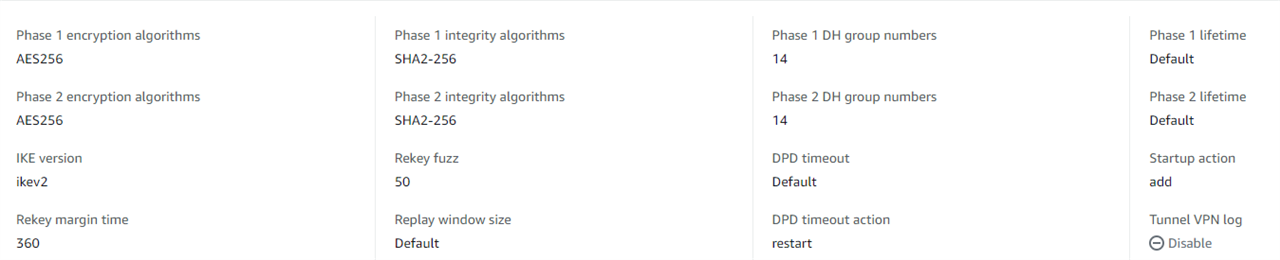
Phase 1 encryption algorithms = AES256
Phase 2 encryption algorithms = AES256
Phase 1 integrity algorithms = SHA256
Phase 2 integrity algorithms= SHA256
Phase 1 DH group numbers = 14
Phase 2 DH group numbers = 14
IKE Version = 2
Phase 1 lifetime (seconds) = 28,800
Phase 2 lifetime (seconds) = 3,600
Rekey margin time (seconds) = 360
Rekey margin time (seconds) = 50
DPD timeout action = Restart
(Note: You can repeat the same process for Tunnel 2.)
7. Click Create VPN Connection
8. Click Download Configuration > Vendor = Generic, Platform = Generic, Software = Vendor Agnostic, IKE Version = iKev2
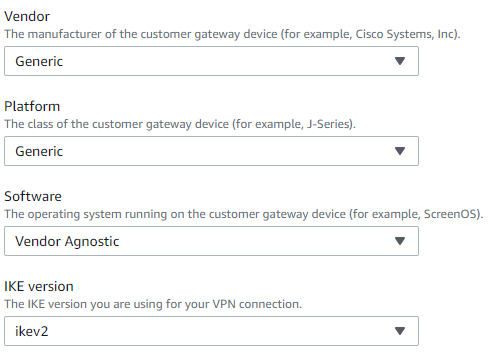
(Note: You will also find a Sophos as a Vendor, but this will download a File that is meant to be used within the Sophos Firewall when choosing Amazon VPC.)
Configure Sophos Firewall
A) IPsec Profiles
1. Open a browser and browse to your Sophos Firewall
2. Log in to the WebAdmin interface and go to Site-to-Site VPN > IPsec > IPsec Profiles
3. Click Add
General Settings
- Name = Ikev2_AWS
- Key exchange = IKEv2
- Key negotiation tries= 0
- Re-key connection.= Check
Phase 1
- Key life = 28800 seconds
- Re-key margin = 360
- Randomize re-keying margin by = 50
- DH group = 14 (DH2048)
- Encryption = 256
- Authentication = SHA2-256
Phase 2
- PFS Group (DH group) = 14 (DH2048)
- Key Life = 3600
- Encryption = AES256
- Authentication = SHA2-256
Dead Peer Detection
- Turn on dead peer detection by ticking the Dead Peer Detection checkbox.
- Check peer every = 30
- Wait for a response of up to 120 seconds.
- When peer unreachable = Re-initiate
4. Click Save
B) Site-to-Site VPN
1. Go to Configure > site-to-site VPN > IPsec > Add
General Settings
- Name = AWS
- IP version = Dual
- Connection Type = Tunnel interface
- Gateway Type = Respond Only
Encryption
- Profile = IKEv2
- Authentication Type = Preshared Key
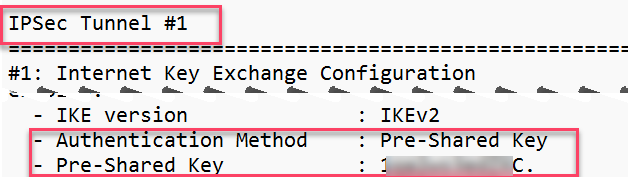
(If you enter a PSK on AWS, you would need to enter it here; if you let AWS auto-create the PSK, you would need to open the downloaded file and find "Pre-Shared Key.")
Gateway Settings
- Listening Interface = Your WAN port (must match the IP you entered in AWS when creating the Customer Gateway)
- Local ID Type = IP address
- Local ID = Enter a random IP or the Public IP of the Listening interface
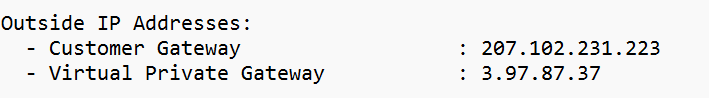
- Gateway Address = AWS Public IP (You will find this in the Downloaded File)
- Remote ID Type = IP address
- Remote ID = Enter a random IP or the Gateway Address of AWS (what I did)
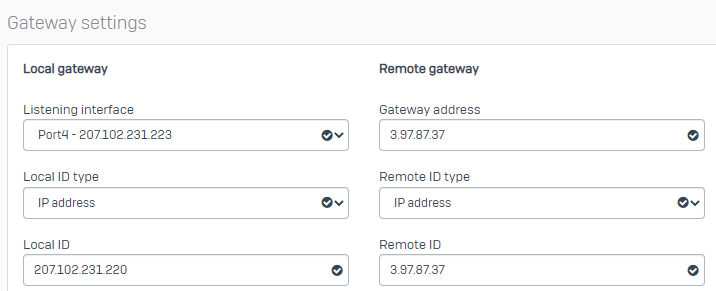
Note: You can't enter a Local and Remote Subnet. If an incorrect tunnel type is selected.
2. Save
This will create the tunnel, but it won't go UP until we turn on it
C) XFRM Interface
1. Go to Configure > Network > Interfaces, find the WAN interface used for the IPsec tunnel, and click the blue bar
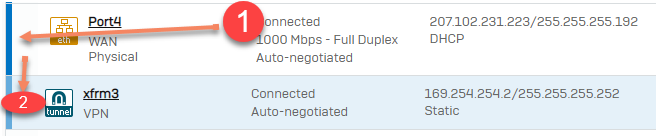
2. Click the xfrm interface
3. Tick the IPv4 Configuration
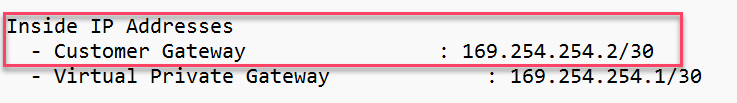
4. In IPv4/Netmask, enter the Inside IP Address - Customer Gateway (that you when downloaded the Configuration File from AWS)
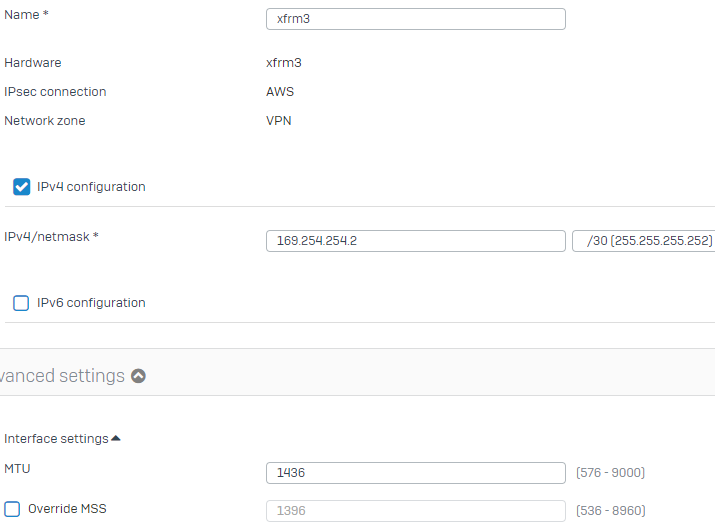
5. Change the MTU to 1436
6. Click save
D) Dynamic Routing
1. Go to Configure > Routing > BGP
Global Configurartion
- Routed ID assignment = Manual
- Router ID = any like IP (e.g. 172.16.1.100)
- Local AS = 64524
(Note: if you use BGP for other communications, change the AWS accordingly.)
Neighbors
- Neighbor = 169.254.254.1
- Remote AS = 64512
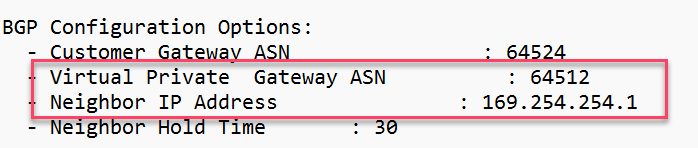
(this information is obtained from the Downloaded configuration file from AWS.)
Networks
- Network = Enter the Network(s) behind your Sophos Firewall you want to advertise to AWS via BGP (e.g. 172.16.2.0/24)
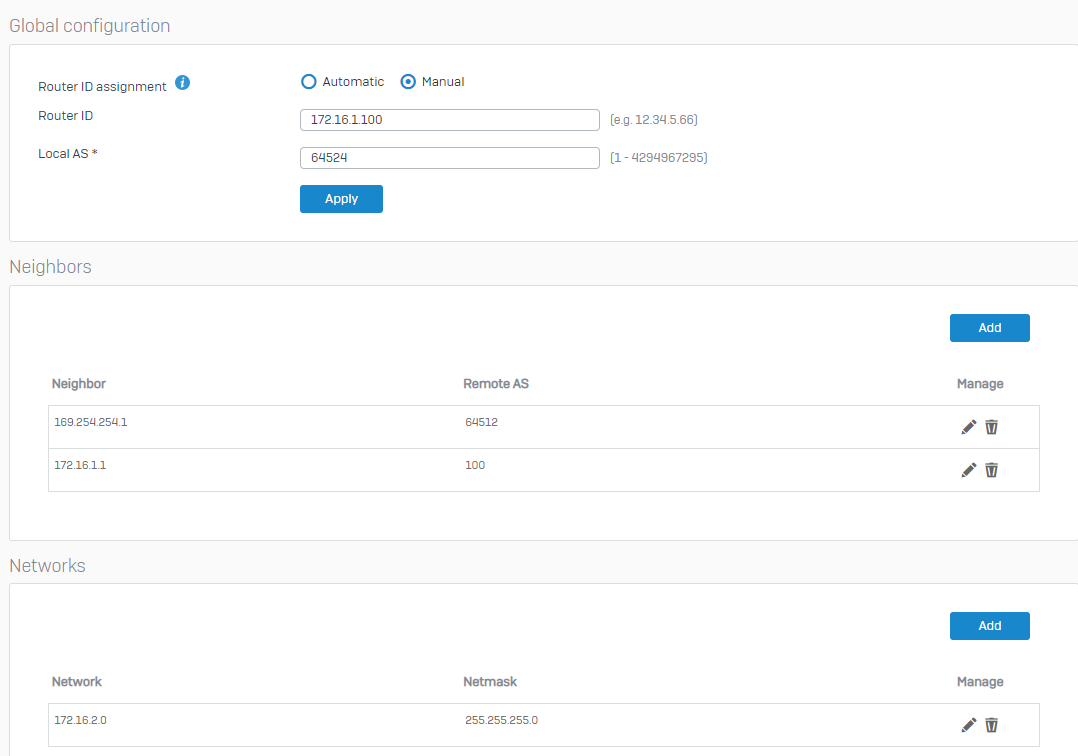
2. Apply
3. Go to System > Administration > Device Access > Local Service ACL
Dynamic Routing = VPN (Thick)
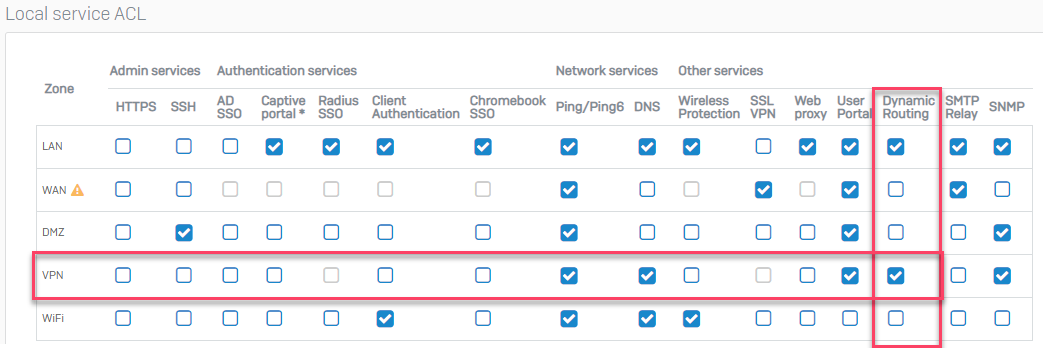
Note: I have LAN selected because I am running an additional neighbor on my LAN zone
4. Navigate to Configure > site-to-site VPN > IPsec
IPsec Connections
Identify the tunnel going to AWS, and click "Active" and "Connection."
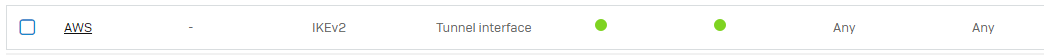
After some seconds, the dots should become green.
Firewall Rules
1. Go to > Protect > Rules And Policies > Firewall Rules > Add Firewall Rule > New Firewall Rule
- Rule Name = Sophos-to-AWS
- Action = Accept
- Rule Position = TOP
- Rule Group = None or Automatic VPN Rules
- Log Firewall Traffic = Tick
Source
- Source Zone = LAN, VPN
- Source Networks = Your Sophos Firewall and AWS networks
Destination and services
- Destination Zones = LAN, VPN
- Destination Networks = Your Sophos Firewall and AWS Networks
- Services = ANY (Recommended to narrow down to the services you’re going to be using; add BGP Port 179 if not selecting any)
2. Save
(Note: you can create two separate Firewall Rules, one for LAN to VPN traffic and the other one for VPN to LAN traffic. This would allow you more granular control and assist with any troubleshooting.
Confirm BGP is working.
On Sophos Firewall
To confirm BGP is working, you can go to
Configure > Routing > Information > BGP
Neighbors = Should have BGP state = Established (if it says Active, it means BGP isn’t forming)
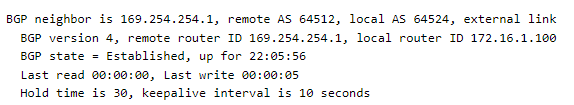
On AWS
1. Go to VPC > Virtual Private Network (VPN) > Site-to-site VPN Connections
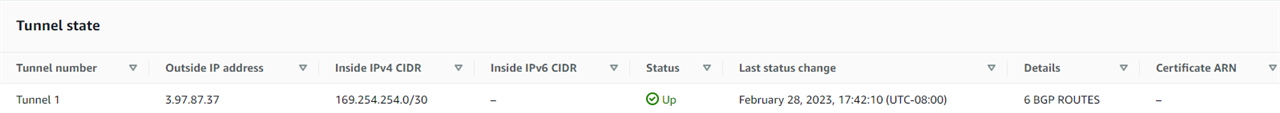
2. Click your VPN Connection > Tunnel Details
Tunnel state = Tunnel 1 Status = UP, Details BGP Routes
Troubleshooting
1. Check your AWS VPN is allowing the correct Subnets/Ports under the Security Groups
2. Check your AWS Route Table for the desired subnet to Route has Route Propagation enabled
3. Check your ASN numbers are within a Private ASN in both your Sophos Firewall and AWS
4. Check all Network ACLs involved have the correct inbound/outbound rules configured
5. Sometimes forcing the VPN Connection on AWS to use Local IPv4 and Remote IPv4 CIDR, will make BGP start working (this should be removed, though, once working)
6. On the Sophos Firewall, you can force traffic to go via the XFRM interface by creating a Static route and starting a Ping. This might also help to force BGP to initialize (should be removed, once working)
Note: The Sophos Firewall side of things is fairly easy to configure and troubleshoot, and for the nature of AWS, ( Route Tables, ACLs, Security Groups, and so on), issues are more prone to occur on that end of the tunnel, please reach out to AWS support to confirm if you need further assistance.
Added TAG
[edited by: Erick Jan at 2:54 AM (GMT -7) on 10 Oct 2024]
