Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended Read explains different packets dropped by Sophos Firewall and helps beginners find out the cause of packet drop.
Log Viewer
Packets dropped by the following security features are displayed in Log Viewer.
- Firewall,
- Web Filter,
- Application filter,
- IPS,
- Advanced threat protection
- SSL/TLS inspection
- Web server protection
Note: Log Viewer keeps a limited number of records. It’s recommended to check the Log Viewer occasionally before the record gets rotated.
Firewall (Invalid traffic)
To view packets dropped by the firewall, go to Sophos Firewall web admin> Log Viewer, and then choose logs of the Firewall in the drop-down menu.
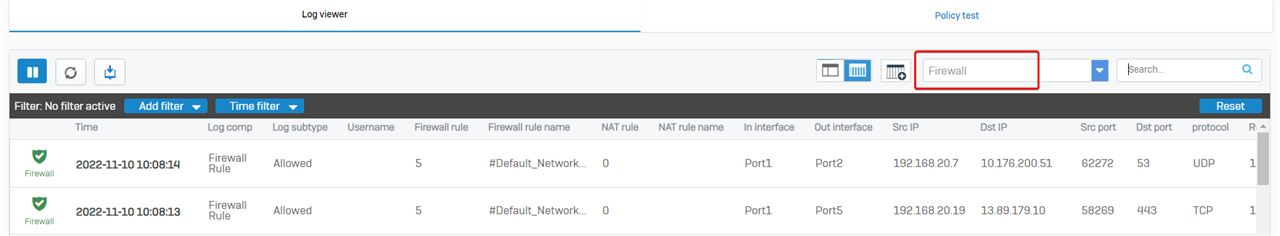
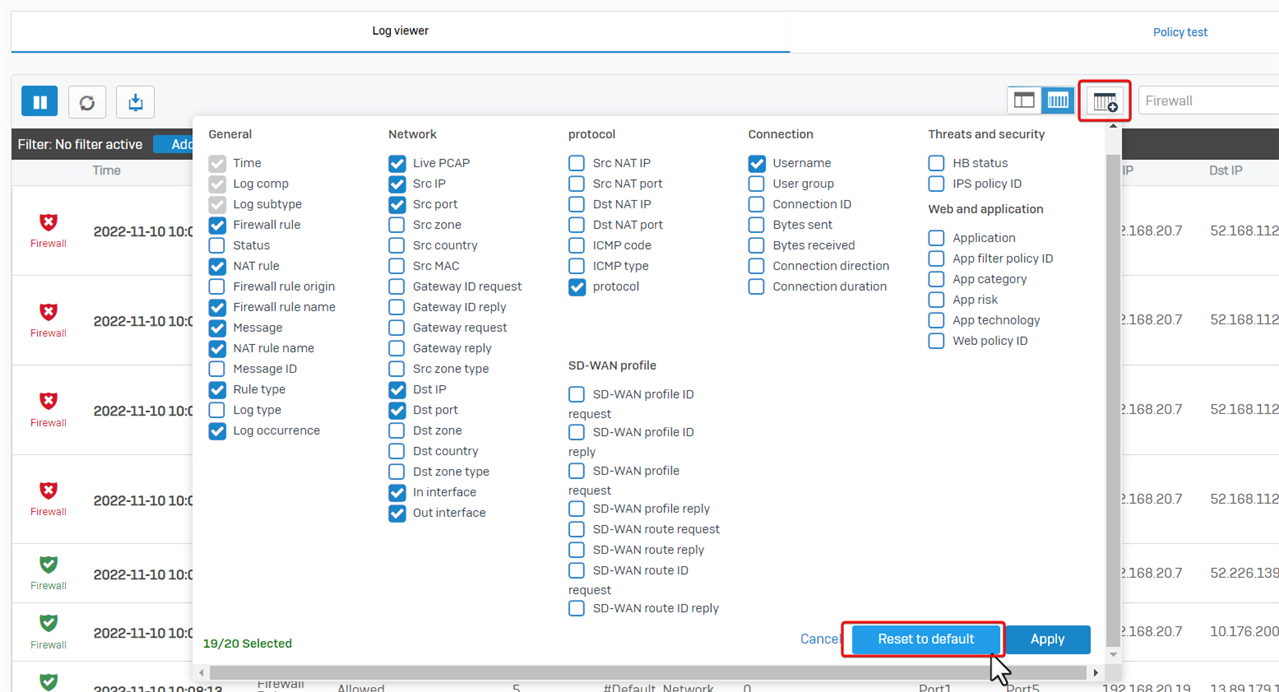
I recommended resetting the columns to make the Firewall page easy to read.
Click the "Add/remove columns" button, and then click "Reset to default."
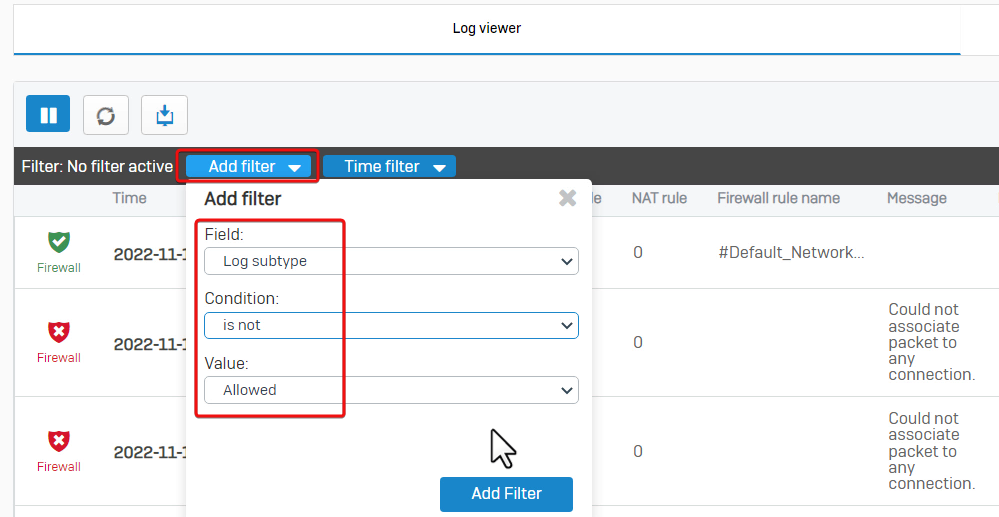
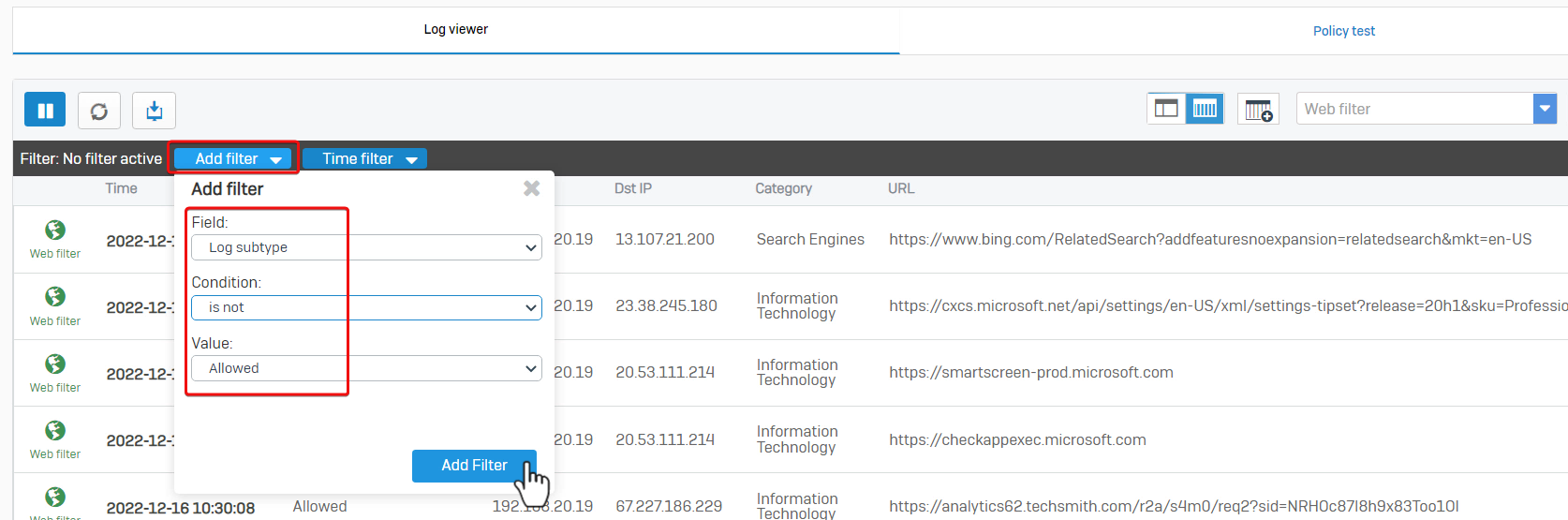
To Filter the dropped packet, click "Add filter", and set "Log subtype, isn’t and Allowed". See the screenshot below for reference.
Kindly note, that dropped packets marked with Invalid Traffic, Denied, firewall rule N/A isn’t a problem in most cases, so there’s no need to worry about them.
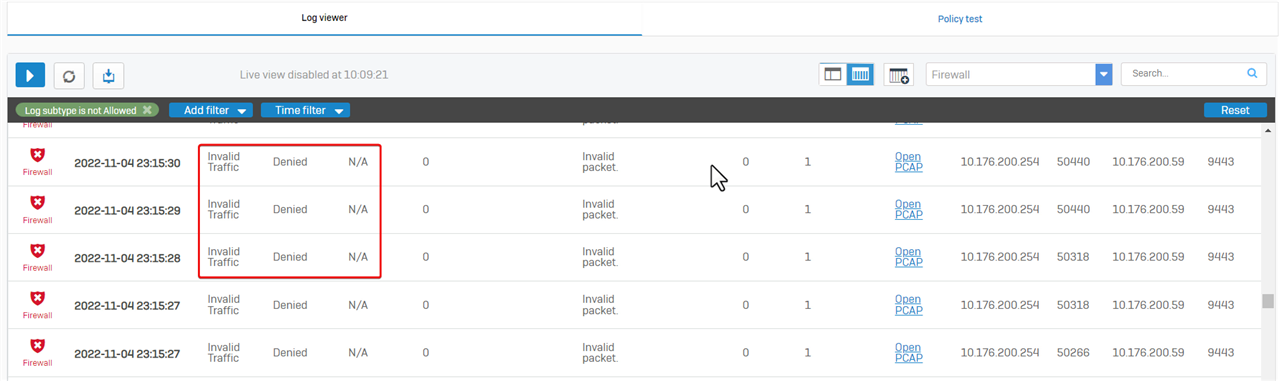
There are several types of Invalid Traffic.
- Invalid packet
The most common one is the "Invalid packet, " a TCP RST or TCP FIN packet. All stateful firewalls drop them to prevent TCP RST/FIN attacks.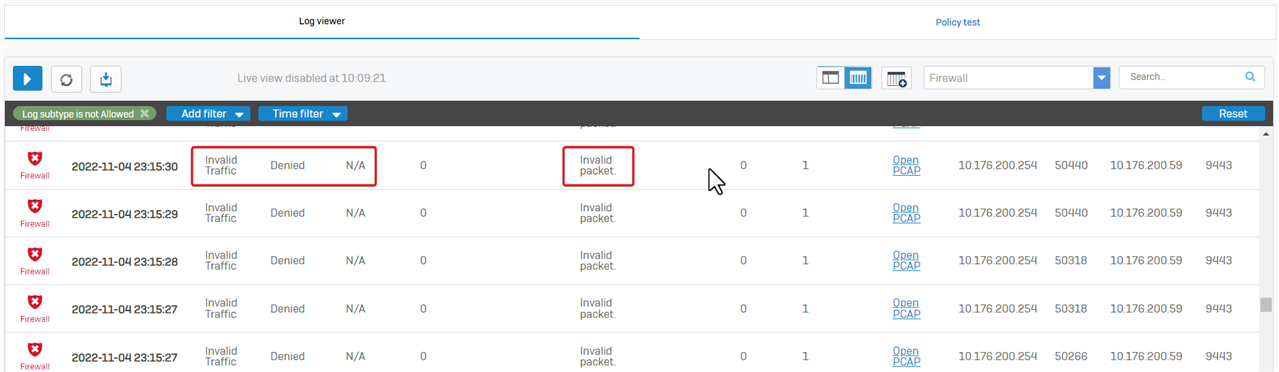
- Couldn’t associate the packet with any connection
Another type is "Could not associate packet to any connection", which refers to a dropped packet that does not belong to a connection.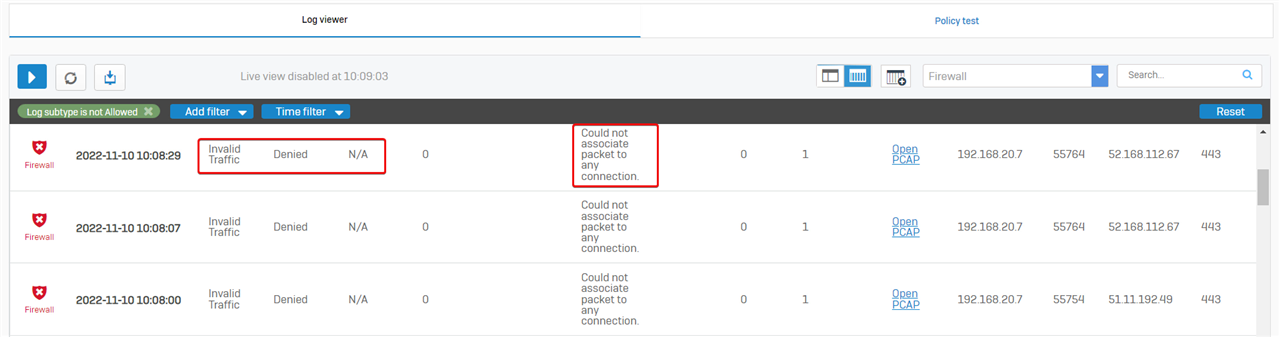
Sophos Firewall checks the data packets for conntrack entries. Conntrack entries are generated when connection initializing packets are sent, for example, TCP SYN, or ICMP echo requests.
If a host sends a packet that doesn't match any established connection, Sophos Firewall drops it and logs it as an invalid traffic event.
A more detailed explanation can be found at Sophos Firewall Administrator Help > Invalid traffic events.
Note that "Could not associate packet to any connection" can be caused by asymmetric routing. - Invalid packet. No ICMP record was found.
Sometimes, the message, “Invalid packet, no ICMP record found” is shown.
This refers to a dropped ping reply without a ping request.
These ping reply packets should not be forwarded, as they could be cyberattacks.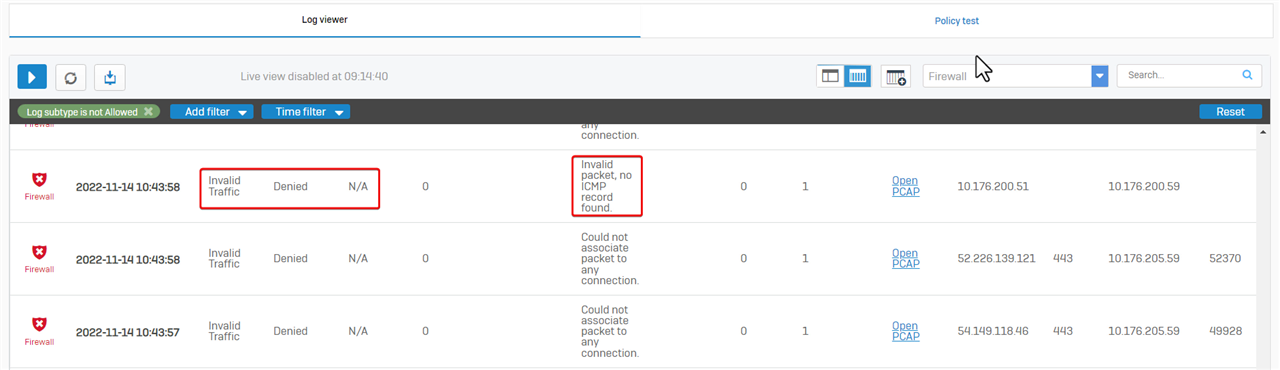
Web filter
Sophos Firewall web admin> Log Viewer > web filter shows packets dropped by the web filter.
To show dropped packets only by clicking on "Add filter", Set "Log subtype isn’t Allowed."
Here is an example: internal computer 192.168.20.7 can't access website https://line.me. The website category is "Online chat", and the related firewall rule ID is 5.
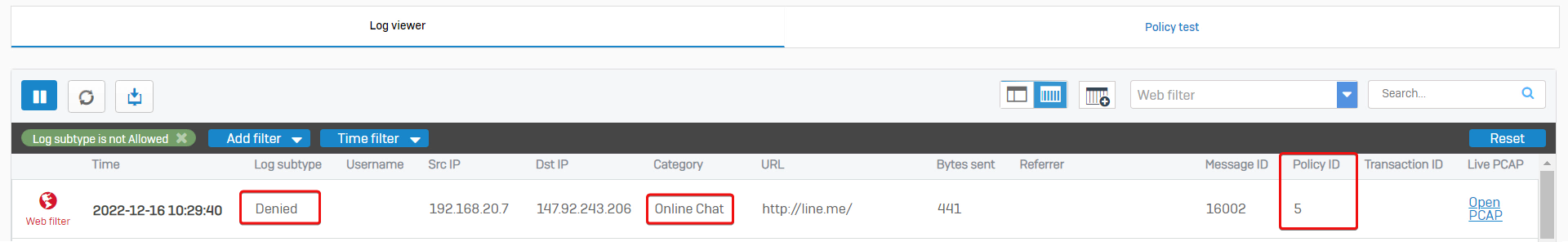
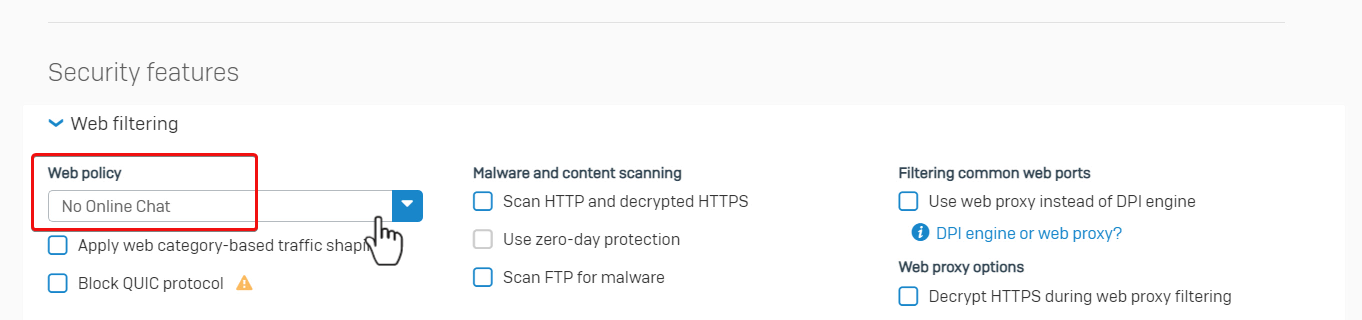
Go to Sophos Firewall web admin> Rules and policies, and check the firewall rule ID 5 details. Web policy "No Online Chat" is applied.
Therefore, Sophos Firewall denied the web access as configured.
Application filter
Sophos Firewall web admin> Log Viewer > Application filter shows packets dropped by the Application filter.
Here, we see that a user is denied access to the destination and the traffic is identified as “Aloha Browser”, and the related firewall rule is ID 5.
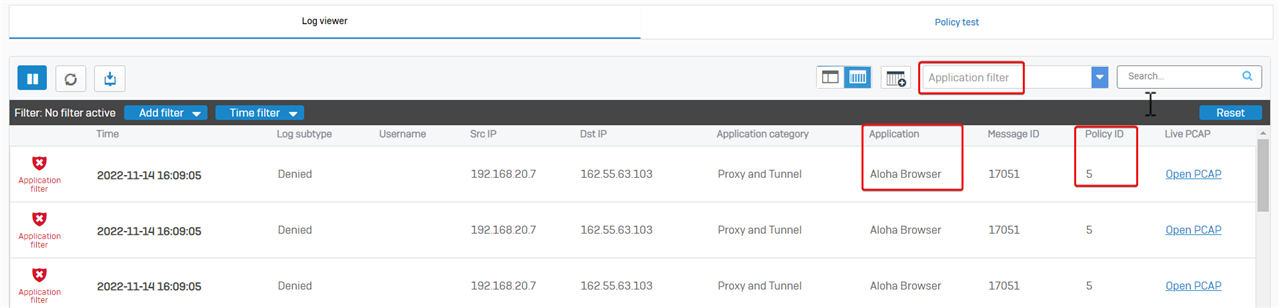
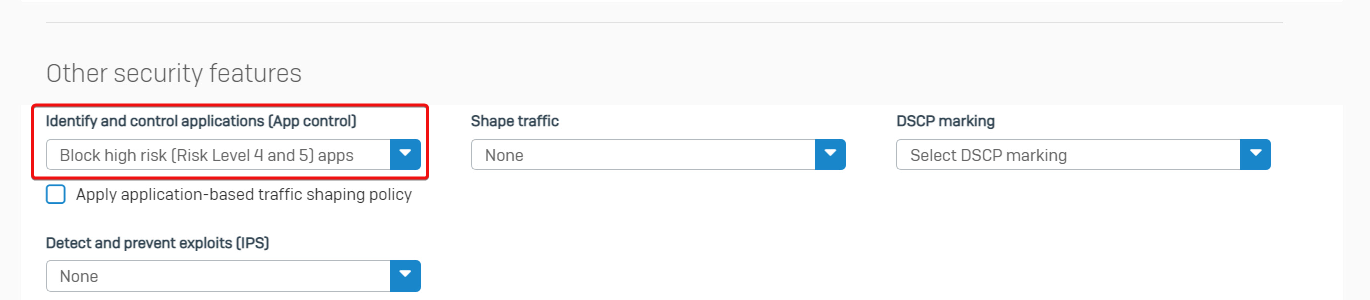
Firewall rule ID 5 has application control turned on to block risk level 4 and 5 apps.
Therefore, Sophos Firewall denies the user access as configured.
IPS
Sophos Firewall web admin> Log Viewer > IPS shows packets dropped by Intrusion Prevention.
The example is that internal computer 192.168.15.15 can't download a file from 65.8.33.12, as the traffic was identified as EICAR. The related firewall rule is ID 5.
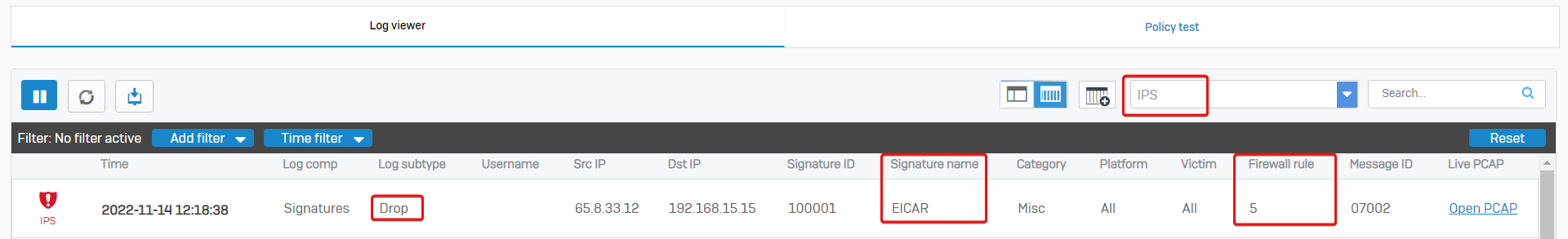
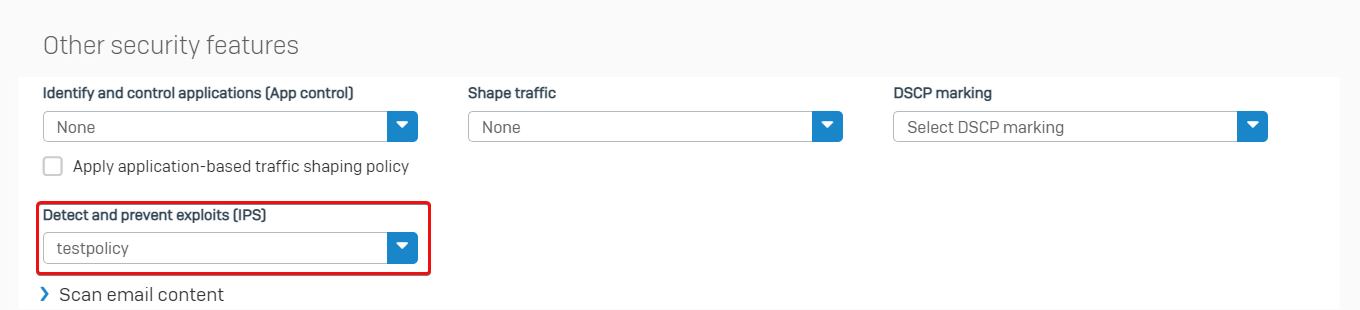
Firewall rule ID 5 has IPS turned on.
Therefore, Sophos Firewall dropped the traffic as configured.
Advanced threat protection
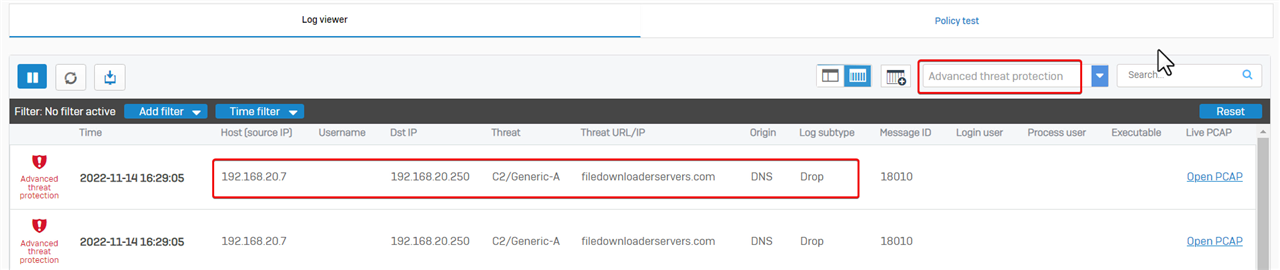
Sophos Firewall web admin > Log Viewer > Advanced threat protection shows packets dropped by Advanced threat protection.
Here is the example: internal computer 192.168.20.7 can't query DNS server 192.168.20.250 for a hostname, as Sophos Firewall detected the hostname malicious and dropped the DNS query.
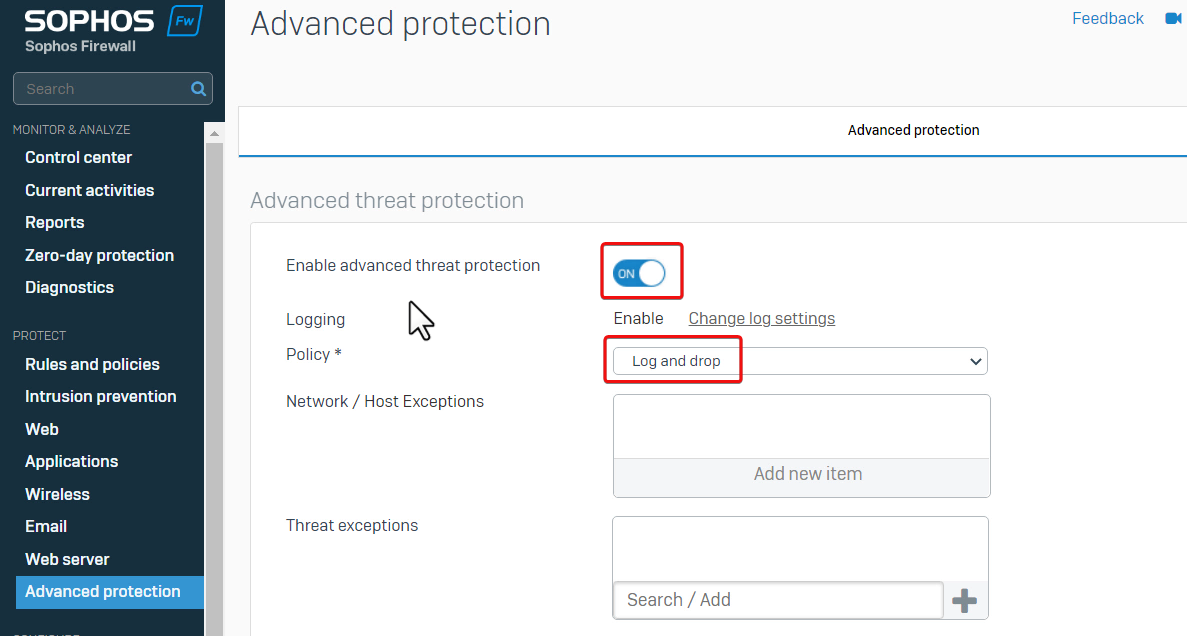
Go to Sophos Firewall web admin> Advanced Protection. We can see Advanced threat protection is turned on, and Policy is set to "Log and drop".
Therefore, Sophos Firewall dropped the packet as configured.
SSL/TLS inspection
SSL/TLS inspection might sometimes fail to decrypt a session and cause an error.
To view SSL/TLS inspection records, go to Sophos Firewall web admin > Log Viewer, and then choose SSL/TLS inspection logs.
Create a filter and set "Action is Error", to show errors.
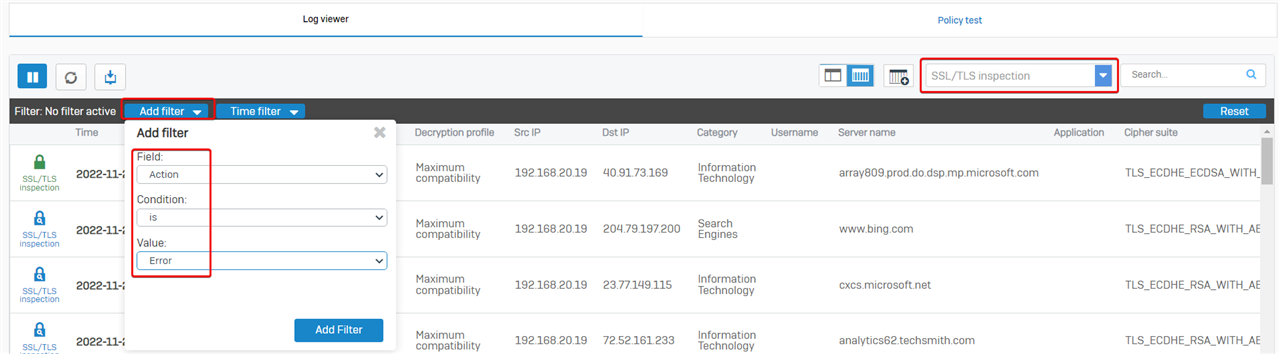
In the example, internal computer cannot visit browser.events.data.msn.com, due to "TLS engine error: FLOW_TIMEOUT"
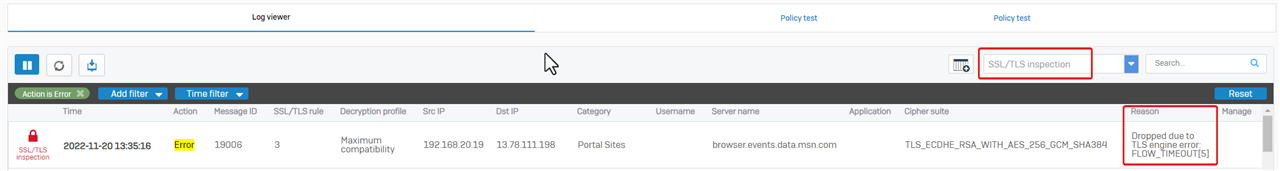
The error causes web access failure. We can configure Sophos Firewall to skip the website from SSL/TLS decrypt.
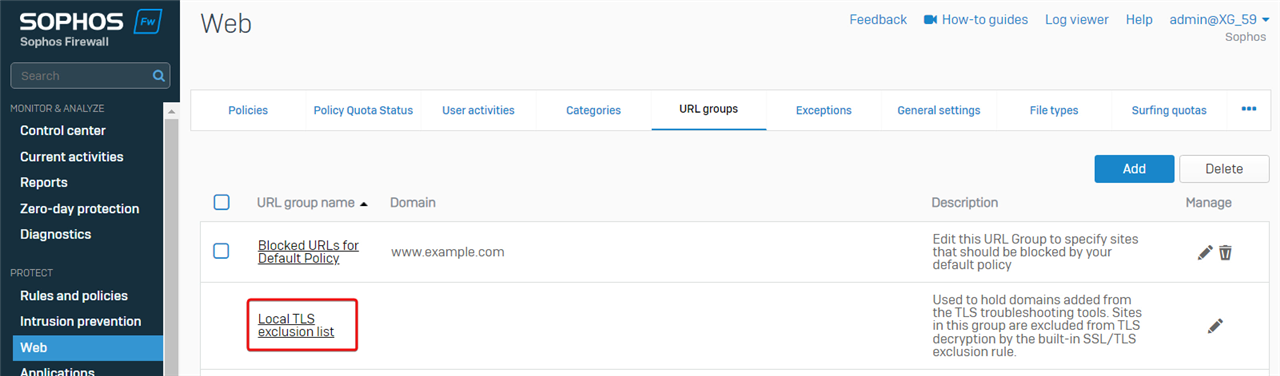
- Edit the default URL group "Local TLS exclusion list" in Firewall web admin GUI > Web > URL groups
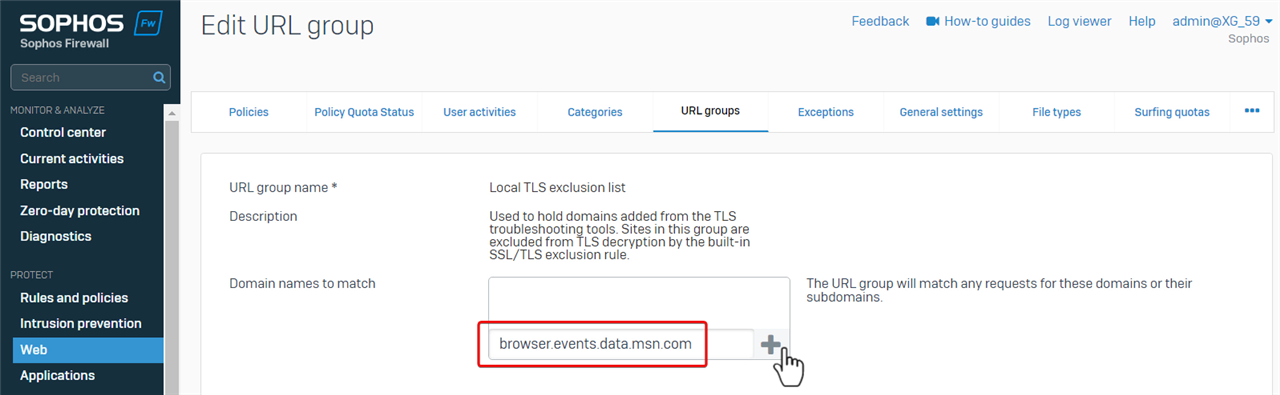
- Add the website browser.events.data.msn.com, and then the SSL/TLS inspection engine won't decrypt the traffic to the website.
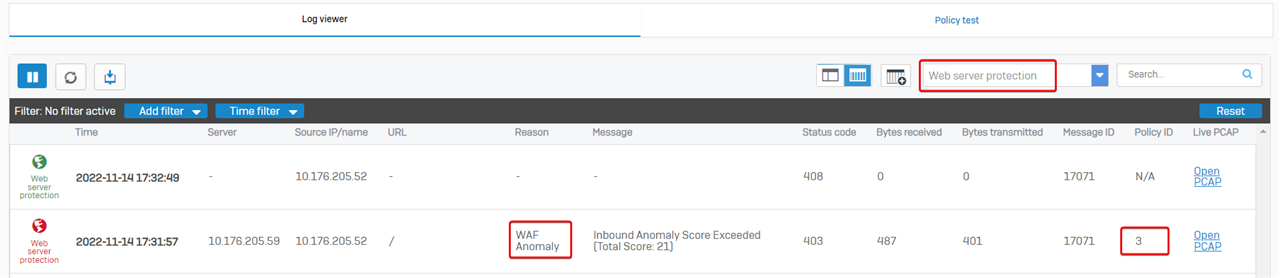
Web server protection (WAF)
For traffic destined for servers protected by web server protection, Sophos Firewall might drop a packet if it’s identified as an attack.
To view packets dropped by web server protection, go to Sophos Firewall web admin > Log Viewer, and then choose logs of web server protection.
In the example, source computer 10.176.205.52 isn’t allowed to access the web server due to "WAF Anomaly", and the firewall rule for WAF is ID 3.
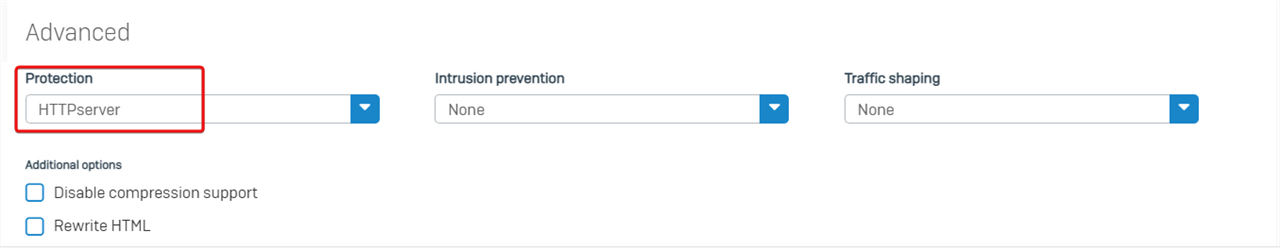
Firewall rule ID 3 has web server protection policy turned on,
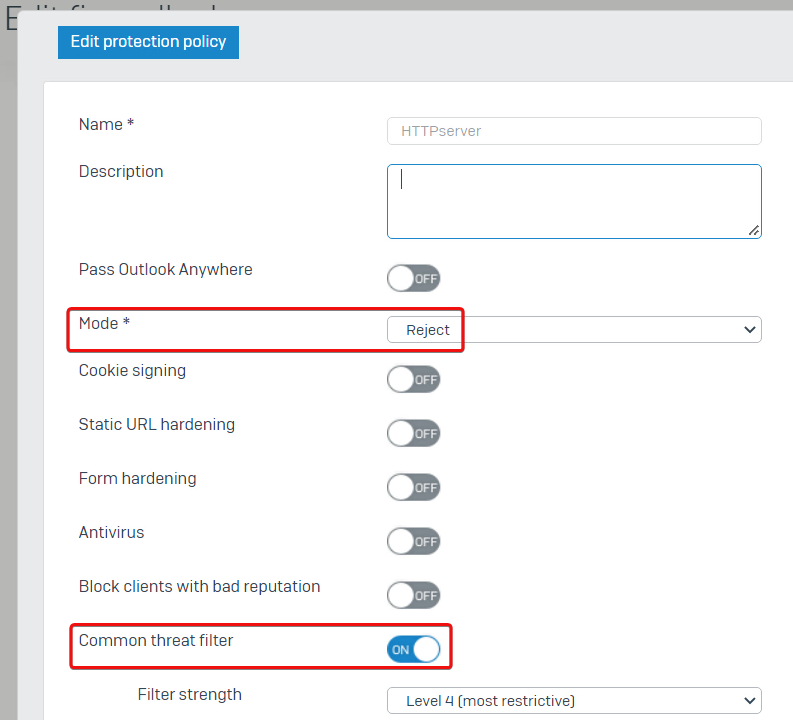
Check the details of the protection policy; we can see the Mode is set to Reject, and the Common threat filter is turned on.
Therefore, Sophos Firewall dropped the web server access as configured.
Troubleshooting
Asymmetric routing
In this example, the PC and HTTP Server are connected by a Sophos Firewall.
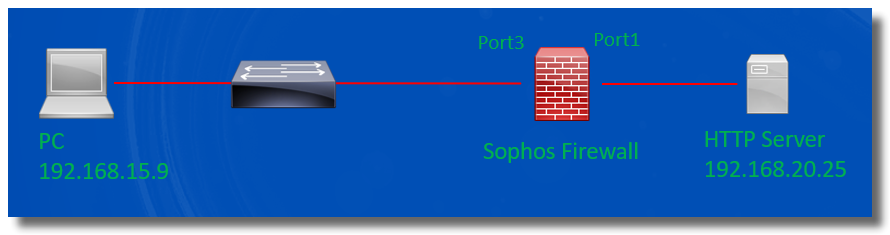
However, the PC can't access HTTP service hosted on the server
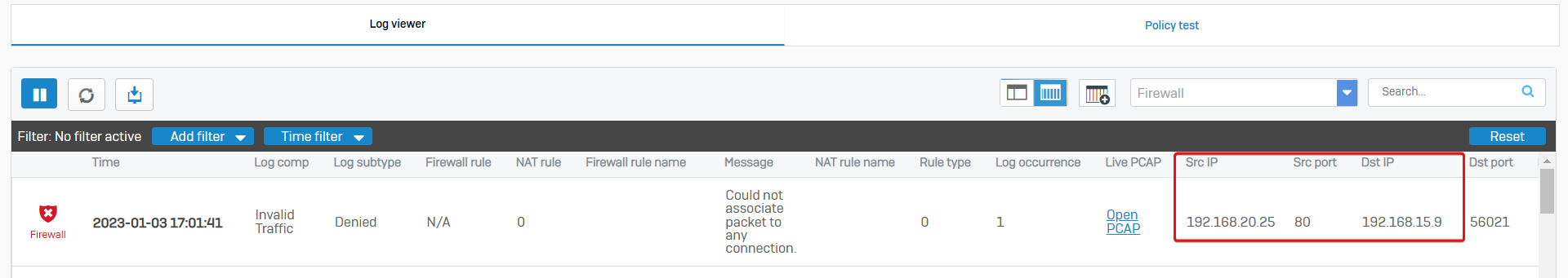
Log Viewer > Firewall shows that the packet from the Server to the PC got dropped by Sophos Firewall with the reason "Could not associate packet to any connection."
We must capture packets to verify if the dropped packet is a problem.
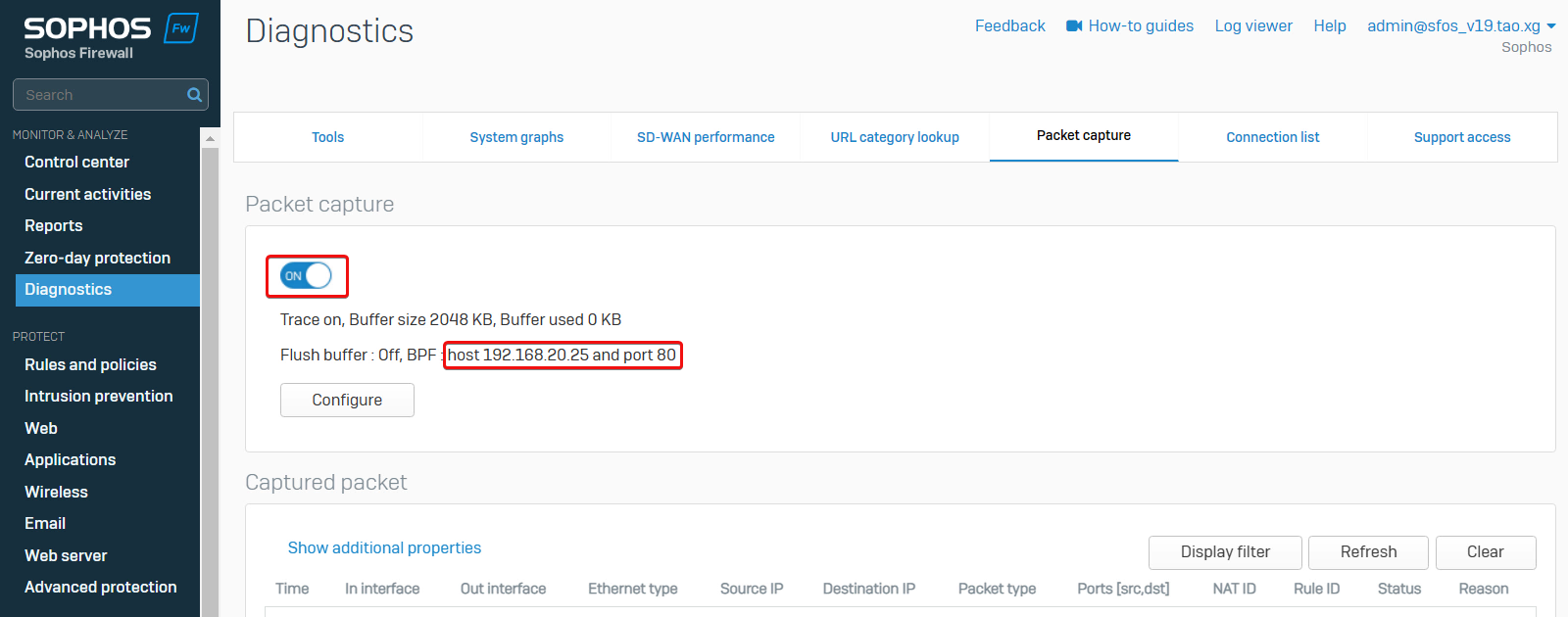
In Sophos Firewall web admin, go to Diagnostics > Packet capture, and click Configure to add a packet filter.
We want to capture packets between the PC and the HTTP server, so we’ll enter the packet filter string “host 192.168.20.25 and port 80”.
Save the filter and turn on Packet capture.
Note:
- The packet filter string is case-sensitive.
- Once the packet filter string is changed, kindly turn it off and then turn on the packet capture to apply the new filter.
- Turn OFF packet capture after the troubleshooting.
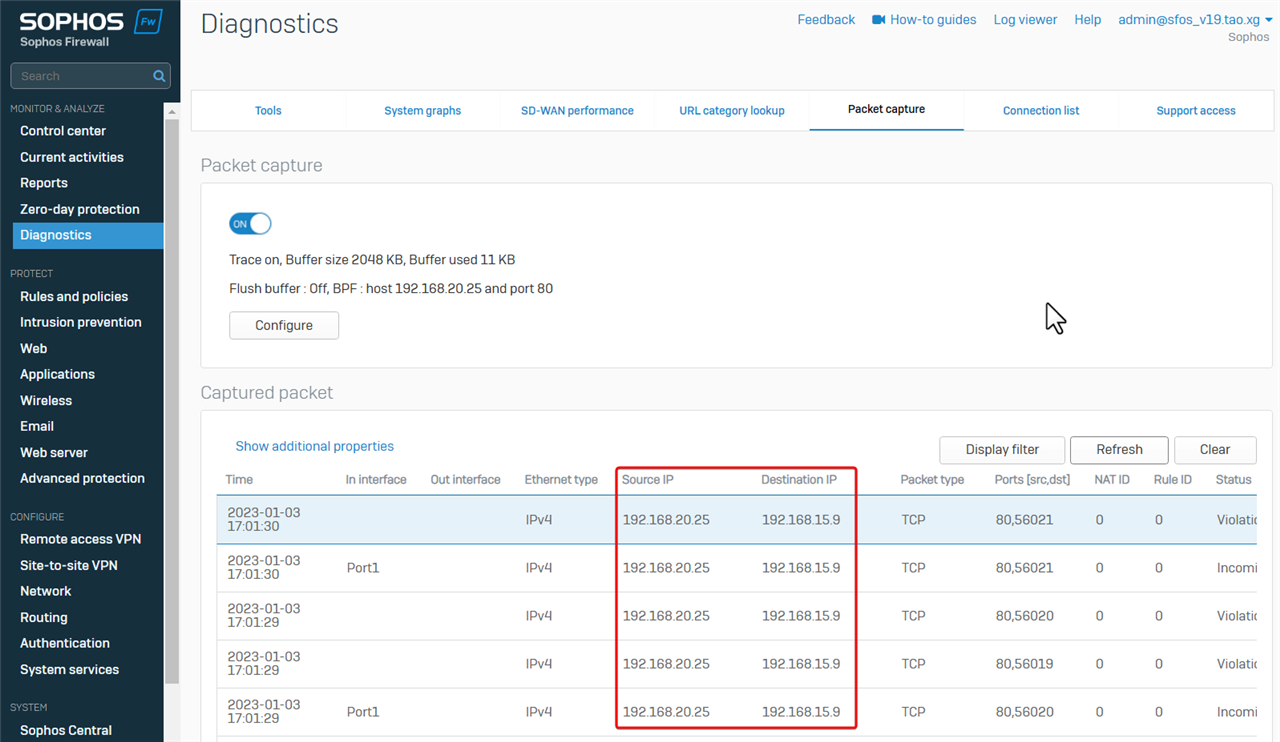
To reproduce the issue, attempt to access the HTTP server from the PC again, and then Refresh the page to view captured packets.
We can see Sophos Firewall received the reply packet from the Server to the PC, but no packets from the PC to the Server.
That indicates the problem of asymmetric routing in the network.
The solution is to fix asymmetric routing in the network.
Once it’s fixed, the PC can visit the HTTP Server.
Web filter
In the example, the internal computer behind Sophos Firewall has a problem visiting youtube.com, where the video preview isn’t loaded.
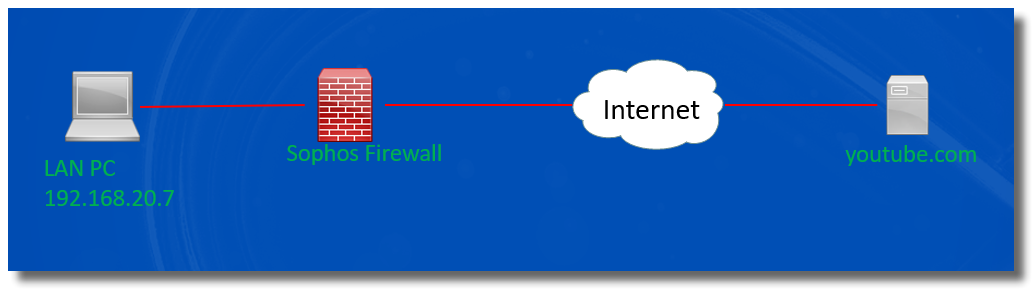
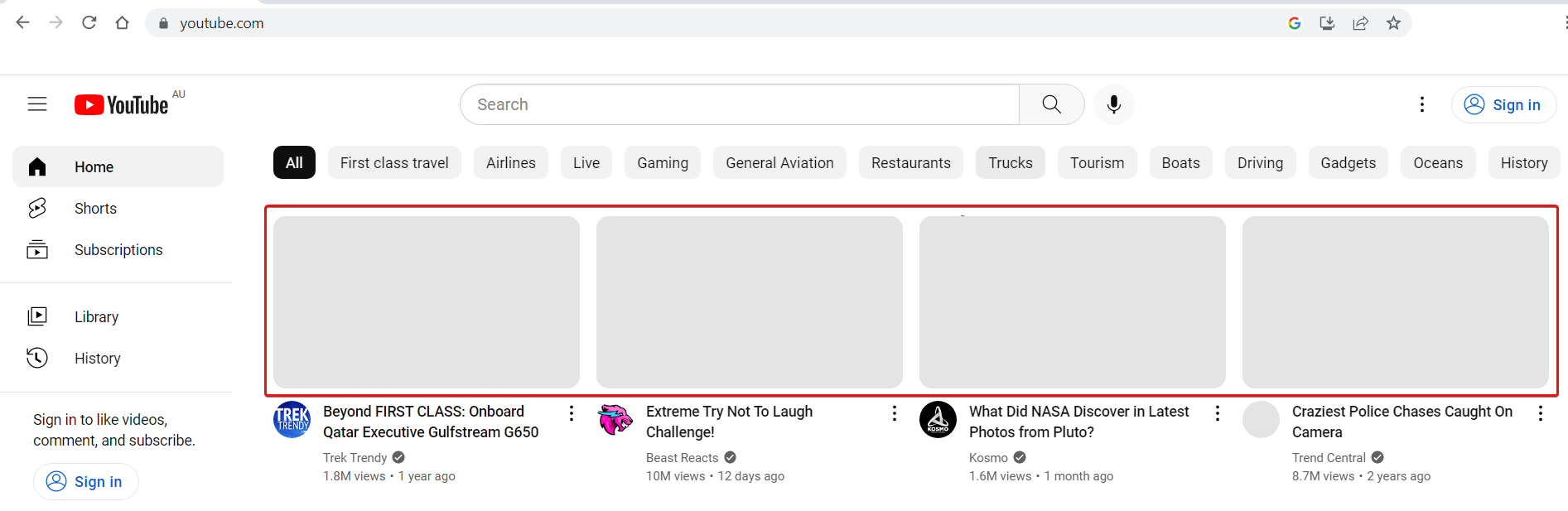
To troubleshoot the issue,
- Open the browser Developer Tools, go to the Network tab, and refresh the web page.
Developer Tools shows 2 domains, yt3.ggpht.com and i.ytimg.com cannot be loaded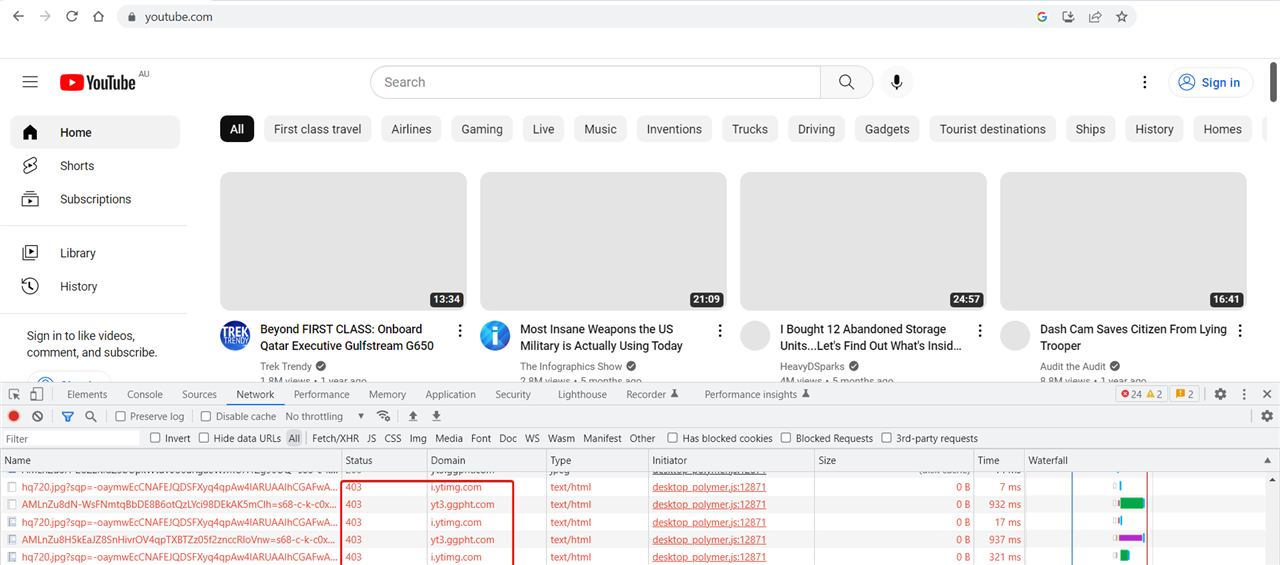
- Go to Sophos Firewall web admin > Log Viewer > web filter. It shows URLs on those two domains got denied by firewall rule ID 8 when users visit YouTube website
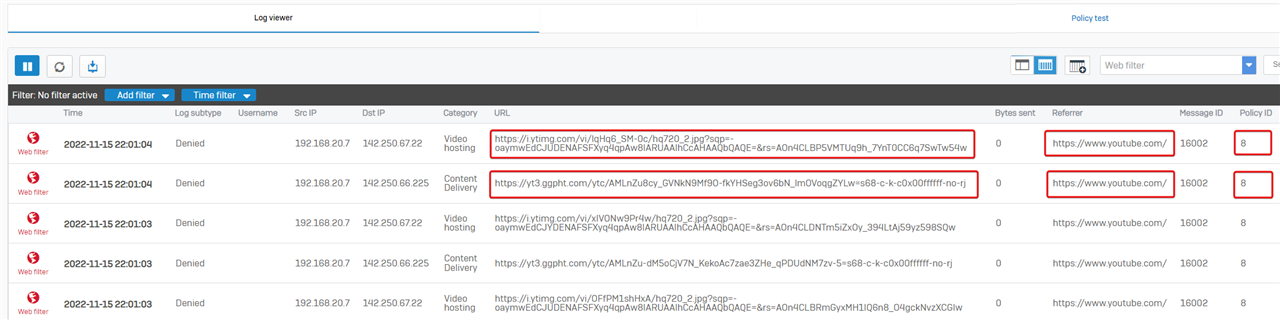
- Go to Sophos Firewall web admin> Rules and policies > Firewall rules. Firewall rule ID 8 was configured to drop traffic to those two domains.
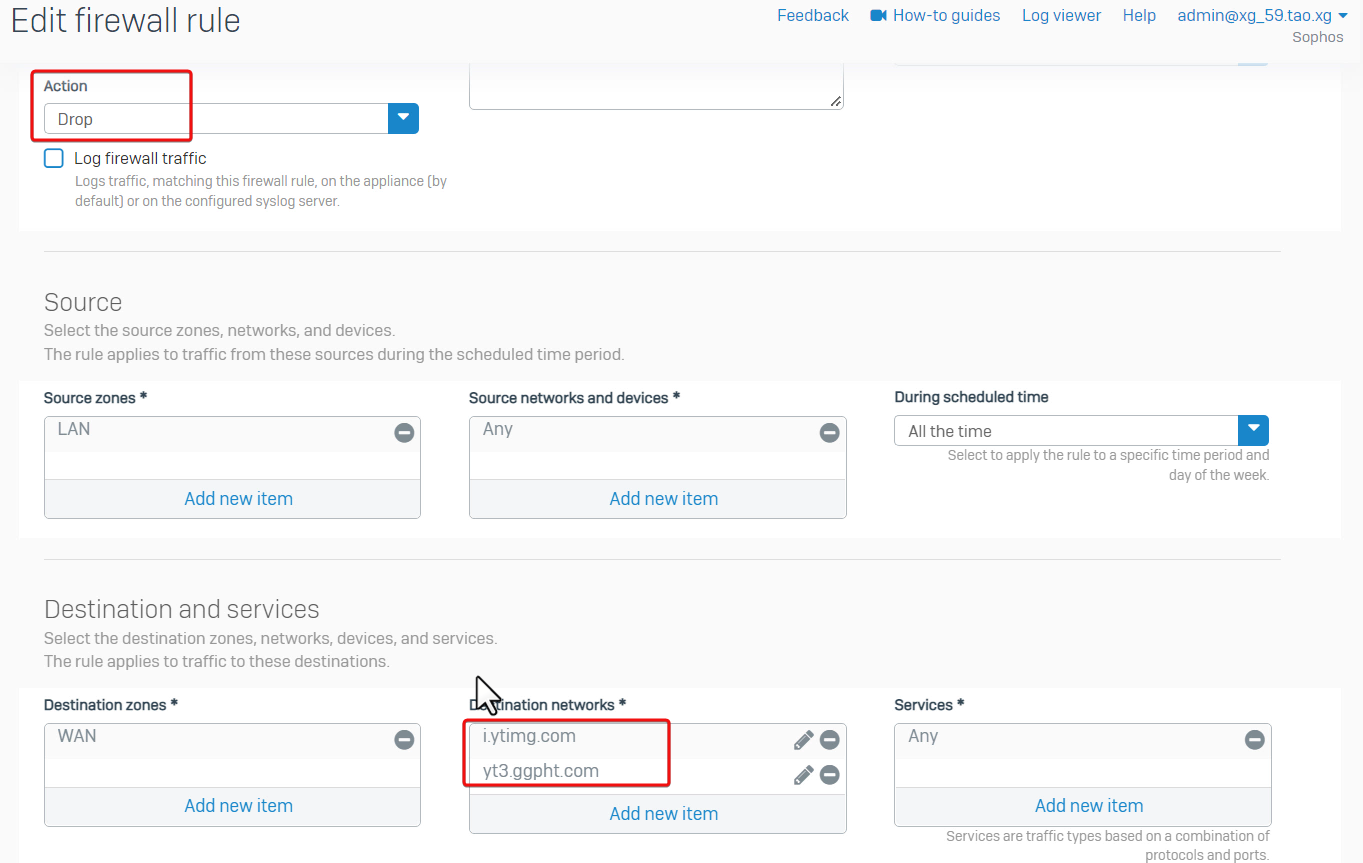
Therefore, it’s a misconfigured firewall rule.
The solution is to turn off the firewall rule, and then the YouTube website can be loaded without any problem.
Application filter
In the example, LAN PC 192.168.20.19 can't access the FTP server on internet.
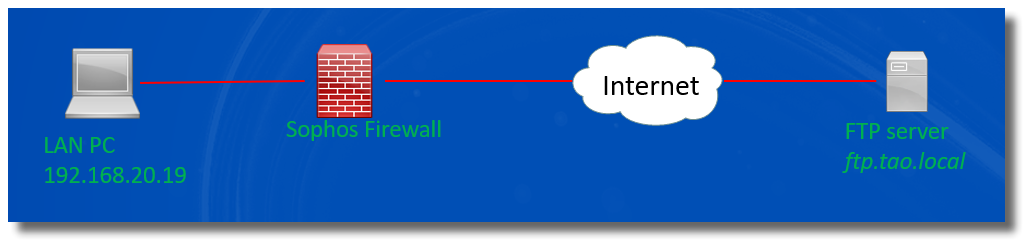
We need to capture packets in Sophos Firewall webadmin to determine if Sophos Firewall forwards traffic between the LAN PC and the FTP server.
In packet capture, we need to provide an IP address, not hostname, so the first step is to query the IP address of the FTP server in nslookup command on the LAN PC.
The output of nslookup shows the FTP server has 2 IP addresses
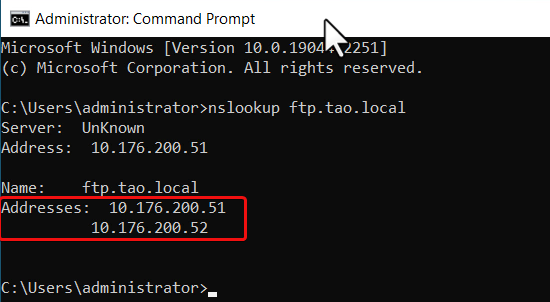
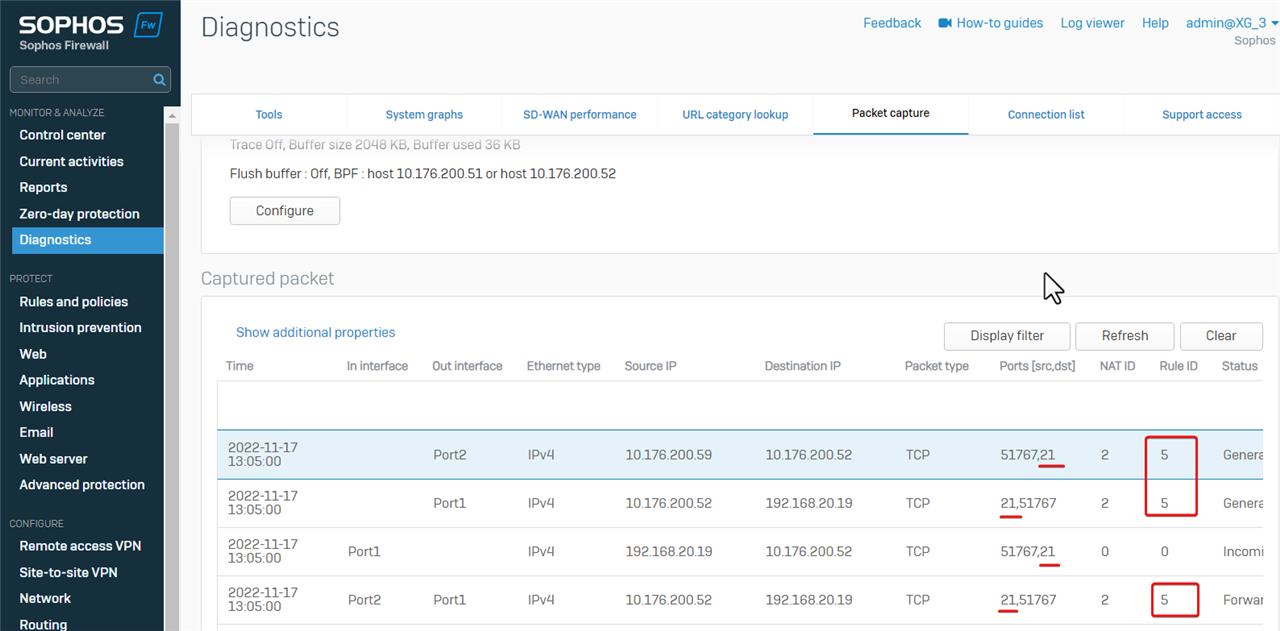
The packet capture filter is "host 10.176.200.51 or host 10.176.200.52" to capture packets on both IP addresses.
In Sophos Firewall web admin> Diagnostics > Packet capture, toggle off packet capture, set the packet capture filter to "host 10.176.200.51 or host 10.176.200.52", and then toggle to turn on the packet capture.
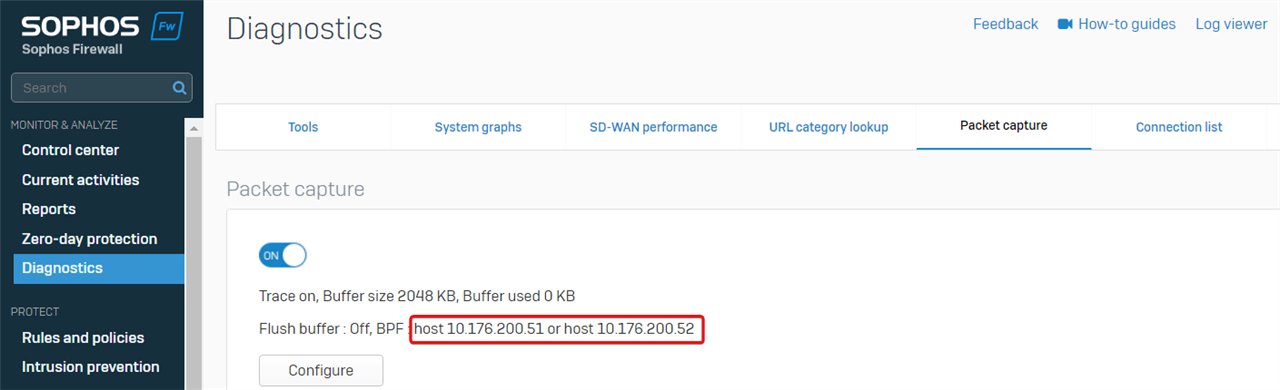
To reproduce the issue on a LAN PC, toggle OFF packet capture immediately.
We can see the FTP traffic from the LAN PC to the external FTP server is controlled by firewall rule ID 5.
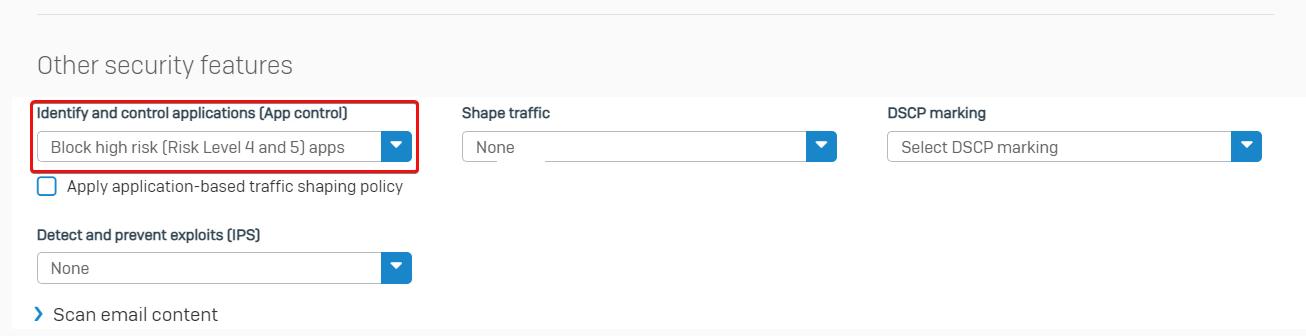
Check details of the firewall rule ID 5, and found that the application control policy Block high-risk Risk levels 4 and 5 apps were turned on.
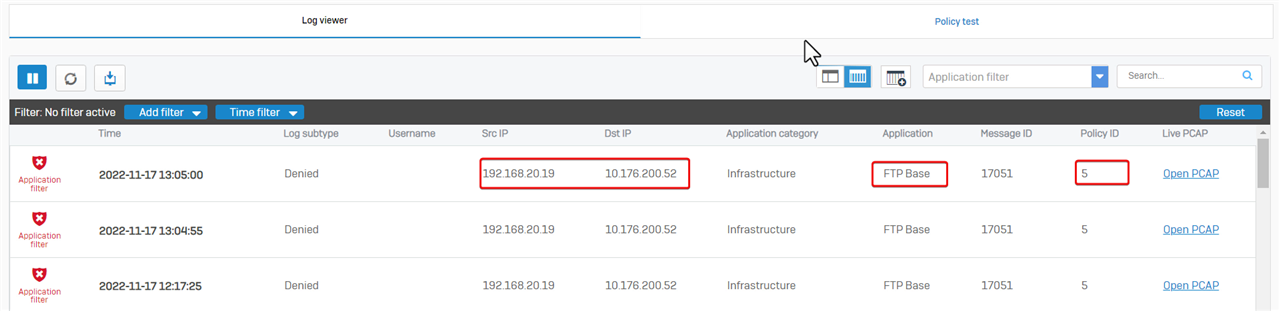
The next step is to check if the FTP session is dropped by application control.
Go to Log Viewer > Application filter. It shows the FTP traffic is dropped, and application is "FTP Base".
Therefore, Sophos Firewall dropped the FTP connection as configured.
We can turn off application control in firewall rule ID 5 to work it around.
Note: Another workaround is to create a new firewall rule for the FTP traffic without application control.
Dos Protection
For example, remote access SSL VPN users can't download large files from the internal web server.
Users can log in to SSL VPN and ping internal resources without problem.
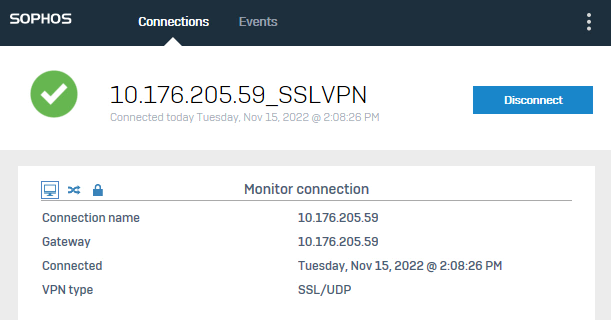
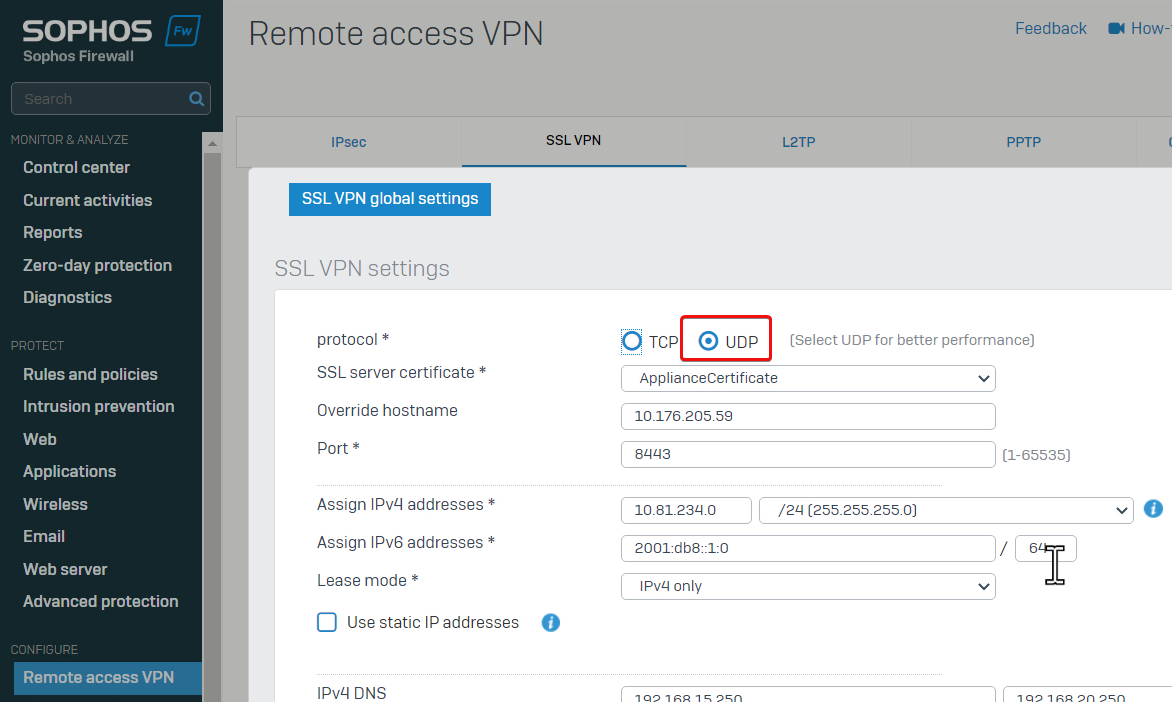
Noticed remote access SSL VPN has been configured to work on UDP.
To troubleshoot the issue,
- I disconnected all other devices from Sophos Firewall so that only that remote access SSL VPN user and the internal web server were connected.
- Then, go to Firewall web admin GUI > Intrusion prevention > DoS attacks.
Refresh the page and notice the number of dropped UDP Floods had increased when the user was downloading a file.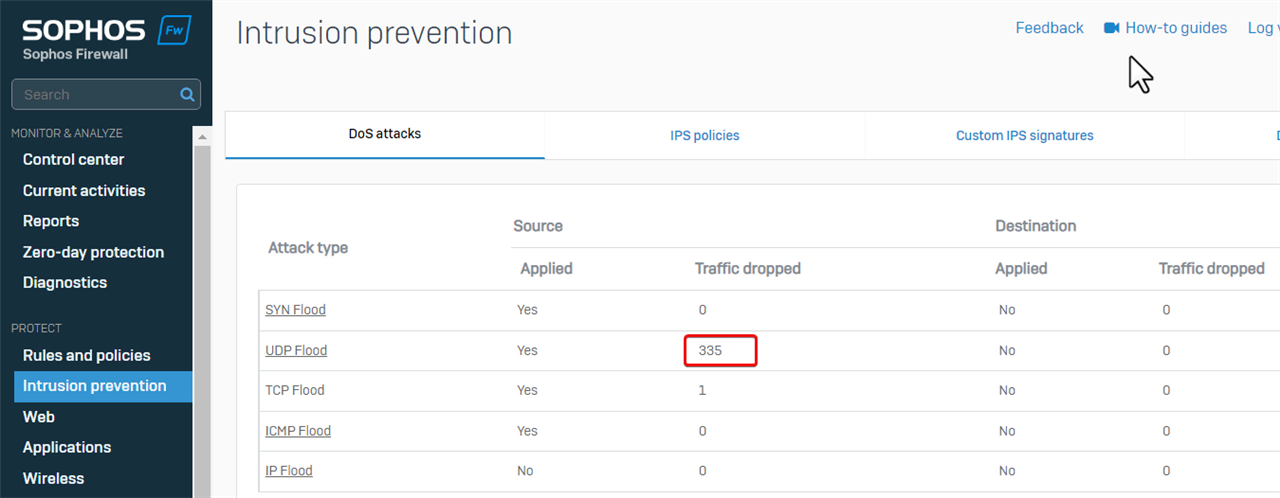
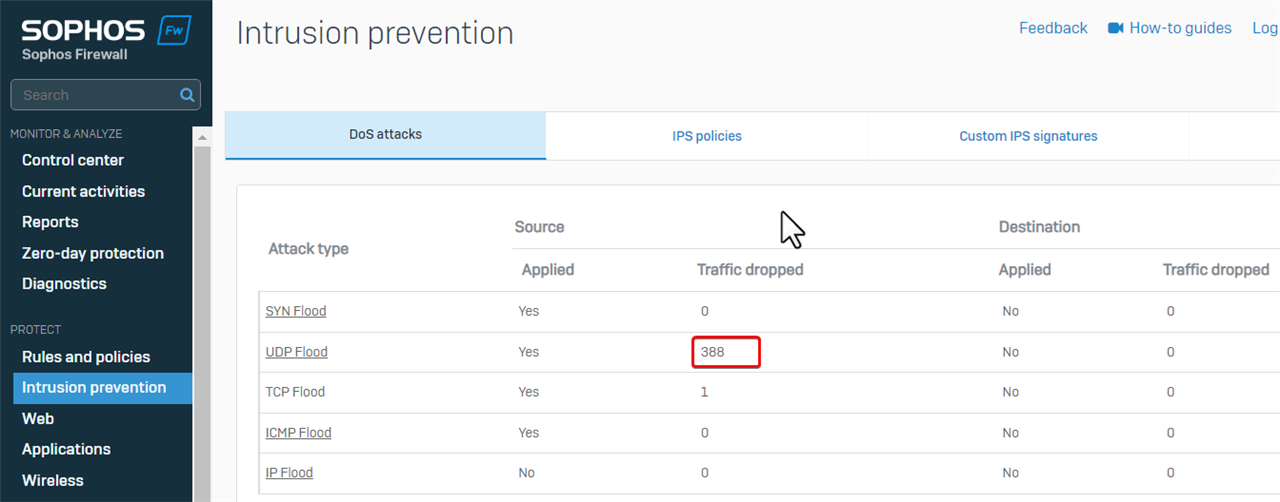
That indicates that Sophos Firewall dropped UDP traffic of SSL VPN due to DoS protection.
The workaround is to increase the default limit of UDP flood.
I also increased the default limit of TCP flood, as traffic from/to web server is on TCP.
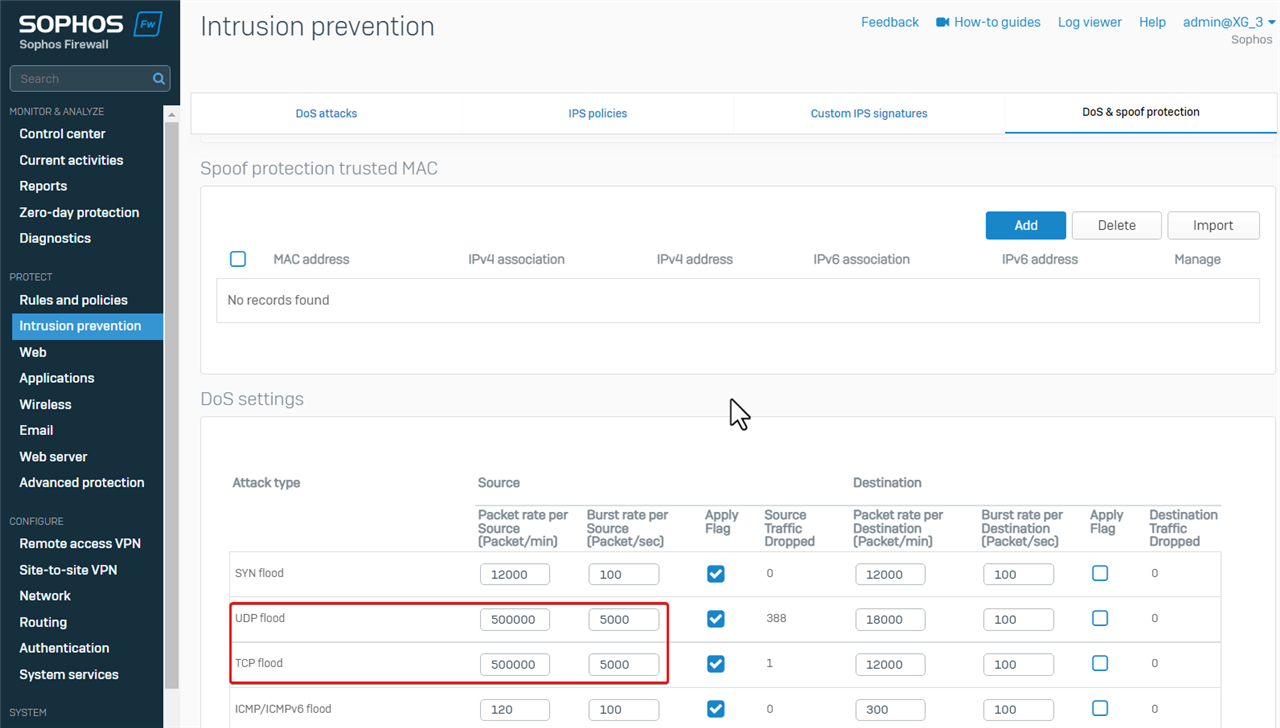
Now, the remote access SSL VPN user can download files from the internal web server without any problem.
No firewall rule
Sometimes, we might experience the problem of ping failure.
In the example, PC 192.168.20.7 behind Sophos Firewall LAN Port1 can't ping another PC 192.168.15.15 behind Sophos Firewall LAN Port3.
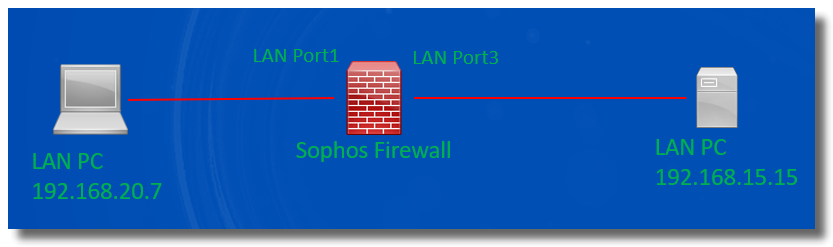
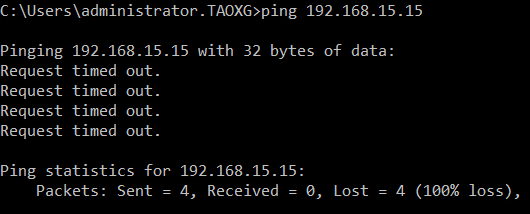
To troubleshoot the issue, capture the packet to see if Sophos Firewall receives and forwards the ping packets.
Go to Sophos Firewall webadmin > Diagnostic > Packet capture, and enter "host 192.168.15.15 and ICMP" as the filter string to capture the ping packet sent from/to 192.168.15.15
Reproduced the issue by ping, and then refreshed the Packet capture page.
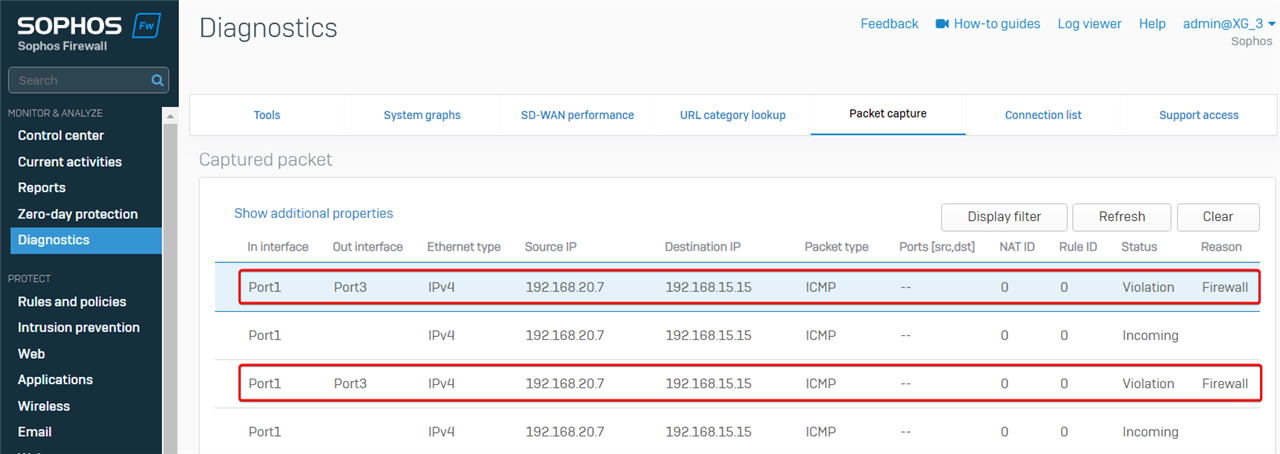
We can see Sophos Firewall received the ping packet sent by 192.168.2.0.7 on LAN Port1, but it didn't forward the ping packet to the destination with Status "Violation" and Reason "Firewall", which indicates no firewall rule allows the traffic.
Therefore, the solution is to create a firewall rule to allow the traffic.
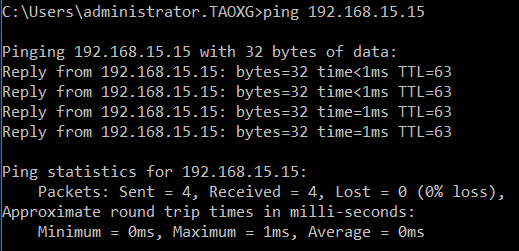
Once the firewall rule for the traffic is created, 192.168.20.7 can ping 192.168.15.15.
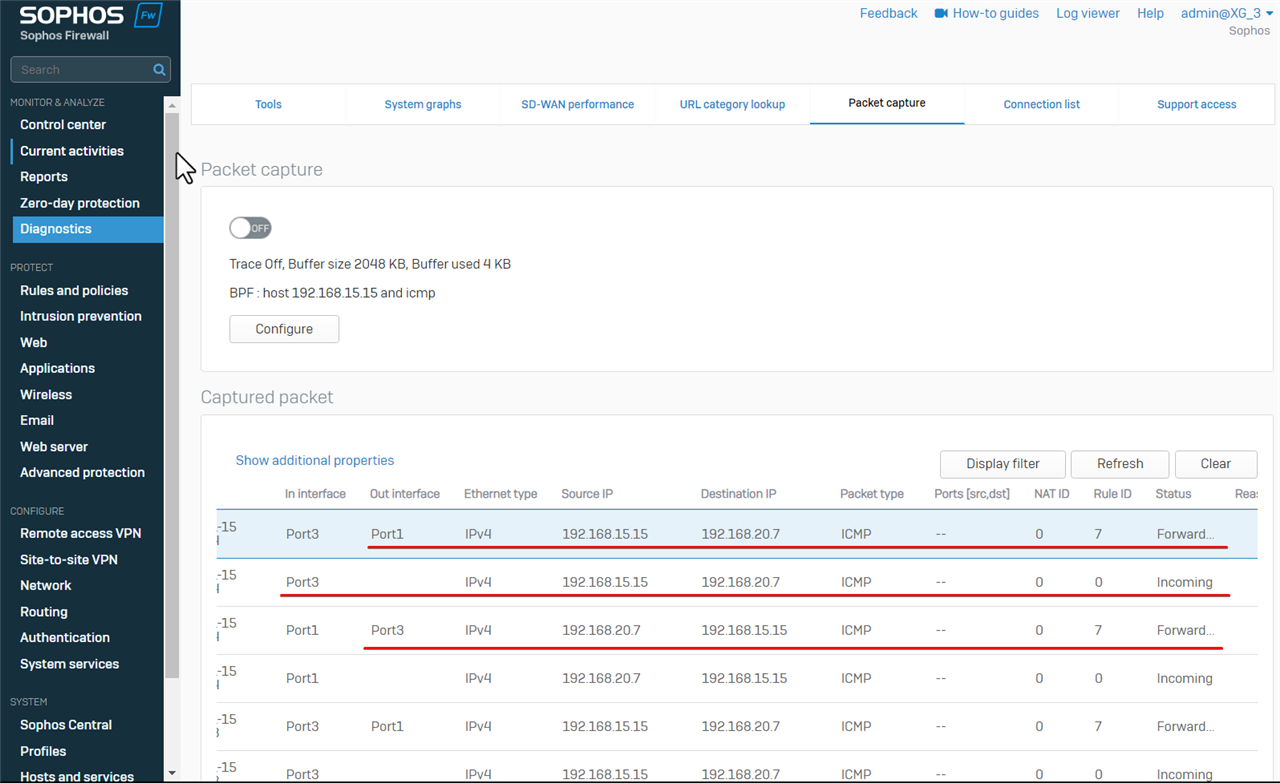
Return to Sophos Firewall web admin> Diagnostic > Packet capture, to capture packets again.
- Clear captured packets
- Refresh the page
- Started the ping again,
We can see
- Sophos Firewall forwarded ping sent by 192.168.20.7 out on Port3
- it received the ping reply sent by 192.168.15.15 on Port3
- and forwarded the ping reply out on Port1 back to 192.168.20.7.
Routing
It’s possible that routing issues can cause network access failure, and packet capture can help us identify that.
For example, LAN PC 192.168.20.19 can't access PC 192.168.25.16 in a remote IPsec VPN network.
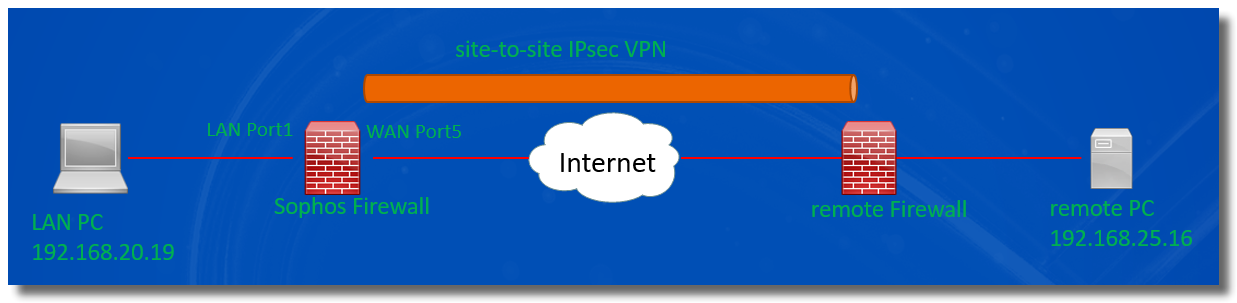
Let's check if Sophos Firewall receives the ping packet from the LAN PC, and forwards it out into IPsec VPN tunnel.
Go to Sophos Firewall > Diagnostics > Packet capture, set the packet filter string to be "host 192.168.25.16 and ICMP", and toggle ON packet capture.
Reproduced the issue by ping from the LAN PC again,
Packet capture shows Sophos Firewall forwarded the ping packet out on Port5.
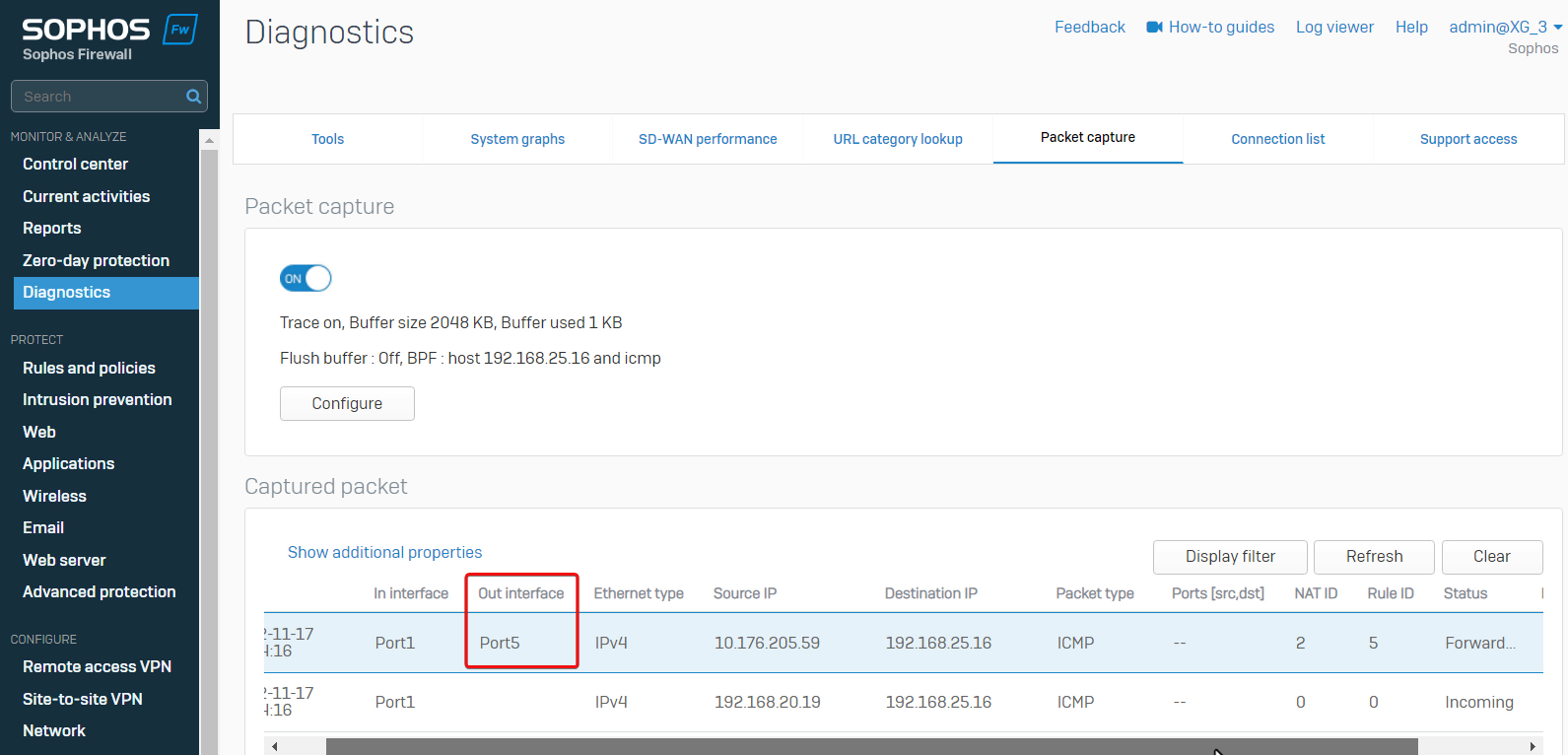
The port5 is the WAN interface on Sophos Firewall. Sophos Firewall will forward the ping packet out on the IPsec VPN virtual interface, not the WAN Port5.
This is a routing issue. We need to check the routing configuration on the Sophos Firewall.
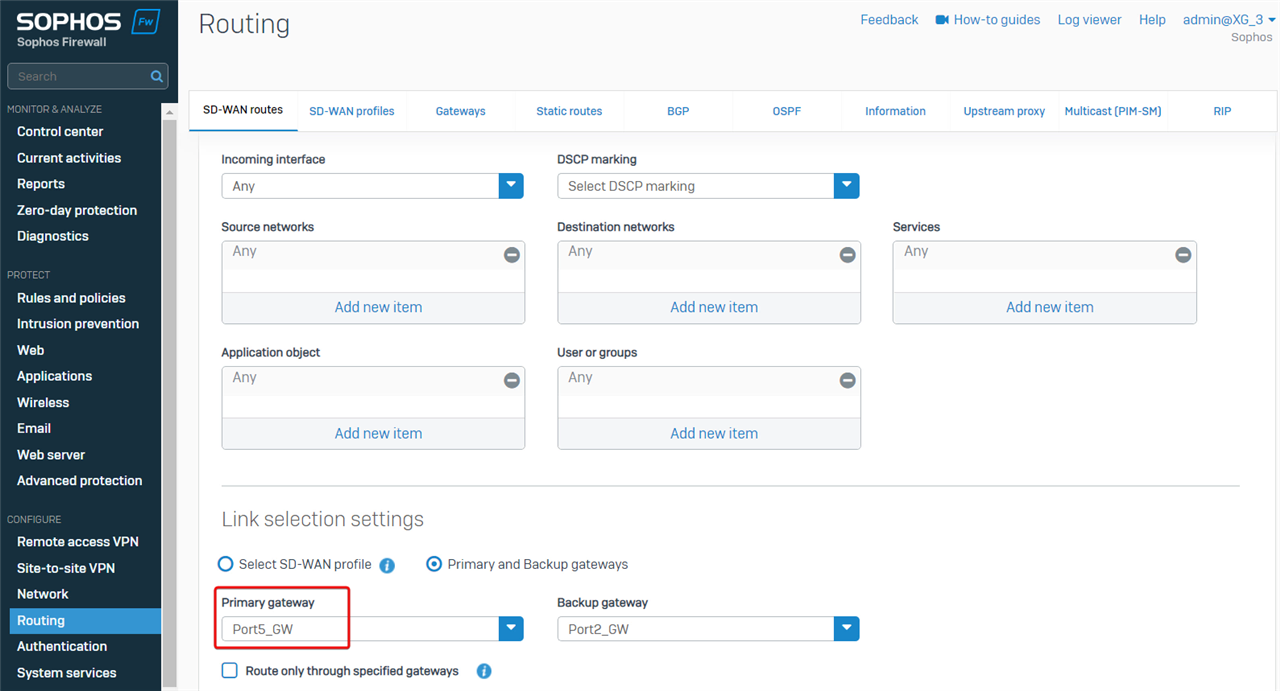
Go to Sophos Firewall webadmin > Routing > SD-WAN routes, and find the SD-WAN route:
- any incoming interface
- any source networks
- any destination networks
- any application object, and
- any user.
- Forwards the traffic out on Port5.
Therefore, the cause of the problem is Sophos Firewall forwards all traffic out on Port5, due to the SD-WAN routes.
The workaround is to make the SD-WAN apply to traffic only destined for internet.
Edit the Destination networks and set it to "internet IPv4".
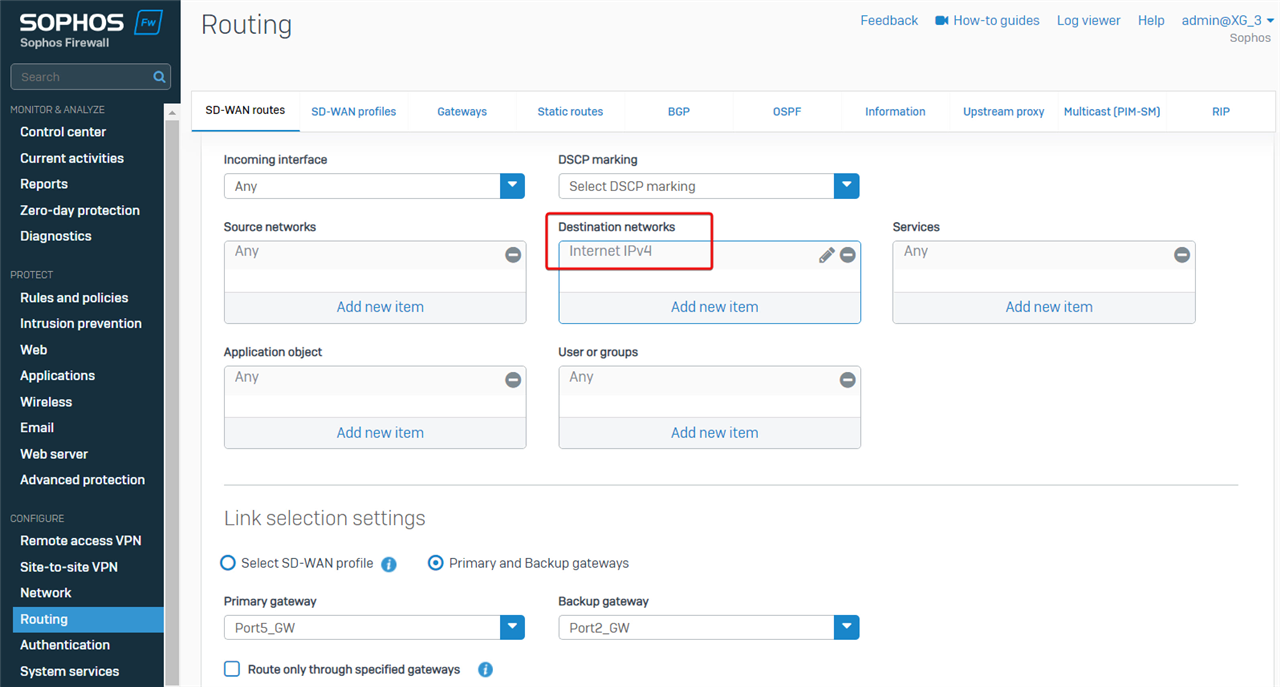
The LAN PC can ping the PC in the remote IPsec VPN network.
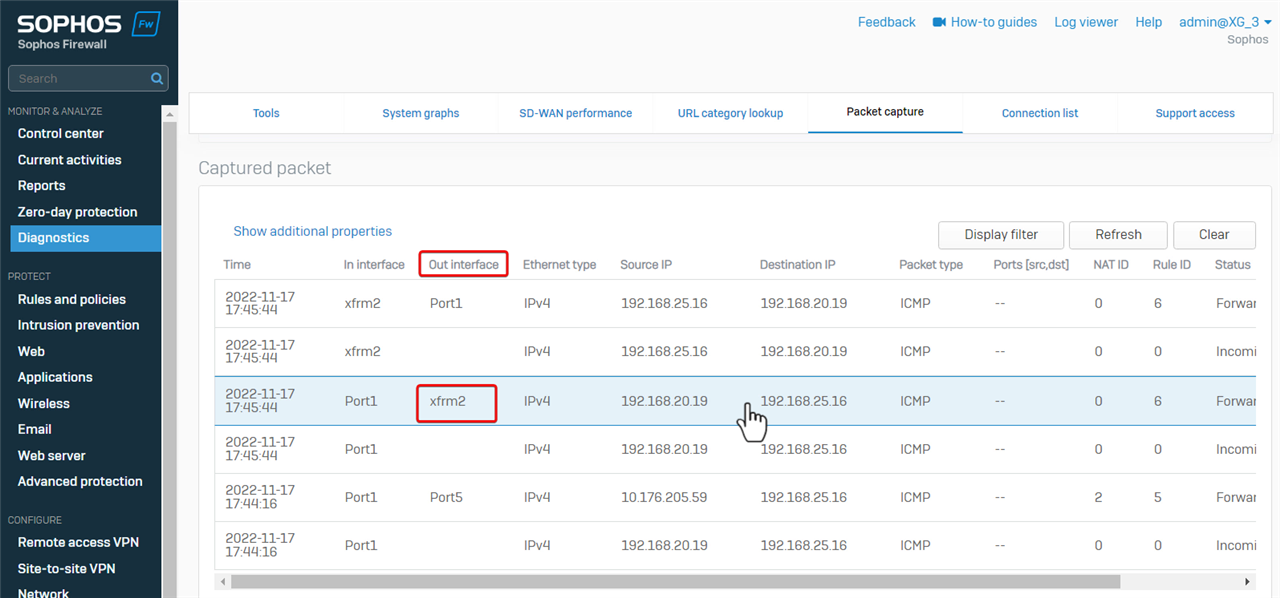
If we capture the packet again, we can see Sophos Firewall forwarded the ping packet out on XFRM, which is the virtual interface of route-based IPsec VPN.
Note
- XFRM is the virtual interface for route-based IPsec VPN
- ipsec is the virtual interface for policy-based IPsec VPN
Summary
- there are different reasons for Sophos Firewall to drop a packet, including the following:
- DoS protection
- not allowed by any firewall rule
- web filter
- application filter
- IPS
- Advanced threat protection
- SSL/TLS inspection
- webserver protection
- invalid traffic in Log Viewer isn’t a problem in most cases, and we don't need to worry about it.
- A misconfigured route might cause problems in network access.
- Packet capture is a useful tool for network troubleshooting.
If a problem can't be identified by the steps above, try to turn off the following to find out which feature causes the problem:
- "Match known users" and all scanning in the firewall rule
- ATP
- IPS service
- SSL/TLS inspection engine in Sophos Firewall webadmin > Rules and policies > SSL/TLS inspection > SSL/TLS inspection Settings > Advanced settings
- firewall-acceleration
Login to SSH terminal of Sophos Firewall as admin
Go to 4. Device Console, and run the following commands
system firewall-acceleration disable - If the problem remains after all the steps above, kindly contact Sophos Support at support.sophos.com/support to investigate the issue further.
Updated doc guide link to latest
[edited by: Raphael Alganes at 3:11 PM (GMT -8) on 12 Nov 2024]


