Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview:
This Recommended Read shares XML import file to import a list of Zoom networks into Sophos Firewall.
Zoom Network XML File
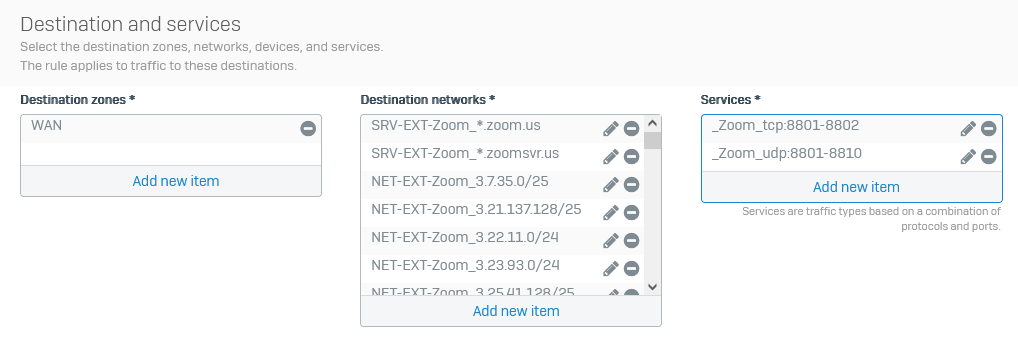
The zoom network list has increased to over 300 networks.
Attached is a Zip File, containing XML file packed into Entities.tar that containing all the networks listed on the Zoom site as of 2024 April 1st.
XML has been created as describes
Sophos Firewall: Creating XML Objects with Notepad++ for mass import
You can extract the .zip file below and import Entities.tar into your Sophos Firewall.
/cfs-file/__key/communityserver-discussions-components-files/258/zoom_5F00_iphosts.zip
______________________________________________________________________________________________________________________________________
Revamped RR
[edited by: Erick Jan at 10:38 AM (GMT -7) on 18 Sep 2024]