Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
Route-based VPNs (RBVPN) are IPsec connections that encrypt and encapsulate all traffic to the XFRM interface. You can create route-based VPN connections for IPv4 and IPv6 protocols between two Sophos Firewall devices, Sophos Firewall, and a third-party firewall, or with a cloud VPN gateway such as GCP.
GCP Classic VPN supports multiple CIDR blocks for traffic selectors with IKEv2, but it uses a single Child SA for all CIDR blocks. However, the Sophos Firewall configured with a policy-based VPN does not support multiple CIDR blocks in a single Child SA with IKEv2. Therefore, route-based VPNs must be used instead of policy-based VPNs to support such a scenario.
This recommended read describes configuring a Route-based IPsec VPN connection between Sophos Firewall and GCP.
Product and Environment
Sophos Firewall
Network diagram
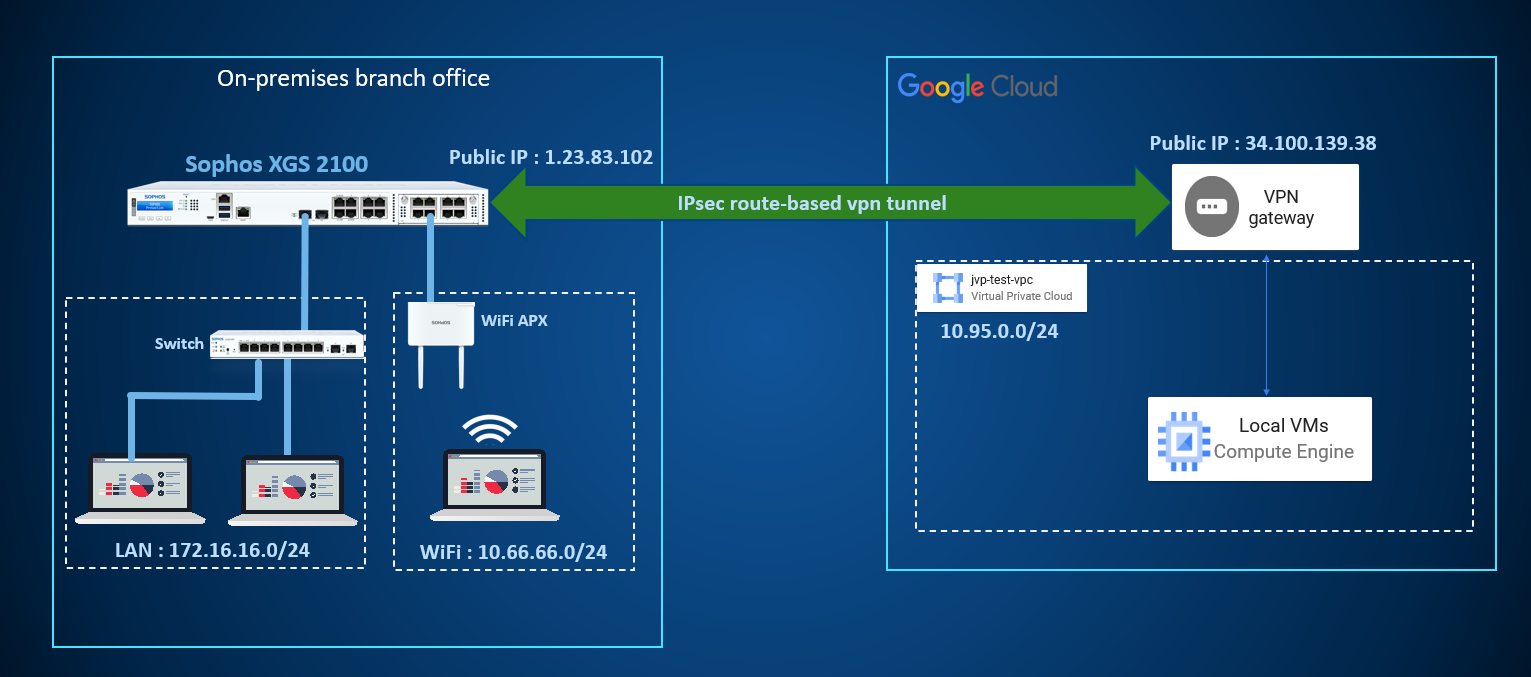
Configuring Route-based VPN (RBVPN) between Sophos Firewall and Google Cloud Platform (GCP)
GCP configuration
- Go to Hybrid connectivity > VPN and click Create VPN connection.
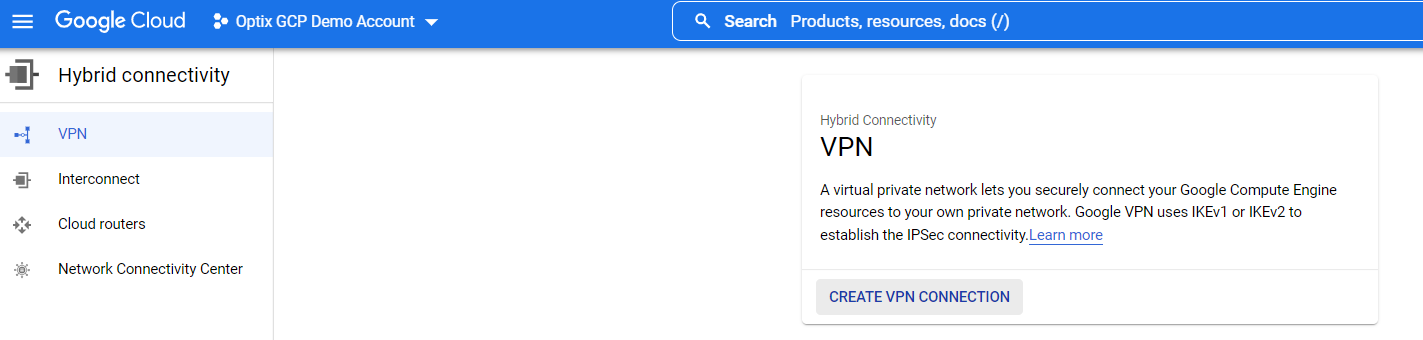
-
Select Classic VPN and click Continue.
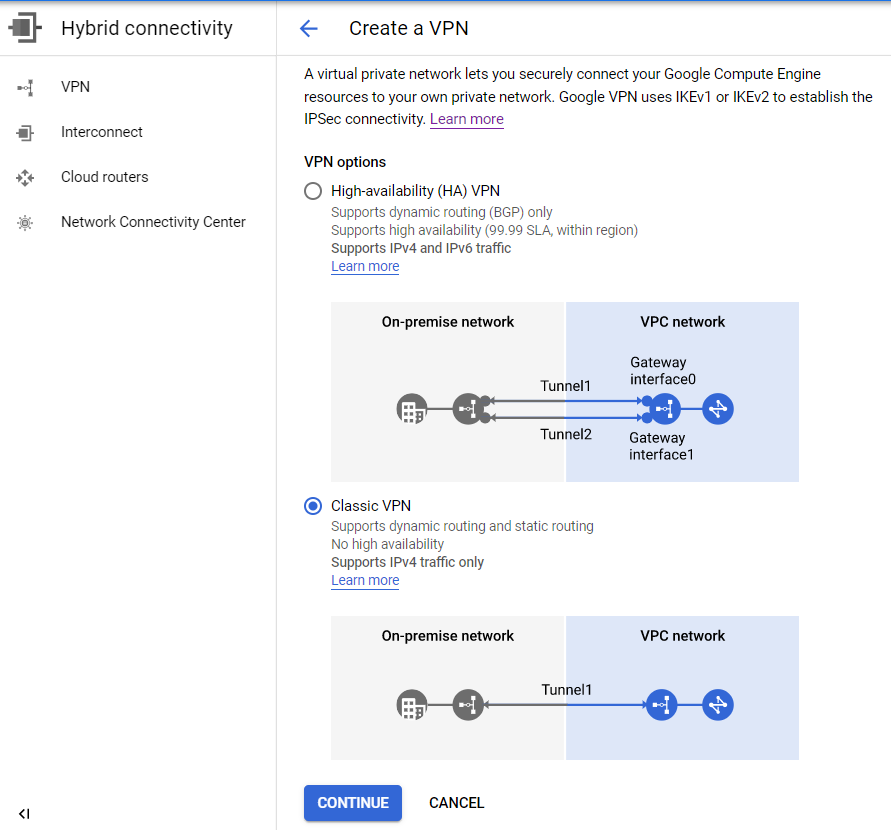
-
Enter the following details for the VPN gateway section:
- Name: Unique name for the VPN gateway matching the naming conventions of GCP.
- Network: Select the VPC network associated with the VM instances or resources deployed in GCP.
- Region: Select the region for the VPN gateway.
- IP address: Create a new public IP address and select it for this VPN gateway. If you already have an unused or unallocated public IP address, you can also select it here.
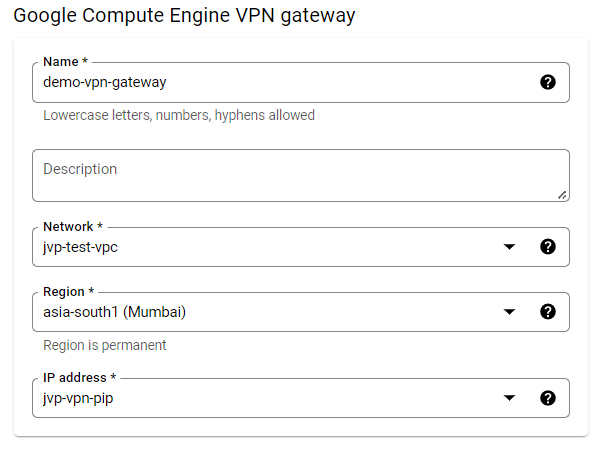
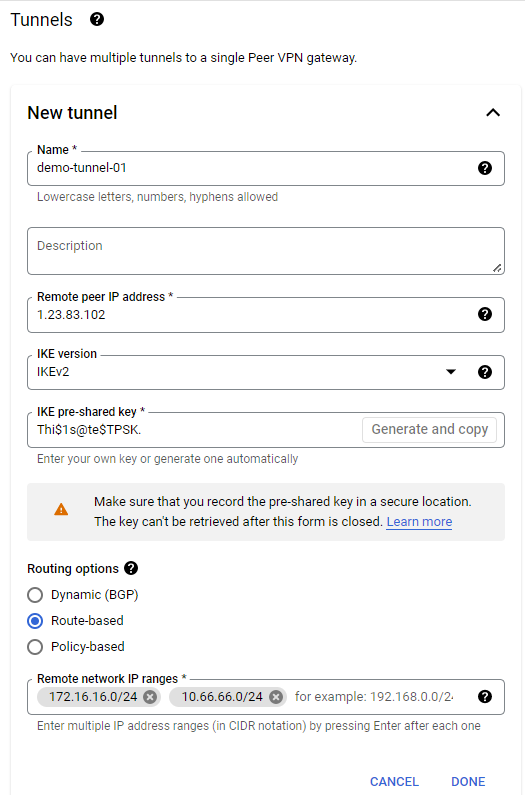
- Enter the following details for the tunnel section:
- Name: Unique name for the tunnel matching the naming conventions of GCP.
- Remote peer IP address: This is the public IP address of the remote side (on-premises firewall) VPN device.
- IKE version: Select IKEv2 here.
- IKE pre-shared key: You can enter the pre-shared key manually or create a random one using the Generate and Copy button.
- Routing options: Select the Route-based option.
- Remote network IP ranges: Enter the network IP address of the remote side (on-premises) with a CIDR block that needs to be reachable via a VPN tunnel.
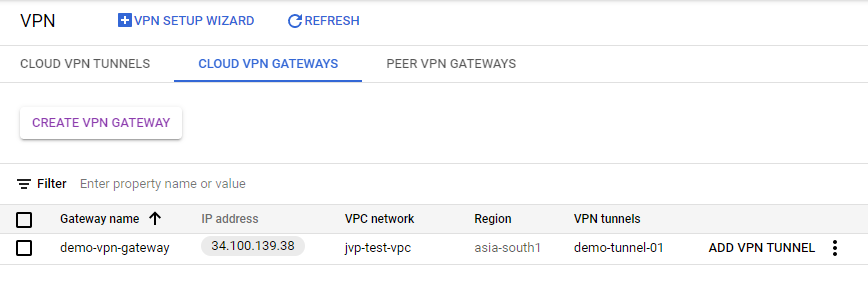
- Verify that the VPN gateway and VPN tunnel is created successfully.

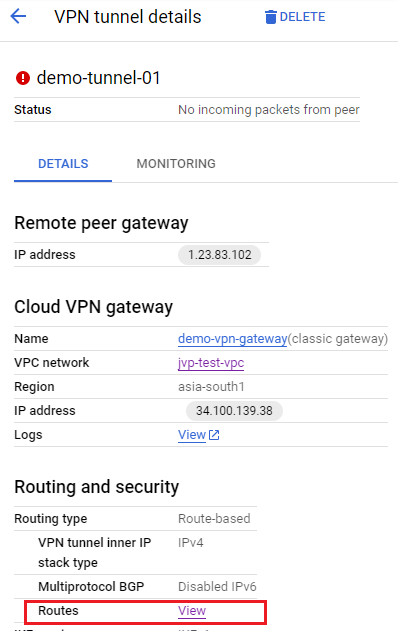
- Click the VPN tunnel to view the details and click View beside the Routes field.
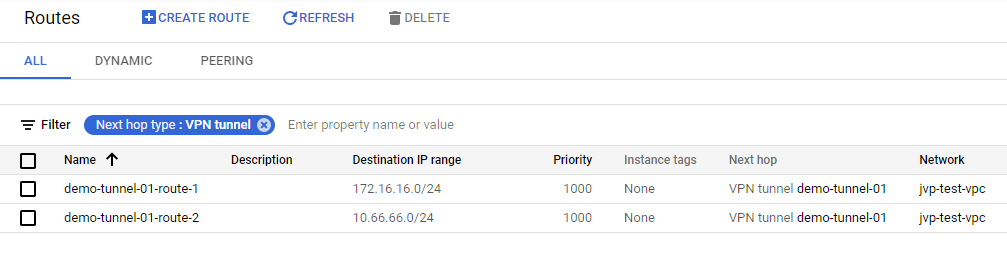
- This will redirect you to the Routes section, and you can apply the filter Next hop type: VPN tunnel to view the routes automatically created for the remote side (on-premises) network.
Sophos Firewall configuration
- Go to SYSTEM > Profiles > IPsec profiles and click the
 (Duplicate this policy) icon for the IKEv2 profile.
(Duplicate this policy) icon for the IKEv2 profile.
Rename this cloned IKEv2 profile as
GCP_IKEv2.Under Phase 1, deselect other DH groups and keep only 14 (DH2048) selected. Then, save the changes.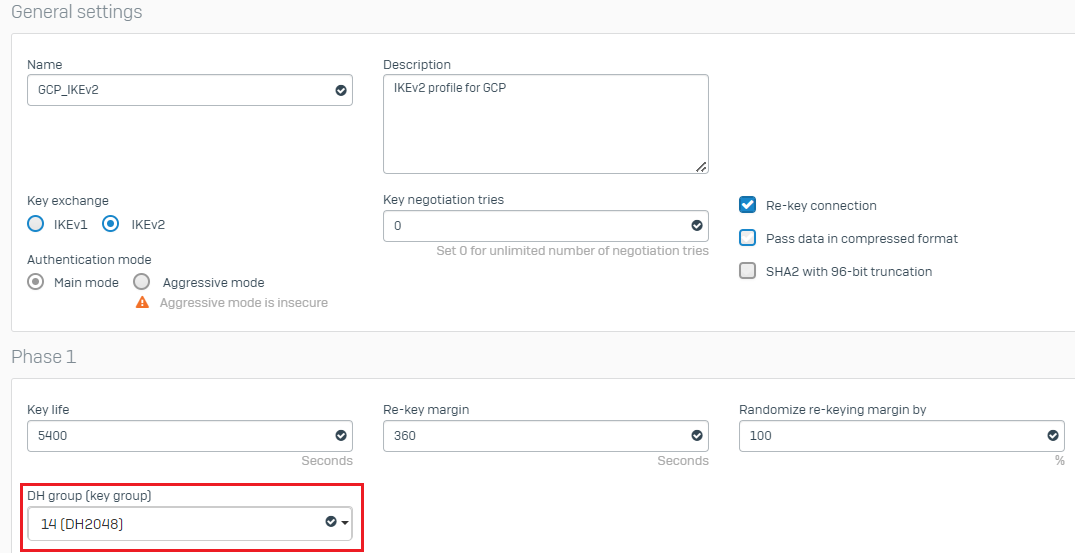
-
Go to Site-to-site VPN > IPsec and click Add under the IPsec connections section to create a new IPsec VPN tunnel.
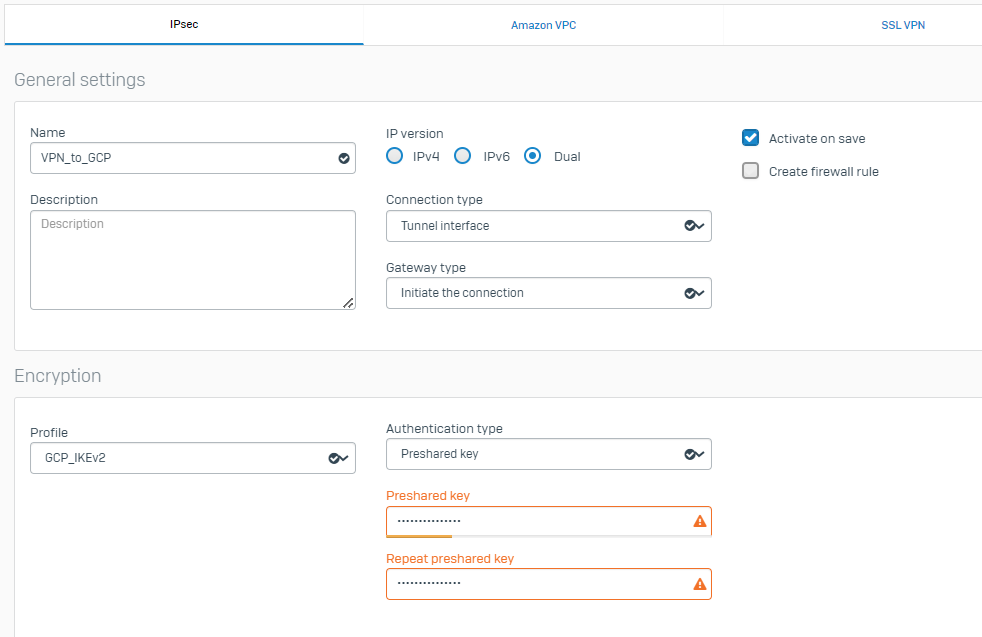
- Enter the following details for each parameter:
- Name: Enter the name of the VPN tunnel.
- Connection type: Select Tunnel interface to configure this as a route-based VPN tunnel.
- IP version: Select Dual to consider local and remote network subnets as Any.
- Gateway type: Initiate the connection.
- Activate on save: This option can be turned on, but it isn’t mandatory.
- Profile: Select GCP_IKEv2 profile.
- Authentication type: Select the Preshared key and enter the same One used in the GCP VPN tunnel configuration.
- Listening interface: Select the WAN interface of Sophos Firewall.
- Gateway address: Enter the public IP address of the GCP VPN gateway.
- Local ID type: IP address
- Local ID: Enter the public IP address associated with the Sophos Firewall’s on-premises network.
Click Save.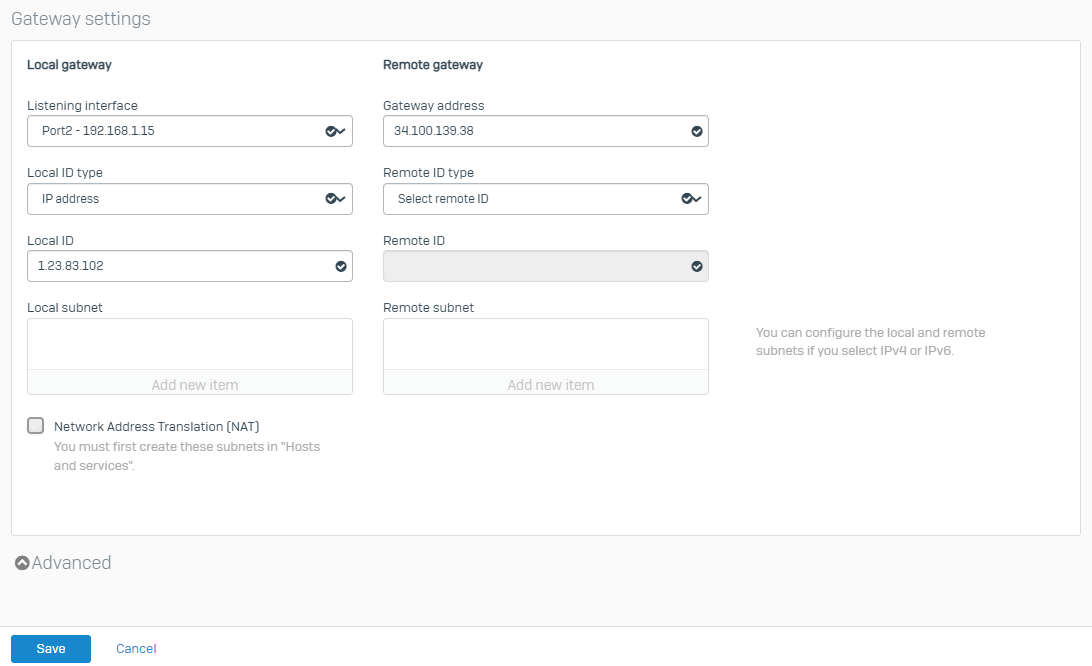
This will connect the IPsec VPN tunnel and show green status.
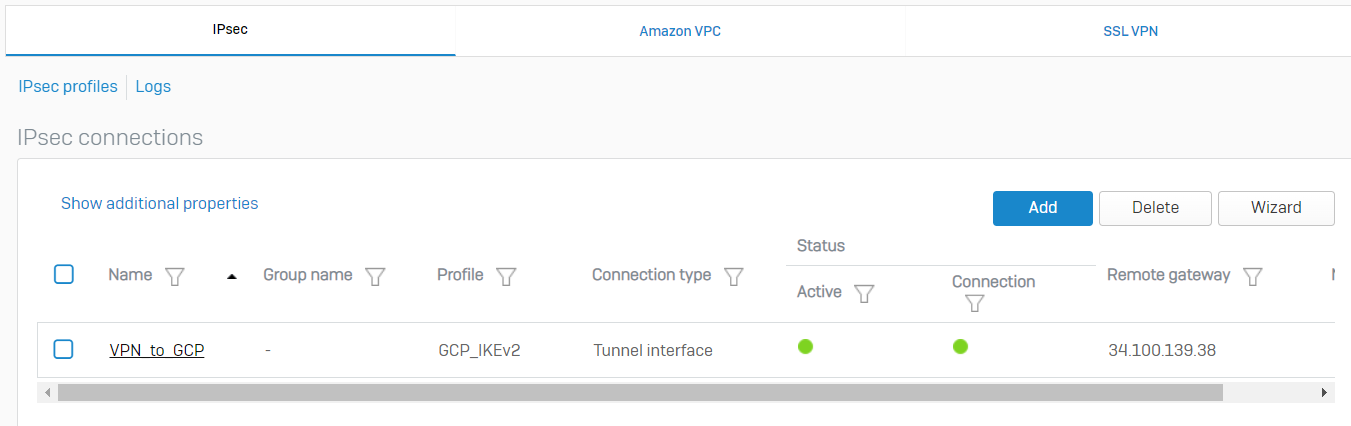
-
Go to CONFIGURE > Network > Interfaces, which will show you the xfrm interface automatically created for this VPN tunnel.
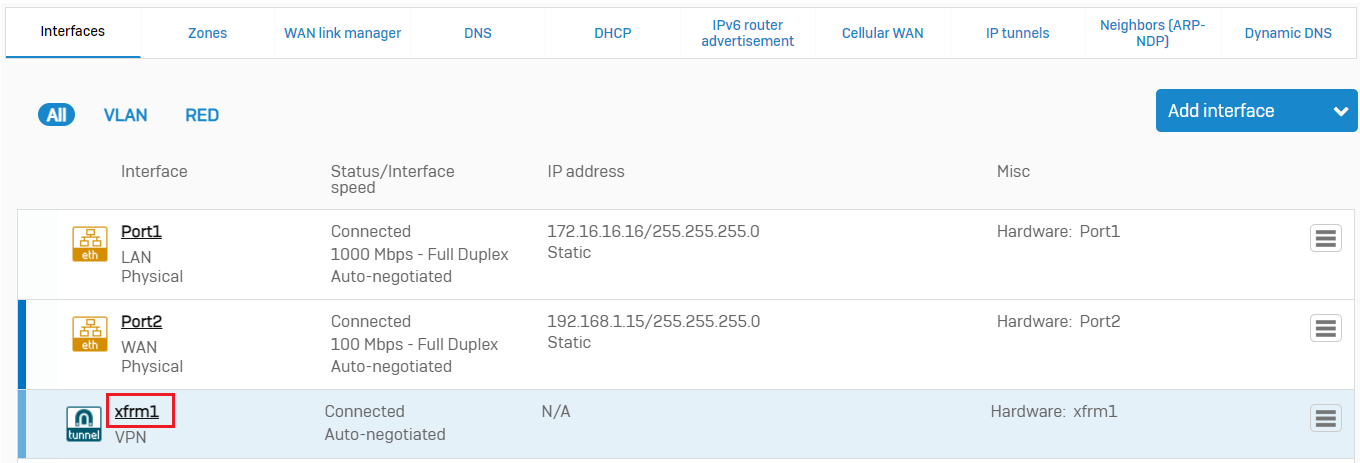
Click the XFRM interface and configure a dummy private IPv4 address that does not overlap with your existing on-premises or GCP-side VPC network.
Click Save.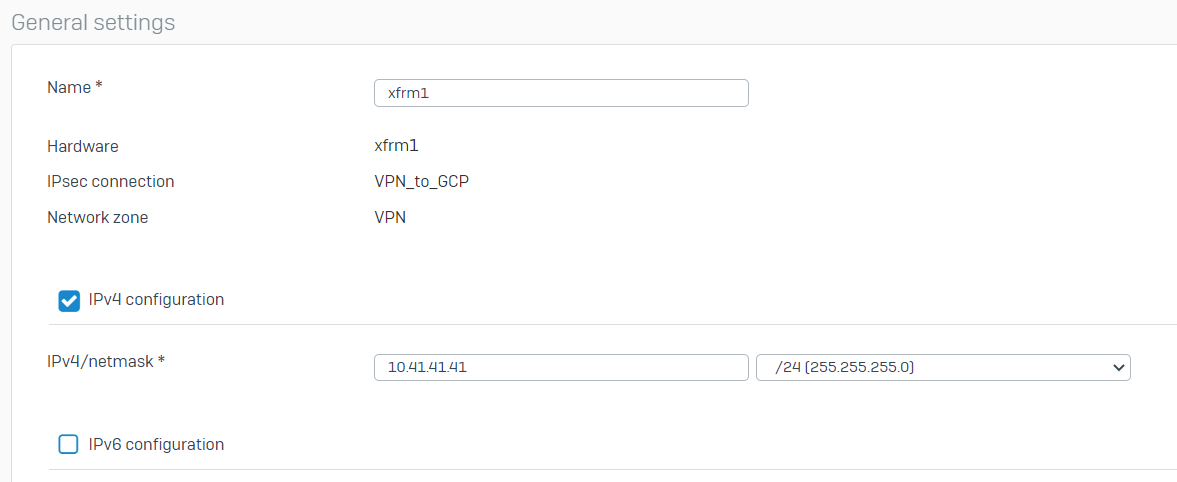
- Go to CONFIGURE > Routing > Static routes and click Add under the IPv4 unicast route.
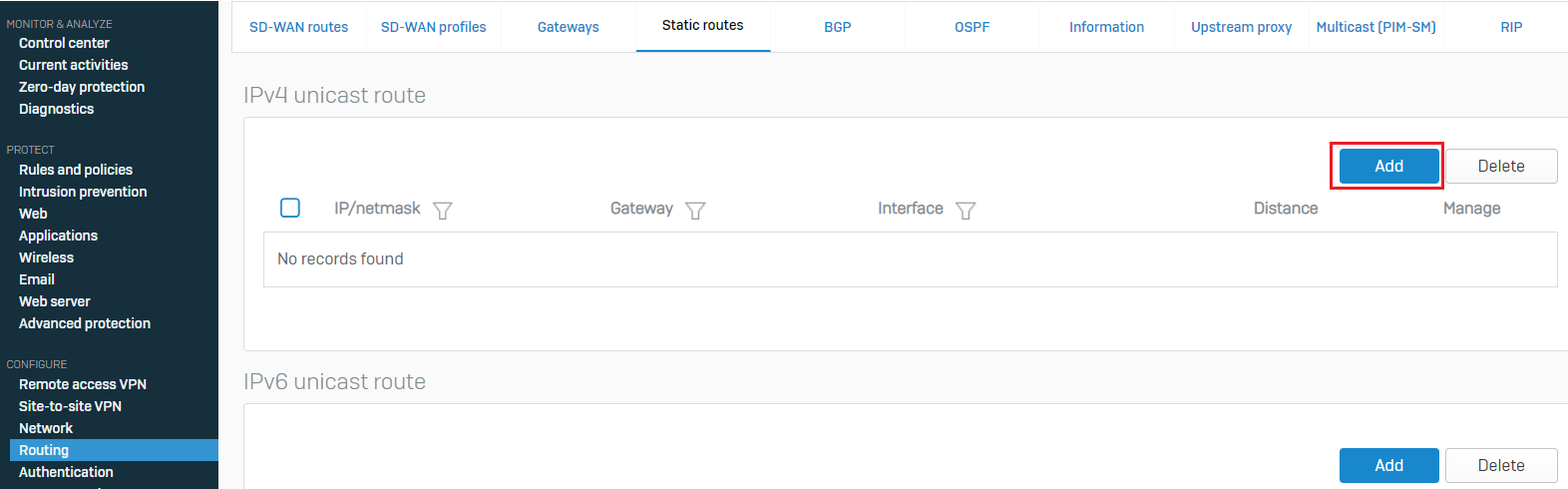
Enter the Destination IP as the network IP address of the GCP-side VPC network with the correct CIDR block selected.
Select the XFRM interface from the list of interfaces and click Save.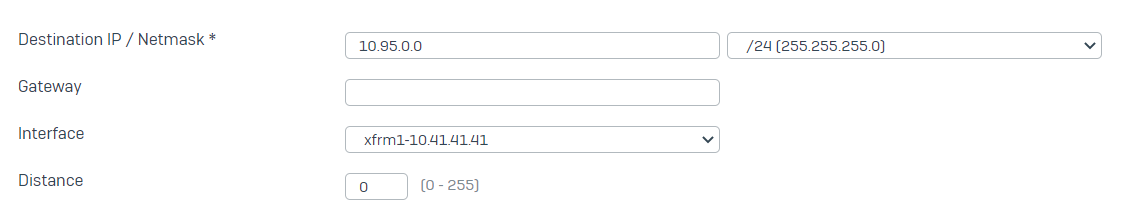
- Go to PROTECT > Rules and policies > Firewall rules and click Add firewall rule > New firewall rule.
Enter an appropriate name to the firewall rule, configure Action as Accept, and turn on the Log firewall traffic option.
Configure Source zones as LAN and/or Wi-Fi.
Configure and select the IP host network objects created for the on-premises local networks as the Source networks and devices.
Configure Destination zones as VPN.
Configure and select the IP host network object for the GCP side VPC network as the Destination network.
You may optionally turn on authentication and security/scanning features such as AV, IPS, and synchronized security.
Click Save.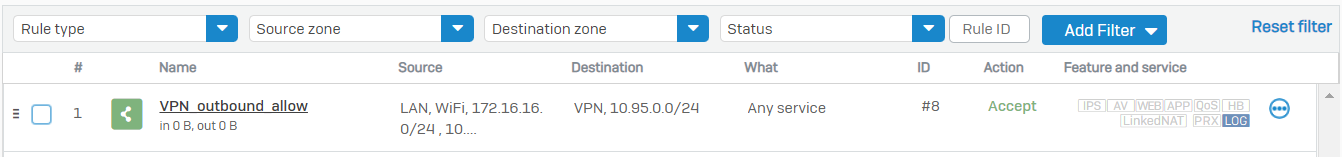
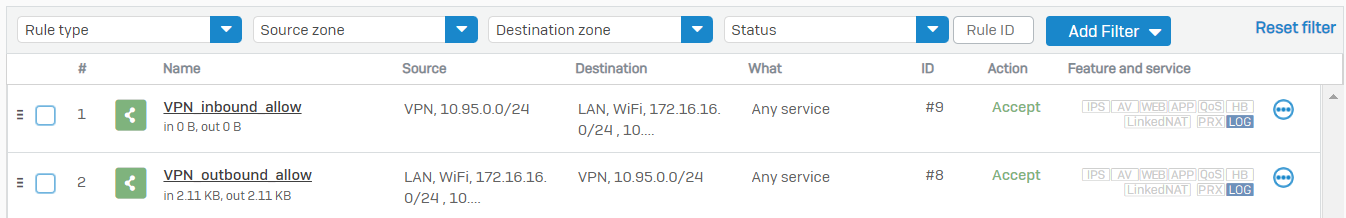
You can create a similar rule for the inbound traffic with the source and destination zones, and networks interchanged compared to the previous rule so that the traffic initiated from the GCP side can successfully communicate with Sophos Firewall local resources.
Related information
Revamped
[edited by: Erick Jan at 7:23 AM (GMT -8) on 13 Dec 2024]
