Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Note: Make sure your Sophos Firewall time is correct to avoid potential Certificate Trust issues
Table of Contents
Overview:
This article describes the behavior of SSL VPN Remote Access when “connection reset” is observed in the logs of client machine, resulting in the connection failing for the SSL VPN.
Scenario:
SSL VPN is not connecting and continuously throwing errors below:
Sample Logs(collected from client system):
OpenVPN 2.3.8 i686-w64-mingw32 [SSL (OpenSSL)] [LZO] [IPv6] built on Jul 3 2017
library versions: OpenSSL 1.0.2l 25 May 2017, LZO 2.09
Enter Management Password:
MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25340
Need hold release from management interface, waiting...
MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25340
MANAGEMENT: CMD 'state on'
MANAGEMENT: CMD 'log all on'
MANAGEMENT: CMD 'hold off'
MANAGEMENT: CMD 'hold release'
MANAGEMENT: CMD 'username "Auth" "sophos.tech"'
MANAGEMENT: CMD 'password [...]'
Socket Buffers: R=[65536->65536] S=[65536->65536]
Attempting to establish TCP connection with [AF_INET]103.121.74.189:8443 [nonblock]
MANAGEMENT: >STATE:1642056545,TCP_CONNECT,,,,,,
TCP connection established with [AF_INET]103.121.74.189:8443
TCPv4_CLIENT link local: [undef]
TCPv4_CLIENT link remote: [AF_INET]103.121.74.189:8443
MANAGEMENT: >STATE:1642056546,WAIT,,,,,,
MANAGEMENT: >STATE:1642056546,AUTH,,,,,,
TLS: Initial packet from [AF_INET]103.121.74.189:8443, sid=bbaa28f6 00afb0f0
WARNING: this configuration may cache passwords in memory --use the auth-nocache option to prevent this
VERIFY OK: depth=1, C=IN, ST=NA, L=NA, O=Sophos Pvt Ltd, OU=OU,
CN=Sophos_CA_C190XXXXXX, emailAddress=sophos@tech.com
VERIFY X509NAME OK: C=IN, ST=NA, L=NA, O=Sophos Pvt Ltd, OU=OU,
CN=SophosApplianceCertificate_C190C4QRBMFTD90, emailAddress=sophos@tech.com
VERIFY OK: depth=0, C=IN, ST=NA, L=NA, O=Sophos Pvt Ltd, OU=OU,
CN=SophosApplianceCertificate_C190C4QRBMFTD90, emailAddress=sophos@tech.com Thu Jan 13 12:19:07 2022 Connection reset, restarting [0]
Thu Jan 13 12:19:07 2022 SIGUSR1[soft,connection-reset] received, process restarting
Thu Jan 13 12:19:07 2022 MANAGEMENT: >STATE:1642056547,RECONNECTING,connection-reset,,,,,
Thu Jan 13 12:19:07 2022 Restart pause, 5 second(s)
Socket Buffers: R=[65536->65536] S=[65536->65536]
Attempting to establish TCP connection with [AF_INET]103.121.74.189:8443 [nonblock] MANAGEMENT: >STATE:1642056552,TCP_CONNECT,,,,,,
What to do:
- Confirm that the ports are not conflicting. The default port for SSL VPN remote access is 8443. If this port is being used somewhere else, it may create conflict and not allow to connect the
- Check the logs on Sophos Firewall. The log file is – “sslvpn.log”, replicate the issue by connecting the VPN and check the live logs using the command below:
SFVUNL_SO01_SFOS 18.5.2 MR-2-Build380# tail -f sslvpn.log
- There might be an error related to the certificate if there are no errors related to the configuration or conflicting ports.
Sample Logs(collected from Sophos Firewall):
Thu Jan 13 12:22:19 2022 [5483] ::ffff:115.98.235.160 TLS: Initial packet from [AF_INET6]::ffff:115.98.235.160:61872, sid=8e9030da 0126b821
Thu Jan 13 12:22:19 2022 [5483] ::ffff:115.98.235.160 VERIFY ERROR: depth=1, error=self signed certificate in certificate chain: C=IN, ST=NA, L=NA, O=Sophos Pvt Ltd, OU=OU,
CN=Sophos_CA_C190XXXXXX, emailAddress=sophos@tech.com
Thu Jan 13 12:22:19 2022 [5483] ::ffff:115.98.235.160 TLS_ERROR: BIO read tls_read_plaintext error: error:14089086:SSL routines:ssl3_get_client_certificate:certificate verify failed
Thu Jan 13 12:22:19 2022 [5483] ::ffff:115.98.235.160 TLS Error: TLS object -> incoming plaintext read error
Thu Jan 13 12:22:19 2022 [5483] ::ffff:115.98.235.160 TLS Error: TLS handshake failed
Thu Jan 13 12:22:19 2022 [5483] ::ffff:115.98.235.160 Fatal TLS error (check_tls_errors_co), restarting
Thu Jan 13 12:22:19 2022 [5483] ::ffff:115.98.235.160 SIGUSR1[soft,tls-error] received, client-instance restarting
Thu Jan 13 12:22:25 2022 [5483] TCP connection established with [AF_INET6]::ffff:115.98.235.160:61873
Thu Jan 13 12:22:26 2022 [5483] ::ffff:115.98.235.160 TLS: Initial packet from
[AF_INET6]::ffff:115.98.235.160:61873, sid=00a4c5a1 a472b11e
Thu Jan 13 12:22:27 2022 [5483] ::ffff:115.98.235.160 VERIFY ERROR: depth=1, error=self signed certificate in certificate chain: C=IN, ST=NA, L=NA, O=Sophos Pvt Ltd, OU=OU,
CN=Sophos_CA_C190XXXXXX, emailAddress=sophos@tech.com
Thu Jan 13 12:22:27 2022 [5483] ::ffff:115.98.235.160 TLS_ERROR: BIO read tls_read_plaintext error: error:14089086:SSL
routines:ssl3_get_client_certificate:certificate verify failed
Thu Jan 13 12:22:27 2022 [5483] ::ffff:115.98.235.160 TLS Error: TLS object -> incoming plaintext read error
Thu Jan 13 12:22:27 2022 [5483] ::ffff:115.98.235.160 TLS Error: TLS handshake failed
Thu Jan 13 12:22:27 2022 [5483] ::ffff:115.98.235.160 Fatal TLS error (check_tls_errors_co), restarting
Thu Jan 13 12:22:27 2022 [5483] ::ffff:115.98.235.160 SIGUSR1[soft,tls-error] received, client-instance restarting
Thu Jan 13 12:22:32 2022 [5483] TCP connection established with [AF_INET6]::ffff:115.98.235.160:61874
We can see it’s the error for certificate verification failure.
Fix:
- Check which certificate is used in the SSL VPN configuration by navigating to VPN > Show VPN.
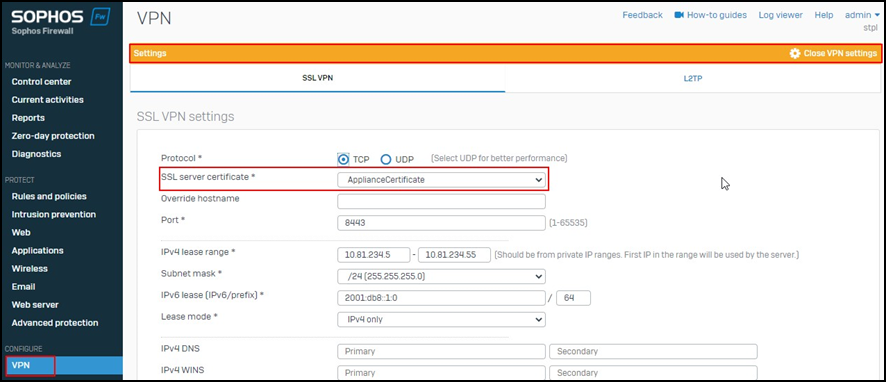
- Check the default certificate. As shown below, many details may not be filled correctly in the certificate and that could be one of the reasons for the certificate check failing.
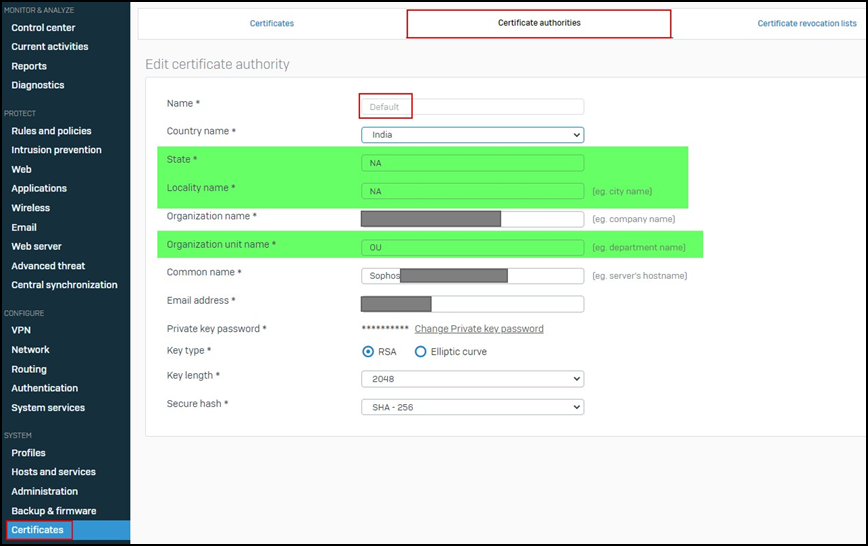
- Please update the certificate with correct information and regenerate the certificate following this KBA - https://doc.sophos.com/nsg/sophos-firewall/21.0/Help/en-us/webhelp/onlinehelp/AdministratorHelp/Certificates/CertificateAuthorities/CertificatesDefaultCAUpdate/index.html
Note: Any kind of changes in certificate would result in service restart where we have used that certificate.
- The screenshot below shows the result after updating the certificate and the VPN connects after certificate regeneration.
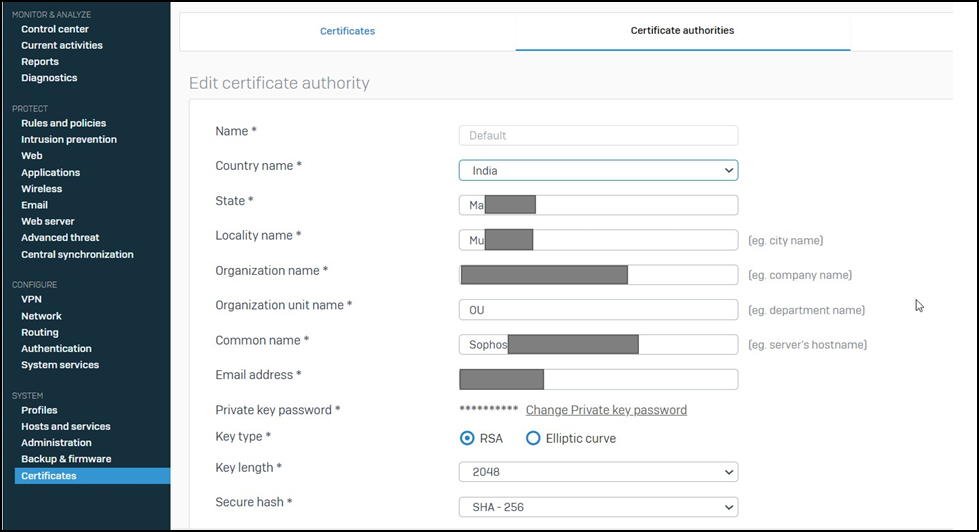
Sample Working Logs:
Thu Jan 13 13:23:19 2022 [1014] Closing TUN/TAP interface Thu Jan 13 13:23:19 2022 [1014] /bin/ip addr del dev tun0 10.81.234.5/24 Thu Jan 13 13:23:19 2022 [1014] /bin/ip -6 addr del 2001:db8::1:0/64 dev tun0 Thu Jan 13 13:23:19 2022 [1014] PLUGIN_CLOSE: /lib/openvpn-plugin-utm.so Thu Jan 13 13:23:19 2022 [1014] SIGTERM[hard,] received, process exiting Thu Jan 13 13:23:20 2022 [2733] OpenVPN 2.3.6 i486-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on Apr 23 2021 Thu Jan 13 13:23:20 2022 [2733] library versions: OpenSSL 1.0.2u-fips 20 Dec 2019, LZO 2.09 Thu Jan 13 13:23:20 2022 [2733] MANAGEMENT: client_uid=0 Thu Jan 13 13:23:20 2022 [2733] MANAGEMENT: unix domain socket listening on /tmp/openvpn_mgmt Thu Jan 13 13:23:20 2022 [2733] cleanup success Thu Jan 13 13:23:20 2022 [2733] WARNING: using --duplicate-cn and --client-config-dir together is probably not what you want Thu Jan 13 13:23:20 2022 [2733] WARNING: --ifconfig-pool-persist will not work with --duplicate-cn Thu Jan 13 13:23:20 2022 [2733] NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Thu Jan 13 13:23:20 2022 [2733] PLUGIN_INIT: POST /lib/openvpn-plugin-utm.so '[/lib/openvpn-plugin- utm.so]' intercepted=PLUGIN_AUTH_USER_PASS_VERIFY|PLUGIN_CLIENT_CONNECT|PLUGIN_CLIENT_DI SCONNECT Thu Jan 13 13:23:20 2022 [2733] Diffie-Hellman initialized with 2048 bit key Thu Jan 13 13:23:20 2022 [2733] WARNING: file '/conf/certificate/private/ApplianceCertificate.key' is group or others accessible Thu Jan 13 13:23:20 2022 [2733] WARNING: experimental option --capath /conf/certificate/openvpn Thu Jan 13 13:23:20 2022 [2733] Socket Buffers: R=[87380->87380] S=[16384->16384] Thu Jan 13 13:23:20 2022 [2733] TUN/TAP device tun0 opened Thu Jan 13 13:23:20 2022 [2733] TUN/TAP TX queue length set to 1000 Thu Jan 13 13:23:20 2022 [2733] do_ifconfig, tt->ipv6=1, tt->did_ifconfig_ipv6_setup=1 Thu Jan 13 13:23:20 2022 [2733] /bin/ip link set dev tun0 up mtu 1500 Thu Jan 13 13:23:20 2022 [2733] /bin/ip addr add dev tun0 10.81.234.5/24 broadcast 10.81.234.255 Thu Jan 13 13:23:20 2022 [2733] /bin/ip -6 addr add 2001:db8::1:0/64 dev tun0 Thu Jan 13 13:23:20 2022 [2733] CSC service status updated to RUNNING Thu Jan 13 13:23:20 2022 [2733] Listening for incoming TCP connection on [undef] Thu Jan 13 13:23:20 2022 [2733] TCPv6_SERVER link local (bound): [undef] Thu Jan 13 13:23:20 2022 [2733] TCPv6_SERVER link remote: [undef] Thu Jan 13 13:23:20 2022 [2733] MULTI: multi_init called, r=256 v=256 Thu Jan 13 13:23:20 2022 [2733] IFCONFIG POOL IPv6: (IPv4) size=50, size_ipv6=65536, netbits=64, base_ipv6=2001:db8::1:1 Thu Jan 13 13:23:20 2022 [2733] IFCONFIG POOL: base=10.81.234.6 size=50, ipv6=1 Thu Jan 13 13:23:20 2022 [2733] IFCONFIG POOL LIST Thu Jan 13 13:23:20 2022 [2733] MULTI: TCP INIT maxclients=330 maxevents=334 Thu Jan 13 13:23:20 2022 [2733] Initialization Sequence Completed Thu Jan 13 13:25:49 2022 [2733] TCP connection established with [AF_INET6]::ffff:115.98.235.160:62896 Thu Jan 13 13:25:50 2022 [2733] ::ffff:115.98.235.160 TLS: Initial packet from [AF_INET6]::ffff:115.98.235.160:62896, sid=353d0f78 06d1ab01
______________________________________________________________________________________________________________________________________
Updated links to latest
[edited by: Raphael Alganes at 3:11 PM (GMT -8) on 19 Nov 2024]

