Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
This recommended read describes the troubleshooting steps & possible solutions when you get an error "Synchronization with server failed" while unable to sync the license of a Sophos device.
Scenario
- Not able to sync the purchased license on Sophos Firewall.
- Getting error "Synchronization with server failed" while syncing purchased license.
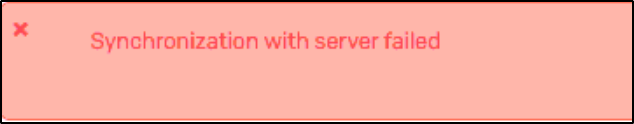
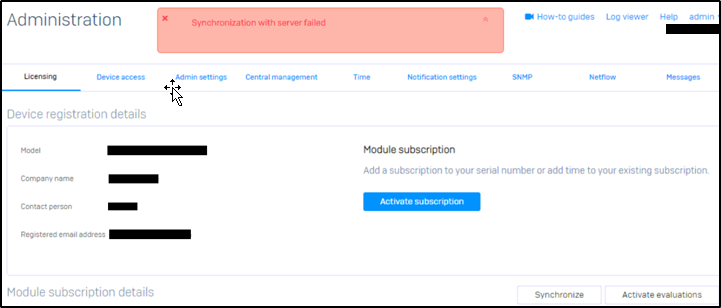
What to do
Step: 1 Correct Activation Key
- Please use the correct activation key given by the licensing team – when syncing the license for the first time on your new device.
- Check license details on the mySophos account portal for a specific appliance and confirm those are registered/displayed correctly. The below steps will help you with the path to check the same:
- Sign in to the Licensing Portal:
- For Customers , For Partners
- Go to My Sophos > Network Protection > View Devices > Search for the appliance's serial number and check the subscription validity.
Note: For more info about licenses, see - https://docs.sophos.com/central/customer/help/en-us/LicensingGuide/FirewallLicenses/index.html
Step: 2 Internet Connectivity
- Check that the appliance has good internet connectivity.
- Try to sync the license, verify the error on GUI, and collect the logs via SSH
- GUI > Administration> Licensing > click Synchronize: Wait until you see the error.
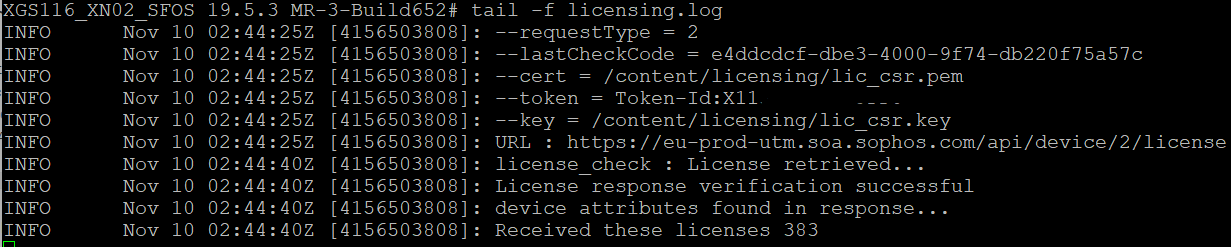
- SSH > Login > 5. Device Management > 3. Advanced Shell > Use the below command to see the logs of license sync.
tail -f /log/licensing.log
Note: Start the log file using the above command and sync the license to get the appropriate logs.
- To retrieve the license and sync the Sophos Firewall try to contact any of the following domains/servers:
- eu-prod-utm.soa.sophos.com
- eu-prod-csr.soa.sophos.com
- From the logs, you'll get the "server name" from which the device is fetching the licensing info. Note - The keyword to find the server-name is "URL"
- Do the nslookup to the server name and check the tcpdump to confirm the connectivity status.
Command to do lookup -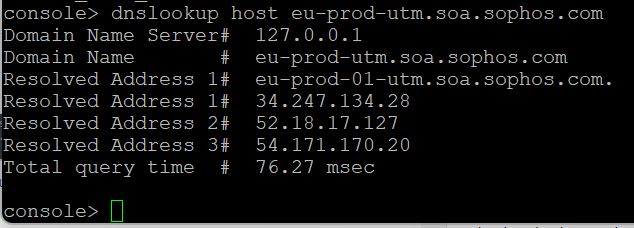
- Command to check tcpdump -
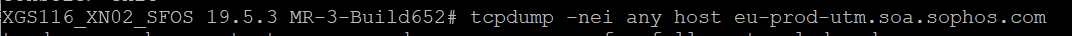
- To confirm the connectivity with the server, you may check the telnet and openssl connection with the below commands:
# telnet eu-prod-utm.soa.sophos.com 443 # openssl s_client -connect eu-prod-utm.soa.sophos.com:443
- If there's no issue with the connectivity, you may get the below outcome:
# openssl s_client -connect eu-prod-utm.soa.sophos.com:443 CONNECTED(00000003) depth=2 C = BE, O = GlobalSign nv-sa, OU = Root CA, CN = GlobalSign Root CA verify return:1 depth=1 C = BE, O = GlobalSign nv-sa, CN = GlobalSign Organization Validation CA - SHA256 - G2 verify return:1 depth=0 C = GB, ST = Oxfordshire, L = Abingdon, O = Sophos Ltd., CN = *.soa.sophos.com verify return:1 --- Certificate chain 0 s:/C=GB/ST=Oxfordshire/L=Abingdon/O=Sophos Ltd./CN=*.soa.sophos.com .. i:/C=BE/O=GlobalSign nv-sa/CN=GlobalSign Organization Validation CA - SHA256 - G2 1 s:/C=BE/O=GlobalSign nv-sa/CN=GlobalSign Organization Validation CA - SHA256 - G2 .. i:/C=BE/O=GlobalSign nv-sa/OU=Root CA/CN=GlobalSign Root CA --- Server certificate -----BEGIN CERTIFICATE----- MIIHQTCCBimgAwIBAgIMO+m+m/tuZVmw8GYUMA0GCSqGSIb3DQEBCwUAMGYxCzAJ BgNVBAYTAkJFMRkwFwYDVQQKExBHbG9iYWxTaWduIG52LXNhMTwwOgYDVQQDEzNH bG9iYWxTaWduIE9yZ2FuaXphdGlvbiBWYWxpZGF0aW9uIENBIC0gU0hBMjU2IC0g RzIwHhcNMTgwMTMwMTAzMTAxWhcNMjEwMzA2MjA0MTAxWjBnMQswCQYDVQQGEwJH QjEUMBIGA1UECBMLT3hmb3Jkc2hpcmUxETAPBgNVBAcTCEFiaW5nZG9uMRQwEgYD VQQKEwtTb3Bob3MgTHRkLjEZMBcGA1UEAwwQKi5zb2Euc29waG9zLmNvbTCCASIw DQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKvs9pl1VOTx5jRBdruY4kA6BASe Mcdm8gL6uCXQrubH4PZ/zuLV5tKdaAqoEIpJd2Ry9Fpmyw5zhqcZOFhngD0a+Ey8 EjCCTnMBhSAtVNO8e+Q4pQsJNiTIkipMh2cSpNGxFbaEM/q7xCKNoQgl22tdtHf8 qmW+HUAuZQm0AG678JI1bH7xE4gXieqn5R7TdJ8k5XcCzwz1EOXqf0qwkF1XmKA4 8b+dTAJZvAJzKNv7H/rBHcvtM/1fYHrLudrGb8h5mVg0EpbrKVv7dNwEZ91LfN91 Whwrko5iVZ8JaaxiSno2/DjR2Lzk4FQhOhIXUw2XRAX3cgS13fYGEVgNGHcCAwEA AaOCA+wwggPoMA4GA1UdDwEB/wQEAwIFoDCBoAYIKwYBBQUHAQEEgZMwgZAwTQYI gBSW3mHxvRwWKVMcwMx9O4MAQOYafDCCAfcGCisGAQQB1nkCBAIEggHnBIIB4wHh AHYA3esdK3oNT6Ygi4GtgWhwfi6OnQHVXIiNPRHEzbbsvswAAAFhRp670AAABAMA RzBFAiANenoxg7rJCcsh2qvqrrzbDugyVuN/lwGq4040Z1WQ3wIhAMJI4WaoXNFr +4AB40U9pnsIvWz1TZaCPmo5XTIzJqbuAHYAVhQGmi/XwuzT9eG9RLI+x0Z2ubyZ EVzA75SYVdaJ0N0AAAFhRp68JgAABAMARzBFAiB9aKYcJowWzqr+3WXqBzpJihIW L9cdiNLomojqxZbQKwIhAPiQ56UQoTdpYfTa7DYdsPUgB1rRjrMhj3J3UL6PGV4a AHYApLkJkLQYWBSHuxOizGdwCjw1mAT5G9+443fNDsgN3BAAAAFhRp6/EgAABAMA RzBFAiAn5qxiaM3T7PrTsGCZ2c+9f+ym9OXtEjxuj8WWTficUgIhAKXrz4eAE7rH GKujyICgs8uqmcpRJjjcnw3FmoSOiH3tAHcA7ku9t3XOYLrhQmkfq+GeZqMPfl+w ctiDAMR7iXqo/csAAAFhRp7BggAABAMASDBGAiEAhW3V9icWo6SBIgeJVgjo6z3r KlpTMq3X5+5ThVEq9nECIQCktZCw3PVghPU2UVIxrp/k2DUa6MOX5BE9V0ve+flY jTANBgkqhkiG9w0BAQsFAAOCAQEAvJHsCp1fcvAfxbf0LCFJu9hIfFtM4J3pfSiI voW9IV2bGM2xRmtA5NToFekN/vX2HrYhB0rqME2+FI5jLpRO2WNBoGWxQSB5LF7m w7n+gkoIRewoGpdA47JT+0zfIplNVG851Ju274WngdCfDZdBtiqQn6L7Eq61IrzU tdlGS5ow2pQfWuMLc18mGzNj8q2Ijvo3q15ZK7R83unu3FrV58RukQovp3qew+ws wlvUY3GRap3Xyk5WtDPVSBJNw2iYejWRdj4axagqUj6IKqhZnBwYgrmYHq0DPHeI 2O+m7NXKSN1PY943uoawrjsSThW84uR0oyHPN8+UOJjCFx04AQ== -----END CERTIFICATE----- subject=/C=GB/ST=Oxfordshire/L=Abingdon/O=Sophos Ltd./CN=*.soa.sophos.com issuer=/C=BE/O=GlobalSign nv-sa/CN=GlobalSign Organization Validation CA - SHA256 - G2 --- No client certificate CA names sent Peer signing digest: SHA1 Server Temp Key: ECDH, P-521, 521 bits --- SSL handshake has read 3605 bytes and written 552 bytes --- New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-SHA384 Server public key is 2048 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: ........... Protocol. : TLSv1.2 ........... Cipher : ECDHE-RSA-AES256-SHA384 ........... Session-ID: 3C3C000060F56ACD91AB1C424061500D598251B31BCBBD6F6F3CDF11100E02B0 ........... Session-ID-ctx: Master-Key: A8F2B1B280A9024573DE727DADBF87019FE7AC991A6B7B 3682BFC65818BC47973033AACBDE25280367B5FE61456EADBF ........... Key-Arg.. : None ........... PSK identity: None ........... PSK identity hint: None ........... SRP username: None ........... Start Time: 1523308380 ........... Timeout.. : 300 (sec) ........... Verify return code: 0 (ok).
- If you observe connectivity-related issues, please see the common reasons below:
- The upstream device is blocking the Traffic.
- ISP is blocking/ not allowing the connection.
Step: 3 Sync License
- If you have multiple ISPs, you can sync the license by using either of the ISP connections to figure out the issue either by CLI or UI using the below options:
- Create an SDWAN route to route the Traffic to the licensing servers through a specific ISP.
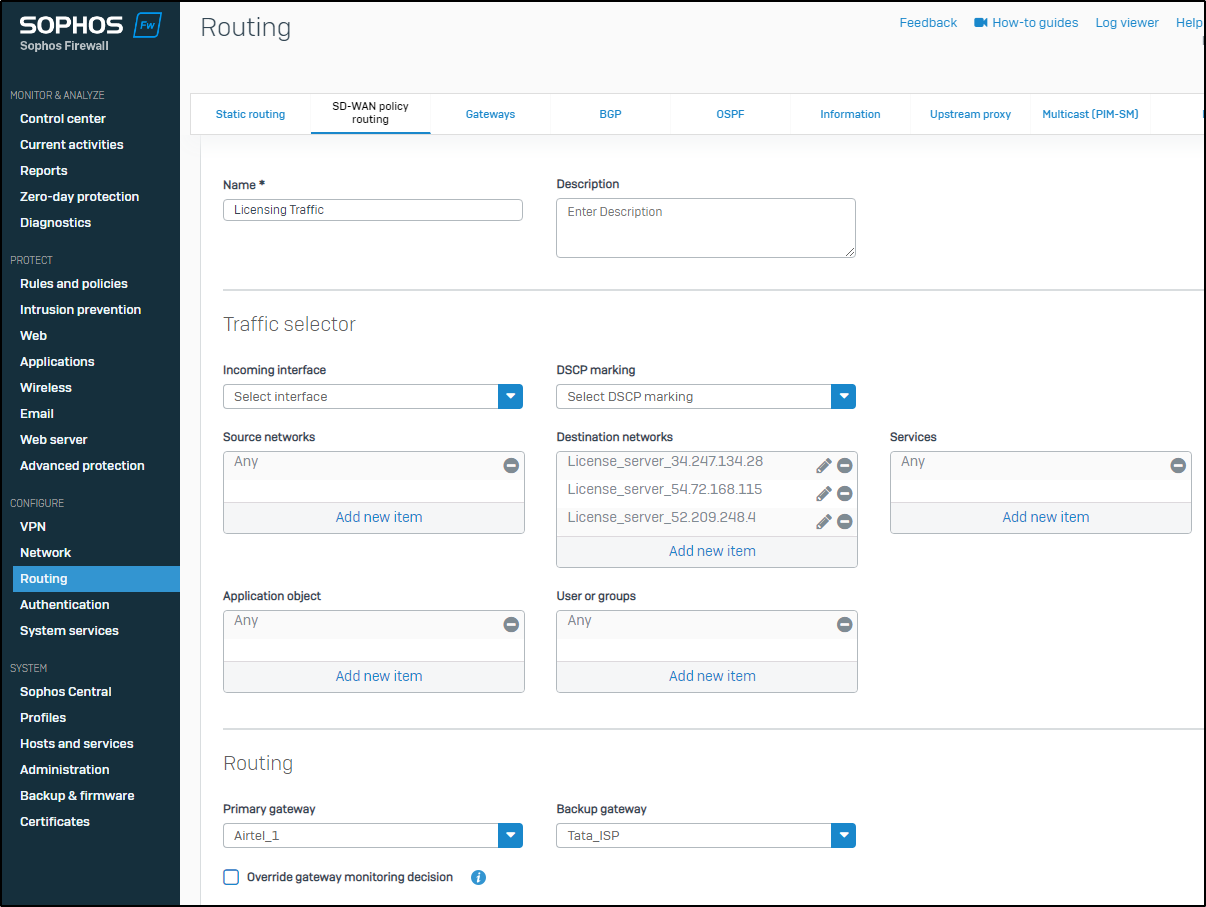
- Once the SD-WAN route is created, we would also need to enable the system-generated Traffic for SD-WAN traffic.
- Please refer doc.sophos.com/.../index.html
- You can also create the SYSTEM NAT from the CLI to pass the Traffic from a specific ISP. The options to add the sys-traffic-nat would be available in the command guide. If required, reach out to Sophos support.
NAT policy for system originated Traffic --------------------- . . Destination Network.... Destination Netmask.... Interface...... SNAT IP ....... 52.209.248.4. . . . . . . 255.255.255.255. . . . . . . . . . . . .14.139.61.129 ....... 54.72.168.115. . . . . . 255.255.255.255. . . . . . . . . . . . .14.139.61.129 ....... 34.249.219.184......... 255.255.255.255....................... 14.139.61.129
Step: 4 Certificate Error
- If there are any errors related to the invalid certificate or certificate signing failures, check below:
- Go to the Certificates > Certificates Authorities > Confirm the Default certificate is filled up correctly with all the details.
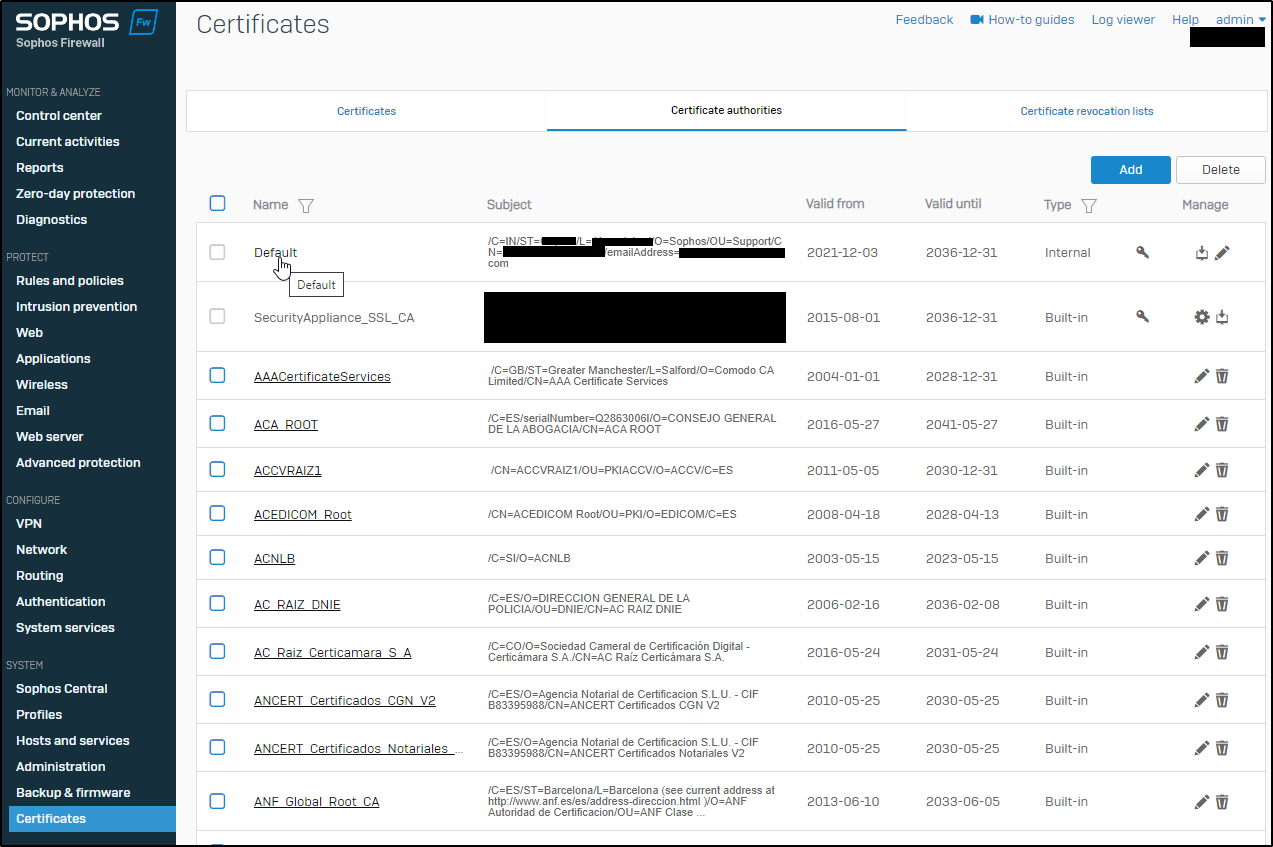
- Ensure that the date on the device is correctly set.
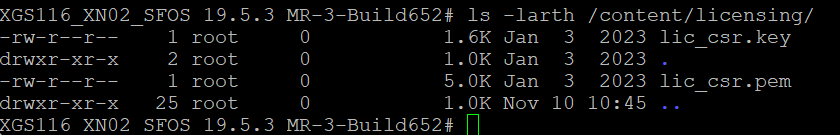
- Verify if the certificate and its key are present. Check the key files using the below commands:
#.ls -larth /content/licensing/
- The output of above command would look as follows:
- If the internet connection is OK with the device, and the server connectivity is perfect from a device to the licensing server, start the licensing.log file and then sync the license from GUI to see the accurate logs.
- Apart from licensing.log, you can check - csc-debug, applog.log.
Sample logs:
INFO Jun 25 17:00:15 [0]: --requestType = 2
INFO Jun 25 17:00:15 [0]: --lastCheckCode = 46dbf4cf-b4b0-43b1-bf99-24c1f7de0ab3
INFO Jun 25 17:00:15 [0]: --cert = /content/licensing/lic_csr.pem
INFO Jun 25 17:00:15 [0]: --token = Token-Id: C320A0000000000
INFO Jun 25 17:00:15 [0]: --key = /content/licensing/lic_csr.key
INFO Jun 25 17:00:15 [0]: URL : https://eu-prod-utm.soa.sophos.com/api/device/2/license
INFO Jun 25 17:00:26 [0]: response : {"errorCode":"ITSERVICELAYER_CLIENT_AUTHENTICATION_ERROR","message":"Authentication failed","statusCode":403,"trackingId":"a0430985-badc-4423-8865-bb252fe849f6"}
ERROR Jun 25 17:00:26 [0]: license_check failed : Authentication failed
ERROR Jun 25 17:00:26 [0]: licensing_do_licensecheck() :parsing response failed...
####################################################
generate certificate signing request (CSR) Thu Jun 25 17:00:27 IST 2020
Thu Jun 25 17:00:28 IST 2020 certificate signing request generated with status :: 0
####################################################
INFO Jun 25 17:00:28 [0]: --requestType = 4
INFO Jun 25 17:00:28 [0]: --serial = C320A0000000000
INFO Jun 25 17:00:28 [0]: --deviceid = 68bbbf67aea2179b44673104389b4b4288f7
INFO Jun 25 17:00:28 [0]: --cert = /_conf/certificate/licensing/mfgr_vendor_AM.pem
INFO Jun 25 17:00:28 [0]: --key = /_conf/certificate/licensing/mfgr_vendor_AM.key
INFO Jun 25 17:00:28 [0]: URL : https://eu-prod-csr.soa.sophos.com/api/certificate/1/signing
INFO Jun 25 17:00:28 [0]: certificate_signing_request() : request : { "serialNumber":"C0A0B74XT26MYED", "deviceId":"68bbbf67aea2179b44673104389b4b4288f7", "certificateSigningRequest":"-----BEGIN CERTIFICATE REQUEST-----
MIIDIjCCAgoCAQAwgZcxCzAJBgNVBAYTAkdCMRQwEgYDVQQIDAtPeGZvcmRzaGly
ZTERMA8GA1UEBwwIQWJpbmdkb24xFDASBgNVBAoMC1NvcGhvcyBMdGQuMQwwCgYD
VQQLDANOU0cxGzAZBgNVBAMMElNGX0MwQTBCNzRYVDI2TVlFRDEeMBwGCSqGSIb3
DQEJARYPaW5mb0Bzb3Bob3MuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIB
CgKCAQEA658alZf50aD2k0YnFKIfRXY9zX6CJydKthgzSBSsEvAhW4ZsfUEP94+n
cQrJ03H6ydZ3TRoNZF9tUa2fEUo882yT+iKqeRO7zIo44QGXFu4uuf33gmTGyZR/
HCyNvRtnPoffKszUu9LcyXfB8bfsYdPOn77hd2AlnRi0OU5EJncyGI3si5vFIGqO
9lmAljIlhiDeuoUjxsYBCkKm+ezr9zwFTV8St8q/l2WMtj0Ld8yXVS/B96MvZECZ
1GOea1q3wmof6J0xPmHL0b6yJ2uR0kPwMvg6TWIO8EJRqCNWnj9p0eOdinHF9PHW
aK4v94/SJrVl5r7pCZVJiAsrqUSGnwIDAQABoEUwGgYJKoZIhvcNAQkCMQ0MC1Nv
cGhvcyBMdGQuMCcGCSqGSIb3DQEJDjEaMBgwCQYDVR0TBAIwADALBgNVHQ8EBAMC
BeAwDQYJKoZIhvcNAQELBQADggEBADPgNyafi3WUqIOlTMdVjLapnZb5C99ESBoE
sI1d57iKOsKFAQCdEMxom2cJA4B6MISeBSvu0laE95pNfkdbRV3H7+sZgVvc6+We
sy4HaXFBSEMXxOQTcr2gaLVDi+PJk4wPha/E2yiP4i4+fHMe8mvNQuFNivcBr7eX
gn8cQRYp6hGnbfZF2v5opkoWu4y4bKNwE9GxKkBqawDE1HKiG3PIOFqRcVjhA7iO
Q57Ku/U93AB6+E85ZLH76e0OSE+7LRpPSfwBjm0wfx1R9dmD6QVTLmIci/MBdXh6
lO96QOwY0zP9Au6+mHtXg2KWgtBXuoSfmQgIDhi5Nmnf8Bg4Mos=
-----END CERTIFICATE REQUEST-----
"}
INFO Jun 25 17:00:30 [0]: certificate_signing_request() : response :{"errorCode":"ITSERVICELAYER_DEVICE_NOTFOUND_ERROR","message":"Device not.found","statusCode":404,"trackingId":"b7b4f2b0-8ee9-4900-86a3-385cfb674e3d"}
ERROR Jun 25 17:00:30 [0]: Certificate signing Failed : Device not found...:(
ERROR Jun 25 17:00:30 [0]: certificate signing request() : parsing failed....
Jun 25 17:03:54 getpublickey success Key: 68bbbf67aea2179b44673104389b4b4288f7 Jun 25 17:04:08 lic_csr lock waiting Jun 25 17:04:08 lic_csr lock acquired Jun 25 17:04:09 getpublickey success Key: 68bbbf67aea2179b44673104389b4b4288f7 Jun 25 17:04:19 lic_csr lock released on fail Jun 25 17:04:20 System is not updated since 11 days Jun 25 17:04:20 MODULE :base Jun 25 17:04:21 getpublickey success Key: 68bbbf67aea2179b44673104389b4b4288f7 Jun 25 17:04:21 REG STATUS:Active###XG86###L0009704722###0001-01-01###2999-12-31###Purchased Jun 25 17:04:21 EXPIREDAYS :357773 Jun 25 17:04:21 MODULE :net Jun 25 17:04:21 getModuleInformation opcode failed Jun 25 17:04:21 REG STATUS :fail Jun 25 17:04:21 MODULE :web Jun 25 17:04:22 getModuleInformation opcode failed Jun 25 17:04:22 REG STATUS :fail Jun 25 17:04:22 MODULE :email: Jun 25 17:04:22 getModuleInformation opcode failed Jun 25 17:04:22 REG STATUS :fail Jun 25 17:04:22 MODULE :waf Jun 25 17:04:23 getModuleInformation opcode failed Jun 25 17:04:23 REG STATUS :fail Jun 25 17:04:23 MODULE :sand Jun 25 17:04:23 getModuleInformation opcode failed Jun 25 17:04:23 REG STATUS :fail Jun 25 17:04:23 MODULE :esup Jun 25 17:04:23 getModuleInformation opcode failed Jun 25 17:04:23 REG STATUS :fail Jun 25 17:04:23 MODULE :epsup Jun 25 17:04:24 getModuleInformation opcode failed Jun 25 17:04:24 REG STATUS :fail Jun 25 17:04:24 MODULE EXPIRE LIST : Jun 25 17:04:24 MODULE EXPIRE WITHIN 5 DAYS : Jun 25 17:04:24 MODULE EXPIRE WITHIN 10 DAYS : Jun 25 17:04:24 MODULE EXPIRE WITHIN 20 DAYS : Jun 25 17:04:24 Request type = 1 Jun 25 17:04:24 apiInterface:versionsupported: true. Jun 25 17:04:24 apiInterface:request mode -> 1804. Jun 25 17:04:24 apiInterface:Current ver :::'1702.1' Jun 25 17:04:24 apiInterface:entityjson::::::::HASH(0x9a58eb0) Jun 25 17:04:24 Info:: Transaction will not be rolled back for opcode lic_registrationinfo. If any operation fails, request is part of multiple request : Jun 25 17:04:26 Request type = 1 Jun 25 17:04:26 apiInterface:versionsupported: true. Jun 25 17:04:26 apiInterface:request mode -> 1803. Jun 25 17:04:26 apiInterface:Current ver :::'1702.1' Jun 25 17:04:26 apiInterface:entityjson::::::::HASH(0x9a58f60) Jun 25 17:04:26 info:: Transaction will not be rolled back for opcode lic_subinfo. If any operation fails, request is part of multiple request :
DEBUG Jun 25 17:04:19 [worker:1940]: request name = lic_csr
DEBUG Jun 25 17:04:19 [worker:1940]: # OPCODE Exited: 'lic_csr' with Status: '500'
INFO Jun 25 17:04:19 [daily_lic_check:1829]: create_act_out_perl_obj: varname=out
INFO Jun 25 17:04:19 [daily_lic_check:1829]: create_act_out_perl_obj: out.status=500
INFO Jun 25 17:04:19 [daily_lic_check:1829]: create_act_out_perl_obj: out.error=OK
INFO Jun 25 17:04:19 [daily_lic_check:1829]: opcode 'daily_lic_check': time taken: 26.308560849 seconds
INFO Jun 25 17:04:19 [daily_lic_check:1829]: opcode 'daily_lic_check': time taken: 26.308560849 seconds
DEBUG Jun 25 17:04:19 [worker:1829]: request name = daily_lic_check
DEBUG Jun 25 17:04:19 [worker:1829]: # OPCODE Exited: 'daily_lic_check' with Status: '500'
INFO Jun 25 17:04:19 [lic_check:1897]: create_act_out_perl_obj: varname=out
INFO Jun 25 17:04:19 [lic_check:1897]: create_act_out_perl_obj: out.status=500
INFO Jun 25 17:04:19 [lic_check:1897]: create_act_out_perl_obj: out.error=Opcode Failed
INFO Jun 25 17:04:19 [lic_check:1897]: do_at: (daily_lic_chk:add)
INFO Jun 25 17:04:19 [lic_check:1897]: do_at: (daily_lic_chk:add)
INFO Jun 25 17:04:19 [lic_check:1897]: do_at: ATTRIBUTE(hours 24) OPCODE(lic_check)
INFO Jun 25 17:04:19 [lic_check:1897]: do_at: ATTRIBUTE(hours 24) OPCODE(lic_check)
INFO Jun 25 17:04:19 [lic_check:1897]: ACTION: DLOPEN(do_nvram_eget, li.rdm)
ERROR Jun 25 17:04:19 [timer:783]: add_sched_node: timer daily_lic_chk already exist
INFO Jun 25 17:04:19 [lic_check:1897]: do_nvram_eget: li.rdm in rdm var
INFO Jun 25 17:04:19 [lic_check:1897]: ACTION: CALL handle_incommunicado_timer
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_ao: OPCODE lic_inc_period
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_ao: OPCODE lic_inc_period
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_ao: OPCODE lic_inc_period CONTENT-TYPE:text, BODY_LEN:0
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_ao: OPCODE lic_inc_period CONTENT-TYPE:text, BODY_LEN:0
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_ao: OPCODE update_cr_alerts
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_ao: OPCODE update_cr_alerts CONTENT-TYPE:text, BODY_LEN:0
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_query: 'select servicevalue from tblclientservices where servicekey = 'initialsetup''
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_query: 'select servicevalue from tblclientservices where servicekey = 'initialsetup''
DEBUG Jun 25 17:04:19 [lic_check:1897]: Initializing database handle
DEBUG Jun 25 17:04:19 [worker:1984]: # OPCODE Called: 'lic_inc_period'
DEBUG Jun 25 17:04:19 [worker:1984]: request name = lic_inc_period
DEBUG Jun 25 17:04:19 [worker:1984]: ### insert_uuid: hdr: len=0 content=1 method=1 name=lic_inc_period
INFO Jun 25 17:04:19 [lic_check:1897]: create_act_out_perl_obj: varname=out
INFO Jun 25 17:04:19 [lic_check:1897]: create_act_out_perl_obj: out.status=0
INFO Jun 25 17:04:19 [lic_check:1897]: create_act_out_perl_obj: JSON out.output={ "servicevalue": [ "0" ] }
DEBUG Jun 25 17:04:19 [lic_check:1897]: json_to_perl: Object
DEBUG Jun 25 17:04:19 [lic_check:1897]: json_to_perl: Array
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_ao: OPCODE lic_appliance_update
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_ao: OPCODE lic_appliance_update
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_ao: OPCODE lic_appliance_update CONTENT-TYPE:text, BODY_LEN:0
DEBUG Jun 25 17:04:19 [lic_check:1897]: do_ao: OPCODE lic_appliance_update CONTENT-TYPE:text, BODY_LEN:0
INFO Jun 25 17:04:19 [lic_check:1897]: UNLOCK: 28
DEBUG Jun 25 17:04:19 [worker:1961]: # OPCODE Called: 'lic_appliance_update'
DEBUG Jun 25 17:04:19 [worker:1961]: request name = lic_appliance_update
DEBUG Jun 25 17:04:19 [worker:1961]: ### insert_uuid: hdr: len=0 content=1 method=1 name=lic_appliance_update
INFO Jun 25 17:04:19 [lic_check:1897]: opcode 'lic_check': time taken: 26.753769911 seconds
INFO Jun 25 17:04:19 [lic_check:1897]: opcode 'lic_check': time taken: 26.753769911 seconds
DEBUG Jun 25 17:04:19 [worker:1897]: request name = lic_check
DEBUG Jun 25 17:04:19 [worker:1897]: response content = '{ "status": "500", "statusmessage": "License Check Failed" }'
DEBUG Jun 25 17:04:19 [worker:1897]: # OPCODE Exited: 'lic_check' with Status: '500'
INFO Jun 25 17:04:19 [apiInterface:1900]: create_act_out_perl_obj: TEXT out.output={ "status": "500", "statusmessage": "License Check Failed" }
DEBUG Jun 25 17:04:19 [worker:1900]: response content = '{ "status": "500", "statusmessage": "License Check Failed" }
- Verify the public key and the device ID in the Sophos Firewall using the following commands:
- From the Advanced Shell, type:
# opcode getpublickey -ds nosync
- From the Device Console, type:
console> system diagnostics show version-info
If you continue observing this issue after following all the steps above, please reach out to the Sophos Support team (support.sophos.com) with the following information:
- Are you facing this issue after an RMA/replacement of the device?
- Share the error message which you receive while syncing the license from the web GUI?
- As mentioned in step-1, share the snap/picture of the subscription from your licensing portal.
- As mentioned in step-2, share the outputs of nslookup, tcpdump, logs(licensing.log), and openssl commands.
- How many ISPs do you have?
- If you have multiple ISPs - Have you tried with SYSNAT or SD WAN route? Please share the snapshot of the configuration.
- Share the output of the page certificate > Certificate authority.
- Enable support access and share the access ID
Related Info
Sophos Firewall: Basic Setup & Registration
updated links to latest, masked s/n
[edited by: Raphael Alganes at 2:15 PM (GMT -8) on 20 Dec 2024]



