Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
______________________________________________________________________________________________________________________________________
Table of Contents
Scenario:
The customer has two locations, the Branch Office (B.O) and a Head Office (H.O). The customer has multiple VLANs configured in the branch office requiring DHCP services for each sub-interface/VLAN. Endpoints in the B.O on their assigned subnet will need to receive their IP address via DHCP Service/Server in the H.O.
- Branch Office
- 1 x Sophos XGS126 Firewall / Firmware Version: 18.5.1 MR-1
- WAN: Public IPv4
- Port8.10 - 172.27.85.1 255.255.255.0
- Port8.195 - 172.27.86.1 255.255.255.0
- 1 x Cisco Catalyst 3560G (48-Ports)
- VLANs: 10 (Data); 195(VoIP)
- 1 x Sophos XGS126 Firewall / Firmware Version: 18.5.1 MR-1
- Head Office
- 1 x Sophos Firewall in Azure (Firmware Version: 18.5.1 MR-1
- WAN: Public IPv4
- PortA: 10.0.2.6
- 1 x Windows Server 2019 w/ DHCP Role
- Eth0: 10.0.2.4
- DHCP Scope Configured: 172.27.85.0/24
- Range: 172.27.85.100-105
- 1 x Sophos Firewall in Azure (Firmware Version: 18.5.1 MR-1
Pre-Requisites:
- Sophos Firewall in Azure configured with a RED Firewall Server interface
- Follow this KB as a Guide for getting started with RED tunnels between Sophos Firewalls
- Follow this KB as a Guide for getting started with RED tunnels between Sophos Firewalls
- Static or Dynamic Routing in Place
- The KB associated with the RED tunnels above also explains how to utilize Static Routes.
Configuration:
Setup - Using the Sophos Firewall in the H.O (Azure) as a DHCP Server that will accept Client Requests via Relay
- Branch Office
- Begin at the branch office to verify that Port8 on our XGS126 has the sub-interfaces configured as above. The Physical Interface does not require any configuration unless you intend to use this in your configuration.
- In the CONFIGURE section, select "Network > Add Interface > Add VLAN."
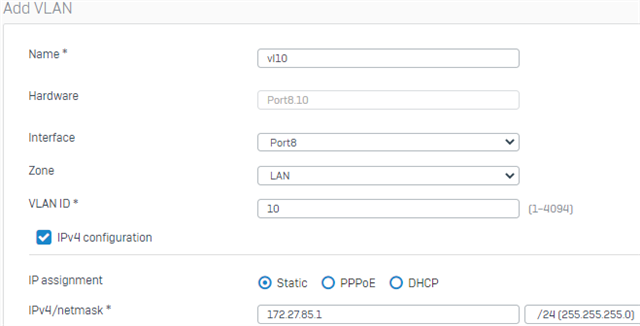
- Configure the VLAN interface
- give the Interface a Name (i.e. vl10)
- select the Port you will associate the VLAN with; this will create a sub-interface(i.e., Port8.vlanid)
- select a Zone(i.e. LAN/DMZ or Custom Zone if created)
- Specify your VLAN ID
- Assign an Interface IP address and subnet mask
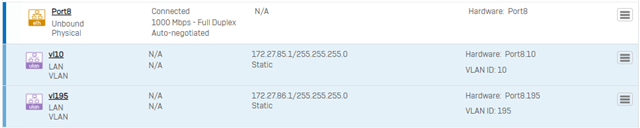
- Repeat this step for any additional sub-interfaces/VLANs you require. (i.e. we have added VLAN195 to Port8 to create Port8.195)
- Configure your Managed Switch interface to recognize VLAN-tagged traffic by placing it in a trunked configuration.
- Next, we will configure a DHCP Relay to the Sophos Firewall running Azure (H.O).
- In the same CONFIGURE section of the Firewall, select "Network > [TAB] DHCP > [Relay] Add"

- Configure your DHCP relay settings for each interface you create above.
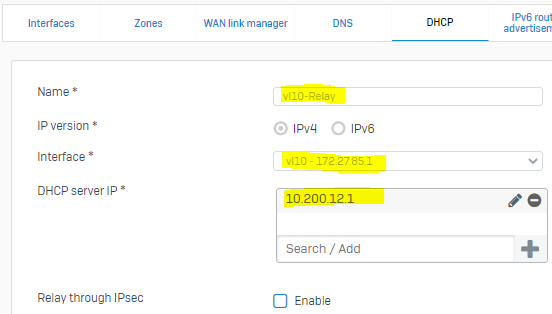
- Note: 10.200.12.1 is the remote interface of our RED tunnel on our Sophos Firewall in Azure (H.O)
- At this point, the Branch Office is configured to forward DHCP requests to 10.200.12.1 where we will now configure the Sophos Firewall in Azure (H.O) with a DHCP Server that accepts client requests via relay.
- Head Office
- Once logged into the Head Office firewall, verify that your RED tunnel is active and connected by viewing your interfaces in CONFIGURE>Network>Interfaces.
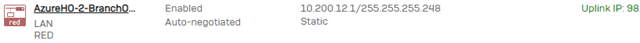
- If you completed the RED tunnel setup and routing configuration, this link will be up and ready to receive the relayed traffic. We can now move on to setting this H.O. firewall up to handle DHCP Requests coming over the RED Tunnel. In the CONFIGURE section, select "Network > [TAB] DHCP"
- In DHCP, we will add a new DHCP Server,
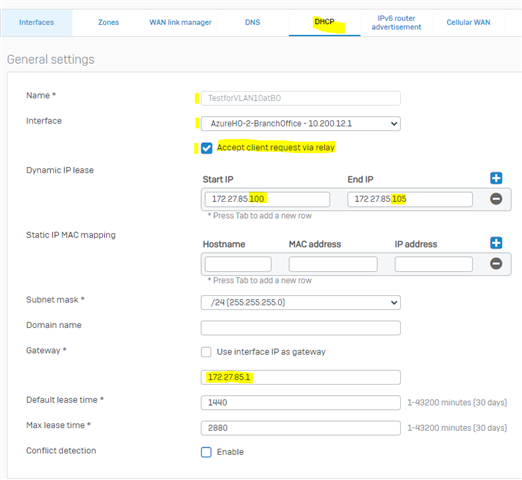
- In the DHCP Server setup window
- Name your DHCP Server
- Select the interface for your RED Tunnel on this Sophos Firewall (H.O).
- Put a check in "Accept Client Request via Relay."
- Configure your Dynamic IP Lease Start IP and End IP
- Configure the subnet mask
- Enter a Gateway IP address of the gateway in your Branch Office for this subnet.
- Configure the DNS you want these clients to use
- For Advanced DHCP Options configuration, you must configure these via Console/CLI.
- Once completed, you must create firewall rules allowing traffic over the RED tunnel.
- Once logged into the Head Office firewall, verify that your RED tunnel is active and connected by viewing your interfaces in CONFIGURE>Network>Interfaces.
Question:
1. I would like to have my Windows Server handle the DHCP requests instead of the Firewall. How do I make this work?
As outlined above, the main difference would be changing your target DHCP server in the Branch Office DHCP relay entry to that of your Windows Server IP address at the Head Office. No DHCP Server would need to be configured on the H.O. firewall; the only requirement would be that your RED Tunnel is up and running, routes are in place, and firewall rules allow the traffic.
______________________________________________________________________________________________________________________________________
Updated KBA Link
[edited by: Raphael Alganes at 10:34 AM (GMT -7) on 21 Oct 2024]
