Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This article describes how to establish a site-to-site IPsec VPN between Sophos Firewall and Check Point firewall.
In this scenario, the Check Point gateway is deployed as Peer A and the Sophos Firewall gateway as Peer B.
The following external IP addresses have been assigned:
- Peer A Gateway: 10.198.66.79
- Peer B Gateway: 10.198.66.115
Applies to the following Sophos products and versions
Sophos Firewall
Prerequisites
- You must have read-write permissions on the SFOS Admin Console for the relevant features.
- You must have Check Point SmartDashBoard R77.30.
Configuration
Check Point
Sign in to the Check Point gateway.
Create a Check Point Gateway Network Object
- Go to Firewall > Network Objects > Check Point and right-click.
- Go to Check Point > Host…
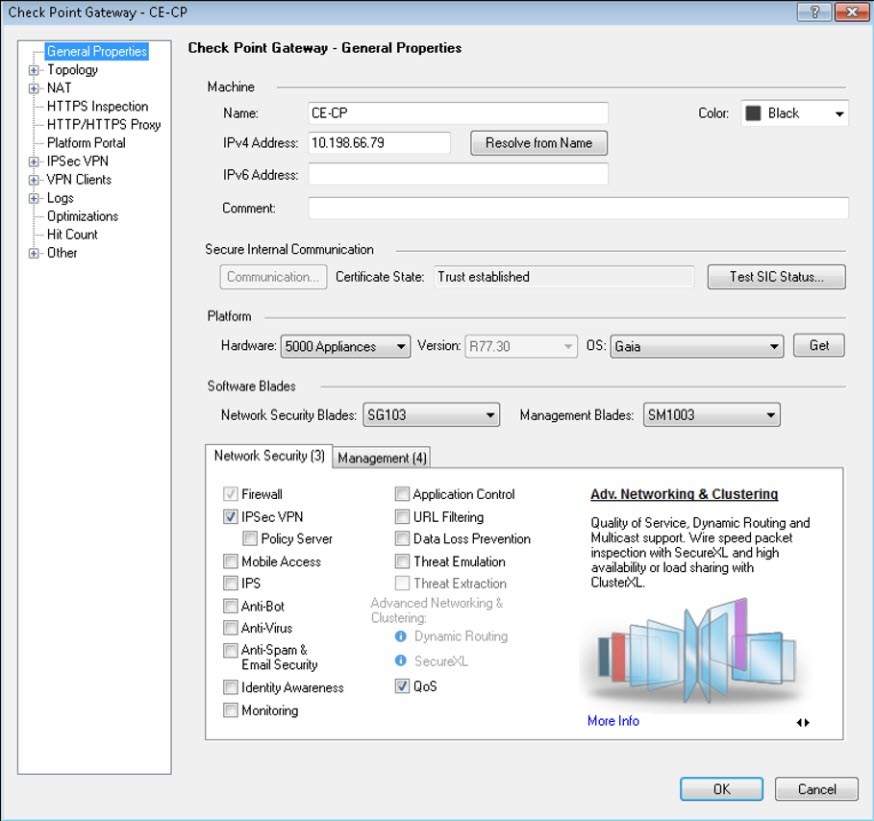
- In General Properties, enter Name.
- For IPv4 Address, enter 10.198.66.79.
- Under Platform, set Hardware to 5000 Appliances, Version to R77.30, and OS to Gaia.
- Under Network Security, select IPSec VPN.
- You can retrieve Topology automatically or manually:
- Automatic: Go to Check Point > Host… > General Properties > Topology. Click Get and click Interfaces with Topology.
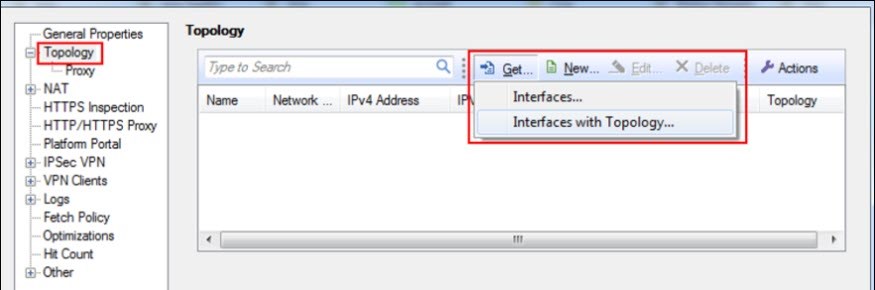
- Manual: Go to Check Point > Host… > General Properties. Click New…
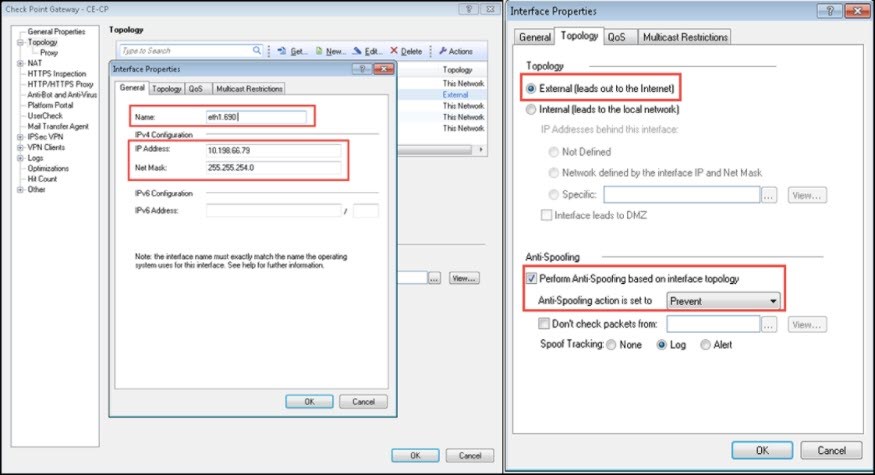
- In Interface Properties, under General, enter Name.
- Enter external network details:
- IP Address: 10.198.66.79
- Netmask: 255.255.254.0
- Under Topology, select External (leads out to the Internet). Under Anti-Spoofing select Perform Anti-Spoofing based on interface topology. Anti-Spoofing action is set to Prevent.
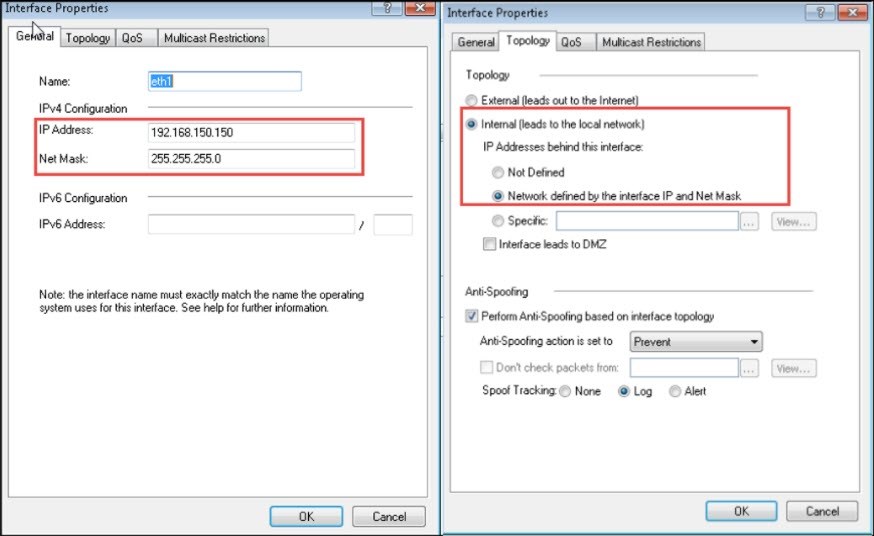
- Enter internal network details:
- IP Address: 192.168.150.150
- Netmask: 255.255.255.0
- Under Topology, select Internal (leads to the local network). Select Network defined by the interface IP and Net Mask.
- Click OK.
Note: Configure the topology based on the Ethernet interfaces.
- Automatic: Go to Check Point > Host… > General Properties > Topology. Click Get and click Interfaces with Topology.
- Under VPN Domain, select Manually defined. We have selected CP_LAN as the internal network behind the Peer A gateway.
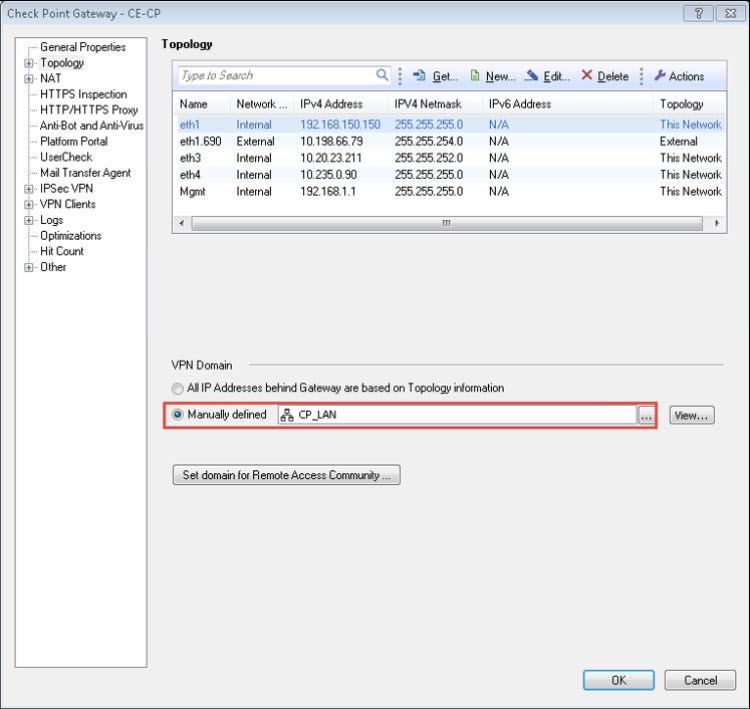
Note: Select All IP Addresses behind Gateway are based on Topology information if you want all networks behind CP firewall to participate in VPN.
Configure Interoperable Device
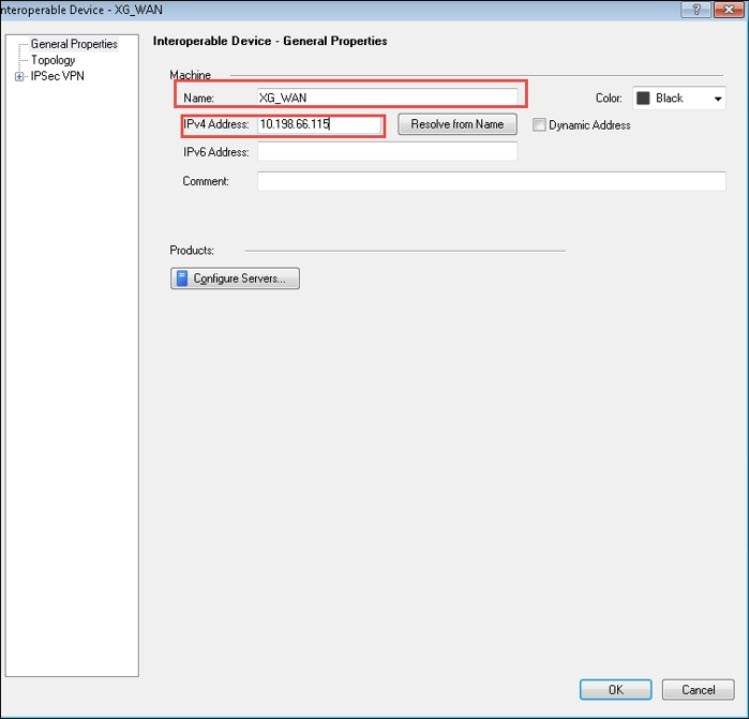
Configure an Interoperable Device to represent the third-party VPN gateway. The public IP address of Peer B gateway is 10.198.66.115.
- Right-click Network Objects and click Interoperable Device.
- Enter Name.
- For IPv4 Address, enter 10.198.66.115.
Create a New VPN Community
- Go to IPSec VPN. Click New and click Star Community.
- Under General, enter Name. In this scenario, we have entered S2S which stands for Site-to-Site.
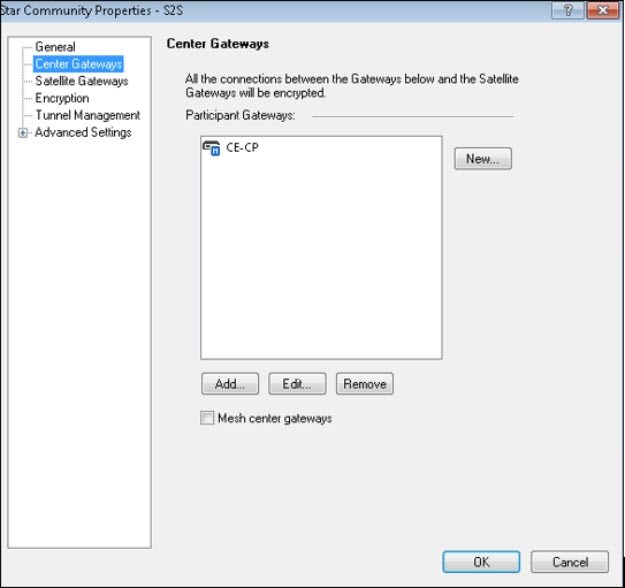
- Under Center Gateways, Add Peer A (Checkpoint Firewall).
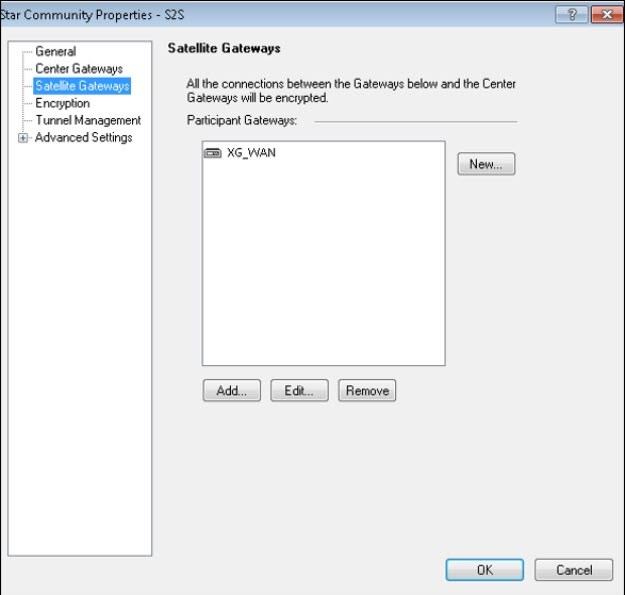
- Under Satellite Gateways, Add Peer B (Sophos Firewall).
- Under Encryption, make sure that the Encryption Method matches the agreed configurations. We have selected IKEv1 for IPv4 and IKEv2 for IPv6.
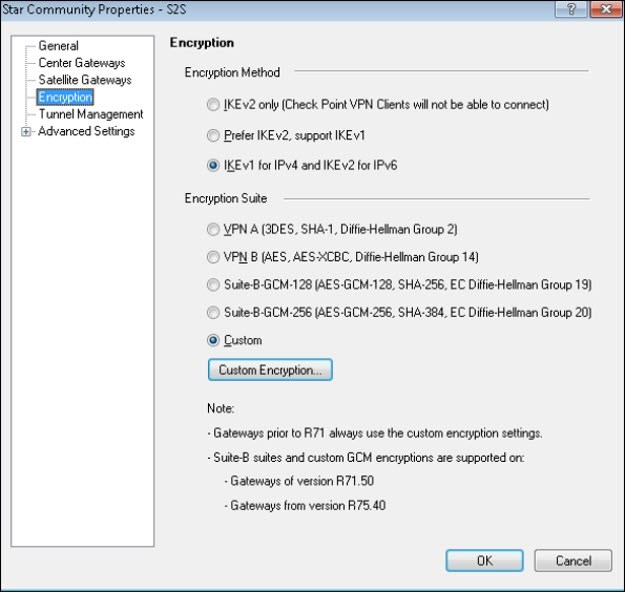
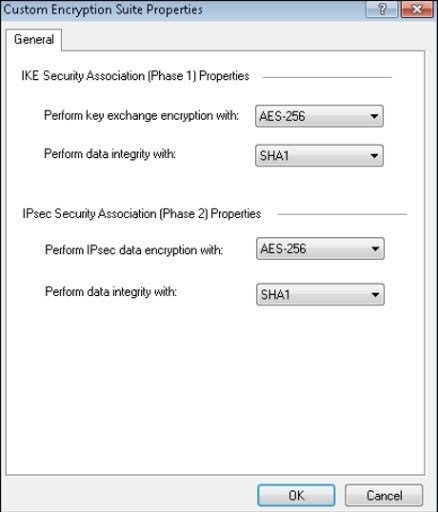
- Under Encryption Suite, select Custom. Click Custom Encryption, and select the required Custom Encryption Suite Properties.
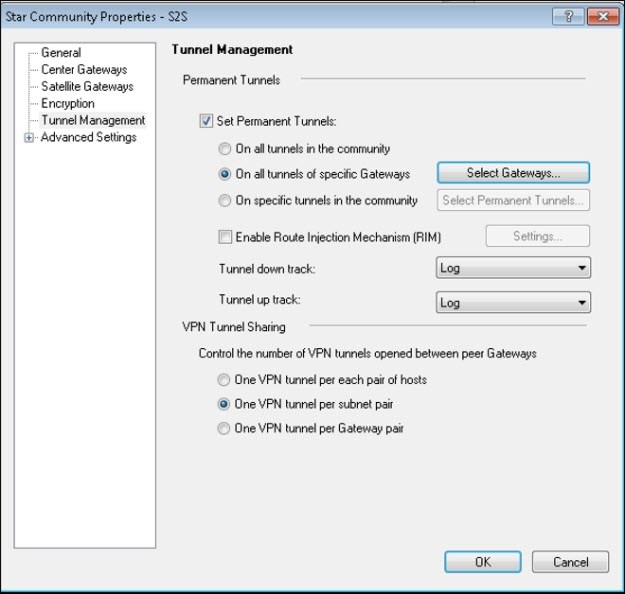
- Select Tunnel Management. Under Permanent Tunnels, select Set Permanent Tunnels.
- Select On all tunnels of specific Gateways and click Select Gateways.
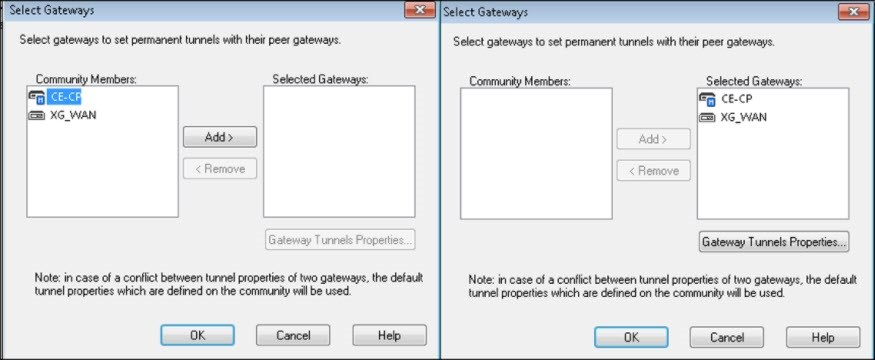
- Under Community Members, select the gateways and Add them to Selected Gateways.
- Under Advanced Settings, select the required settings.
VPN Routing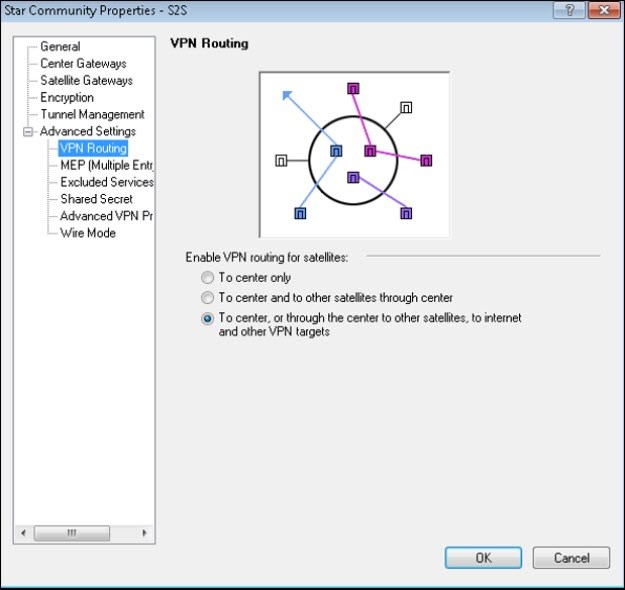
Shared Secret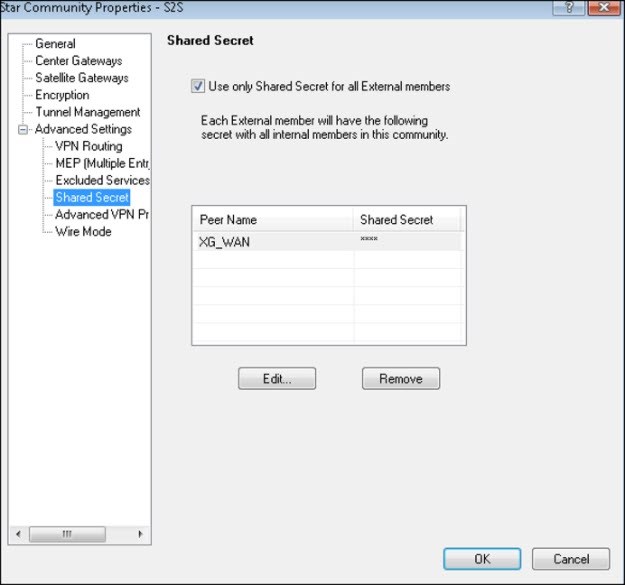
Note: This is a pre-arranged code that you must securely share with the peer gateway administrator. (Based on the option selected in Satellite Gateway while creating IPsec VPN communities.)
Advanced VPN Properties
Under NAT, select Disable NAT inside the VPN community.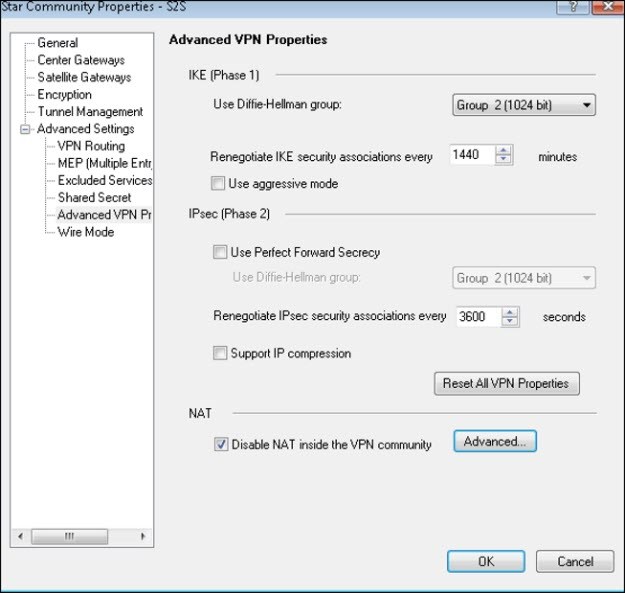
Define a Topology for VPN Community
- Go to Network Objects > Interoperable Device.
- Go to Topology. Under VPN Domain, select Manually defined.
- Add XG_LAN.
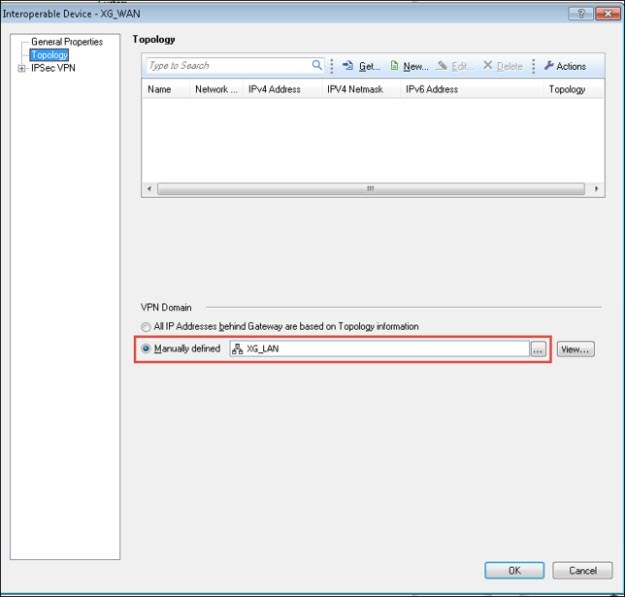
Note: XG_LAN is the network behind Peer B gateway.
Access Control Policy
- Create a policy to allow traffic of S2S VPN Community only.
- Go to Rule Base, Firewall > Policy.
- To add the VPN access rule, right-click the rule number.
- Select Add Rule > Above.
- Select Only connections encrypted in specific VPN Communities option and click add.
- Select the S2S VPN community.
- Click OK.
Note: To allow VPN traffic, add the relevant rules to the firewall rule base.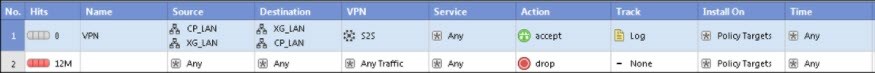
- Install policy on the Gateway.
Sophos Firewall
Sign in to SFOS Admin Console.
Create IPsec policy
- Go to Configure > VPN > IPsec policies and click Add.
Note: The Sophos Firewall parameters must match the parameters you have defined in the Check Point Firewall.
For Version 19.
1. Go to System>Profile>IPsec Profiles>and click Add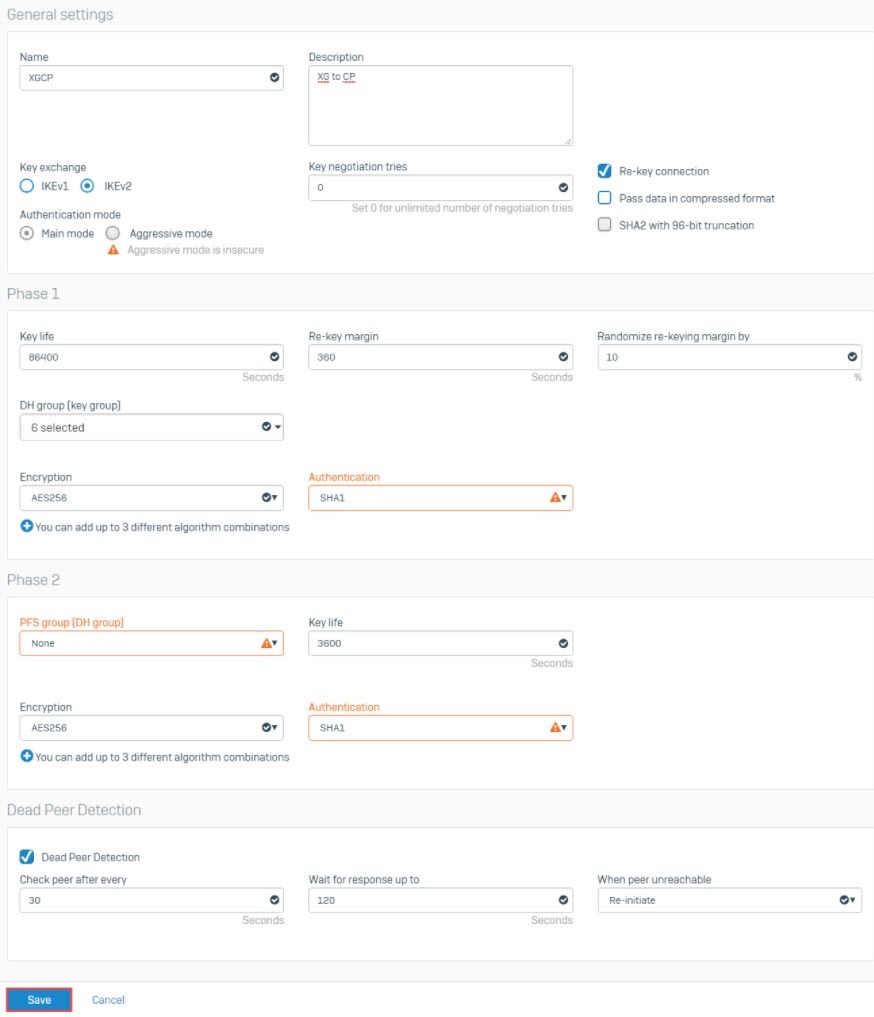
- Click Save.
Create Network Object
- Go to System > Hosts and services > IP host and click Add.
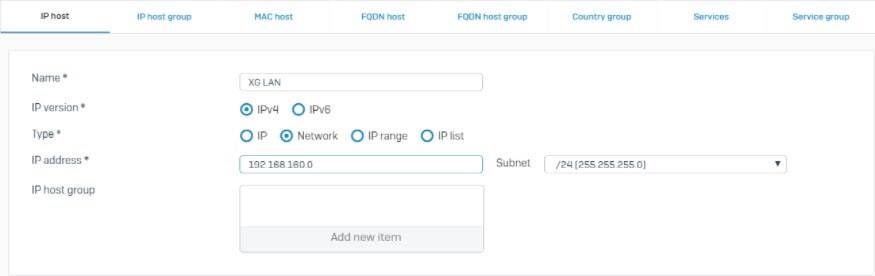
- Similarly, create a Network Object for networks behind the Check Point Gateway.
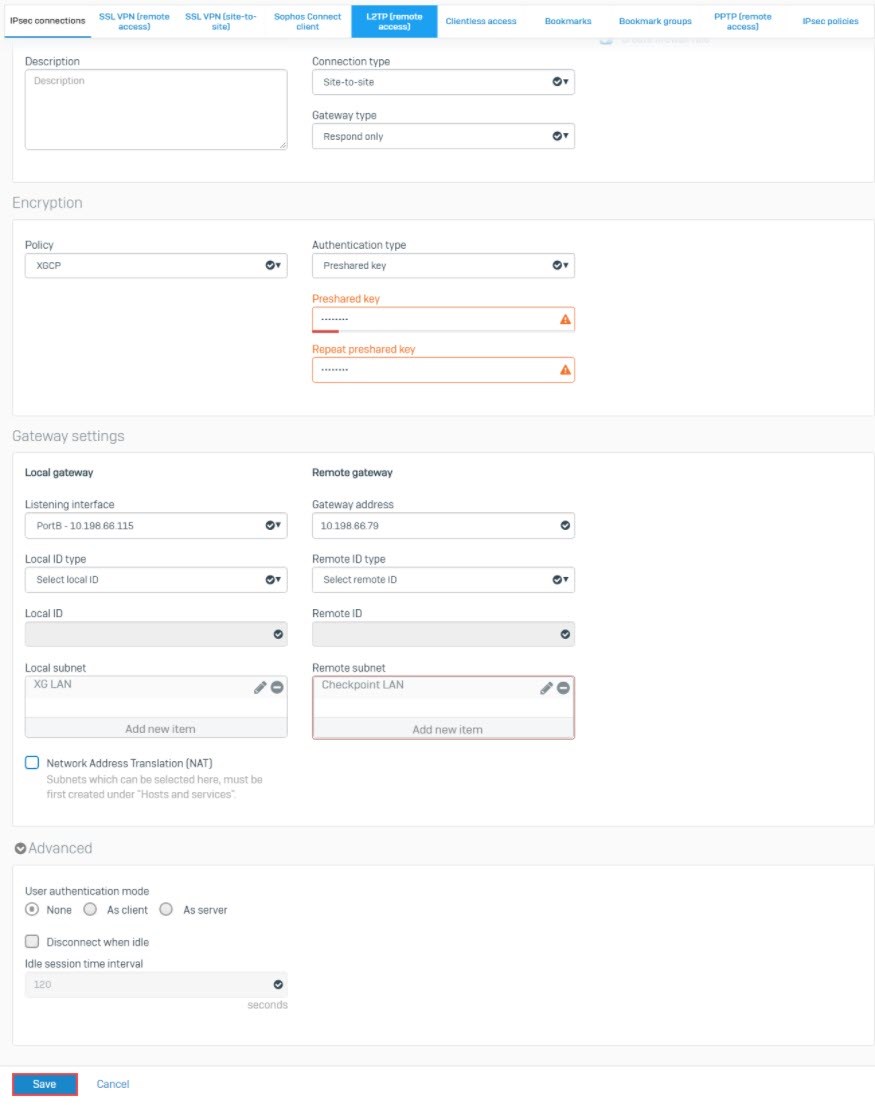
Create an IPsec Connection
- Go to Configure > VPN > IPsec connections and click Add. /For Version 19. Go to Configure >Site-to-Site VPN>IPsec and click Add
- For Name, enter S2S.
- For IP version, select IPv4.
- Set Connection type to Site-to-site.
- Set Gateway type to Respond only.
- Make sure that the Create firewall rule is enabled.
- Set Policy to XGCP (Created in Create IPsec policy).
- For Authentication type, select Preshared key and use the shared key, which was created in Check Point Firewall.
- Under Local gateway, set the Listening interface to the local WAN interface 10.198.66.115 and the Local subnet to XG LAN.
- Under Remote gateway, set the Gateway address to the Peer A gateway 10.198.66.79 and the Remote subnet to Checkpoint LAN.
- For User authentication mode select None.
- Click Save.
- An automatic firewall rule is also created.
Activate the tunnel
- Go to Configure > VPN > IPsec connections and click the
 icon under the Active column to activate the IPsec connection.
icon under the Active column to activate the IPsec connection. - Click the
 icon under the Connection column to activate the tunnel.
icon under the Connection column to activate the tunnel.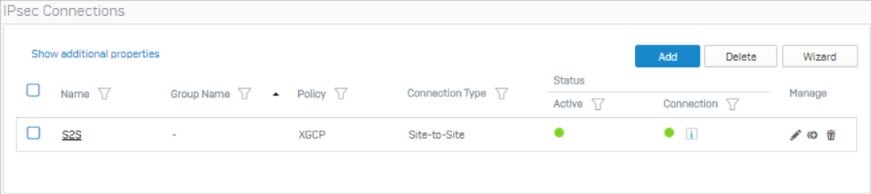
- The IPsec connection between Sophos Firewall and Check Point Firewall is now established.
Sign up to the Sophos Support Notification Service to get the latest product release information and critical issues.
Edited TAGs
[edited by: Raphael Alganes at 5:32 AM (GMT -7) on 17 Sep 2024]

