Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended Read provides three different ways to set up a Sophos Firewall with DUO 2FA.
I've spent some time trying all the different ways to set this up, and this post gives different ways to do this with advantages and disadvantages to each approach and some working configs (as of SFOS 18.0.3 MR-3). Although the article is titled “3 ways,” I have since added an additional configuration, so it’s now four ways.
This isn’t meant to be an exhaustive guide to setting up DUO 2FA with Sophos. Some useful guides are listed in the next paragraph, but I found the lack of examples made configuration much more difficult than needed. Hopefully, this will fill in the gaps in the existing documentation with real working examples.
Further information about the DUO setup that I found useful is https://duo.com/docs/authproxy-reference, which details all the configuration options. There’s also a Sophos UTM setup guide here: https://duo.com/docs/sophos-utm, but it uses an LDAP client (rather than LDAPS), so it isn’t very secure. Also, one of my alternative configurations may better suit your environment and requirements.
If you’re using Sophos in an Active Directory environment, it’s worth understanding a little about usernames and Groups in Sophos before you choose a method. Commonly, you’ll have defined an AD Server in Authentication Servers and use that as your Firewall authentication method. Combined with Heartbeat and STAS, this will automatically identify your network users and create user accounts within Sophos. The user accounts are created in UPN (userPrincipalName) format, e.g. joe.bloggs@mydomain.com. You can combine this with Groups, automatically assigning users to a Group and defining permissions for that Group. Unfortunately, nearly all the other authentication methods, despite authenticating against AD, create a new user in SAN (sAMAccountName) format, e.g. joe.bloggs. Consequently, you end up with two user accounts for the same person, joe.bloggs@mydomain.cmo and joe.bloggs. Furthermore, these SAN format users are automatically created in the default group, which can’t be changed, so there is no group support. Therefore, each user has to be configured individually after they have first logged in. I believe that Sophos will address this limitation at some stage, but that is the current situation. Only one of the methods I have detailed currently works with existing UPN users and allows full Group support (although changes have been promised for V18.0 MR4).
DUO Proxy has a dual personality in that it supports both LDAP and RADIUS clients and LDAP and RADIUS servers. So, as well as ‘pure’ configs (LDAP server and client, or RADIUS server and client), you can mix and match. So, for instance, you can have a configuration where you connect to it via RADIUS, but it authenticates against a backend LDAP server (and vice versa). The different configurations posted here use different combinations of LDAP and RADIUS in the DUO Proxy.
If you’re using a DUO Proxy configuration that utilizes LDAP, you must do a certificate setup. If you’re using DUO Proxy as an LDAP client, you’ll have to import your domain certificate authority certificate. It’s commented on in the config files below, and details on how to do it are in the first link at the start of this post. You must generate a self-signed certificate if you’re using DUO Proxy as an LDAP server. It’s commented in the config files below, and one way to do it’s given here: https://help.duo.com/s/article/2209?language=en_US
A word about LDAP and LDAPS. For proper security, all these configs are configured using LDAPS rather than LDAP (although I refer to it as LDAP throughout this post). If you haven’t already configured your AD for LDAPS, then you’ll have to do this first. N.B. As part of their monthly updates, Microsoft will be rolling out an update that blocks LDAP by default (March 2021), so it’s something worth doing anyway. Plenty of internet articles explain how to turn on LDAPS on AD.
N.B. If you have any issues with your configs and the DUO Proxy won’t start, check the DUO Proxy connectivity_tool.log for the reason.
A summary of the different methods of authentication with DUO Proxy:
Sophos AD Server, DUO LDAP client, and server – the only method that currently supports UPN users and Groups.
Sophos RADIUS Server, DUO RADIUS server, and LDAP client – marginally the easiest to set up. Currently, this doesn’t support UPN users and Groups, but this is planned for V18.0 MR4. If this change happens, then this will probably be the best setup for most users.
Sophos LDAP Server, DUO LDAP client, and server – can support UPN users but not Groups.
Sophos RADIUS Server, DUO RADIUS server, and RADIUS client – probably only of interest if you have an existing RADIUS server you want to utilize for authentication.
Sophos AD Server, DUO LDAP client and server
This is the only method that currently matches existing UPN accounts and has Groups support. However, there’s one issue that you need to be aware of. AD authentication in Sophos has a timeout of 5 seconds. That means you have to respond to the DUO prompt immediately or suffer a login failure. This limits its usefulness; I prefer this authentication method for its benefits, but we use it for a few tech-savvy people who can work with a 5-second limit. If you’re interested in using this method, can I ask you to vote for an adjustable timeout so that we can have longer than 5 seconds to log in? You can do it here: https://ideas.sophos.com/forums/330219-Sophos-firewall/suggestions/42133204-adjustable-timeout-for-active-directory-authentica
The only other issue with this method of authentication is that you have to run the DUO Proxy on a server other than your AD server, as Sophos won’t allow you to setup two AD authentication servers with the same IP (I’m assuming that you already have a non-DUO AD authentication server for things like Firewall Authentication).
This setup allows users to log in with a SAN or UPN format username and will match to (or create) a UPN format user.
In this configuration, the DUO Proxy runs on server2.mydomain.local, 192.168.1.2 the AD runs on server1.mydomain.local, 192.168.1.1
My DUO configuration file (I have removed settings that are for my specific requirements and irrelevant to this posting):
[main] log_auth_events=true ; Default is false. Personally, I like to have a log. [ad_client] host=server1.mydomain.local ; service_account_username= ; service_account_password= ; username and password above are not needed as we are using sspi authentication ; see DUO documentation for details. You may wish to change this. search_dn=DC=mydomain,DC=local ; security_group_dn=CN=DUO Users,OU=Security Groups,DC=mydomain,DC=local ; I have commented out the above line but have it enabled in my setup ; It limits authentication to members of the specified group transport=ldaps ; Microsoft are (rightly) pushing people hard to move to LDAPS rather than LDAP ssl_ca_certs_file=MyDomainCA.pem ; This is a pem formatted copy of your domain certificate authority certificate. ; If it is not saved in the ‘conf’ folder you will have to specify full path. ; See DUO documentation for more info about this. auth_type=sspi ; See DUO documentation for details of different authentication types, you don’t ; have to use sspi [ldap_server_auto] ikey=AKKLBAD89AKG3DJG82 skey=KrLcC48eXYAcRGgy8Ew6S4Yom7muo8N4sRwD api_host=api-101d7231.duosecurity.com ; The above details are fake and should be replaced by your own DUO details. client=ad_client failmode=secure ; failmode above set to your own requirements, see documentation. api_timeout=30 ssl_port=636 ssl_key_path=mydomain.key ssl_cert_path=mydomain.pem ; The above two entries assume you save the required certificate and private key ; in the DUO ‘conf’ folder. See documentation for creating certificate and key. ; If you don’t use the conf folder then the format is as below. N.B. There are no ; quotation marks even if the folders have spaces! ; ssl_key_path= C:\My Folder\Duo Security Authentication Proxy\mydomain.key ; ssl_cert_path=C:\My Folder\Duo Security Authentication Proxy\mydomain.pem exempt_primary_bind=false ; The above is the correct setting for how XG works. Details in DUO documentation.
My Sophos Authentication Server configuration:
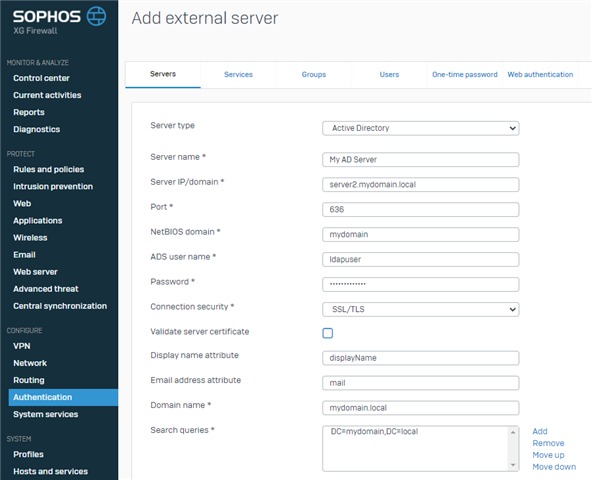
N.B. You don’t need an administrator account for the ADS user account. We setup a dedicated user account (ldapuser) for this purpose with a non-expiring password.
Sophos RADIUS Server, DUO RADIUS server, and LDAP client
This configuration allows users to log in with SAN or UPN but currently will match or create an account in SAN format, potentially creating duplicate users, and there will be no Group support (see the start of the article for more details). However, UPN and Group support is planned for V18.0 MR4. If this change happens, then this will probably be the best setup for most users.
In this configuration, the DUO Proxy, and AD run on the same server, server1.mydomain.local, 192.168.1.1
My DUO configuration file (I have removed settings that are for my specific requirements and irrelevant to this posting):
[main] log_auth_events=true ; Default is false. Personally, I like to have a log. [ad_client] host=server1.mydomain.local ; service_account_username= ; service_account_password= ; username and password above are not needed as we are using sspi authentication ; see DUO documentation for details. You may wish to change this. search_dn=DC=mydomain,DC=local ; security_group_dn=CN=DUO Users,OU=Security Groups,DC=mydomain,DC=local ; I have commented out the above line but have it enabled in my setup ; It limits authentication to members of the specified group transport=ldaps ; Microsoft are (rightly) pushing people hard to move to LDAPS rather than LDAP ssl_ca_certs_file=MyDomainCA.pem ; This is a pem formatted copy of your domain certificate authority certificate. ; If it is not saved in the ‘conf’ folder you will have to specify full path. ; See DUO documentation for more info about this. auth_type=sspi ; See DUO documentation for details of different authentication types, you don’t ; have to use sspi [radius_server_auto] ikey=AKKLBAD89AKG3DJG82 skey=KrLcC48eXYAcRGgy8Ew6S4Yom7muo8N4sRwD api_host=api-101d7231.duosecurity.com ; The above details are fake and should be replaced by your own DUO details. radius_ip_1=0.0.0.0/0 radius_secret_1=mynpssecret failmode=secure ; failmode above set to your own requirements, see DUO documentation. client=ad_client port=1812 client_ip_attr=NAS-IP-Address
My Sophos Authentication Server configurations:
RADIUS Server
Unfortunately, editing this article won't allow me to add any images, so instead, the settings are:
Server type - RADIUS server
Server name - My RADIUS server (or whatever you want to call it)
Server IP - 192.168.1.1 (the IP of your AD server)
Authentication Port - 1812 (matches the config above and is the standard port for RADIUS)
Time-out - 30 (number of seconds to complete 2FA)
Enable accounting - not ticked
Shared secret - whatever it is set to in your config, in my example above it’s mynpssecret
Enable additional settings - off
Sophos LDAP Server, DUO LDAP client and server, - and - Sophos RADIUS Server, DUO RADIUS server and RADIUS client.
The example configuration file allows both the above configurations in one DUO proxy configuration file. You can connect to it via LDAPS, and it’ll authenticate against a backend AD server (via LDAPS). You can also connect to it via RADIUS, which authenticates against a backend RADIUS server (in our case, Microsoft’s NPS server). If you want the LDAP solution, you can remove the [radius_client] and [radius_server_auto] sections from the config. If you want the RADIUS solution, you can remove the [ad_client] and [ldap_server_auto] sections from the config.
The RADIUS configuration allows users to log in with SAN or UPN but will match or create an account in SAN format, so it’ll potentially create duplicate users, and there will be no Group support (see the start of the article for more details). I haven’t included any details of setting up a RADIUS server, as that is outside the scope of this post.
The LDAP configuration allows users to log in with SAN OR UPN. Which, depends on the setting of ‘Authentication attribute’ when you setup the server in Sophos. If you have a setting of ‘sAMAccountName’, then you can use SAN format username login. If you have a setting of ‘userPrincipalName’, then you can use the UPN format username login.
If using ‘sAMAccountName’, this method will also match or create an account in SAN format. If using ‘userPrincipalName’, this method will match or create an account in UPN format, BUT if there’s an existing account, it’ll overwrite any Group setting and change it to the default Group.
I run DUO proxy for these setups on the same server as AD and our NPS (RADIUS) server. For that reason, you will see I am using non-standard ports, so it doesn’t clash with the existing services. If you’re running DUO Proxy on a different server, you can use the standard ports – make sure the config settings match the Sophos settings.
In this configuration, the DUO Proxy, RADIUS server, and AD all run on the same server, server1.mydomain.local, 192.168.1.1
My DUO configuration file (I have removed settings that are for my specific requirements and irrelevant to this posting):
[main] log_auth_events=true ; Default is false. Personally, I like to have a log. [ad_client] host=server1.mydomain.local ; service_account_username= ; service_account_password= ; username and password above are not needed as we are using sspi authentication ; see DUO documentation for details. You may wish to change this. search_dn=DC=mydomain,DC=local ; security_group_dn=CN=DUO Users,OU=Security Groups,DC=mydomain,DC=local ; I have commented out the above line but have it enabled in my setup ; It limits authentication to members of the specified group transport=ldaps ; Microsoft are (rightly) pushing people hard to move to LDAPS rather than LDAP ssl_ca_certs_file=MyDomainCA.pem ; This is a pem formatted copy of your domain certificate authority certificate. ; If it is not saved in the ‘conf’ folder you will have to specify full path. ; See DUO documentation for more info about this. auth_type=sspi ; See DUO documentation for details of different authentication types, you don’t ; have to use sspi [radius_client] host=192.168.1.1 secret=mytopsecretpass pass_through_all=true pass_through_attr_names=Filter-Id [ldap_server_auto] ikey=AKKLBAD89AKG3DJG82 skey=KrLcC48eXYAcRGgy8Ew6S4Yom7muo8N4sRwD api_host=api-101d7231.duosecurity.com ; The above details are fake and should be replaced by your own DUO details. client=ad_client failmode=secure ; failmode above set to your own requirements, see DUO documentation. port=340 ; custom port so it doesn’t clash with AD LDAP (see comments above) api_timeout=30 ssl_port=637 ; custom port so it doesn’t clash with AD LDAPS (see comments above) ssl_key_path=mydomain.key ssl_cert_path=mydomain.pem ; The above two entries assume you save the required certificate and private key ; in the DUO ‘conf’ folder. See documentation for creating certificate and key. ; If you don’t use the conf folder then the format is as below. N.B. There are no ; quotation marks even if the folders have spaces! ; ssl_key_path= C:\My Folder\Duo Security Authentication Proxy\mydomain.key ; ssl_cert_path=C:\My Folder\Duo Security Authentication Proxy\mydomain.pem exempt_primary_bind=false ; The above is the correct setting for how XG works. Details in DUO documentation. [radius_server_auto] ikey=AKKLBAD89AKG3DJG82 skey=KrLcC48eXYAcRGgy8Ew6S4Yom7muo8N4sRwD api_host=api-101d7231.duosecurity.com ; The above details are fake and should be replaced by your own DUO details. radius_ip_1=0.0.0.0/0 radius_secret_1=mynpssecret failmode=secure ; failmode above set to your own requirements, see DUO documentation. client=radius_client port=1814 ; custom port so it doesn’t clash with RADIUS (NPS) server (see comments above) pass_through_all=true client_ip_attr=NAS-IP-Address
My Sophos Authentication Server configurations:
RADIUS Server
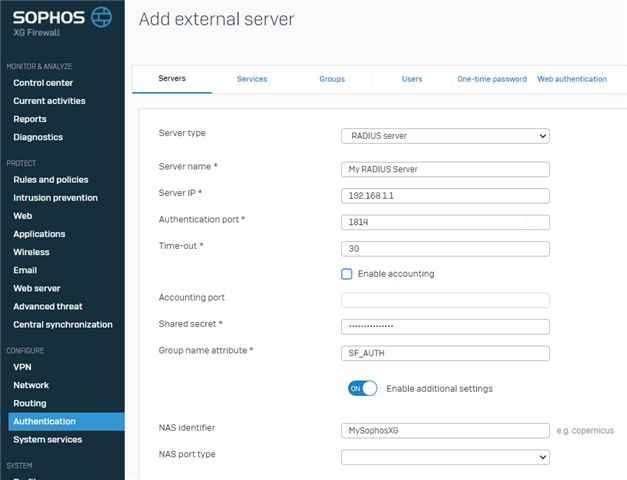
N.B. Non-standard Authentication port to match configuration file.
LDAP Server

N.B. Authentication attribute – This can be set to sAMAccountName or userPrincipalName. Accounts are created/matched to user accounts in the same name format (SAN or UPN).
N.B. You don’t need an administrator account for the ADS user account. We set up a dedicated user account (ldapuser) for this purpose with a non-expiring password.
N.B. Non-standard Port to match configuration file.
Added TAG
[edited by: Erick Jan at 5:22 AM (GMT -7) on 10 Oct 2024]


