Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Overview
This recommended read describes setting up Radius with authentication on Windows Server 2016 and configuring it to work with Wireless Protection on the Sophos Firewall.
Table of Contents
This applies to the following Sophos products and versions
Sophos Firewall
Prerequisites
Important: The Microsoft KBs articles at the bottom of this document must also be followed for the certificates to work properly.
This article is based on a clean installation of Windows Server 2016. This procedure has been tested using Windows Server 2016 with Sophos Firewall with the following Wireless Network configuration:
- Encryption Mode: WPA2 Enterprise
- Algorithm: AES (secure)
- Client Traffic: Separate Zone
- Client Isolation: Disabled
- Hide SSID: Disabled
If you already have some of the below steps configured, use this KB as a starting point for troubleshooting issues you may be experiencing.
Prerequisites:
- Sophos Firewall with Wireless Protection
- Sophos AP
- Windows Server 2016
Windows Server required Roles & Features:
- Active Directory
- Active Directory Certificate Services
- Network Policy and Access Services
This article assumes the following:
- Have Active Directory installed and configured on your network
- Have the Network Policy and Access Services role installed
- Have a configured certificate authority or have a valid certificate you wish to use with NPS (Radius)
- Your access point is connected and functional on your Sophos Firewall
How to configure Wireless Protection with Radius authentication
This procedure consists of the following three sections:
- Wireless Protection Configuration (Sophos Firewall)
- Radius Configuration (Windows Server)
- NPS Certificate Configuration using Certificate Templates (Windows Server)
Wireless Protection Configuration
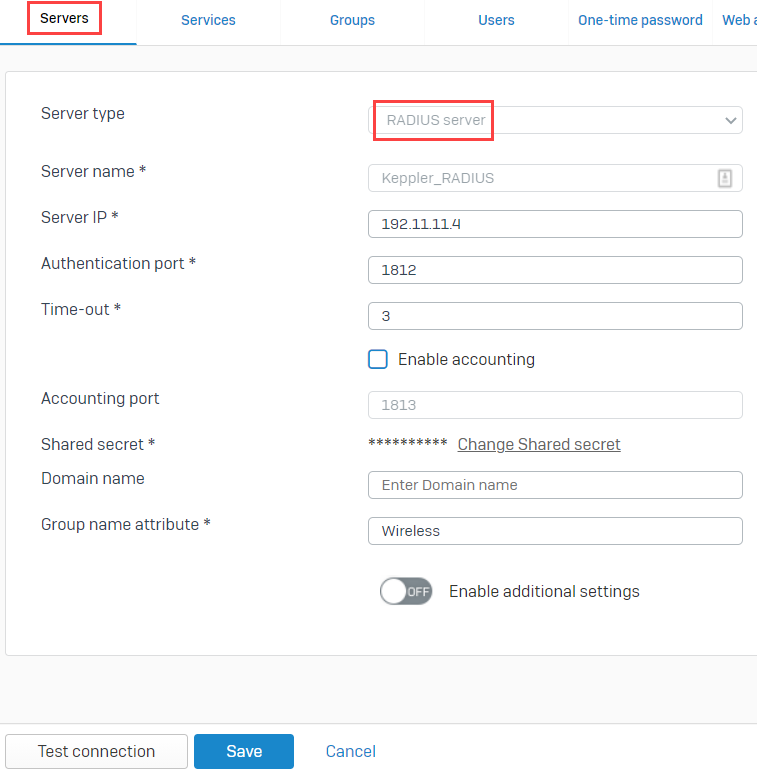
- You can add a RADIUS server under Configure > Authentication > Servers > Add. For more details about adding a RADIUS server, see Add a RADIUS server.
- Remember the shared secret, as it’ll be used later when configuring the RADIUS server.
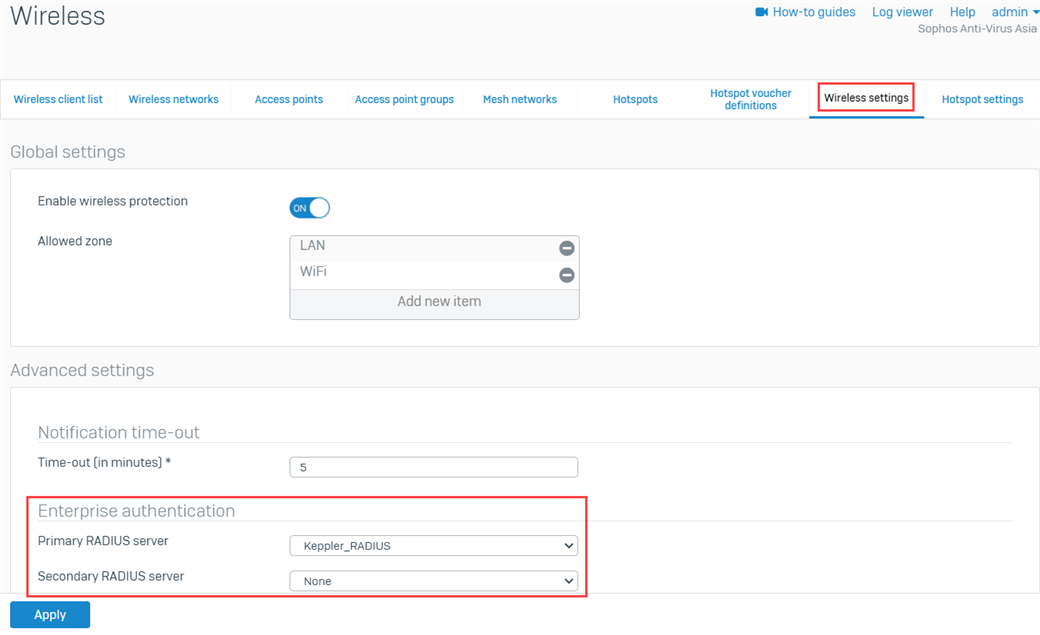
- Select your RADIUS server from the drop-down box under Protect > Wireless > Wireless settings.
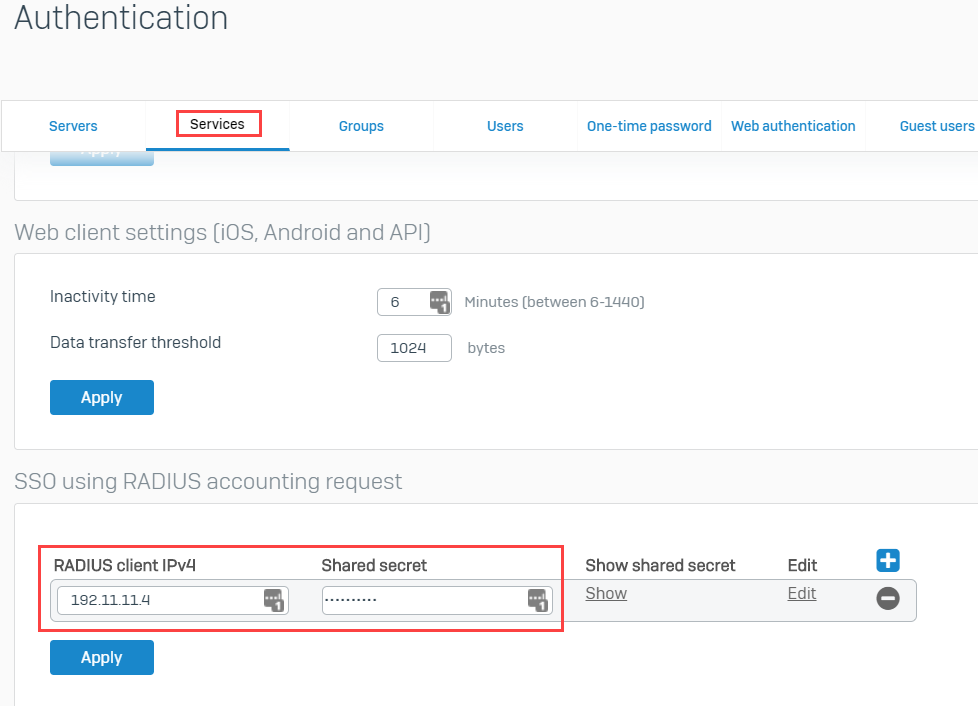
- Go to Authentication > Services and scroll down until the SSO using the radius accounting request section to set the Radius Client IPv4 to the Radius server's IP address and shared secret.
Configuring RADIUS on your Windows Server
Authorize your Network Policy Server with your Active Directory
Radius Client Setup
- Run the Network Policy Server (NPS) to RADIUS Clients and Servers > RADIUS Clients. Right-click the RADIUS Clients and select New.
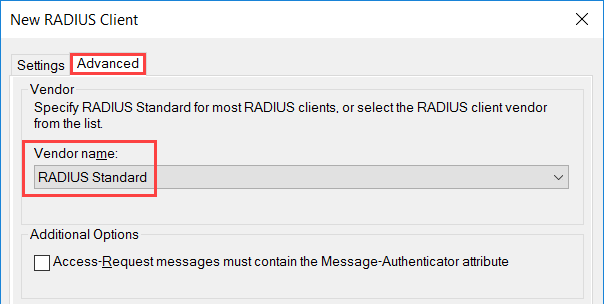
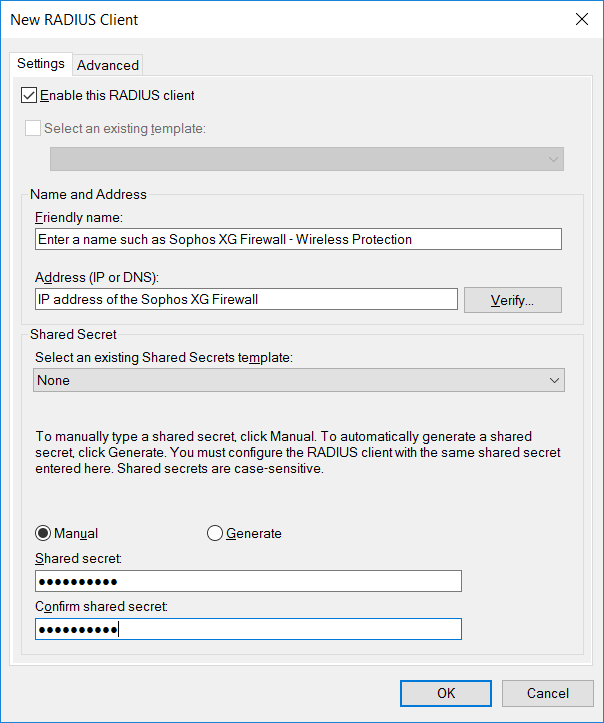
- Under the Settings tab, enter the values as shown below:
- Friendly Name: You may put any name here. You’ll need to enter the name again in the steps below.
- Address (IP or DNS): Enter the IP Address or internal DNS name of your Sophos Firewall. Click verify and make sure the IP or hostname is resolved correctly.
- Shared Secret: Enter the shared secret you entered in Step 1 of the Wireless Protection Configuration above.
- Under the Advanced tab, enter the value as shown below:
- Click Apply.
Policies
Connection Request Policies:
- Run the Network Policy Server (NPS) to Policies > Connection Request Policies. Right-click Connection Request Policies and select New.
- Enter a Policy name. In our example, we have called it Wireless.
- Click Next.
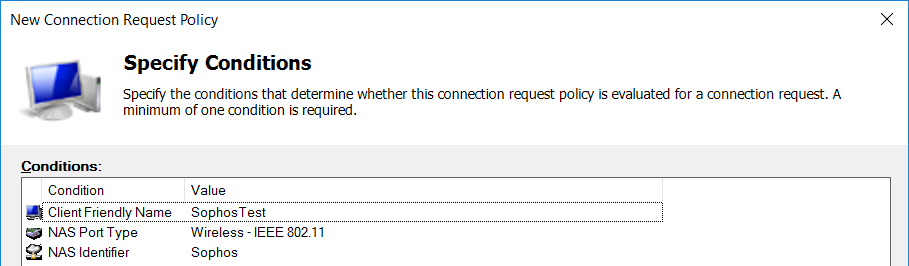
- Add the following conditions:
- Click Next for the following windows, and then click Finish – The default settings are fine for the rest of the configuration.
Network Policies:
Click Network Policies from the NPS Console
- Right-click Network Policies and select New.
- Enter a name, preferably the same as the Connection Request Policy.
- Click Next.
- Click Add.
- Choose how you want the users to authenticate. For this, we’re using User Groups and the group Domain Users.
- Click Next until you arrive at Configure Authentication Methods.
- We’ll use PEAP. Click Add and choose Microsoft: Protected EAP (PEAP).
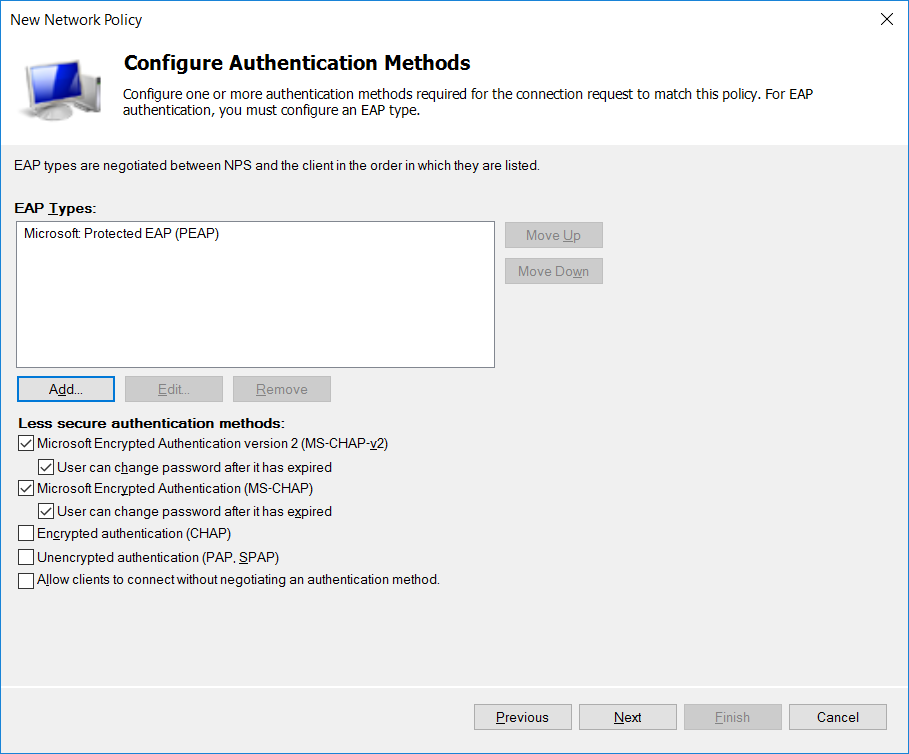
- Choose the authentication methods as shown above.
- Click Next.
- Under NAS Port Type, choose Wireless – IEEE 802.11.
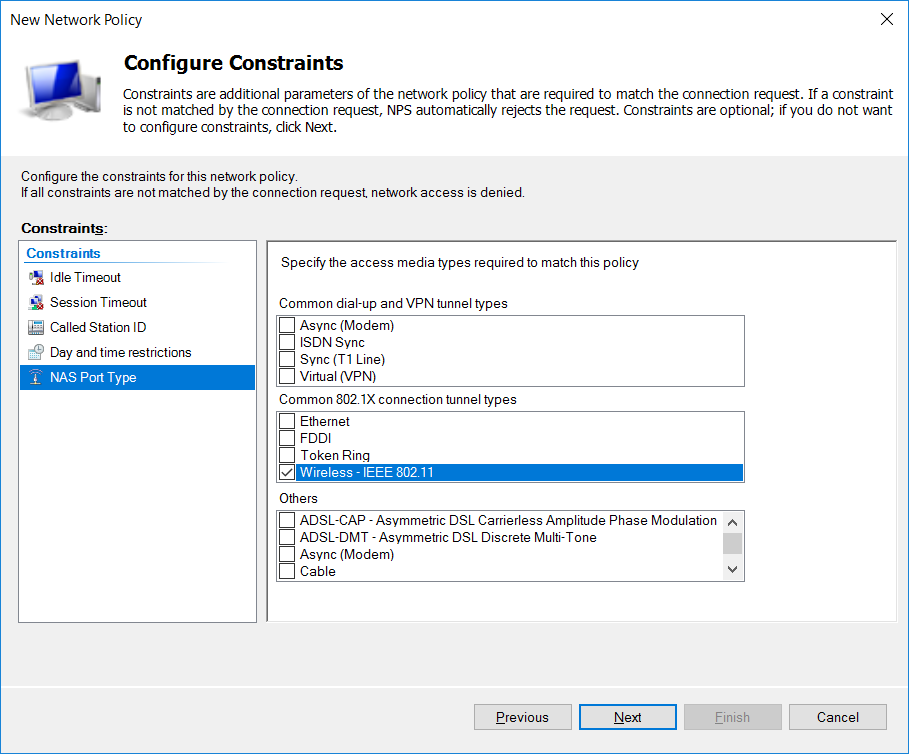
- Click Next, Next, and then Finish.
NPS Certificates
Please make sure the certificate you’re using has a valid subject, as in the following screenshot:
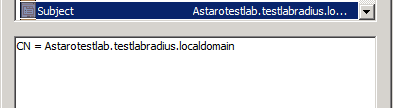
You can use your current certificate, but we recommend creating a separate RAS and IAS certificate template if your Radius server is on the same device as your Domain Controller. If you renew your Domain Controller cert, it can stop authentication via Radius.
The following links point to a few Microsoft KB articles describing how to deploy a CA and NPS Server-Cert. You must follow the below links in order. Remember, this document outlines a new configuration. Please tailor this section according to how you have your certificates set up.
- Deploy a CA and NPS Server Certificate
- NPS Server Certificate: CA Installation
- NPS Server Certificate: Configure the Template and Autoenrollment
Revamped RR
[edited by: Erick Jan at 10:29 AM (GMT -7) on 18 Sep 2024]