Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Overview
The post provides a simple guide for configuring firewall rule and NAT for LAN-to-WAN, LAN-to-VPN, WAN-to-DMZ traffic, and Full NAT.
More technical details can be found at
LAN-to-WAN traffic
Network plan:
internal computers --- Port1 [Sophos Firewall] Port2 --- Internet
Sophos Firewall LAN interface Port1 connects to internal computers, and WAN interface Port2 connects to Internet.
To allow internal computers access Internet:
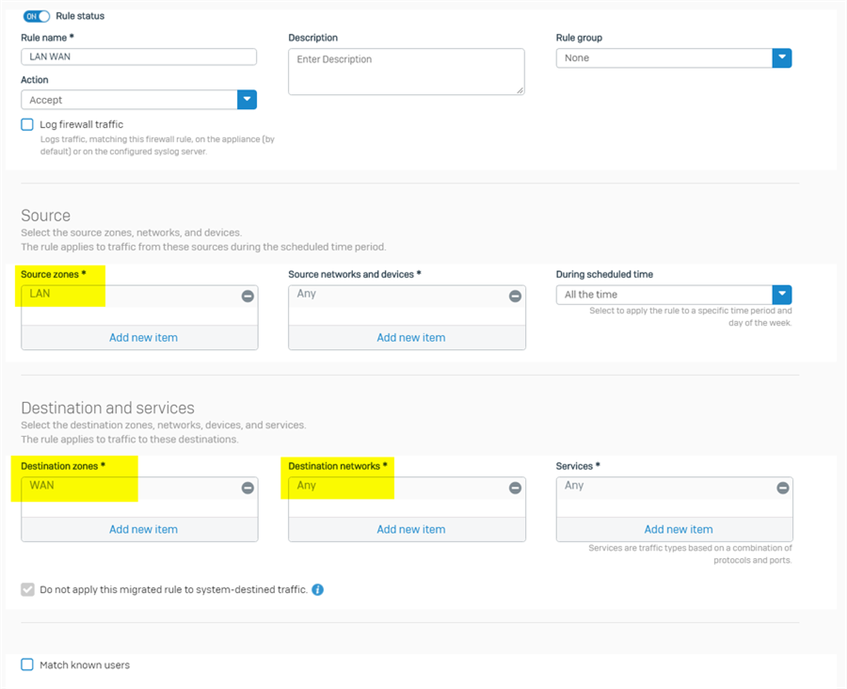
1. go to firewall webadmin > Rules and policies > Firewall rules, create a firewall rule to allow LAN to WAN traffic
- source zone: LAN, the zone internal computers locates
- source networks: Any, or specific internal subnet
- Destination zone: WAN
- Destination networks: Any
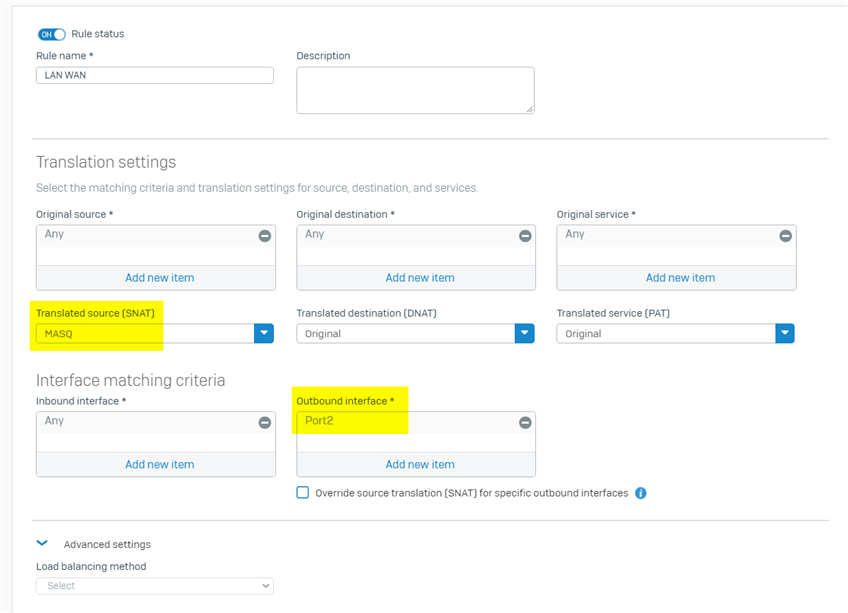
2. go to firewall webadmin > Rules and policies > NAT rules, create NAT rule to apply Masquerading on LAN to WAN traffic
- Original source: Any
- Original destination: Any
- SNAT: MASQ, or the preferred WAN IP for Masquerading
- Inbound interface: Any
- Outbound interface: Port2, the Sophos Firewall WAN interface
Note:
- I recommend to set "Outbound interface" to WAN interface. If outbound interface is set to "Any", the NAT rule will be also applied on LAN to VPN (LAN to DMZ) traffic, and then stops LAN to VPN (LAN to DMZ) traffic, and might cause network issue.
- It is recommended to move the LAN to WAN NAT rule to bottom, otherwise, it can be applied on other traffic, and cause unexpected result.
Specify primary gateway
When there are multiple WAN interfaces, we can use SD-WAN policy routing to specify primary gateway for LAN to WAN traffic.
Note: Primary/Backup gateway was removed from firewall rule since v18.0.
Assume Sophos Firewall has 2 WAN interfaces, Port2 and Port3, we need to specify Port2 as primary gateway for LAN to WAN traffic.
1. Go to webadmin > Routing > SD-WAN policy routing, add a new IPv4 SD-WAN policy route
- incoming interface: Port1, the LAN interface
- Source networks: 192.168.3.0/24, which is LAN subnet
- Destination networks: Any
- Services: Any
- Application object: Any
- User or groups: Any
- Primary gateway: Port2_GW, gateway of WAN interface Port2
- Backup gateway: Port3_GW, gateway of WAN interface Port3
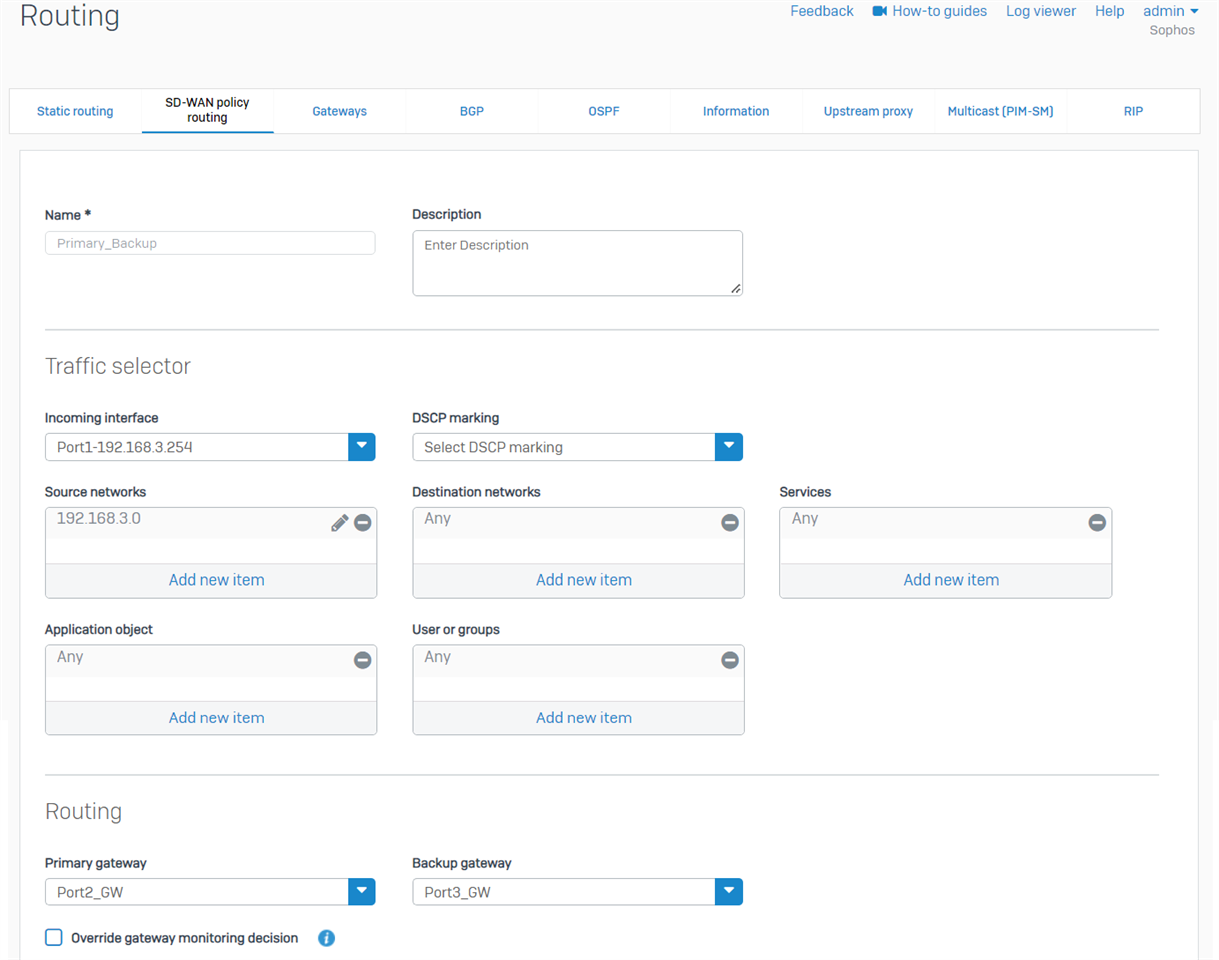
Detail of those gateways can be checked on webadmin > Routing > Gateways
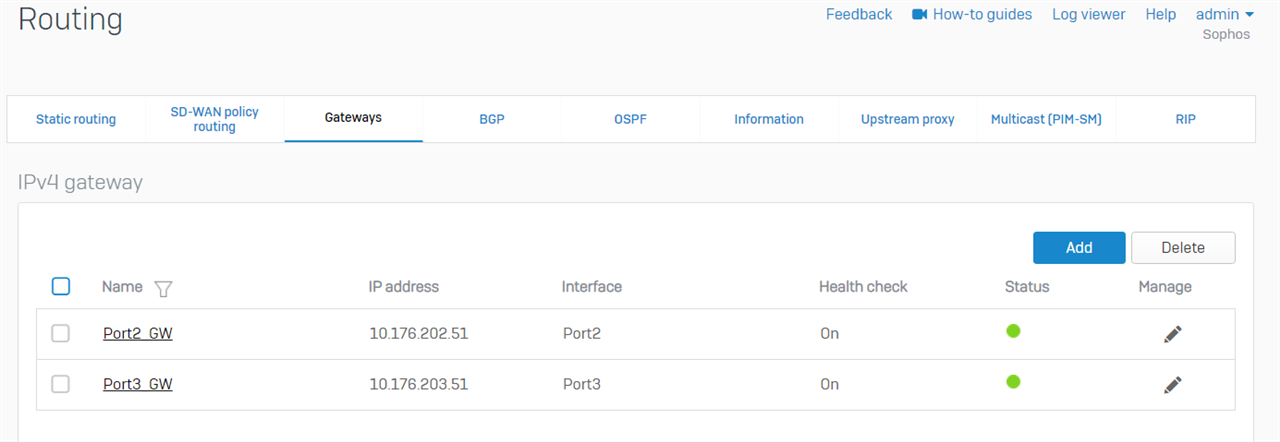
2. Make sure the SD-WAN policy route doesn't interrupts other traffic:
- If policy based site-to-site IPsec VPN is in use, and 192.168.3.0/24 is local VPN subnet, please make sure "VPN routes" is preferred over "SD-WAN policy routes", otherwise, 192.168.3.0/24 cannot access any remote VPN subnet.
- If 192.168.3.0/24 needs to access another LAN network, for example, 192.168.21.0/24 via Sophos Firewall, please make sure "static routes" is preferred over "SD-WAN policy routes", otherwise, 192.168.3.0/24 cannot access any other LAN network.
- To check route precedence, please run the following command in Sophos Firewall SSH terminal > Device Console:
system route_precedence show - To change route precedence, please run Device Console command
system route_precedence set - To make SD-WAN policy routes to be the least preferred, please run Device Console command
system route_precedence set vpn static sdwan_policyroute - Make sure route precedence is configured to match your network requirement.
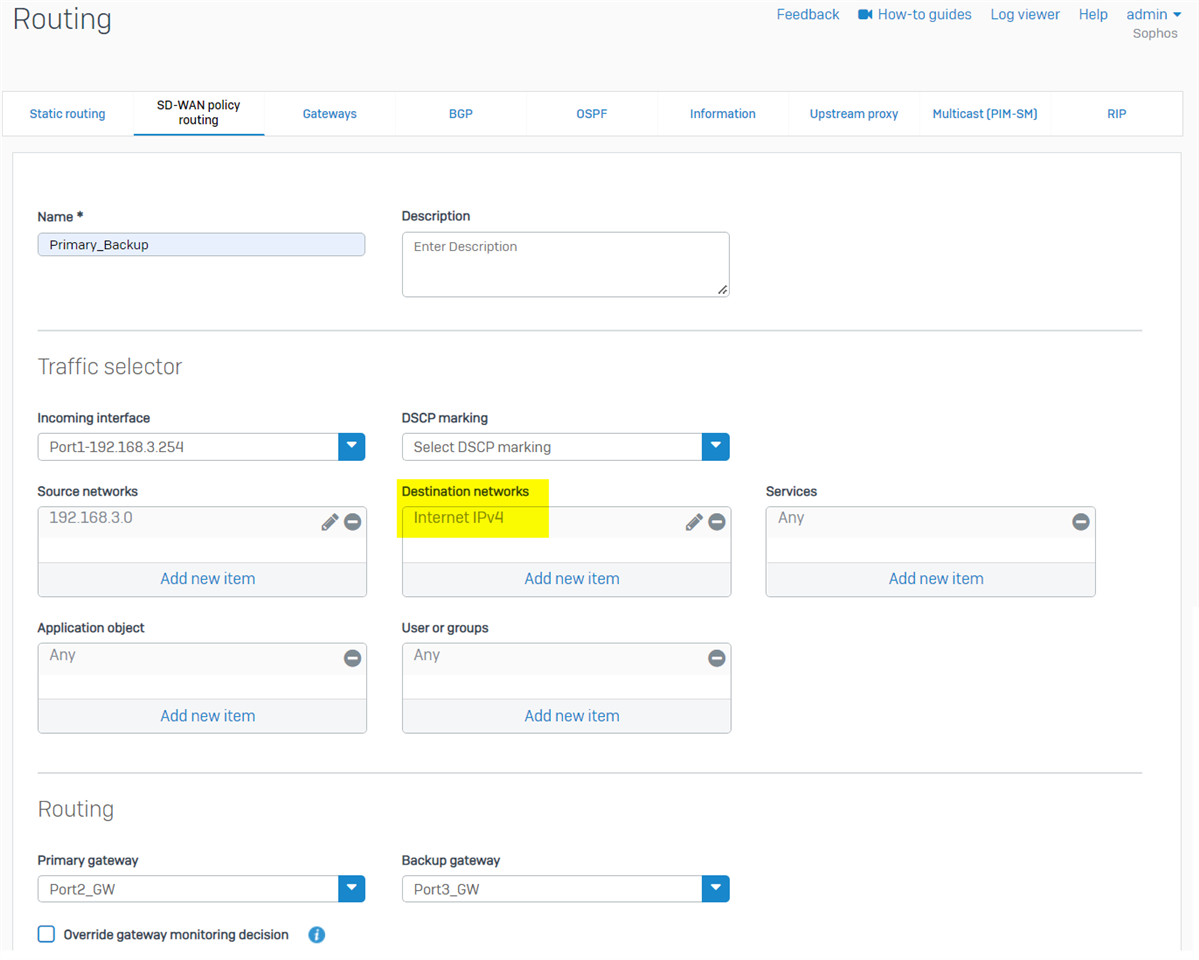
Note: if Sophos Firewall was freshly installed from v18.5 IOS, there is an IP host group "Internet IPv4", which covers all Internet IPv4 address. We can use it as Destination network in the SD-WAN policy route to prevent interference with other routes, and no need to worry about route precedence, as screenshot below.
For Sophos Firewall upgraded from v18.0 or earlier version, we must manually create the IP host group "Internet IPv4", as per KBA Sophos Firewall: Auto-create an object for IPv4 internet addresses group
LAN-to-VPN traffic
Network plan:
internal computers --- Port1 [Sophos Firewall] Port2 --- IPsec VPN --- [remote VPN gateway] --- remote VPN network
Sophos Firewall LAN interface Port1 connects to internal computers, and WAN interface Port2 connects to Internet.
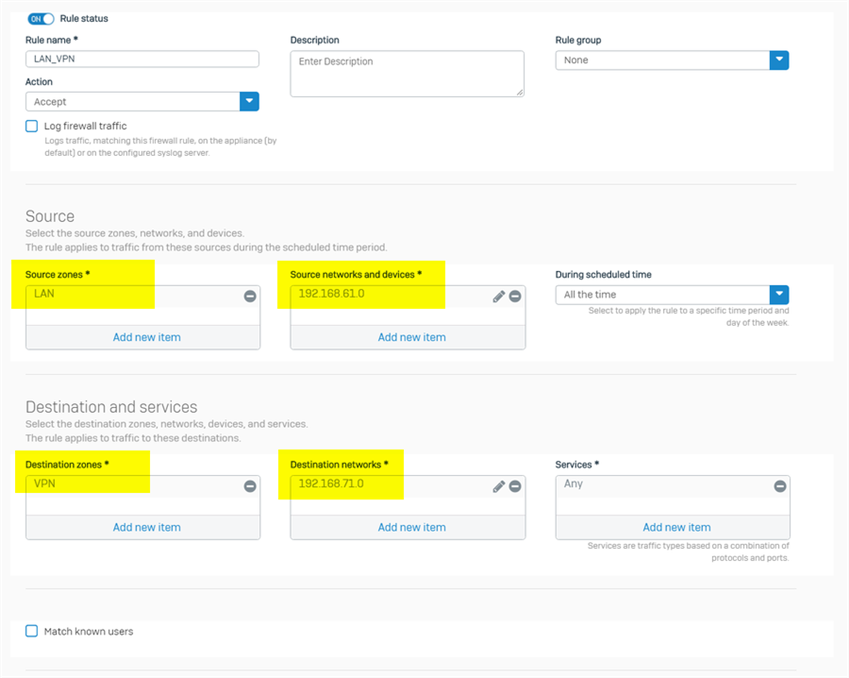
To allow internal computers access remote VPN network, just create a LAN to VPN firewall
- source zone: LAN
- source networks: 192.168.61.0/24, or any other local subnet configured in site-to-site IPsec VPN
- Destination zone: VPN
- Destination networks: 192.168.71.0/24, or any other remote VPN subnet configured in site-to-site IPsec VPN
You might need to create another firewall rule for VPN to LAN traffic. Please make sure there is no NAT rule applied to LAN to VPN traffic, unless NAT is necessary for local VPN network to reach remote VPN network.
WAN-to-DMZ traffic
Network plan:
external users --- Internet --- Port2 [Sophos Firewall] Port1 --- internal Exchange server (in DMZ zone)
Sophos Firewall WAN interface Port2 connects to Internet, and DMZ interface Port1 connects to internal Exchange server.
External users need to access HTTPS service on internal Exchange server by visiting Sophos Firewall public IP.
To allow the DNAT access:
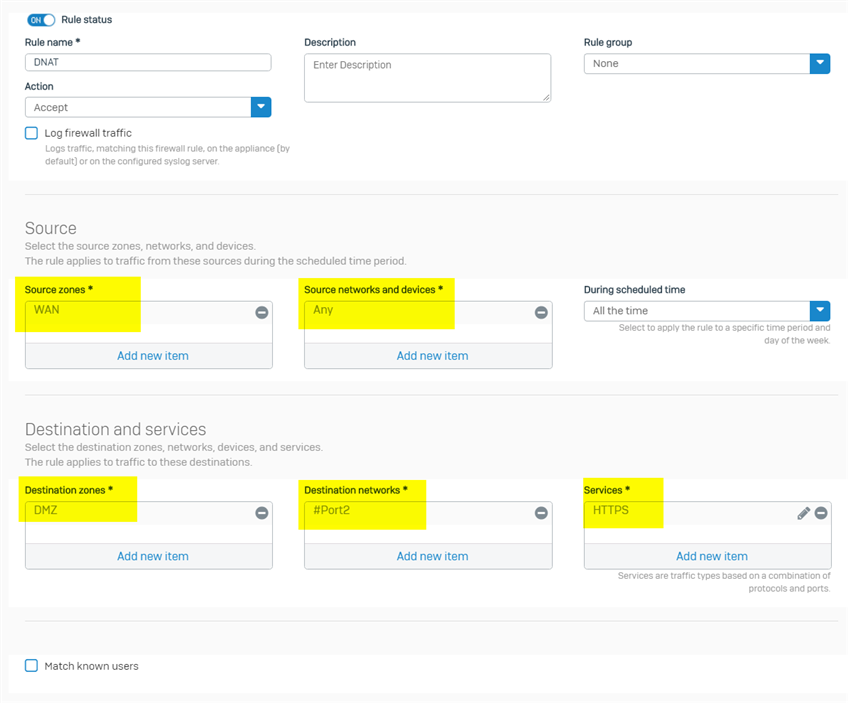
1. create a firewall rule to allow WAN to internal Exchange server traffic
- source zone: WAN
- source networks: Any, or specific IP addresses of all external users
- Destination zone: DMZ, the zone internal Exchange server locates
- Destination networks: Sophos Firewall public IP visited by external users, in this scenario, it is IP address of WAN Port2
- Services: HTTPS
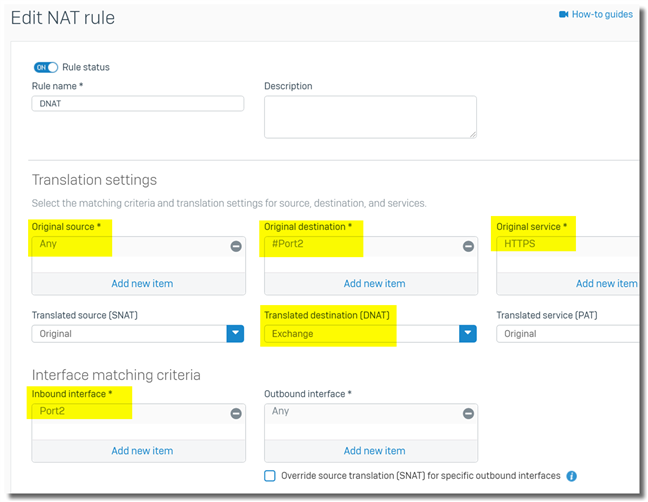
2. create a DNAT rule
- Original source: Any, or specific IP addresses of all external users
- Original destination: Sophos Firewall public IP visited by external users, in this scenario, it is IP address of WAN Port2
- Original service: HTTPS
- DNAT: IP address of internal Exchange server
- Interface matching criteria > Inbound interface: Port2. Inbound traffic arrives Port2 will be checked against the DNAT rule. It is to prevent the DNAT rule from matching LAN-to-WAN, or LAN-to-DMZ traffic.
Note:
- "Interface matching criteria > Outbound interface" needs to be Any in this setup.
- If "Interface matching criteria > Outbound interface" is configured to Port1, the DNAT rule won't match inbound HTTPS traffic arriving Port2.
- "Interface matching criteria > Outbound interface" is normally configured in SNAT rule, where outbound interface is determined by routing before NAT.
- Don't set service to be "Any" in firewall rule and NAT rule, as
- it exposes all service ports of the internal host to Internet, which is a huge security risk, and
- it forwards all traffic to the internal Exchange server, and we are not able to access the Sophos Firewall public IP address for HTTPS, SSH, VPN, etc.
LAN-to-DMZ server via public IP, Full NAT
Network plan:
internal computer, 192.168.20.0/24 --- Port1 [Sophos Firewall] Port6 --- internal Exchange server (in DMZ zone), 192.168.15.15
Sophos Firewall LAN interface Port1 connects to internal computer, and DMZ interface Port6 connects to internal Exchange server.
Internal computers need to access HTTPS service on internal Exchange server via its public IP 10.176.200.58.
There are two steps:
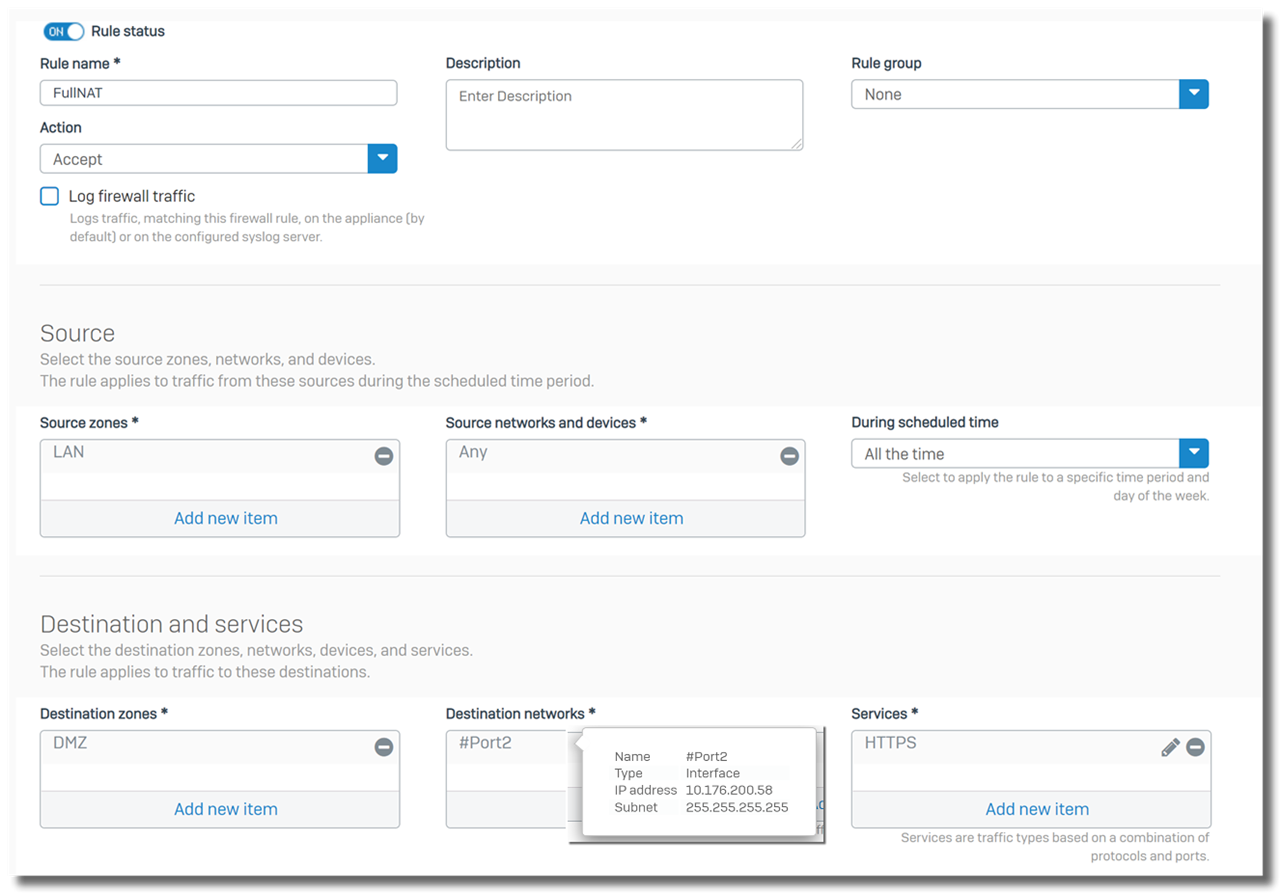
1. create a firewall rule on top of list, to allow internal computers access the Exchange server
- source zone: LAN
- source networks: Any, or specific IP addresses of internal computers
- Destination zone: DMZ, the zone internal Exchange server locates
- Destination networks: public IP address of the Exchange server. In this example, it is 10.176.200.58, IP address of Sophos Firewall WAN Port2
- Services: HTTPS
2. create a Full NAT rule on top of list
- Original source: IP addresses of internal computers. In this example, it is 192.168.20.0/24
- Original destination: public IP address of the Exchange server. In this example, it is 10.176.200.58
- Original service: HTTPS
- DNAT: IP address of internal Exchange server. In this example, it is 192.168.15.15
- SNAT: public IP address of Exchange server, or IP address of Sophos Firewall Port6. In this example, I chose IP address of Sophos Firewall Port6, 192.168.15.254
- Interface matching criteria > Inbound interface: Port1, so that inbound traffic arrives Port1 will be checked against the DNAT rule.
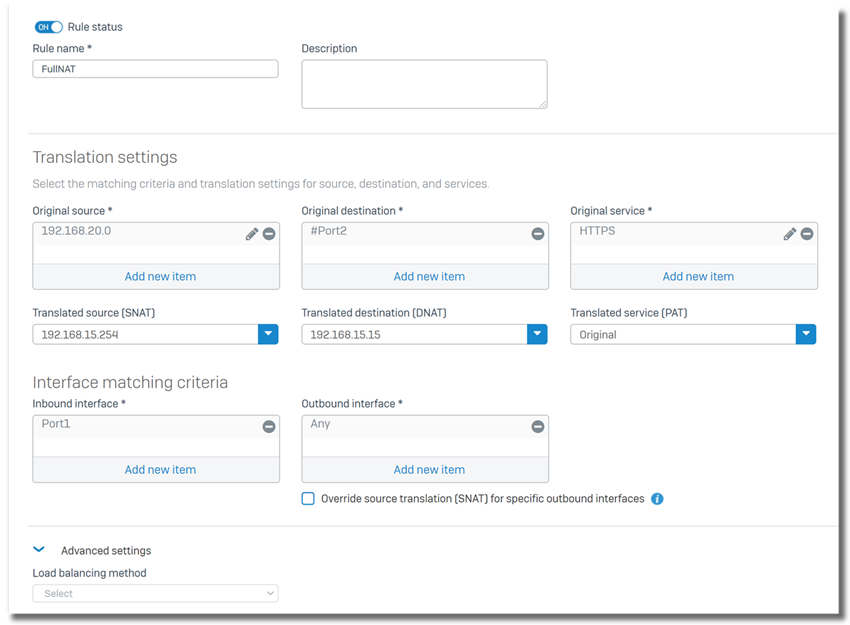
Note:
- "Interface matching criteria > Outbound interface" needs to be Any in this setup.
- The logic of Full NAT configuration is to configure firewall rule and NAT rule for DNAT first, and then configure SNAT in the NAT rule.
Enjoy.
Update history
2022-08-25
- added more explanation about why not to set servcie to be "Any" in firewall rule and NAT rule.
- changed article subject
2022-05-31
- fixed out-of-date URL
- added IP host group "Internet IPv4" into SD-WAN policy route
2021-08-19
- added section "LAN-to-DMZ server via public IP, Full NAT"
- fixed several typo
2021-02-12, added section "specify primary gateway"
2021-01-22, added Interface matching criteria in section "WAN-to-DMZ traffic".
2020-12-23, updated section "LAN-to-WAN traffic".
2020-08-19, changed article subject
2020-07-22, first version.
______________________________________________________________________________________________________________________________________
Updated doc guide and KBA links
[edited by: Raphael Alganes at 12:54 PM (GMT -7) on 22 Oct 2024]