Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended Read describes the Application filter recommended settings for CLI and GUI to block critical/evasive applications such as Psiphon, Tor Proxy (Tor Browser), Torrent, Ultrasurf, HotSpot Shield, etc.
CLI settings
IPS-Settings
- Max Packet value must be at least 80
- Max Session byte values must be 0
- Packet Streaming must be ON
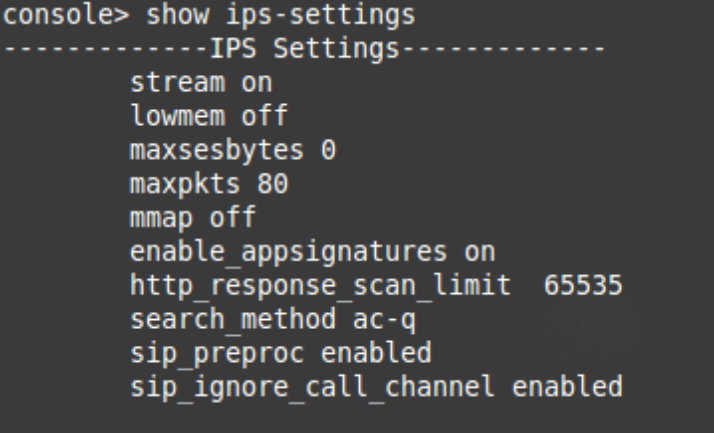
To verify the current configurations, log in to Sophos Firewall Console and select 4. Device Console
show ips-settings
To set the following commands for the recommended settings, you may follow the below configurations
set ips maxpkts 80set ips maxsesbytes-settings update 0
set ips packet-streaming ON
Advanced-Firewall Settings
- Midstream Connection Pickup must be OFF
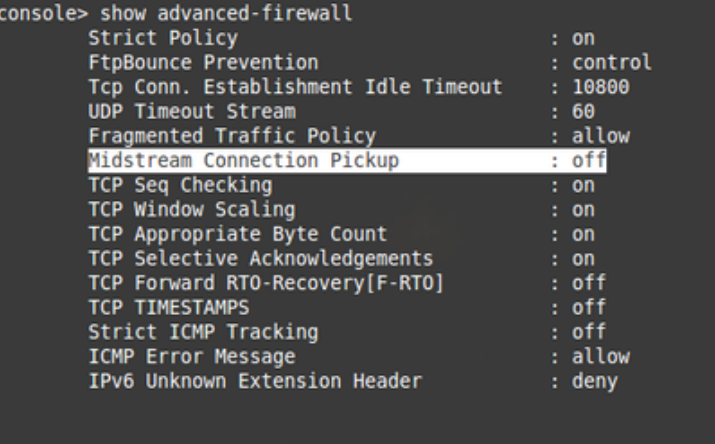
You may verify and set the commands by following the commands below.
show advanced-firewall
set advanced-firewall midstream-connection-pickup off
GUI settings
Application filter policy settings
Along with the "P2P" and "Proxy and Tunnel" categories, applications listed below must be denied in the concerned application filter policy.
- DNS Multiple QNAME
- OpenVPN
- QUIC
- Non-SSL/TLS traffic on port 443
Firewall rule settings
The same application filter policy (as configured above) must be applied to the "DNS Firewall rule" if there’s one.
For Psiphon Proxy
1. SSL/TLS inspection must be turned on under SSL/TLS inspection settings, and one decryption rule needs to be created based on firewall rules.
a. Action must be "Decrypt."
b.Profile is set to "Maximum Compatibility"
2. In the firewall rule, Legacy Proxy has to be "Disabled" (web Policy = None).
3. Block Invalid Certificates (PROTECT>web>General Settings>HTTPS decryption and scanning) must be turned on in SFOS.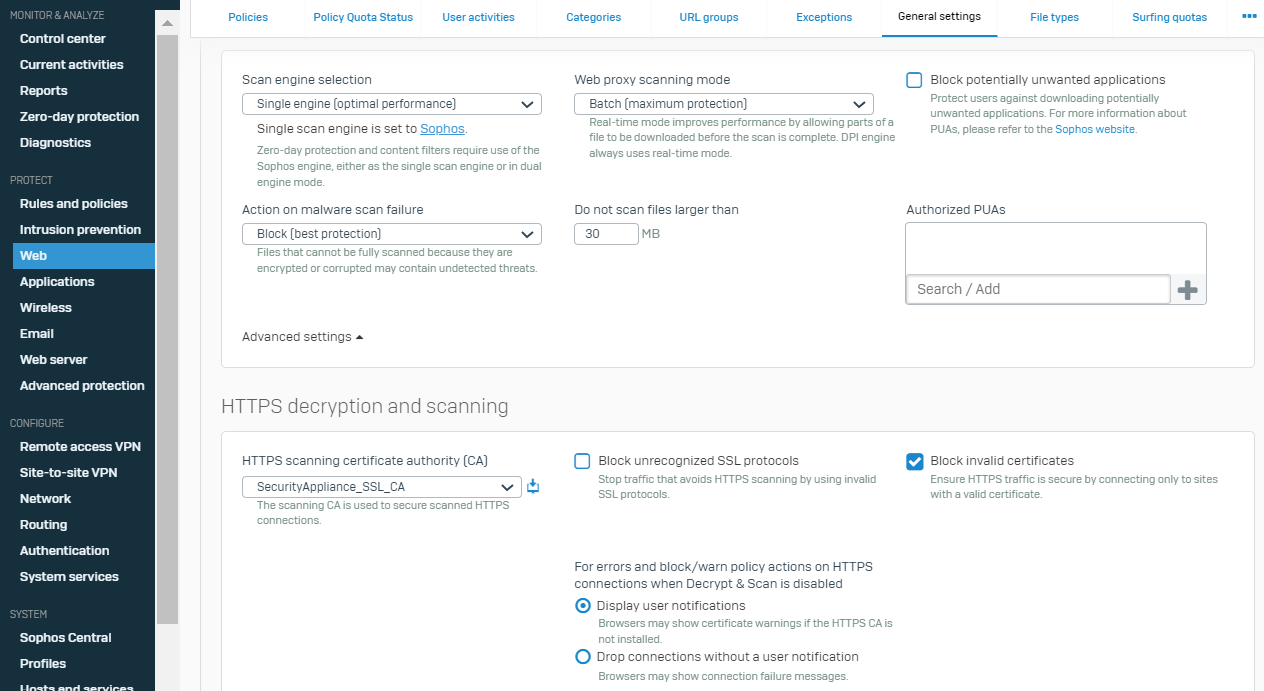
4. Allow only HTTPS, HTTP, DNS, ICMP, and SMPT. Services on LAN/WAN: If the Psiphon is connected even after following all the steps, other port traffic may pass through other firewall rules (one can allow 1025 to 65535 Ports).
a. For example, the primary rule must only allow limited services.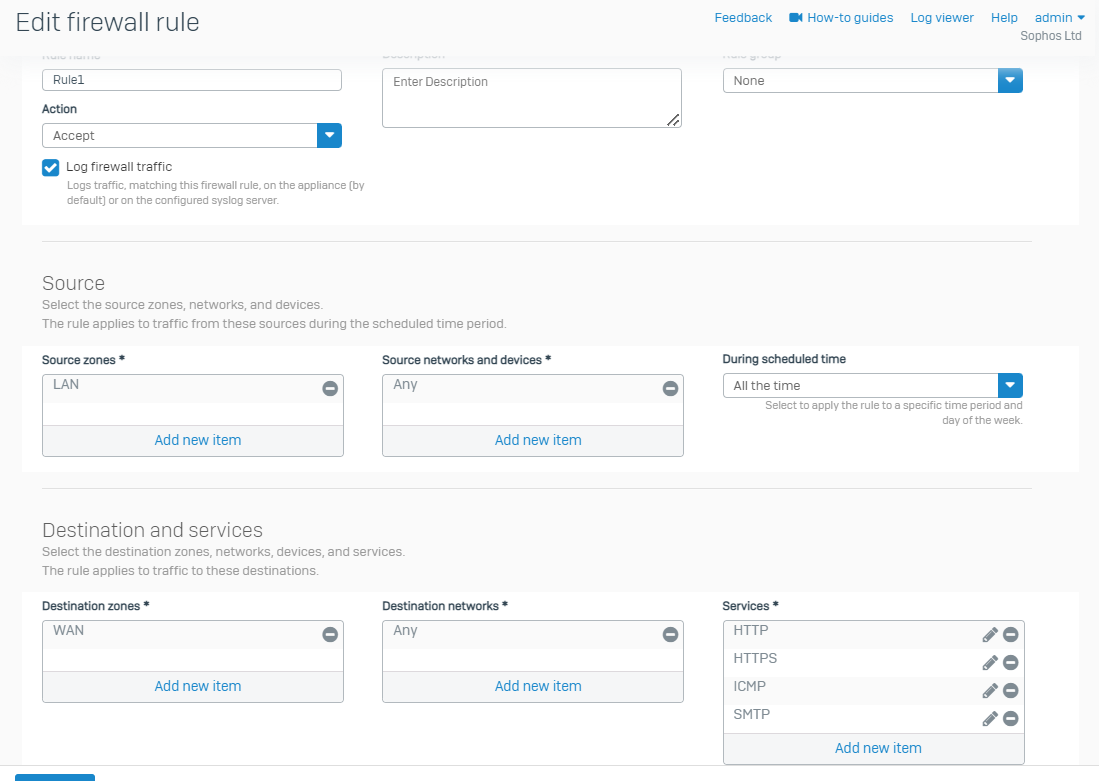
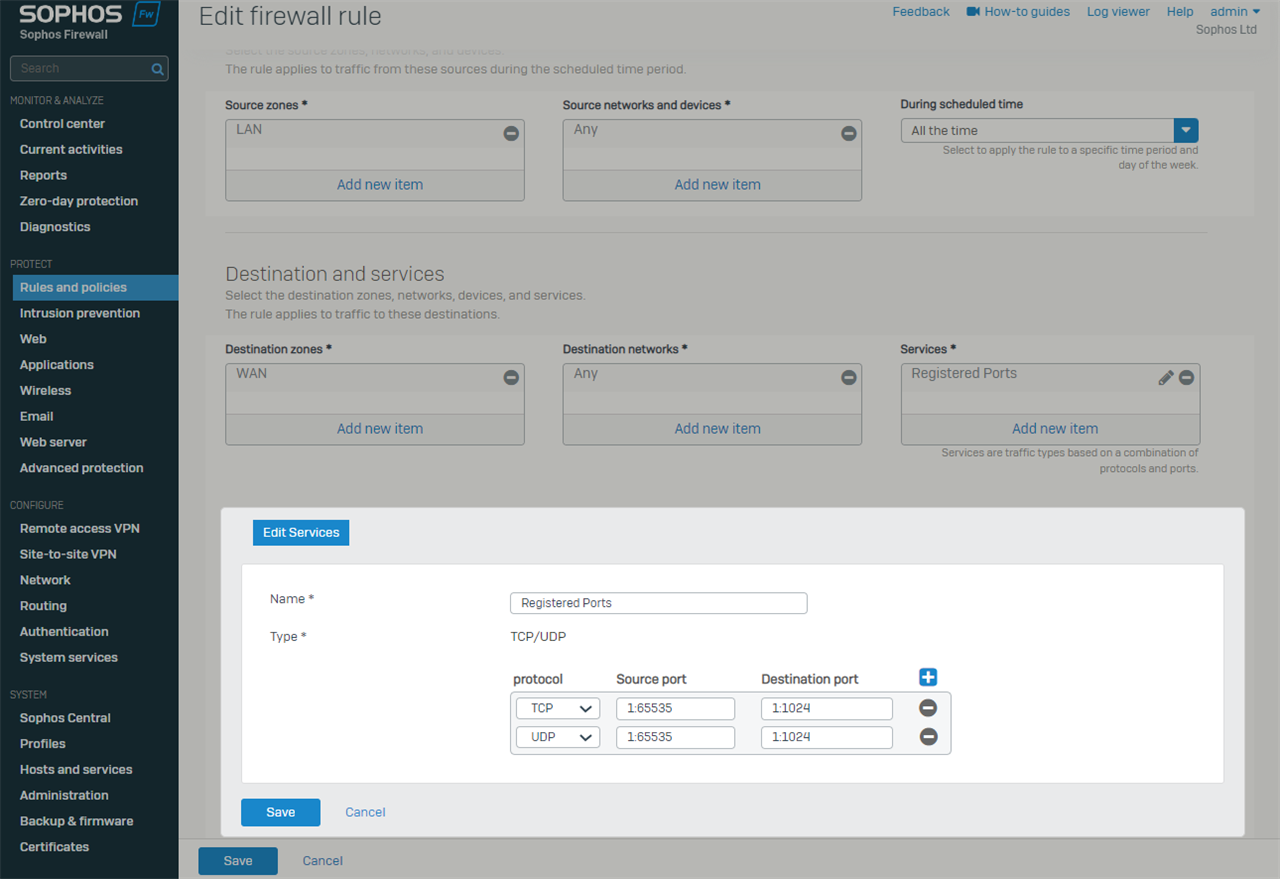
b. And the rule below the primary rule must 'deny' traffic for port ranges 1 to 1024 (Registered Ports) for the same source machines.
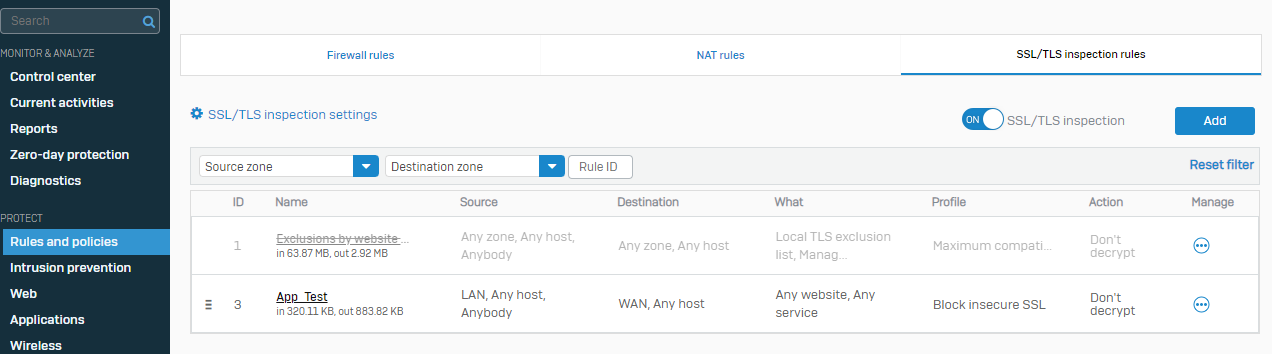
Betternet VPN
To block Betternet VPN, We have to block Invalid Certificates (Usually used by Such Proxy applications). Perform the below steps to
reach out to set
- CLI + GUI Settings mentioned above.
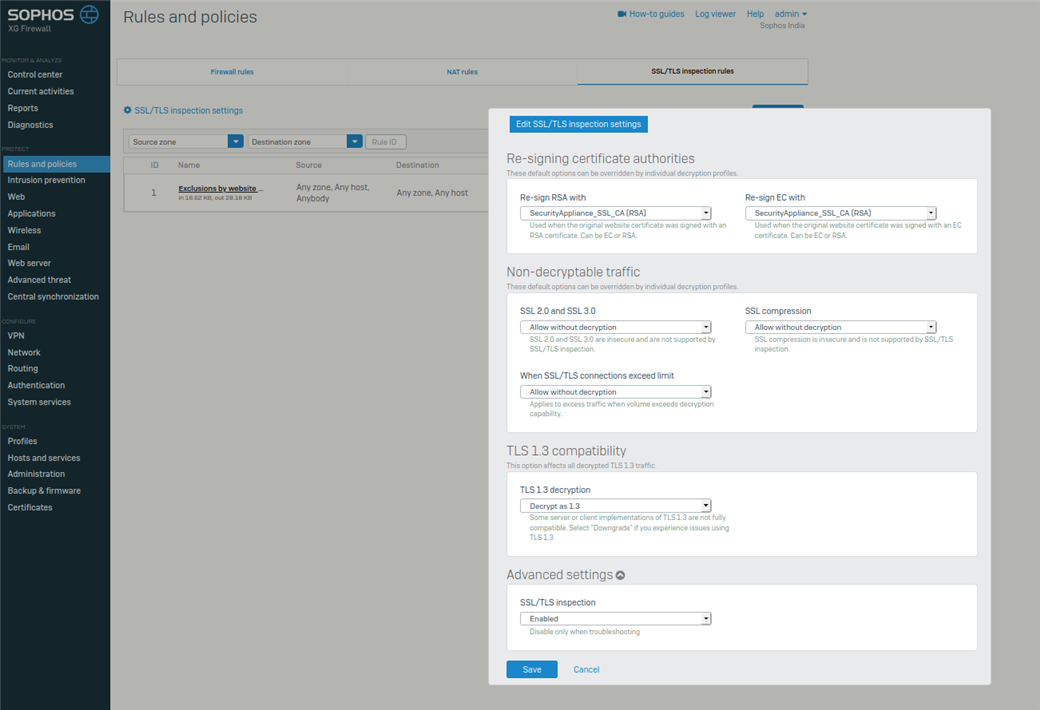
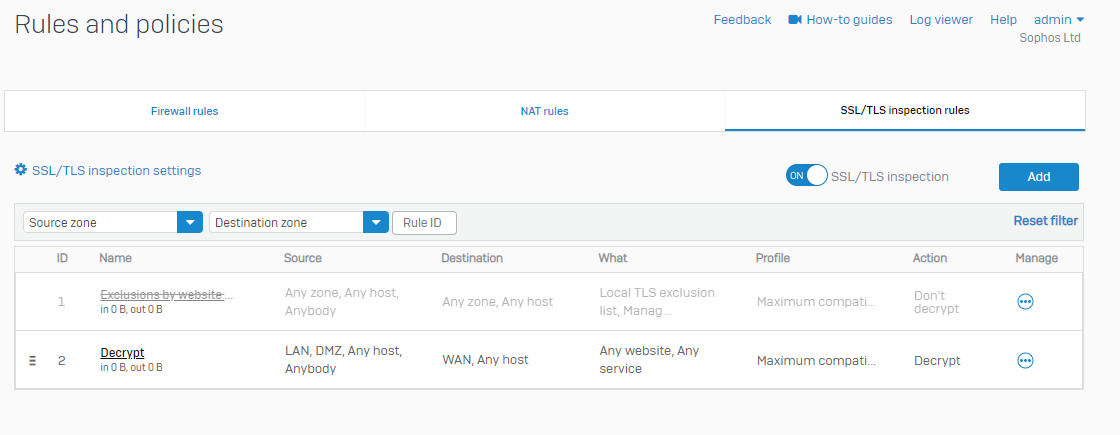
- In SFOS UI> Rules and Policies > SSL/TLS Inspection Rules> Create a rule with Action "Don't Decrypt" and Profile as "Block Insecure SSL".
- Turn off the Default rule "Exclusions by the website."
Hot Spot Shield Proxy
- Turn on HTTPS scanning.
- Configure all CLI and GUI settings.
- Turn on the option on the web > General Settings > Block unrecognized SSL protocols.
- Turn on the option on the web > General Settings > Block invalid certificates.
Corrected Grammar,Horizontal Lines and added TAG
[edited by: Erick Jan at 1:51 AM (GMT -7) on 10 Oct 2024]