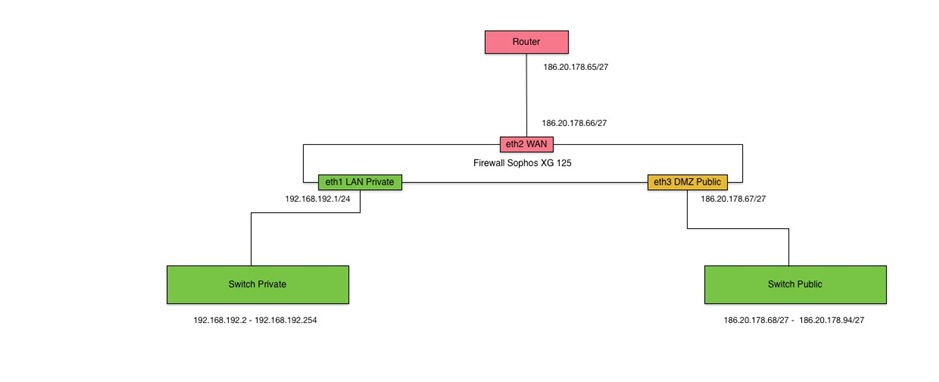
Hello
I want to configure my Firewall to have a private LAN with private IP Addresses and a DMZ Zone with our public range (255.255.255.224).
In the public zone it must be possible to reach the devices directly by public IP address and to connect via VPN to have access to data in a secure way.
How it could be done?
I created a simple picture for illustration.
Thank you for replying.
Regards
This thread was automatically locked due to age.