UTM only supports IKEv1 (so a wildcard gateway address with psk and local\remote IDs configuration has not been tried - this system has over 15 VPN Tunnels)
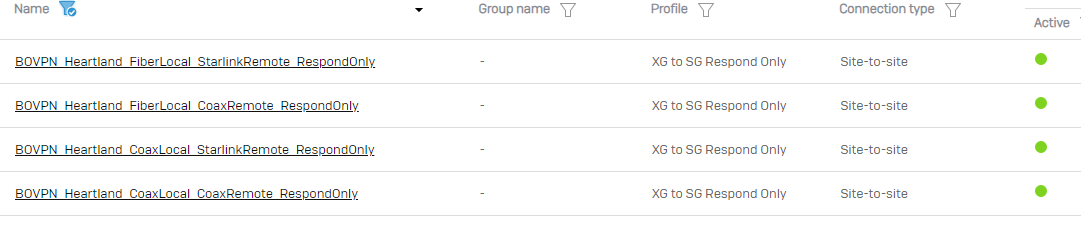
My XGS has been setup with a proper profile to allow IKEv1 UTM devices to initiate a connection to it, and my XGS has quite a few VPNs setup in respondonly mode
In the case of 1 particular VPN scenario, the remote UTM is behind a dynamic IP
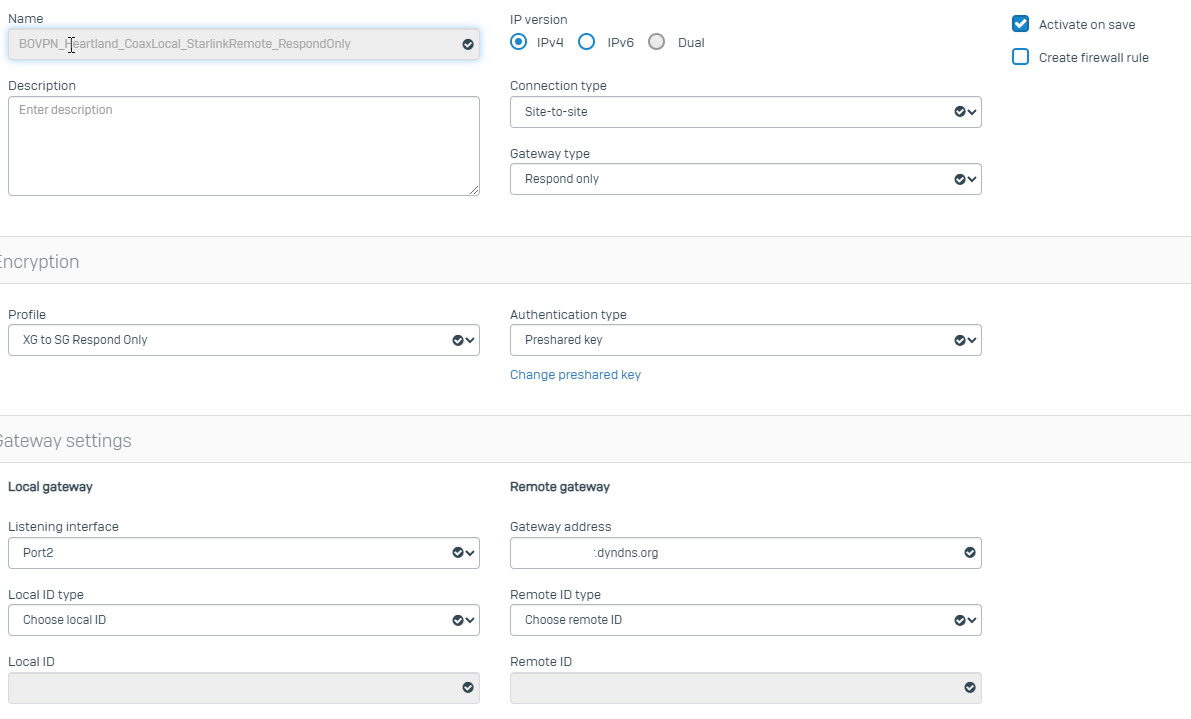
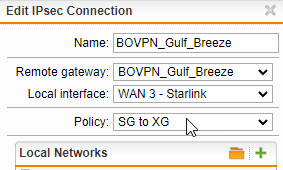
If I set my XGS Gateway Address to the (current) IP of the remote UTM, the connection is established and all works well.
If I set my XGS Gateway Address to an FQDN which resolves (accurately, via DynDNS) of the remote UTM, the connection never establishes, and the log files appear as far as i can see, to be sparse.
When I use the FQDN in the Gateway Address field, the log file simply says:
|
IPSec
|
Deny Session
|
|
(unnamed) - Couldn't authenticate the remote gateway. Check the authentication settings on both devices. (Remote: xxx.xxx.xxx.xxx)
|
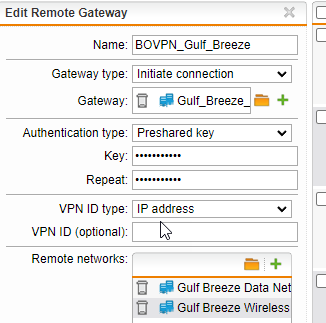
For both of those instances above, I leave the Local ID and Remote ID as not chosen. I have tried setting 1 or both of them statically to an email or a dns host name (and setting the VPN ID on the UTM side to match) but it doesn't appear to help. *in fact, i believe i tried setting them while using the aforementioned numerical IP input above for the Gateway Addrss, and in that case it "breaks" and does not establish the connection, unless i missed a configuration variety, i believe that might relate to the IKEv1 \ v2 from how i read the help file
Leaving the VPN ID Type as IP Address on the UTM Side, but not specifying it, tells it to use the IP address of the interface it is going out of
I am at a loss for why I can't seem to get the XGS to establish a connection when using an FQDN, as the help file says "You can use a DNS hostname when the remote gateway has a dynamic IP address"..but doesn't go so far as to conclude with on a respond only mode in addition to an initiate connection mode.
thanks for any insight
clarification and typos
[edited by: HopefulSoul at 3:54 PM (GMT -8) on 15 Jan 2025]