Hello, everyone.
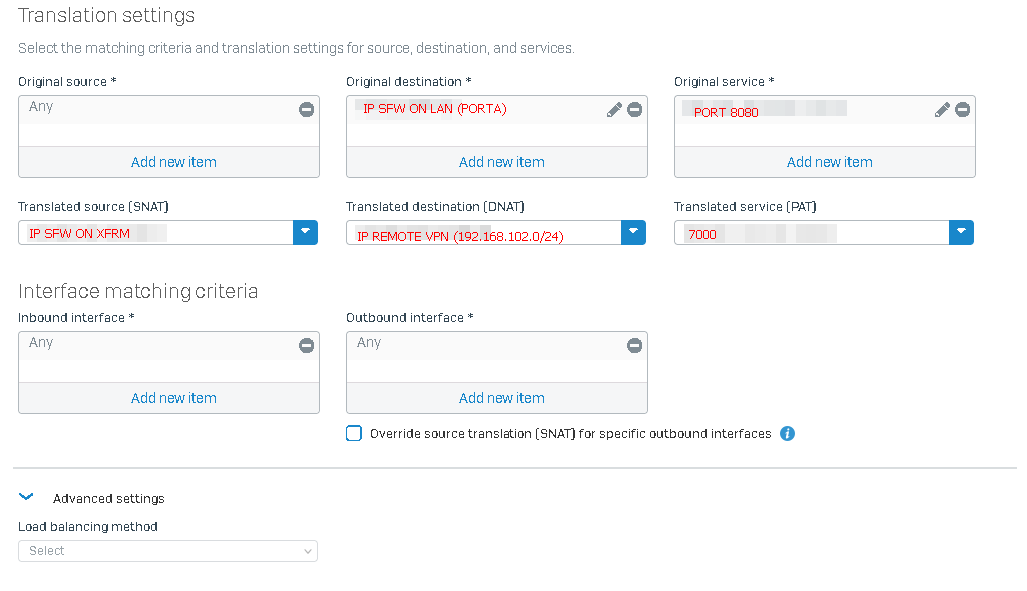
I created a DNAT rule. I receive the communication on the local interface at the SFW's IP address on the LAN and translate it to another destination that is remote on the VPN. I force a SNAT with the SFW's IP address that is assigned to the xfrm interface.
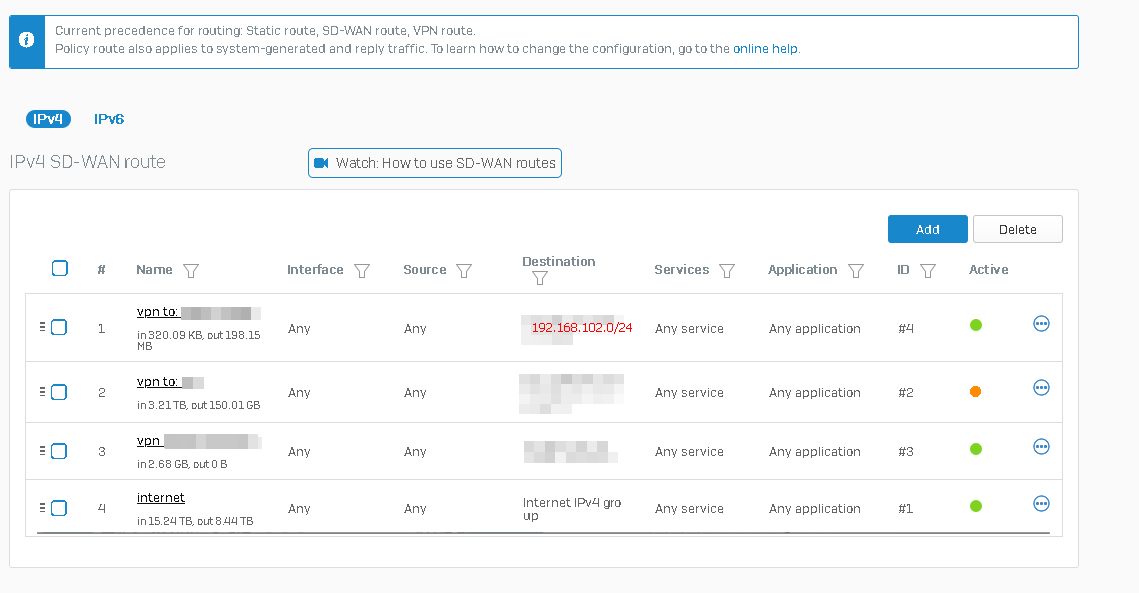
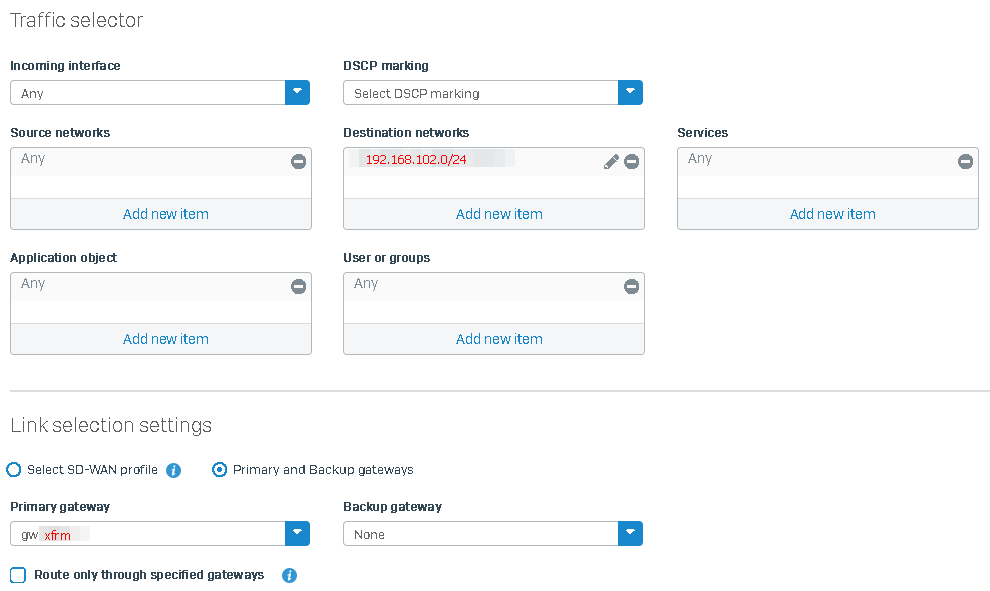
In short, it looks like this:
Source: Any host
Service: TCP 8080
Destination: Interface PortA (IP 192.168.101.1)
Source: IP 172.16.0.1 (IP on the XFRM interface)
Service: Original
Destination: 192.168.102.1
Inbound: Any interface
Outbound: Any interface
I have a firewall rule created to allow this communication.
I capture the packets and see that the NAT and FW rules are correct and the traffic passes through. However, the outgoing interface is not XFRM, it is PortB, which is on the Internet. It should not go out through this interface, but through XFRM.
I noticed that the problem only occurs when it points to the IP of PortA, which is directly connected to Sophos. If I change it to any other destination that is not a Sophos interface, for example 192.168.101.10, the SNAT rule works.
What am I missing here?
The Sophos version is 19.5.1
Thanks for your support and time reading.
Edited TAGs
[edited by: Erick Jan at 12:12 AM (GMT -8) on 13 Nov 2024]