We have AD synced Groups. We use them for FW Rule permissions, SSL VPN access and MFA control on the Firewall.
Now we have this scenario:
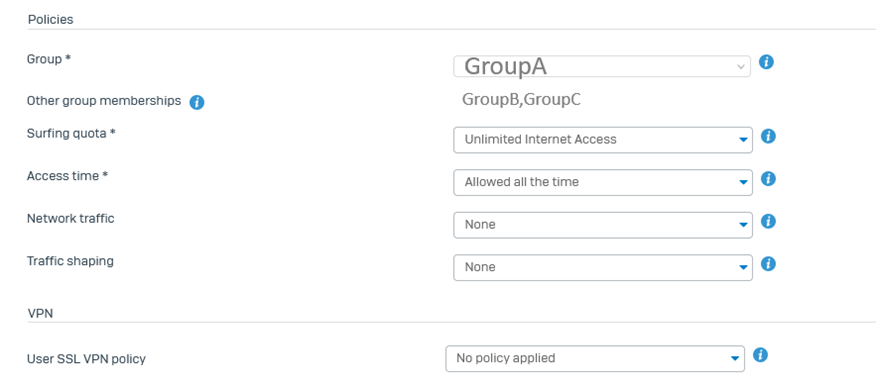
User XY is member of these groups:
Group A (used for a firewall rule)
Group B (all members of the company, used for MFA assignment)
Group C (some members of the company, used for SSL VPN profile)
The firewall thinks, Group A is the primary group.
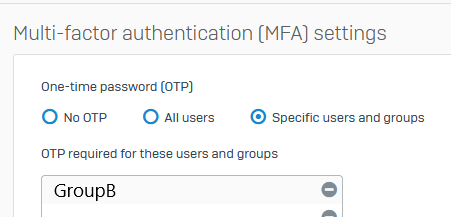
In MFA we use GroupB to define all users must use 2FA.
In SSL VPN Profile we use GroupC. This works.
Unfortunately MFA is not working as expected because the firewall is not offering the QR Code to the user.
This would only work, if we add GroupA to MFA Users. But this sounds false to me.
Also I don't want to add the individual user to the MFA setting which would also work.
How can we assure, the MFA engine accepts all potential groups of a user?
This thread was automatically locked due to age.
