Firewall is able to reach Sophos licensing system
https://eu-prod-utm.soa.sophos.com
in manual setup wizard
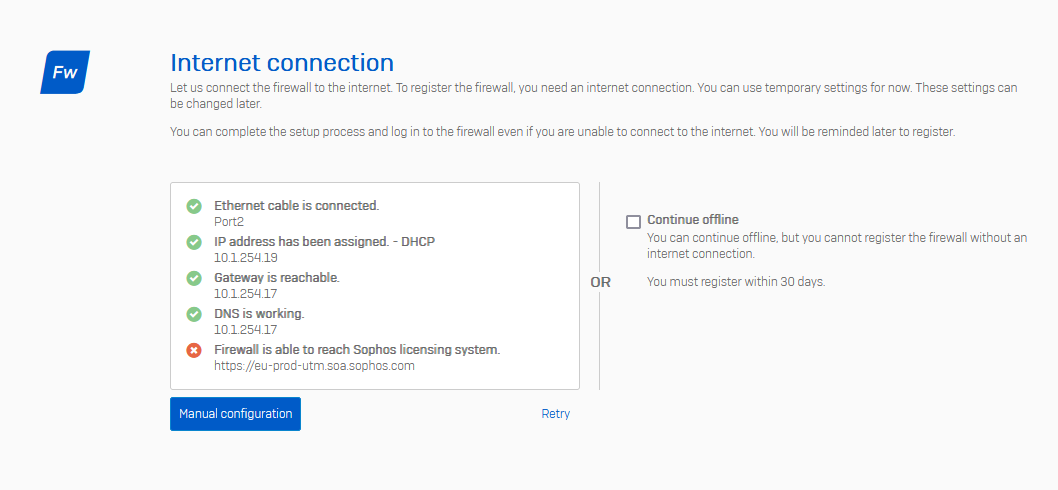
That no NTP server enabled per default flaw should be fixed quickly.
XGS136_XN02_SFOS 21.0.0 GA-Build169# date
Thu Jan 1 01:16:05 BST 1970
XGS136_XN02_SFOS 21.0.0 GA-Build169# ntpclient n -s -c 0 -l
Starting NTP Client v0.0.2
Configuration:
-f inital_freq 0
-c probe_count 0
-d (debug) 0
-g goodness 0
-i interval 600
-l live 1
-T TimeOut 30
-o Offset 900
-q min_delay 800.000000
-s set_clock 1
-H Num of Hours 24
-x cross_check 1
-p local_port 0
-L LogFile 'STDERR|STDOUT'
-D Daemonize 0
-h Host pool.ntp.org
ERROR Jan 01 00:16:53Z [13616]: setup_receive: bind for fd,family (3,2)
ERROR Jan 01 00:16:53Z [13616]: setup_receive: bind for fd,family (4,10)
MESSAGE Jan 01 00:16:53Z [13616]: Switch to Server 'pool.ntp.org' => '167.235.70.245'.
MESSAGE Jan 01 00:16:53Z [13616]: ntp_step called
MESSAGE Oct 18 14:47:10Z [13616]: ntp_step called
MESSAGE Oct 18 14:47:12Z [13616]: Set time to : '18-10-2024 15:47:10'.
MESSAGE Oct 18 14:47:12Z [13616]: Shutdown NTP-Client
then it worked
manual config wizard finished and brought me to the EULA page
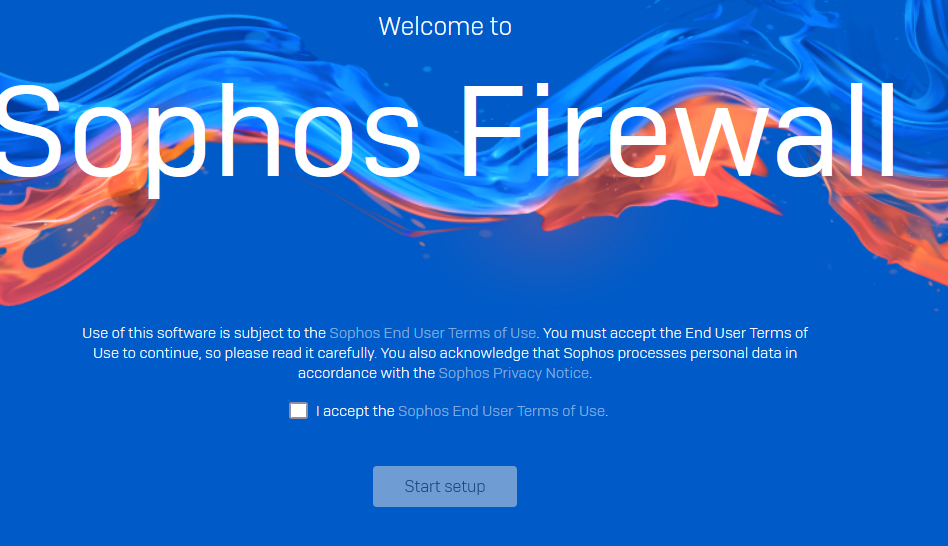
Added TAGs
[edited by: Erick Jan at 12:21 AM (GMT -7) on 21 Oct 2024]
