Hi,
what would be the proper way to configure different WAN ALIASES for outbound traffic, for example in this manner:
- LAN users would use WAN Alias 1 for browsing and accessing web
- LAN2 users would use WAN Alias 2
- FreeWiFi users would use WAN Alias 3
I have WAN configured as IP 1.1.1.218/28 (with gateway 1.1.1.217).
Then I configured WAN ALIASES as 1.1.1.219/32, 1.1.1.220/32, 1.1.1.221/32 and 1.1.1.222/32
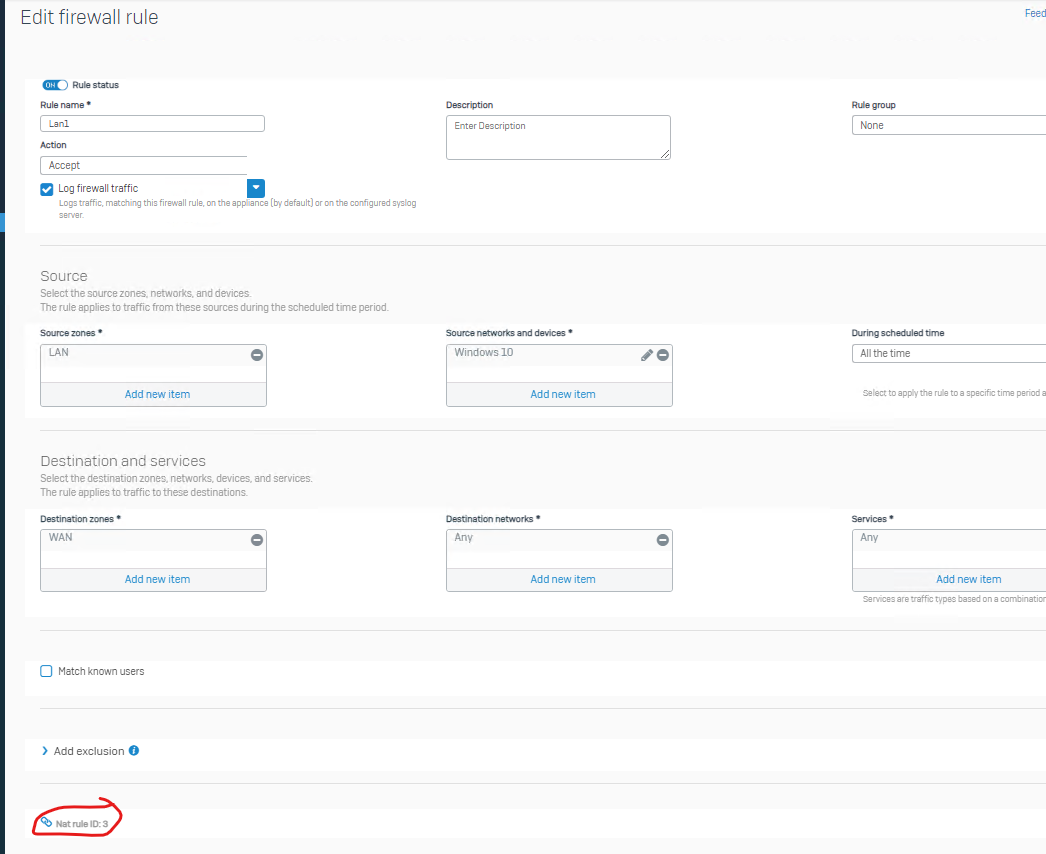
Then I created Hosts objects for each alias.
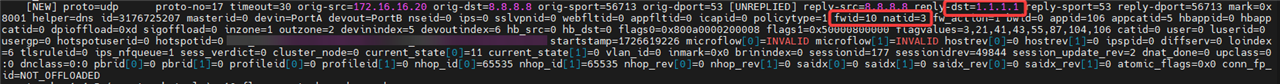
Now here's my dylema: Do I need to configure multiple MASQ NAT rules for each outbound traffic?
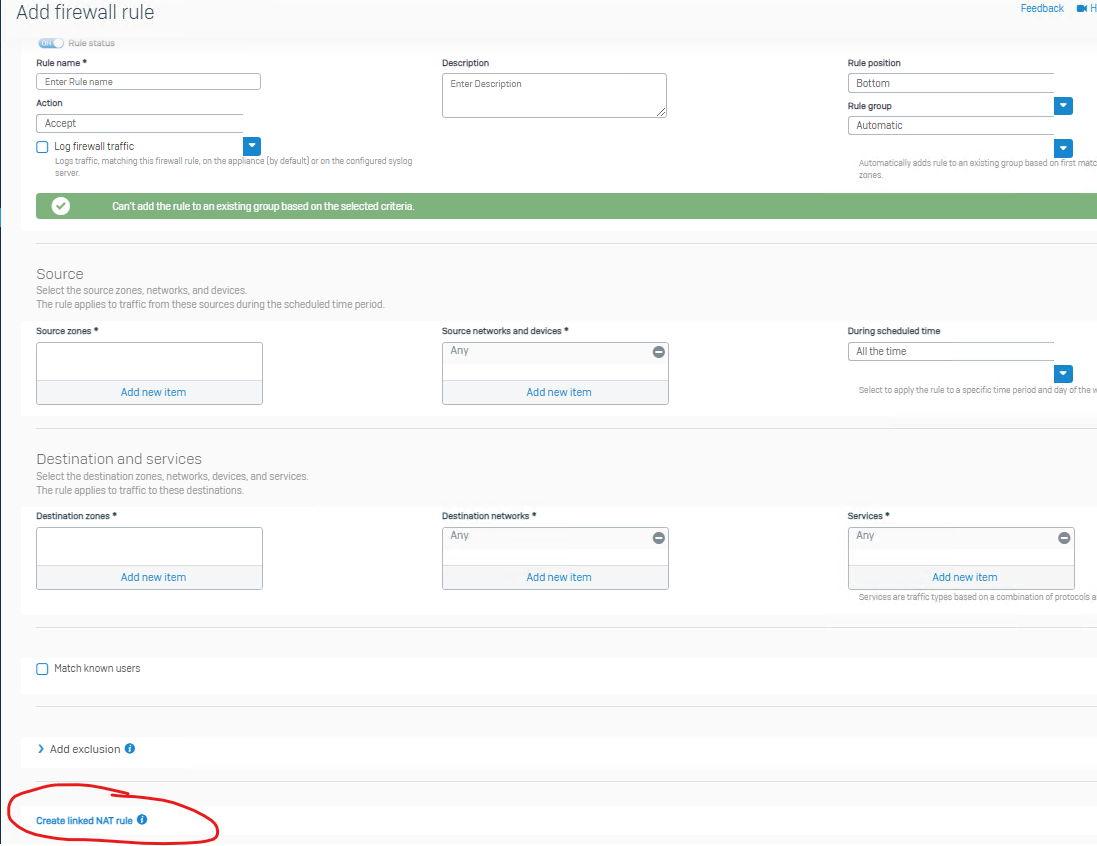
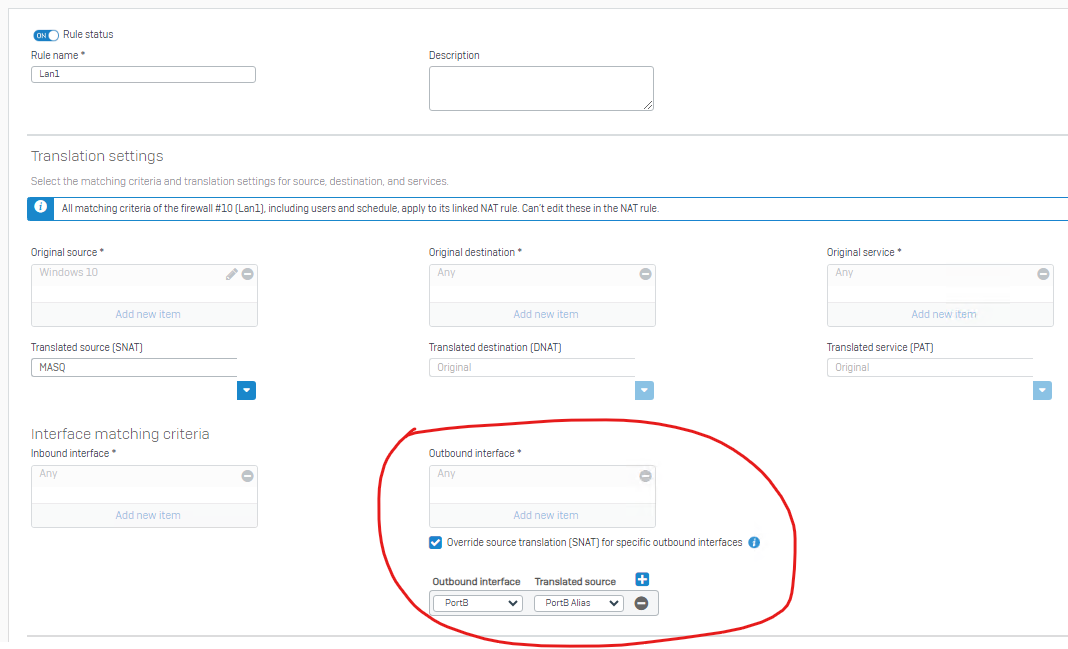
For example, I would create MASQ NAT rule, with ORIGINAL SOURCE=LAN, OUTBOUND INTERFACE=WAN Port2, and Override SNAT=Translated source to WAN ALIAS.
But what about #NAT_Default_Network_Policy default MASQ rule? Should I place mine below or above this one?
Or is there some better/proper way to do outbound routing?
This thread was automatically locked due to age.