Hi,
I have set up email scanning according to this guide: https://docs.sophos.com/nsg/sophos-firewall/20.0/Help/en-us/webhelp/onlinehelp/AdministratorHelp/Email/HowToArticles/EmailConfigurePOPIMAPScan/index.html#add-a-firewall-rule
I have found that the certificate used by the firewall to decrypt the mail traffic contains empty fields and non ASCII character. Note: "domain.local" is just replaced values from the "correct values".
DNS:domain.local, DNS:domain.test.local, DNS:domain.test2.local, DNS:S¼Ax, DNS: , DNS: d
This (four last rows) is automatically added (to the certificate - presented from firewall) when you "enable" scanning for IMAPS and/or POPS in the firewall rule.
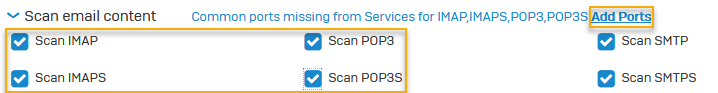
If you disable scanning for IMAPS in the firewall rule, these values will be removed. The certificate then only shows the correct sub alt. names (presented from the mail server).
DNS:domain.local, DNS:domain.test.local, DNS:domain.test2.local
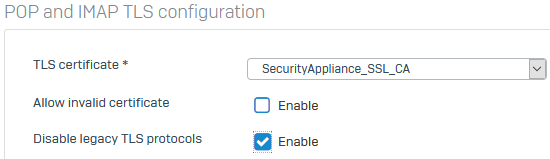
The certificate selected for POP and IMAP TLS configuration is the CA certificate for the mail server.
Below you see an example of where it is activated in the configuration.
Now to my questions,
- Why does it behave this way?
- How do I configure the firewall, so that these strange characters are not added to the certificate when scanning IMAPS and POPS?
- Is there something that I have configured wrongly?
Update:
Forgot to write how the result was presented. I ran into some issues with some email clients not accepting the certificate. I then used OpenSSL to get feedback from the connection.
openssl s_client -showcerts -connect domain.local:993 | openssl x509 -text -noout
Regards,
Triune
This thread was automatically locked due to age.


