Hello,
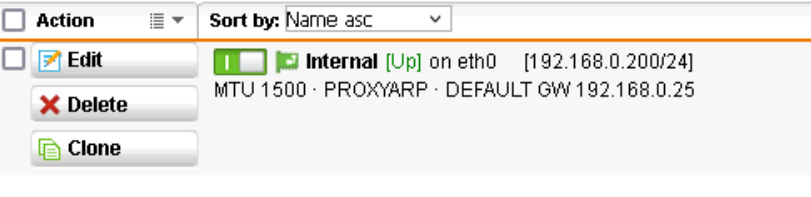
I try@home to migrate from UTM zu SFOS. On the good old UTM there was only one LAN Interface. This was the gateway for some PCs.
At the network configuration on the UTM, I configured the real-router-getway as gateway in this one UTM NIC. It has worked.
Now at SFOS I cant configure a gateway at the LAN (also only one NIC) interface.
What would be the 1:1 configuration for SFOS like the UTM was?
best regards
michael
This thread was automatically locked due to age.