Hello everyone,
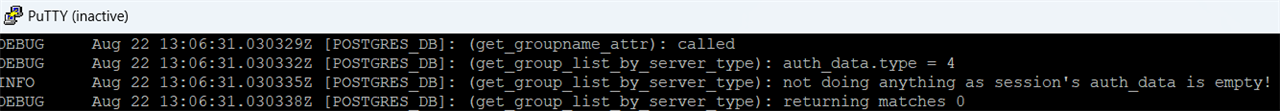
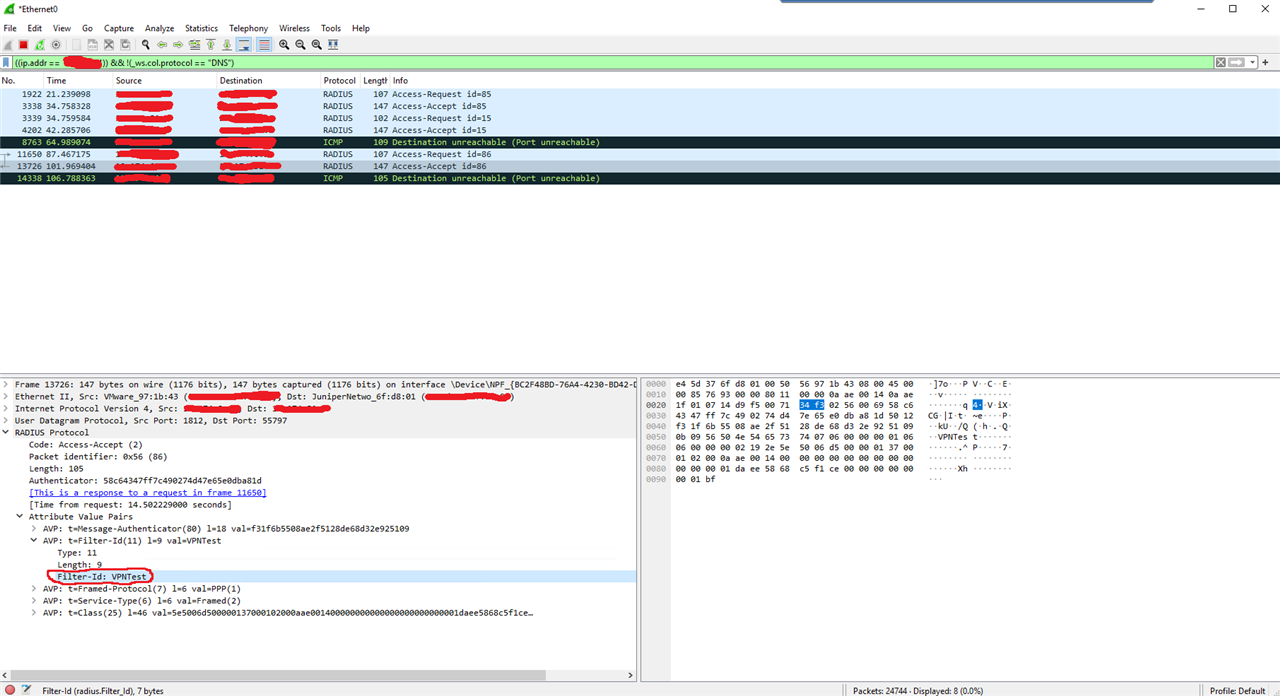
I have issue with Sophos XG firewall running SFOS 19.5.4 MR-4-Build718 configured for authentication via RADIUS server running on Windows Server (NPS service) with Azure MFA extension. We use it for MFA for VPN users. It works fine except recognition of user group membership returned in Filter-Id field by NPS server. I have checked with Wireshark that NPS service returns Filter-Id field containing correct user group. However, Sophos XG accept response from NPS server and user get authenticated but user group is not recognized and user falls into Open Group only. Note that I have configured Filter-Id as Group member attribute in Sophos XG definition for RADIUS server. In addition, have checked debug access_server.log on Sophos XG firewall and found following:
This thread was automatically locked due to age.


