I have enabled SSL/TLS inspection to do MITM for HTTPS(443) trafic from LAN to WAN. I have push by GPO certificat CA to windows computer. That work just fine for most site.
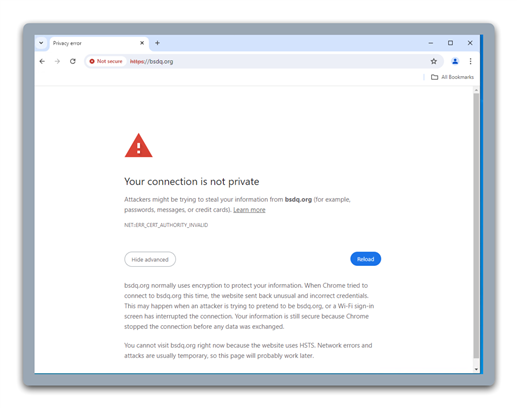
Now I have an issue with site that have HSTS enabled.
For those site that enable HSTS. I have to add site to web / URL groups / Local TLS exclusion list and need to maintain that exclusion list so they are not decrypted.
But what if I want the automaticaly exclude site with HSTS enabled ?
What we know is that HSTS is enabled with a property set in the html header.
Date: Fri, 09 Aug 2024 18:58:44 GMT
Content-Type: text/html; charset=utf-8
Transfer-Encoding: chunked
Connection: keep-alive
Location: /fr/
Vary: Cookie
Strict-Transport-Security: max-age=15724800; includeSubDomains
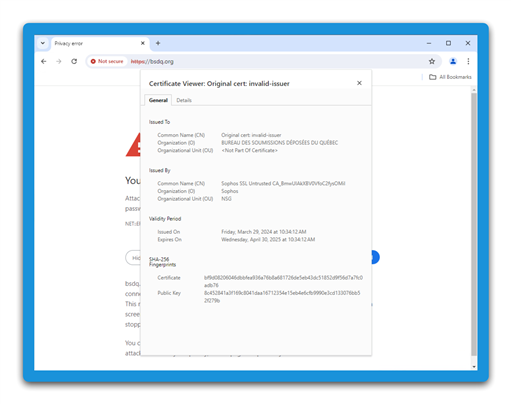
SSL/TLS allow for 2 types of exlusions, certificat and web category (or URL). HSTS is enabled in the web page header with property, so certificat property can not be user to "do not decrypt" HSTS site.
Now looking a web site category, I can define a new one. Web site can be categorized by URL, back to square 1 whre I have to maintain a list of URL. That leave me with "keyword". I have try to set Strict-Transport-Security as keyword, but look like header is not scanned for keywords. No luck...
Is there a way to automatically detect website with HSTS enable and "do not decrypt" these, or put website with HSTS in a specific URL categorie to skip them ?
What are you doing ?
This thread was automatically locked due to age.