Hello,
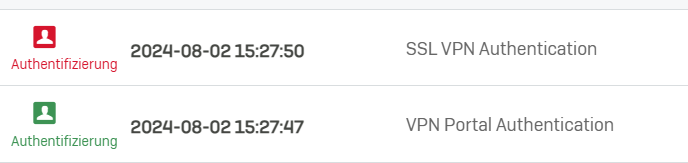
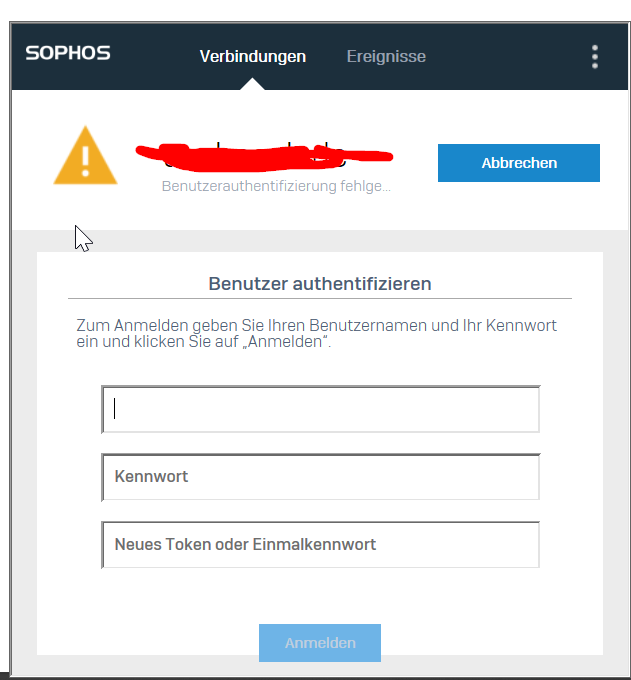
we build a Sophos Connect Provisioning File for our XGS 3300 on FW 20MR1. We have the following Problem. If the Users "starts" the provisioning File and Enter his Credentials for log in, he gets an UserAuthentification error - with the Correct Credentials. After checking the SSL-VPN Client we can see that the process worked - the Users has the new .ovpn config after login.
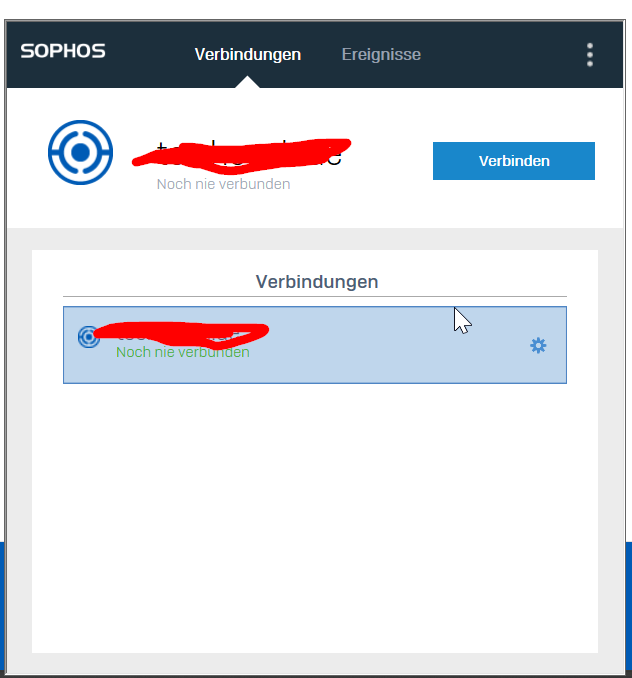
My Problem is that there is always an error displayed and no success information when the new config is downloaded. So our users dont get the Displayed Information that the renewal is done. When they now click on abort/cancel they can connect with the new/latest config. Is there any way that the user gets an information that the config Update was successful?
This thread was automatically locked due to age.