HI - Time sensitive here, back against the wall (will pay outside consultant if needed). Sophos Partner, long out of the loop.
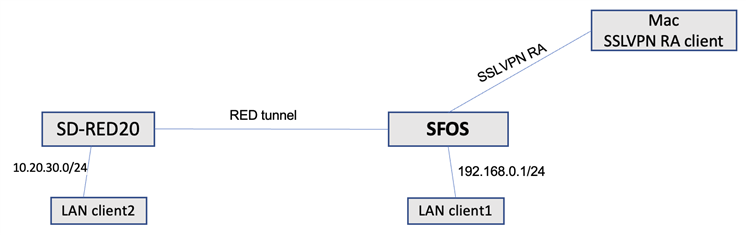
I have (2) REDS. Both are reachable from main XG network. I am unable to reach the RED hosts from the SSL VPN.
REDS are in standard split tunnel
RED1 - 10.20.30.0/24
RED2 - 10.20.31.0/24
XG LAN 192.160.0.0/24 (don't ask, I inherited)
SSLVPN 10.81.234.5/24 (oddity there in definition, but should work as it i a /24)
Defined host networks for all.
REDS have local subnet and ssl subnet in split network settings boz
Firewall rule to allow SSL network to RED networks
Logs show nothing being blocked.
I am at my wits end and have to have these routing by Friday.
Any help would be appreciated.
This thread was automatically locked due to age.