I have something strange for the following situation.
VPN connection between site A and site B (tried both policy-based and route-based) and a policy-based VPN-connection between site B and site C.
Intention is to reach site C from site A while there is no possibility to add Site A's subnet to the tunnel between B and C. Therefore from B the traffic should be SNATted to a site B ip-address.
- Site C's subnet is in the tunnel between site A and site B.
- Site A can succesfully reach resources at site B.
- Subnet Site A: 10.0.0.0/24
- Subnet Site B: 192.168.21.0/24
- Subnet Site C: 10.23.1.0/24
At site B we did a packet capture to see what happens with the traffic and this is what happens with a ping from site A to site B, which is expected output, packet comes in gets forwarded, reply comes in and gets forwarded back to source:
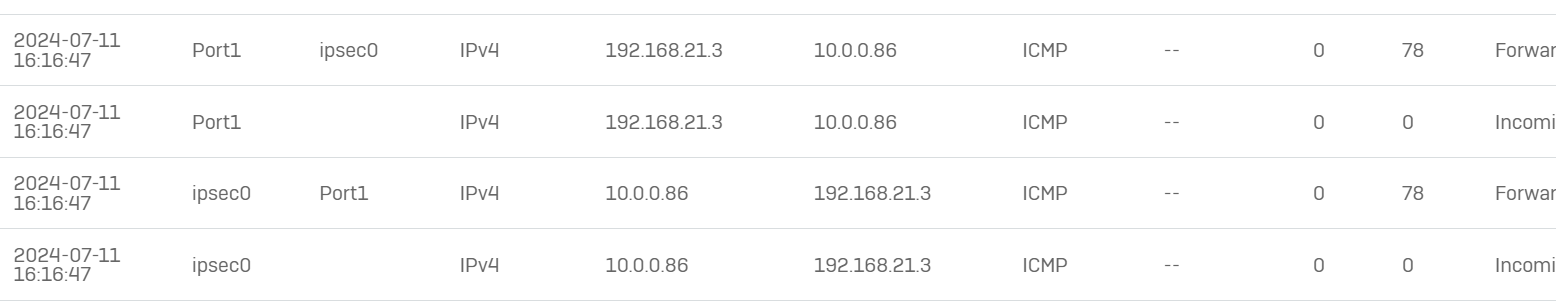
However, when pinging to site C we see the packet arriving on ipsec0 just as above, then the second packet is weird; it lists traffic from ipsec0 to ipsec0 as status Generated (and not forwarded) with the source and destination address inverted and from the pinging station at site A they receive a really strange output:
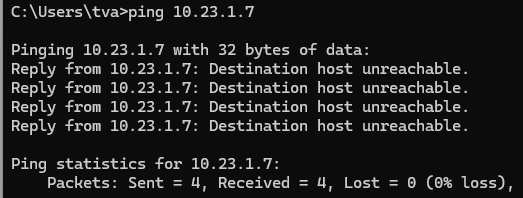
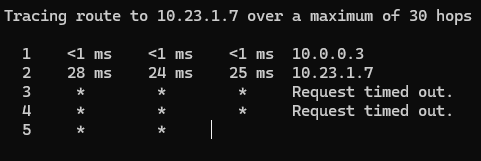
- I tried adding ipsec_route to 10.23.1.0/24 net from the console at site B
- tried it without the ipsec_route
- for route-based VPN I also created a SD-WAN route to 10.0.0.0/24 network to the tunnel interface
- Route precedence is: VPN, SD-WAN, Static
- tried to NAT traffic for 10.23.1.0/24 with firewall rule with Linked NAT rule
- tried to NAT this subnet directly from the policy based ipsec connection
Most of the time it is just a request timeout and at some config we got the above strange output from ping.
Site A is a OPNsense firewall, site B is the Sophos XG with 19.5.3 MR-3 version on it. Site C has Cisco firewall IIRC.
I don't know what else I can try or where I am making a thinking fault. I have similar setups on other sites where traffic from A is SNATTED at B to C and they all work flawlessly, but not on this occasion.
Anyone have a clue what I'm missing and why the packet capture status says Generated instead of Forwarded?
This thread was automatically locked due to age.

