Hello there.
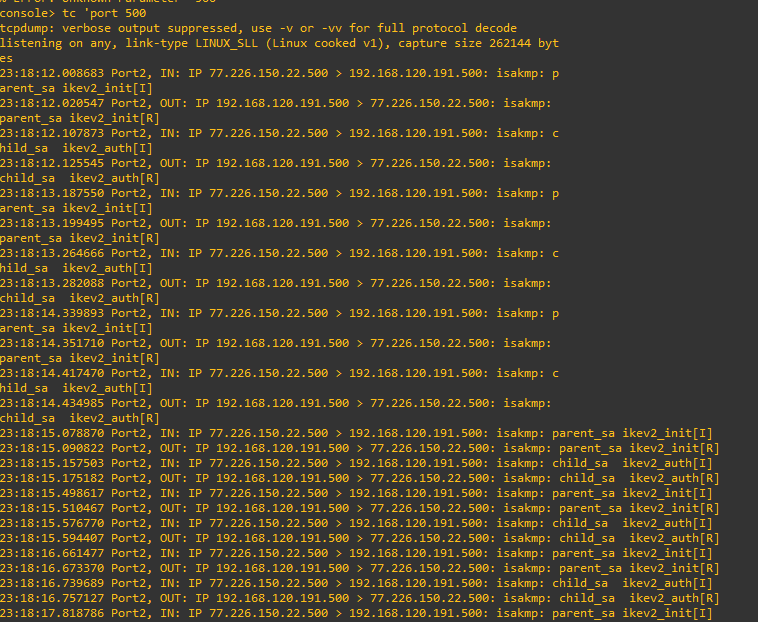
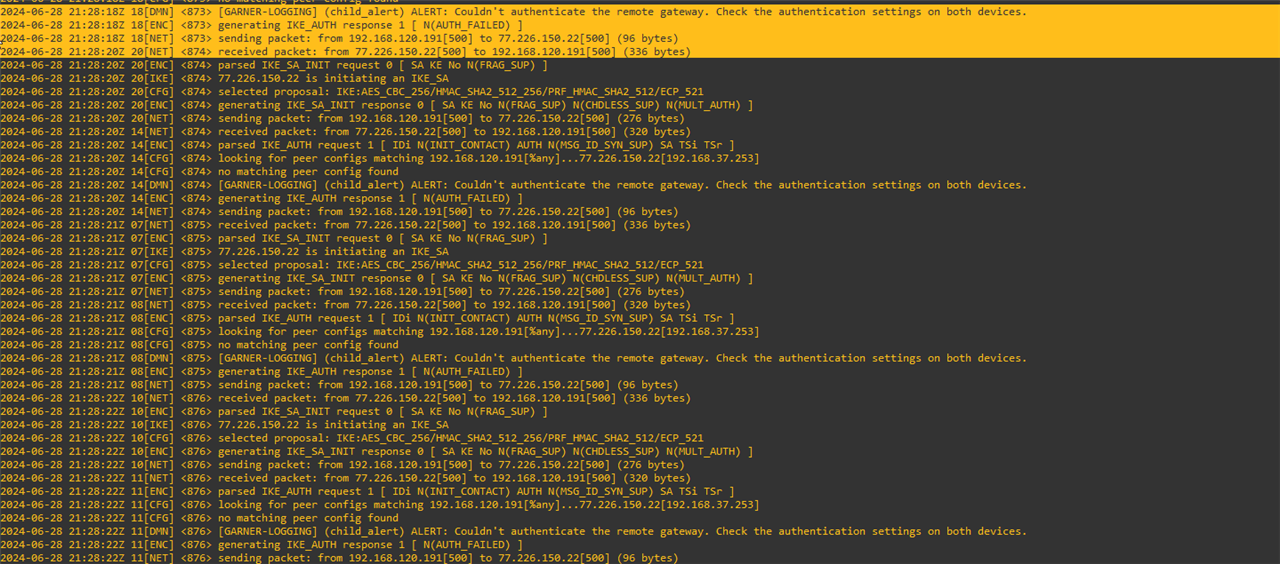
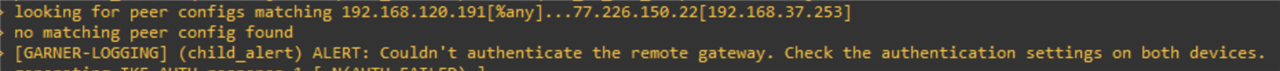
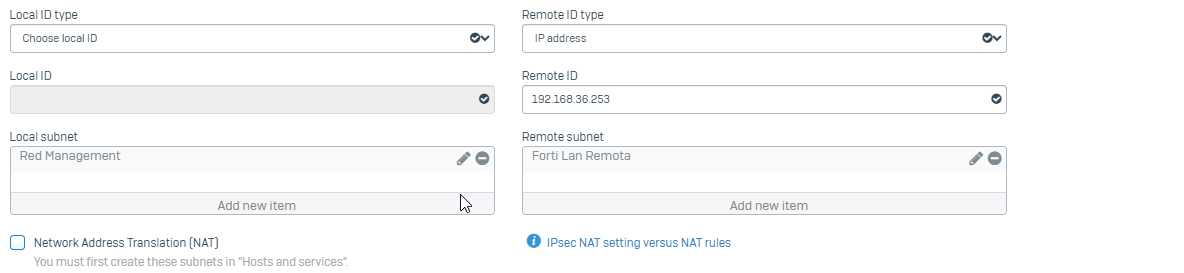
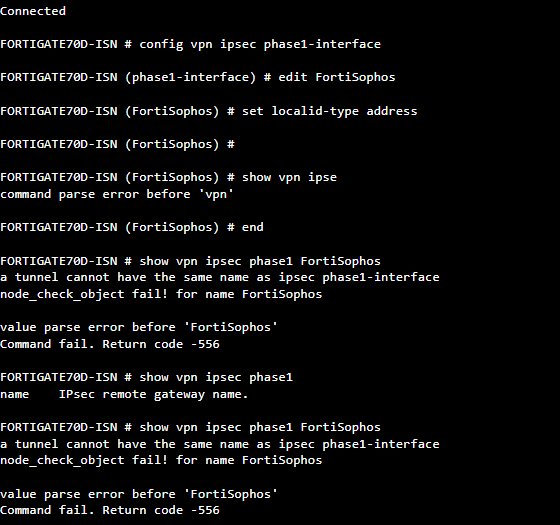
I have doing some labs and until now I have achieved to make a Sophos-Sophos and Forti-Forti Ipsec tunnel. However I am trying to make a Sophos XG-Fortigate IPSEC tunnel but my tunnel does not wake up.
I have followed this guide and configure my tunnel according to it.
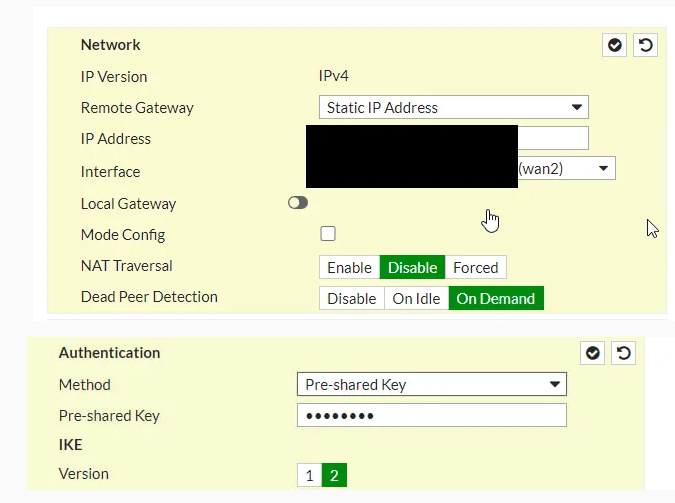
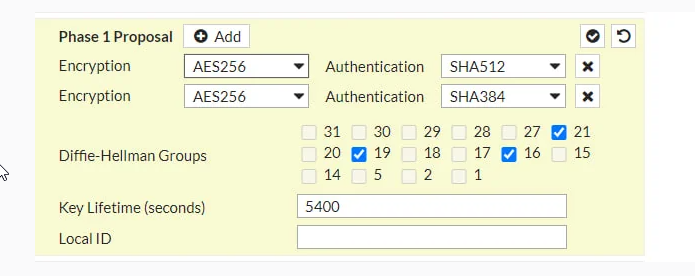
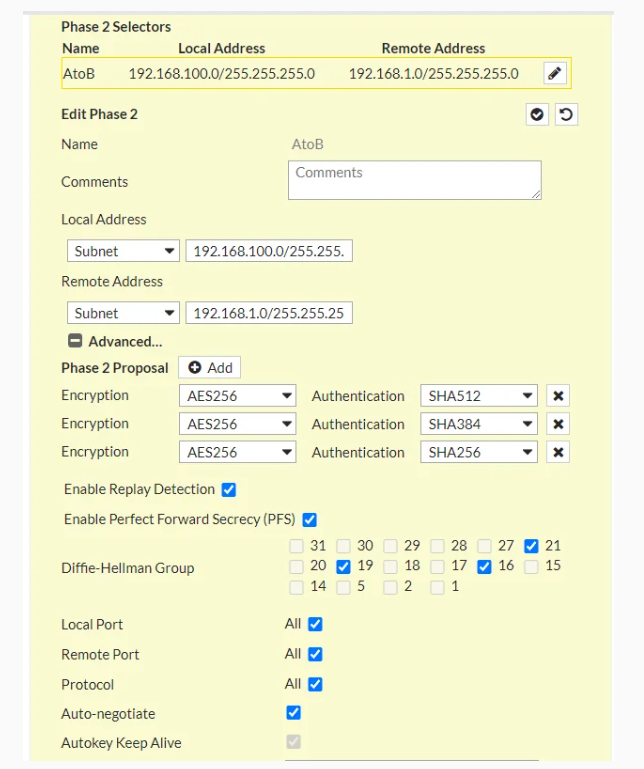
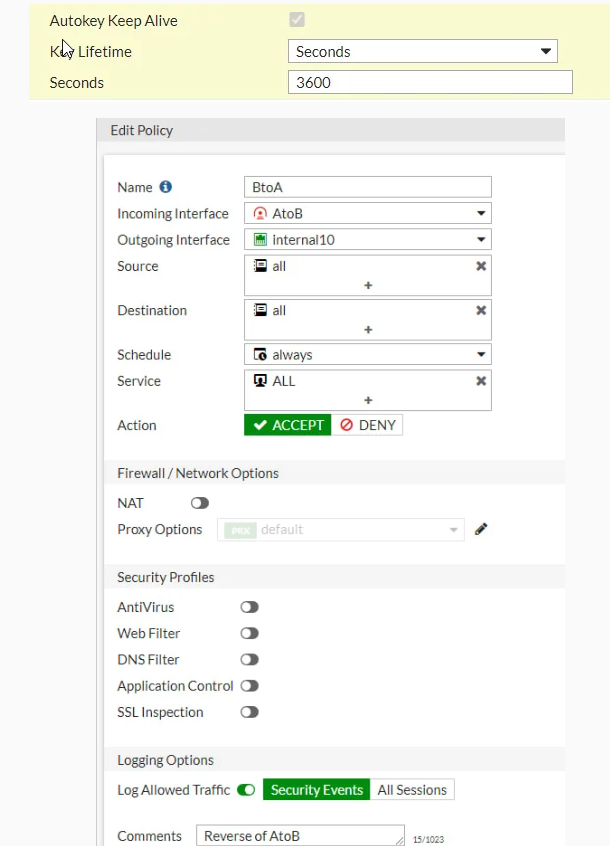
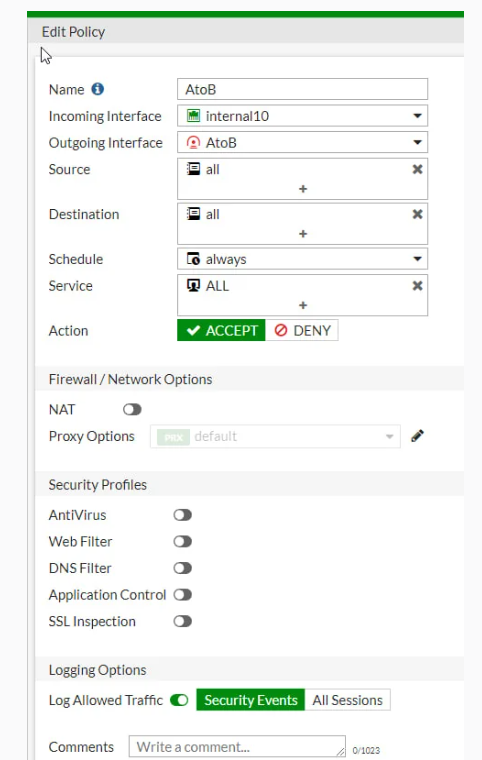
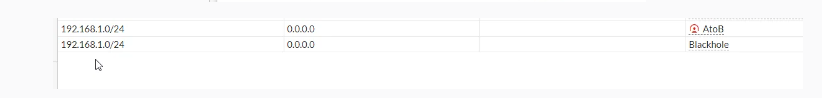
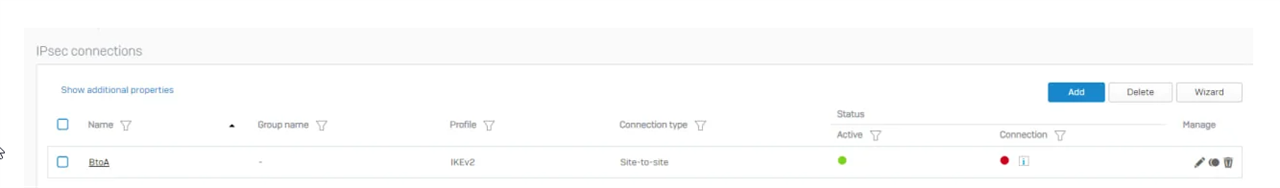
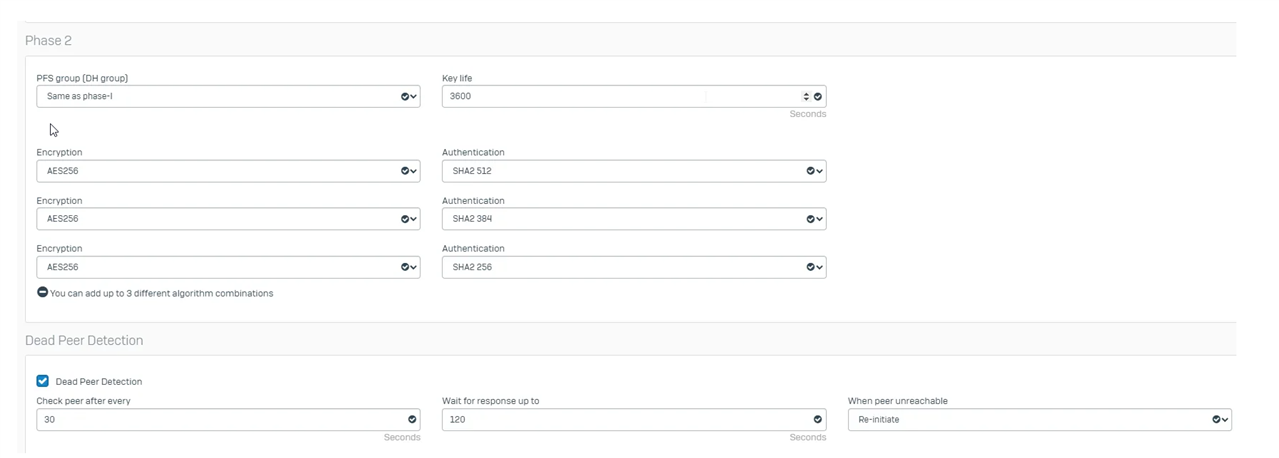
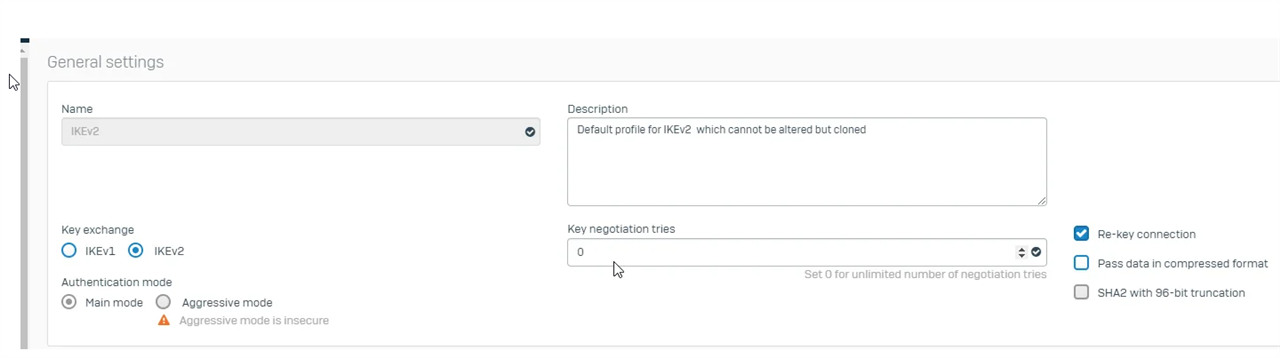
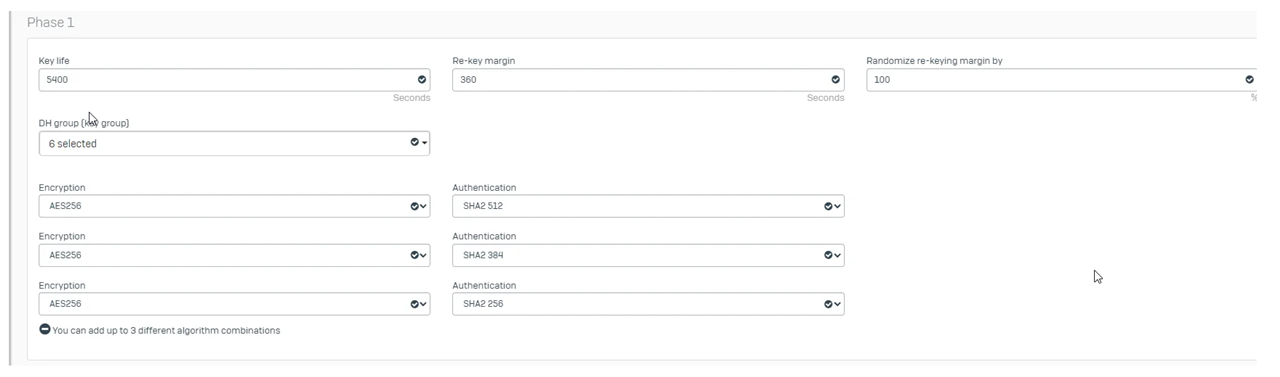
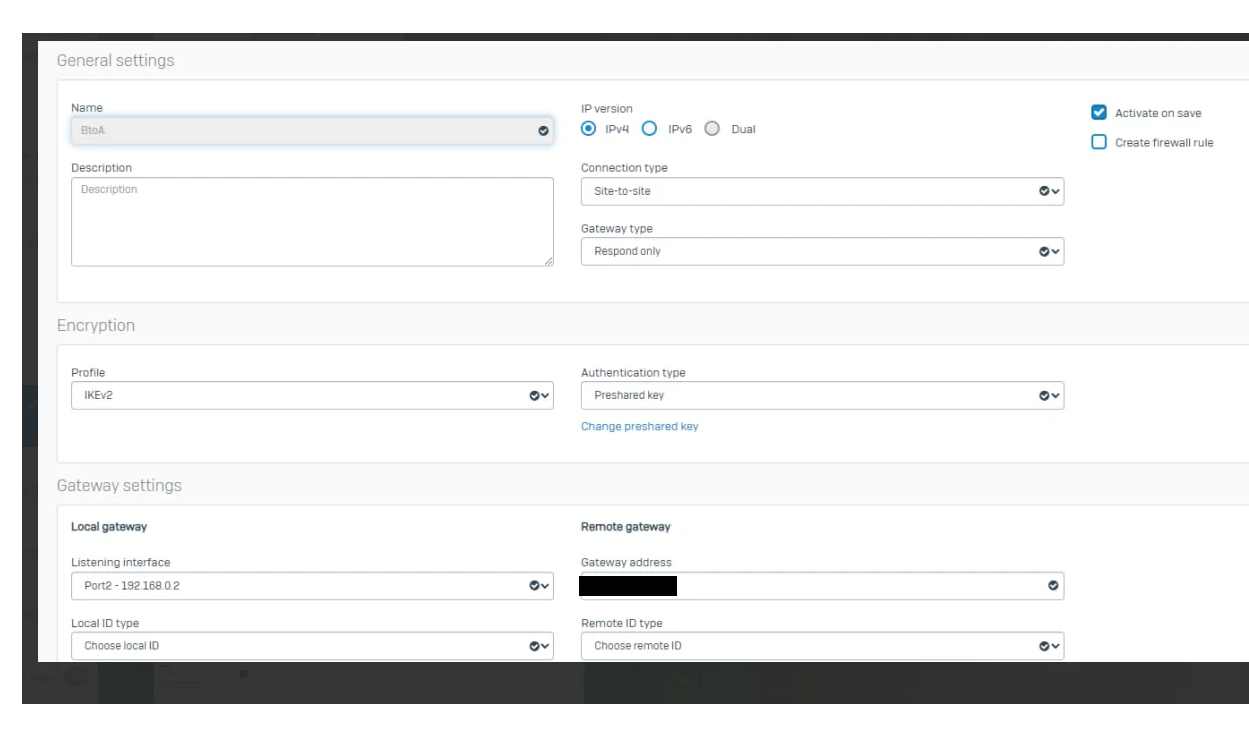
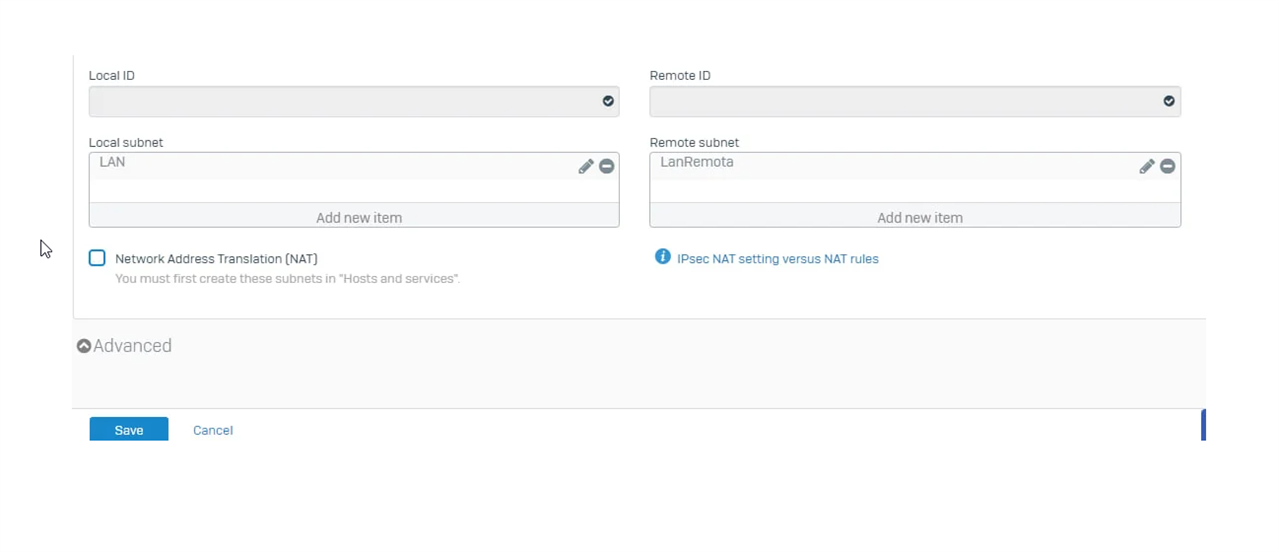
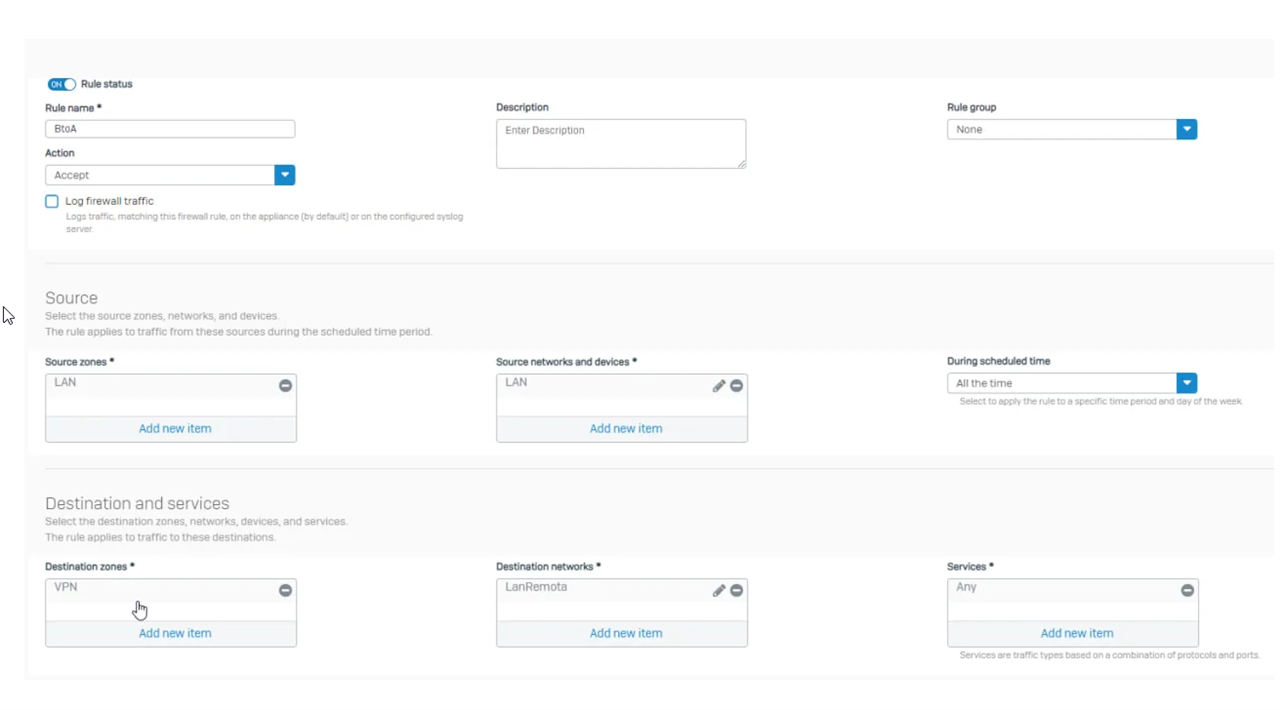
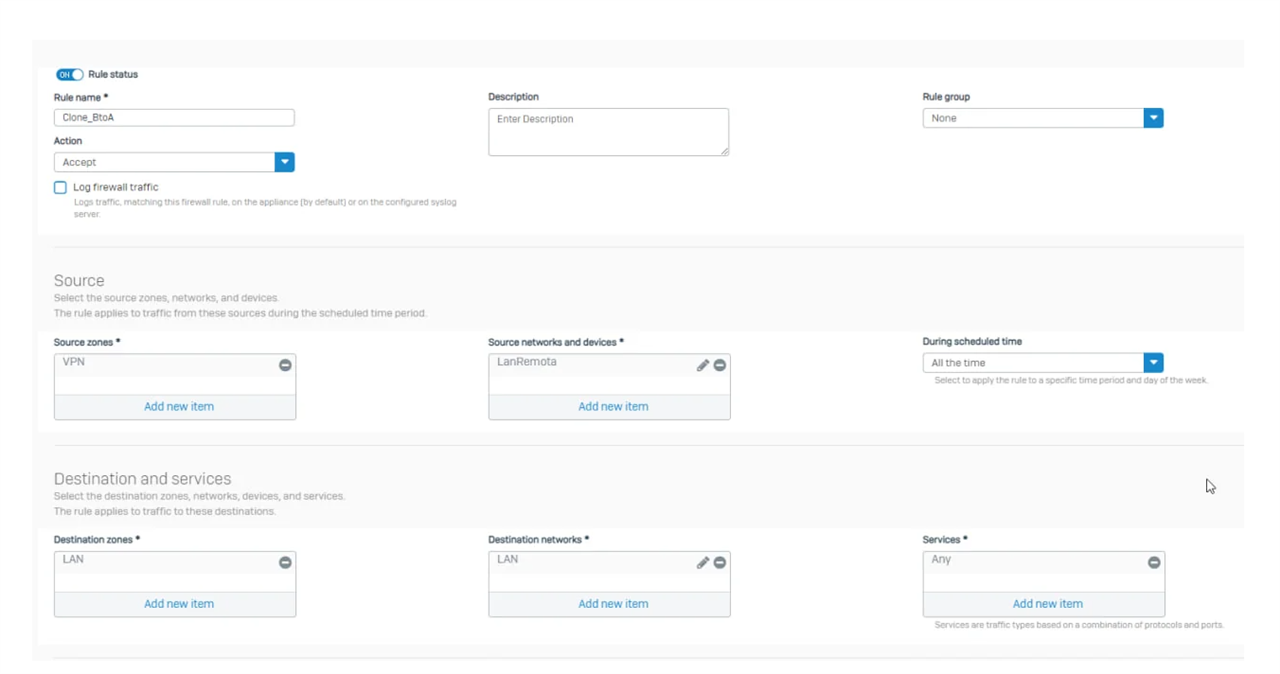
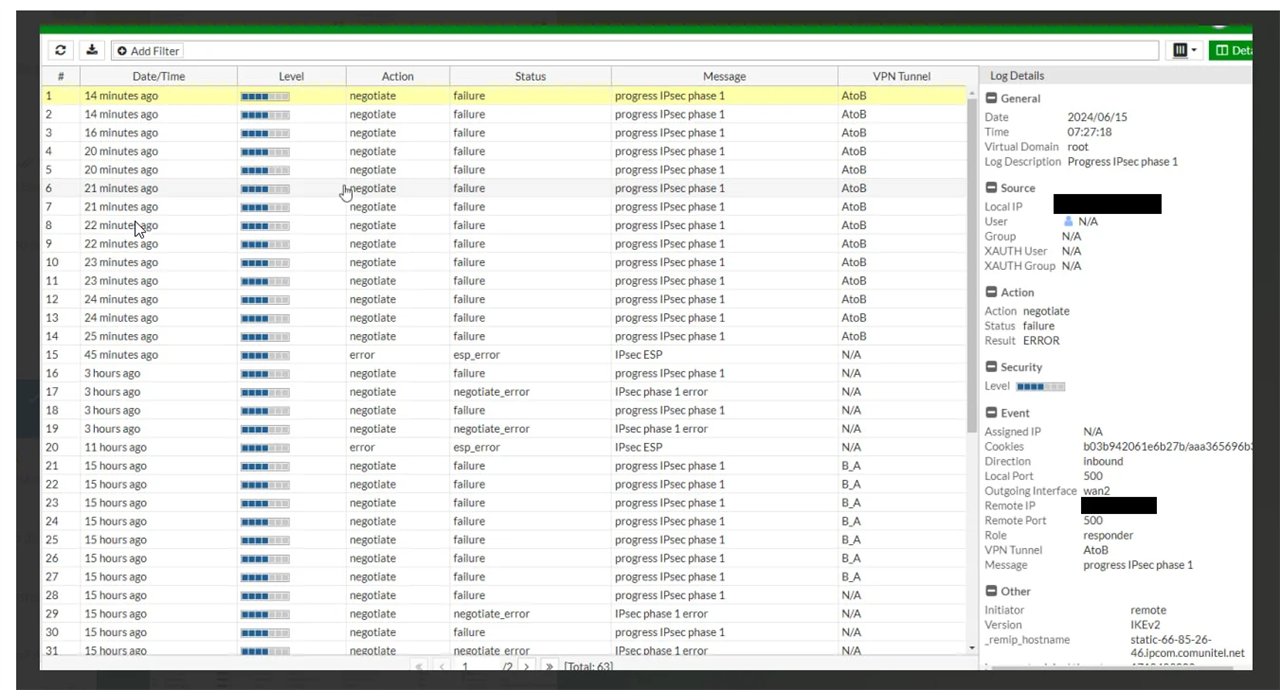
Can you help me to fix this?
This thread was automatically locked due to age.