Hi everyone,
I'm enforcing my TLS inspection rules to more strict and secure with best practices. So my Decryption Profile:
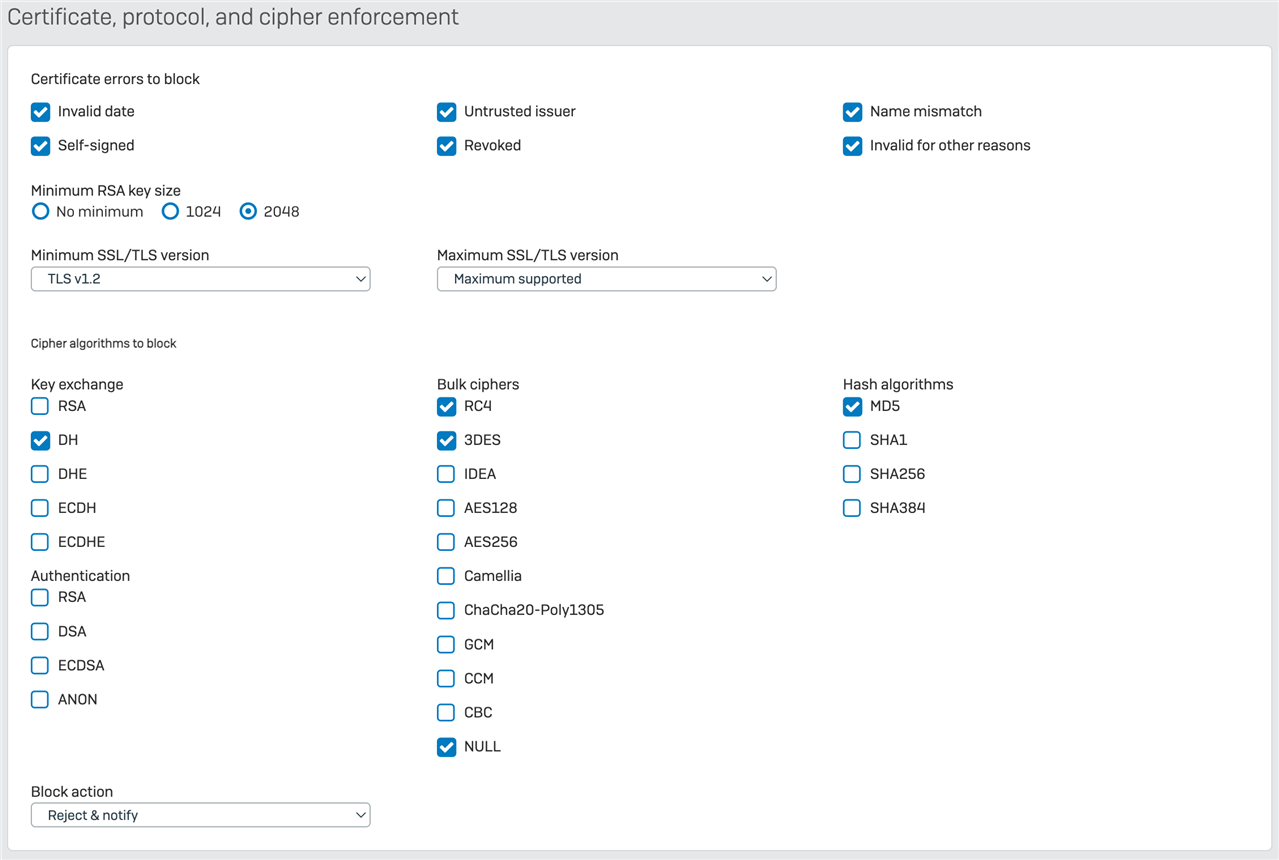
Using https://badssl.com/ for tests scenarios I had success in almost all practices:
| invalid date | |
| self-signed | |
| untrusted issuer | |
| revoked | |
| name mismatch | |
| invalid for other reasons |
CVE-2016-0701)
|
Revoked certificates aren't blocked as desired and good practice in other technologies.
Samples:
https://www.ssl.com/sample-valid-revoked-and-expired-ssl-tls-certificates/ (https://revoked-rsa-dv.ssl.com/)
https://badssl.com/ (https://revoked.badssl.com/)
Ref documents:
Untrusted user - Revoked: You must import a certificate revocation list (CRL) for this feature to work.
Also a old document from UTM:
I don't think is feasible create CRLs just for firewalls , since OCSP was created to solve this problem.
So OCSP isn't working by default? Is there any plan to cover this?
This thread was automatically locked due to age.

