Good day,
On our XG230 [SFOS 20.0.0 GA-Build222] we have two IPsec site-to-site tunnels on two different GWs.
Both connect to the same remote GW but use Different NATed local Subnets to Fortigate Firewall. IPSec policies are the same no change there.
When connecting the Primary tunnel over Port 3. Connection is established and traffic flows.
Connecting the Backup tunnel over port 2. Connection is established but no traffic is flowing
- Checked SD-WAN's
- Checked FW rules
Anyone have suggestions on how to get the traffic to flow over the Backup line which uses port 2 or the backup GW?
IPsec logs:
MRI_Ent2_SC-1[7524945]: ESTABLISHED 2 hours ago, <BackupGW IP>...105.243.233.162[105.243.233.162]
MRI_Ent2_SC-1[7524945]: IKEv2 SPIs: 1f652a70fc26c820_i* 220f6adcc589567d_r, rekeying in 21 hours
MRI_Ent2_SC-1[7524945]: IKE proposal: AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
MRI_Ent2_SC-1{20285}: INSTALLED, TUNNEL, reqid 107, ESP SPIs: c3a8933a_i 62641c46_o
MRI_Ent2_SC-1{20285}: AES_CBC_256/HMAC_SHA2_256_128, 0 bytes_i, 47012 bytes_o (909 pkts, 79s ago), rekeying in 9 hours
MRI_Ent2_SC-1{20285}: 172.31.1.9/32 === 10.89.140.53/32
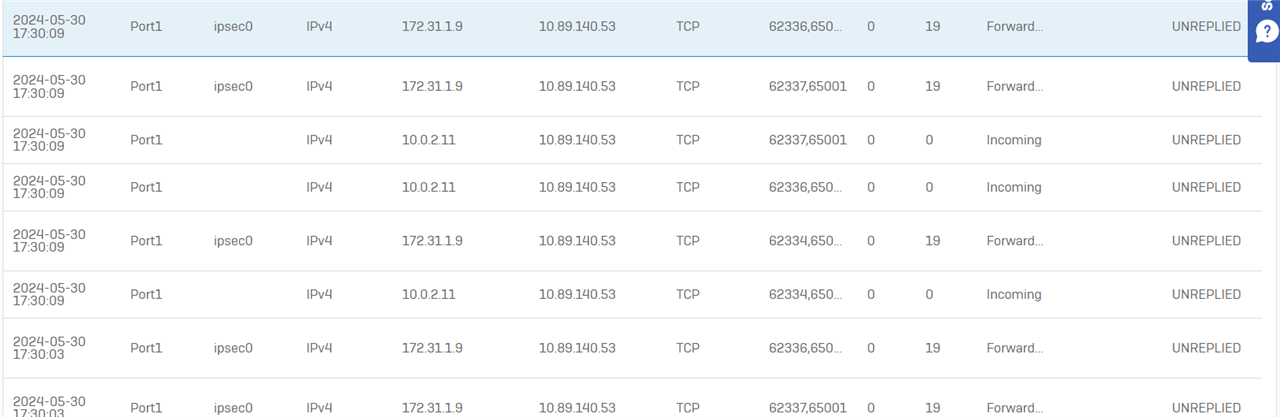
Packet Cap when on backup GW:
This thread was automatically locked due to age.


