Hello,
Is there a way to configure a VPN tunnel interface scenario, using the same WAN interface to receive the connection from remote points?
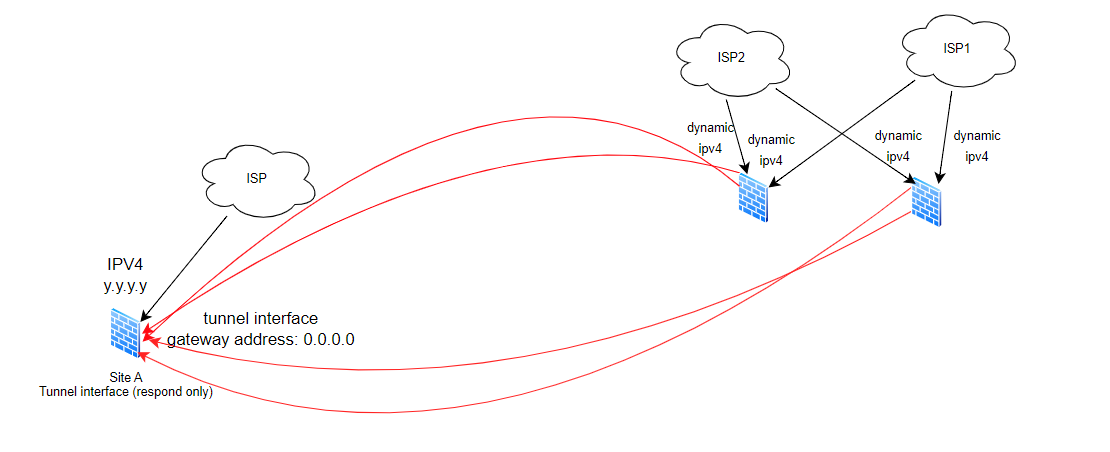
In this case, I have only 1 internet link on site A with a fixed IP, and I have several remote branches with internet links with dynamic IP, so I would like to use SD in the branches, to control VPN traffic based on criteria defined in the SDWAN profile (latency, jitter).
However, I came across the following problem: do I need to have only 1 tunnel interface on site A to receive the connection from all branches? Or do I need to have 1 tunnel for each branch? as the remote IPs are dynamic, I cannot set them in the site A tunnel and as I only have 1 internet link in the head office, I cannot create more than 1 tunnel, as it conflicts with the existing tunnel!
Using only 1 tunnel at site A, when the primary VPN at the remote branch goes down, the tunnel interface at site A goes into "down" mode, and this drops communication
This thread was automatically locked due to age.


