Hi all,
# XG330
I have a project to set up an SFTP server to transfer data securely from a remote station to the SFTP server located in
the DMZ.(Head Ofice)
the server is installed, configured and integrated into the dmz.
the remote client uses an sftp tool to automatically transfer data with a configured task, using : ipaddr: non-standard port
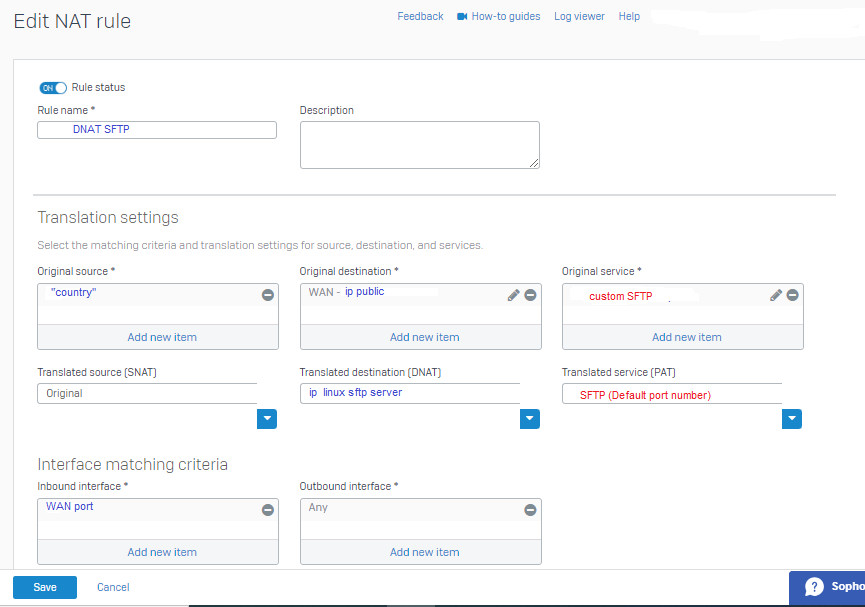
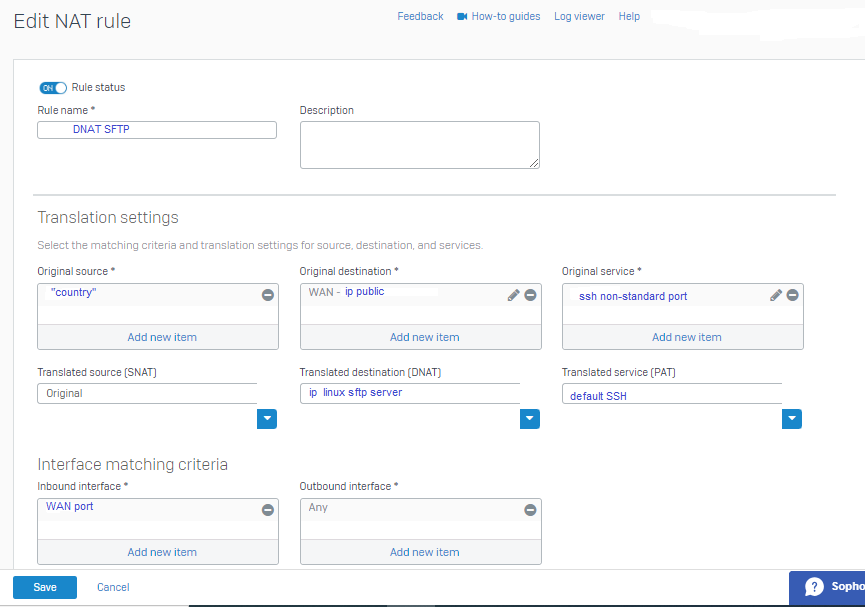
So I created a dnat rule as follows:
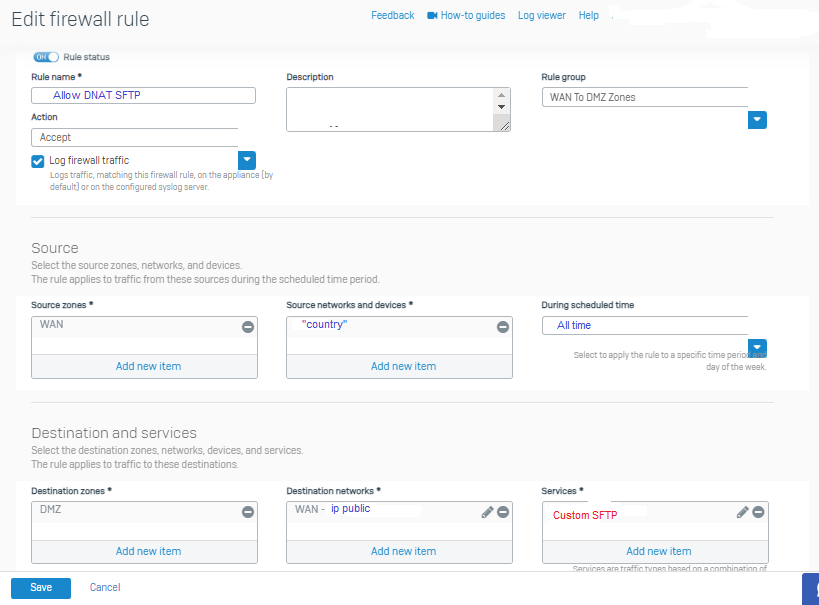
and I created the firewall rule as follows:
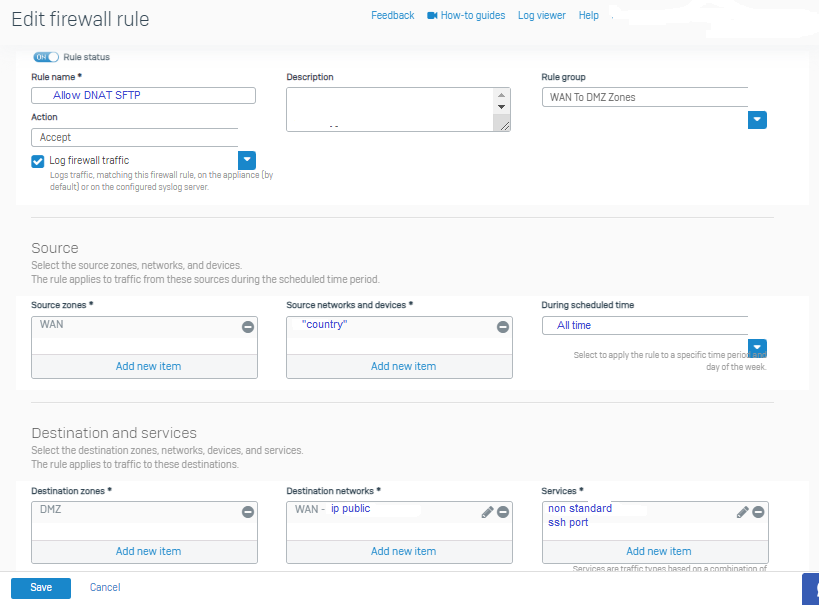
For more security the client will have to connect with a non-standard SFTP port, then the FW will have to do the port translation of the non-standard port
to the default SSH port which is 22.
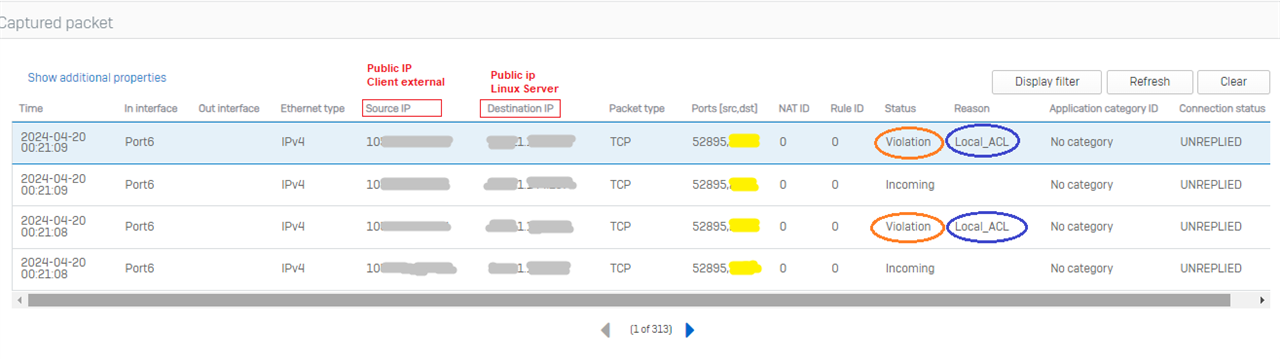
the first connection tests were not successful! Impossible to connect
Is there anything I forgot?
Are there other particularities to take into account and adjust the configuration?
thanks
This thread was automatically locked due to age.