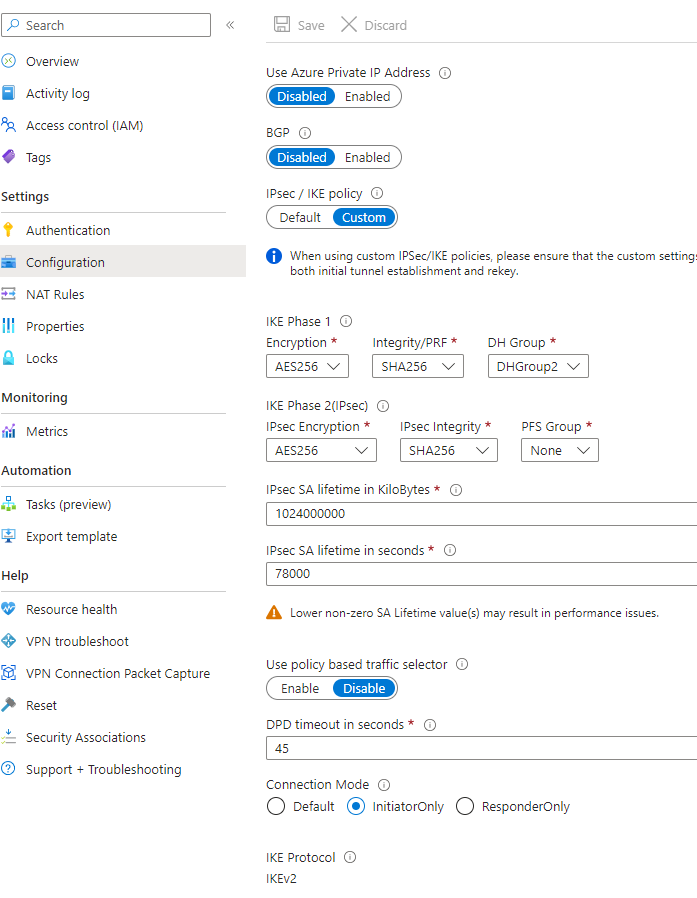
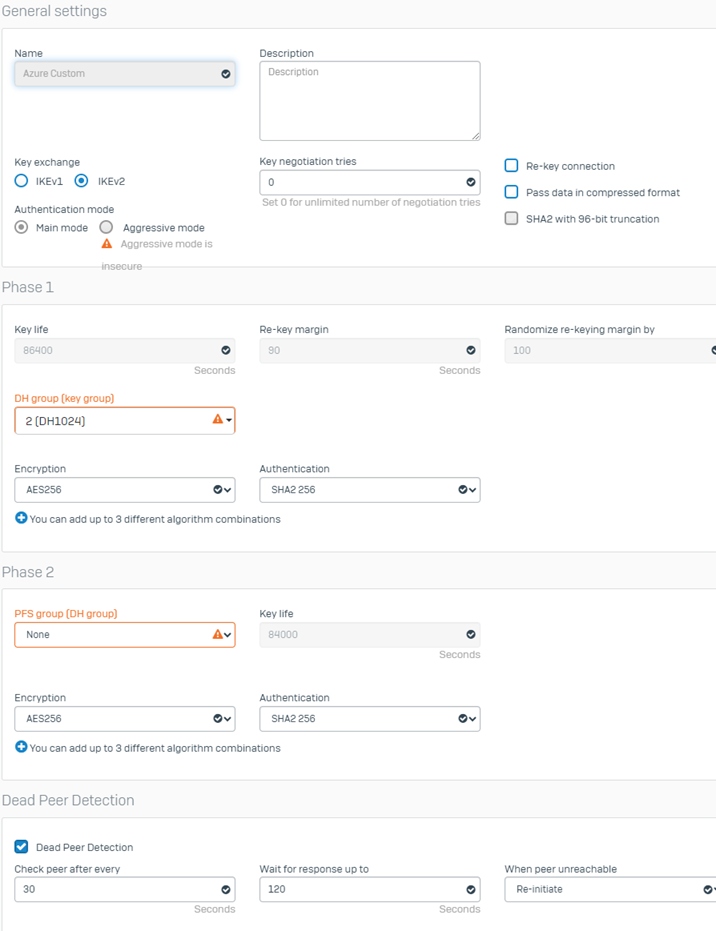
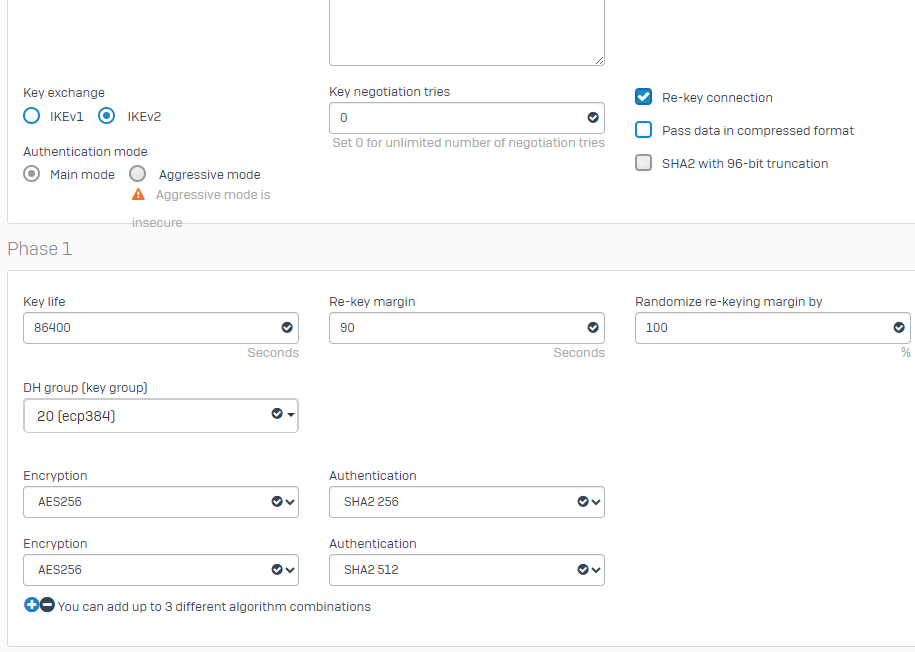
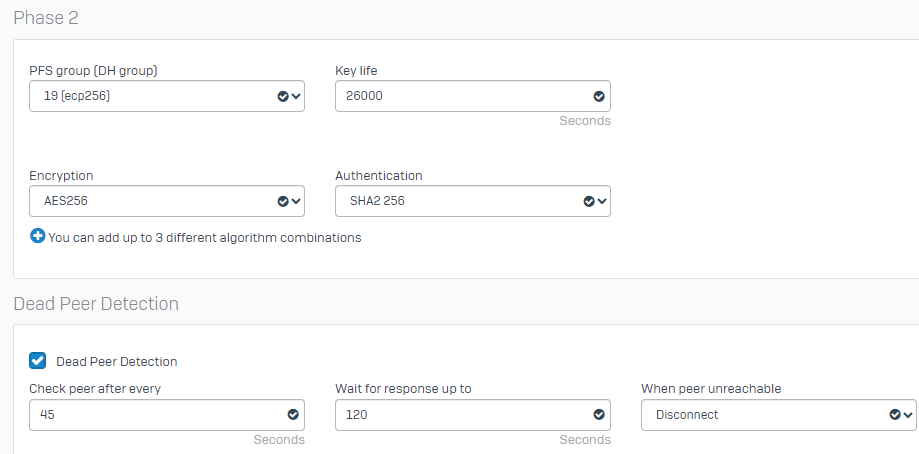
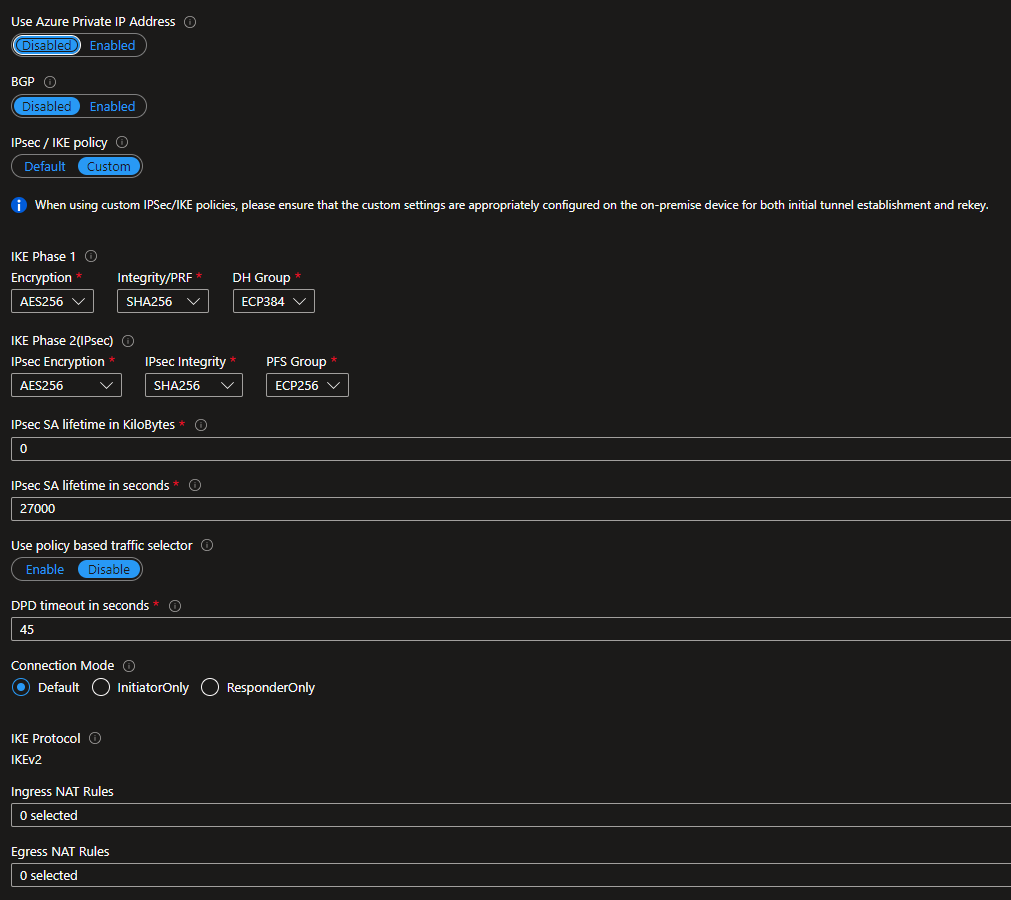
Hello! We are an MSP with about 20 clients that have servers hosted in Azure. These 20 clients have various hardware models of Sophos XG and XGS firewalls with various steps of firmware from 19.5.3 to 20.0.22. Those firewalls have an IPSec site to site tunnel built to the Azure Virtual Gateways for each client. We have been plauged with constent disconnects across all 20 connections. We've opened multiple cases with Sophos, cases with Microsoft and had a third-party review the policy settings.
- We've adjusted Key Timers for both Phases, using lower values on the initiator side as recommeded.
- We've tried multiple encryption levels and DH group combinations.
- Dead Peer Detection is enabled for 30 second checks, at both ends.
But it never fails that every night we recieve the alerts that multiple of these tunnels have disconnected. We have to manually log into each firewall and toggle the tunnel back to green. Sometimes the connection is Green/Green but traffic isn't passing so we have to toggle the connection off then back on.
We're grasping at straws here and are just questioning Sophos' ability to handle connections with Azure at this point.
Anyone have any magic recipes of IPSec Policies that have worked solid for them in this situation, specifically with Azure?
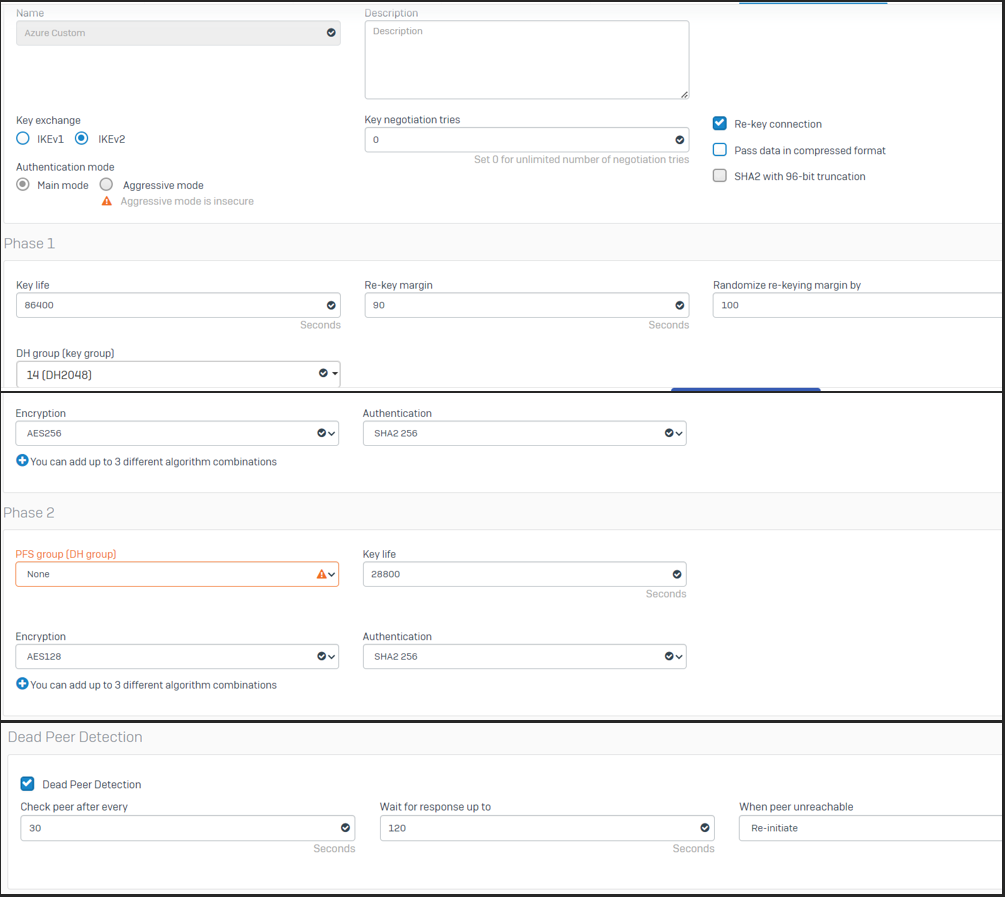
I've attached the latest policy we are using with no luck
.
This thread was automatically locked due to age.