Good Eve.
Trying to connect to a network switch via https.
Error page : The trust status of this website's certificate could not be securely established.
About this request
URL: https://somePublicIP
- Certificate details:
- Valid From: Feb 19 03:51:01 2024 GMT
- Valid To: Feb 18 03:51:01 2025 GMT
- Serial Number: 57:60:17:61:a4:06:e2:5b:92:2b:95:5b:85:5f:62:1d
- Subject: C= , ST= , L= , CN=192.168.0.2, O= , OU=
- Issuer: C= , ST= , L= , CN=192.168.0.2, O= , OU=
Its a self signed cert the device created. I know it works and I'm the only IP that can connect via the other sides firewall rules. It works bypassing SFOS.
In SFOS
I've added the public IP to every place i can think of to allow the connection.
I've created a URL group with the IP and added it to the policy.- I'm blocking urls with IPAddresses
I've added it to the Local TLS exclusion list
I've created an web exception
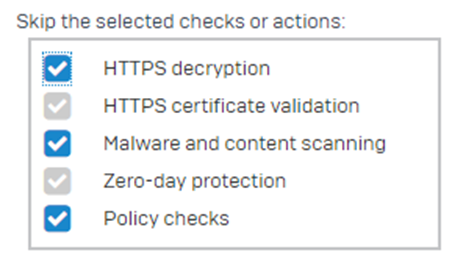
I've created a SSL/TLS inspection rule exemption
I've run conntrack -F
What am I missing? At this point id expect SFOS to totally ignore the IP.
An old post talked about adding the devices Cert to SFOS but that would be impossible if you cant connect to it. Shouldn't SFOS be skipping its checks by now?
All help would be greatly appreciated.
This thread was automatically locked due to age.
